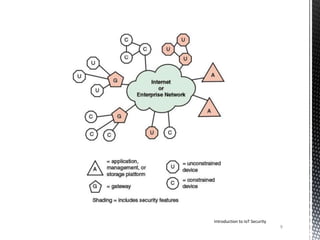
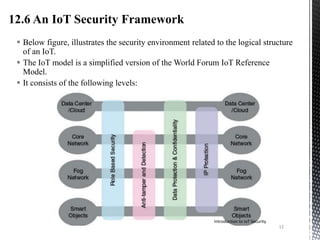
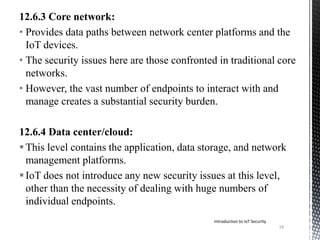
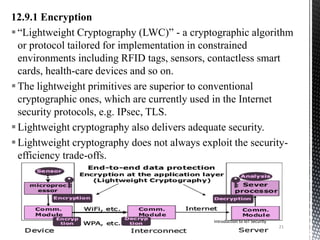
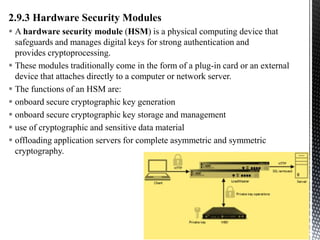
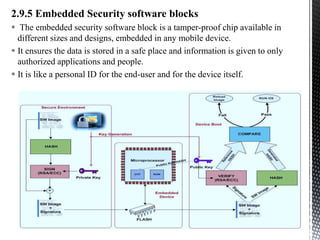
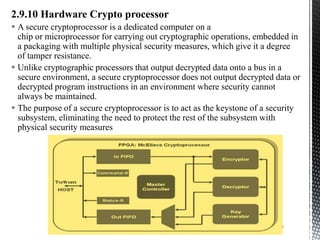
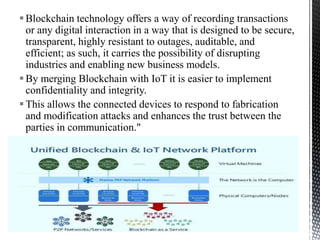
This document provides an introduction to IoT security. It discusses key components of IoT including sensors, actuators, microcontrollers, communication capabilities, and identification. The document outlines the ITU-T IoT reference model and describes security challenges at different levels including devices, fog networks, core networks, and data centers. It also discusses common IoT security issues such as unpredictable behavior, device similarity, problematic deployments, lack of upgrades, and lack of transparency. Finally, the document summarizes common IoT security tools including encryption, passwords, hardware security modules, two-factor authentication, and public key infrastructure certificates.