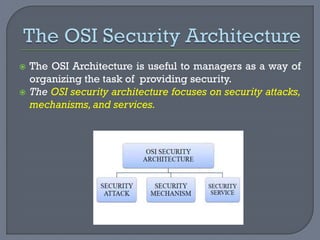
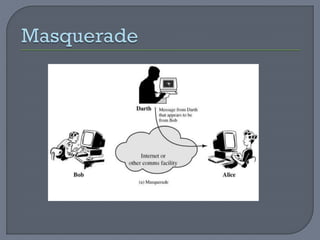
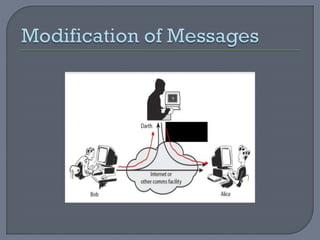
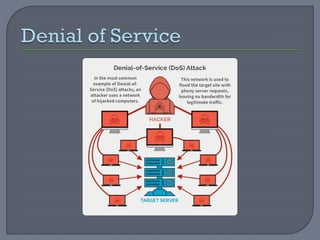
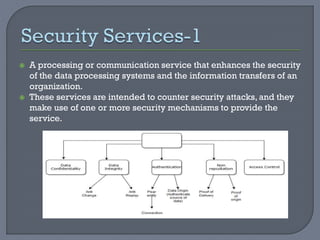
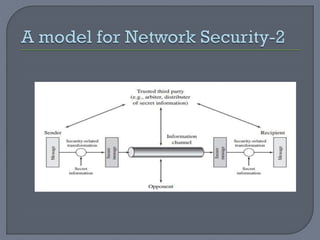
The document provides an overview of network security, defining networks and detailing various security mechanisms, services, and attacks. It outlines different types of attacks, including passive and active attacks, and explains security services like authentication and data integrity that counter these threats. Additionally, it discusses a model for network security which highlights the importance of secure transmission and secret information sharing between entities.