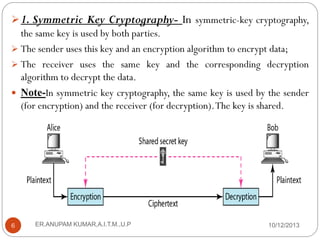
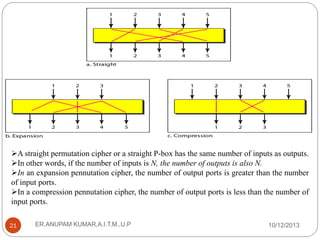
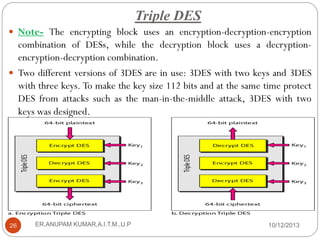
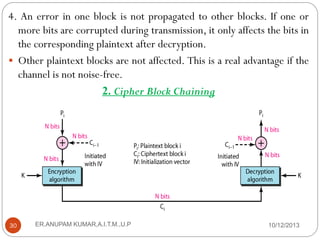
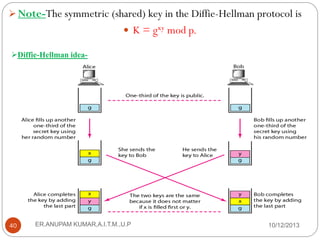
This document provides an overview of cryptography presented by Mr. Anupam Kumar. It begins with an introduction to cryptography, including the components involved such as plaintext, ciphertext, ciphers, keys, and common roles like Alice, Bob and Eve. It then describes the two main categories of cryptography - symmetric-key and asymmetric-key cryptography. Symmetric-key uses a shared secret key for encryption and decryption, while asymmetric-key uses separate public and private keys. The document provides examples of traditional ciphers like substitution, shift and transposition ciphers, as well as modern ciphers like the XOR cipher.