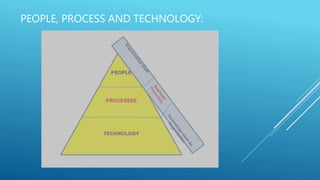
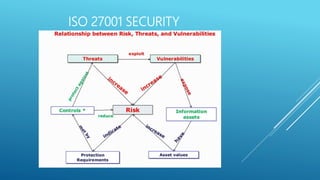
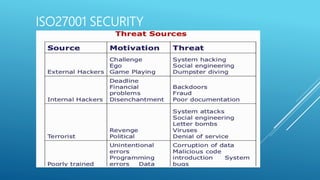
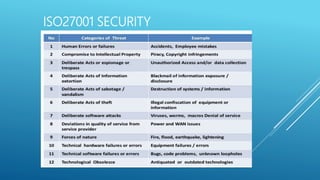
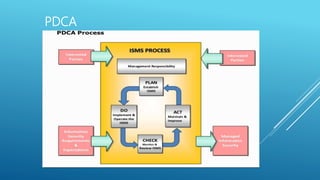
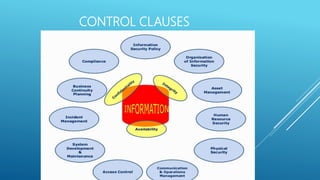
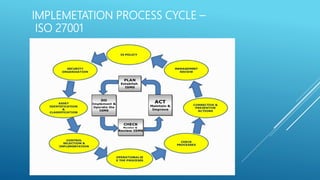
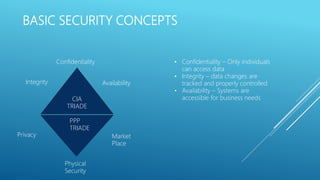
The document provides an introduction to information security, detailing key concepts such as the CIA triad (confidentiality, integrity, availability), risk assessment processes, and the importance of a robust security policy. It outlines the need for a structured approach to information security management systems (ISMS) in accordance with ISO 27001 and emphasizes the roles of people, processes, and technology in securing information assets. Additionally, it discusses the benefits of a security policy and the necessity of ongoing assessments and updates to address emerging threats.