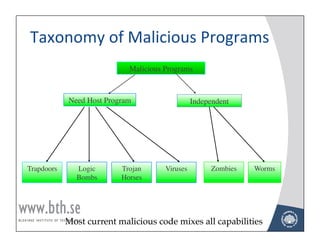
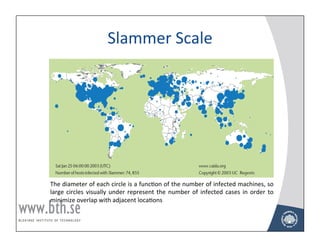
The document provides an overview of malicious software including viruses, worms, Trojan horses, and distributed denial of service (DDoS) attacks. It defines viruses as self-replicating code that attaches itself to other programs and executes when the host program runs. Worms are independent programs that replicate themselves across networks to infect other computers. The document also describes other types of malicious software like backdoors, logic bombs, and Trojan horses, and explains how DDoS attacks are constructed to overwhelm servers.













































![Where
malware
Lives:
Auto
start
• Folder
auto-‐start
• Win.ini
:
run=[backdoor]"
or
"load=[backdoor]".
• System.ini
:
shell=”myexplorer.exe”
• Autoexec.bat
• Config.sys
• Init.d
48!](https://image.slidesharecdn.com/malicioussoftware-121211103119-phpapp02/85/Malicious-software-48-320.jpg)


















