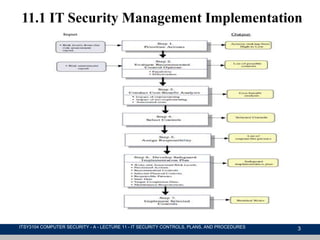
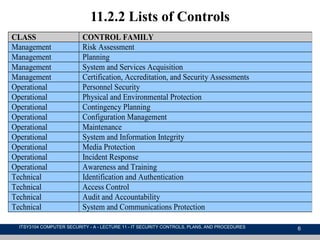
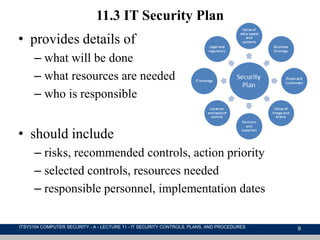
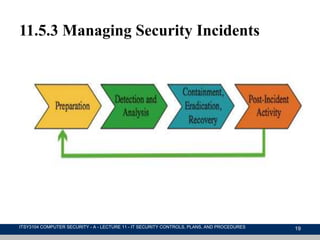
This document discusses IT security management, focusing on the implementation of security controls and procedures essential for protecting against threats and vulnerabilities. It covers the classification of security controls, the importance of an IT security plan, the training required for personnel, and the ongoing maintenance and evaluation of security measures. Additionally, it emphasizes the need for incident management protocols and the regular monitoring of risks to enhance organizational security.