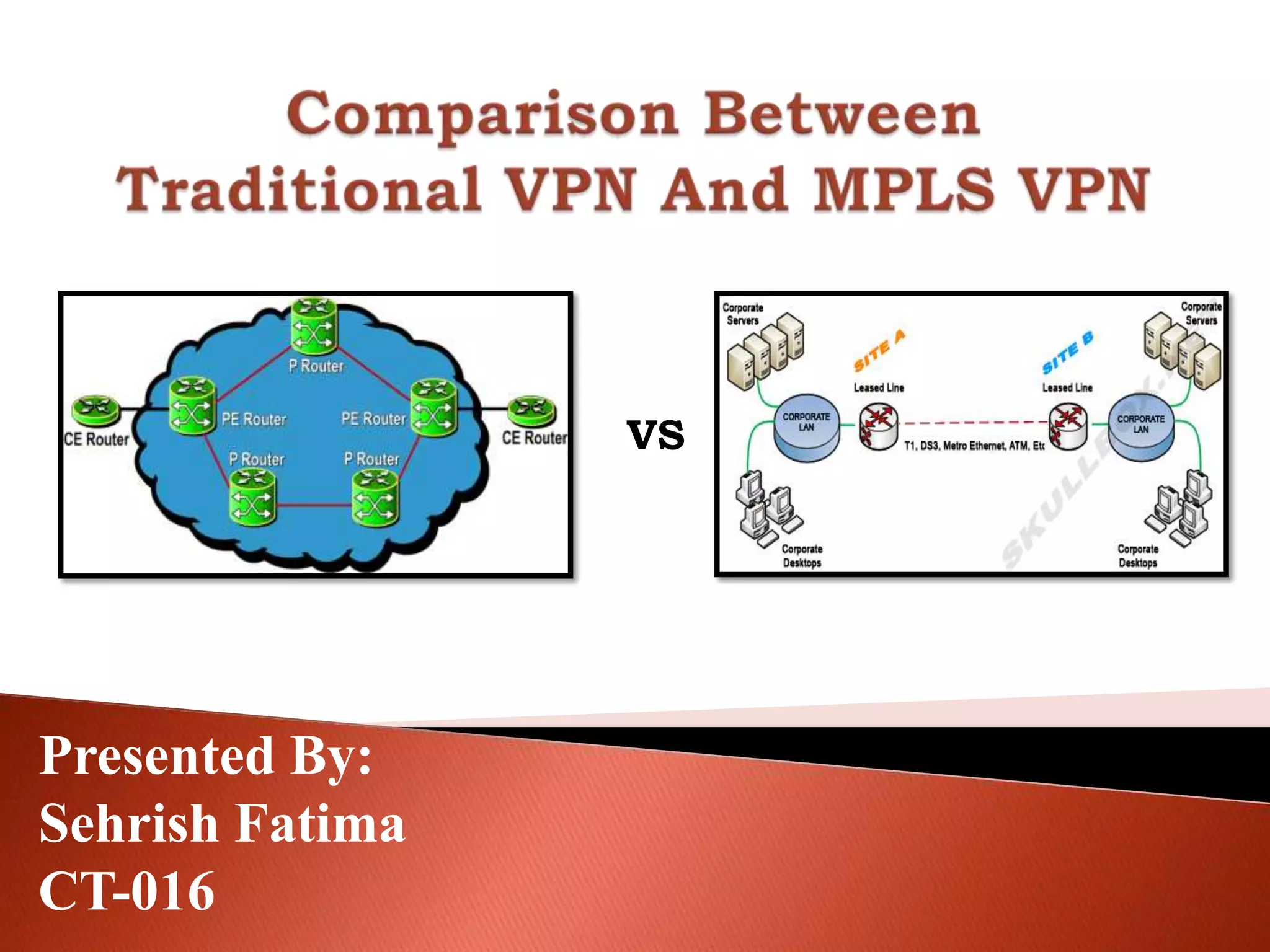
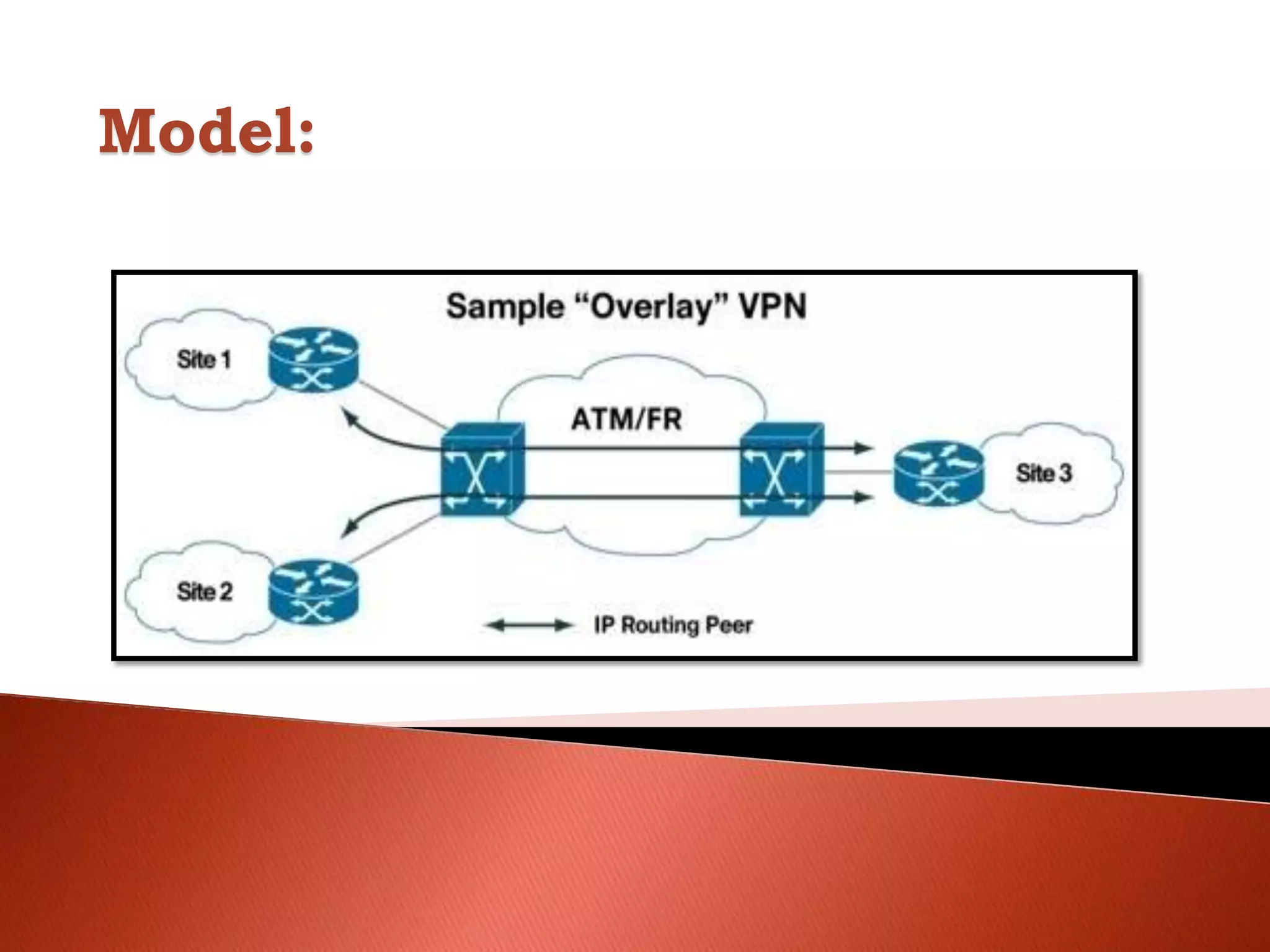
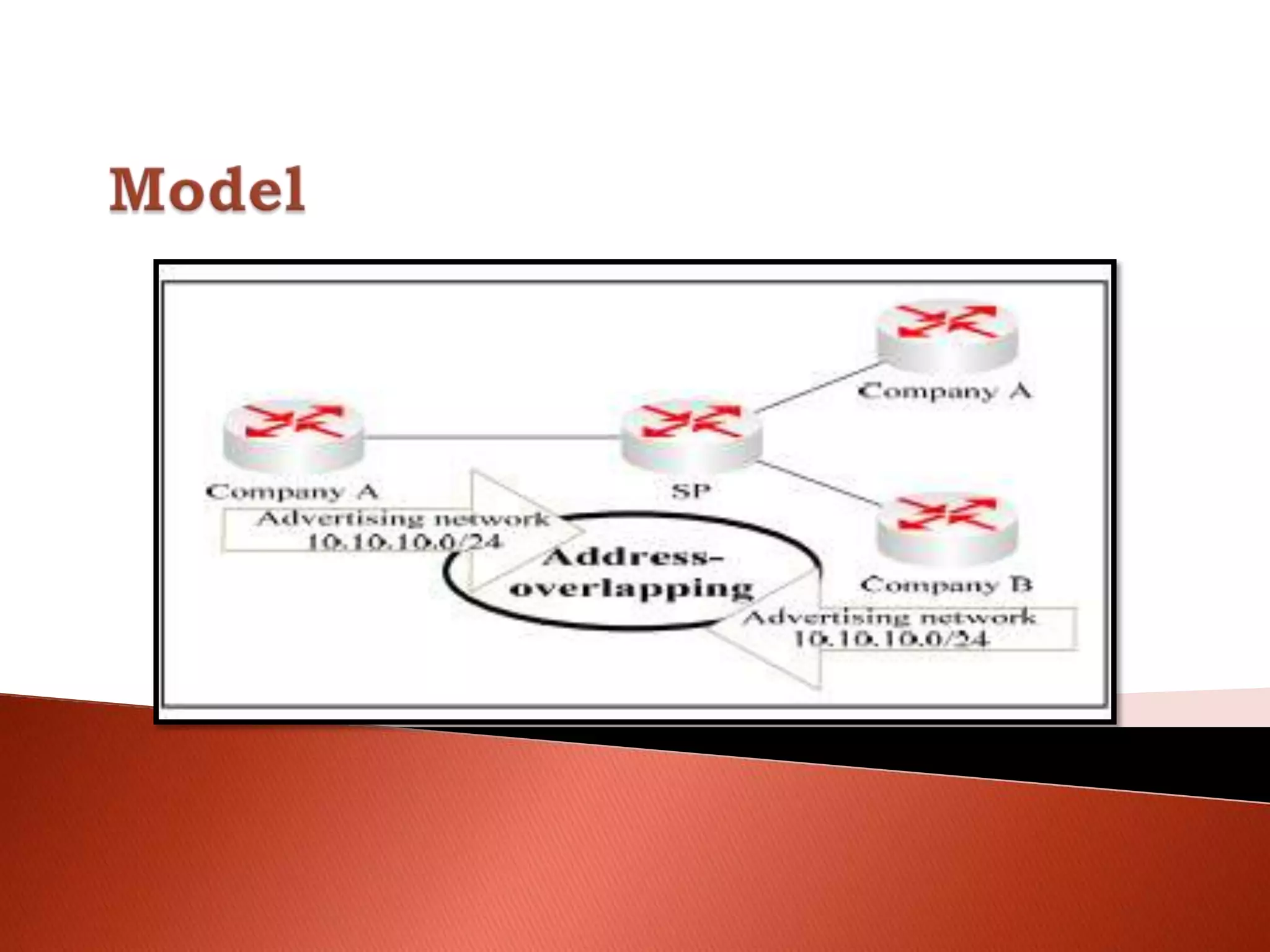
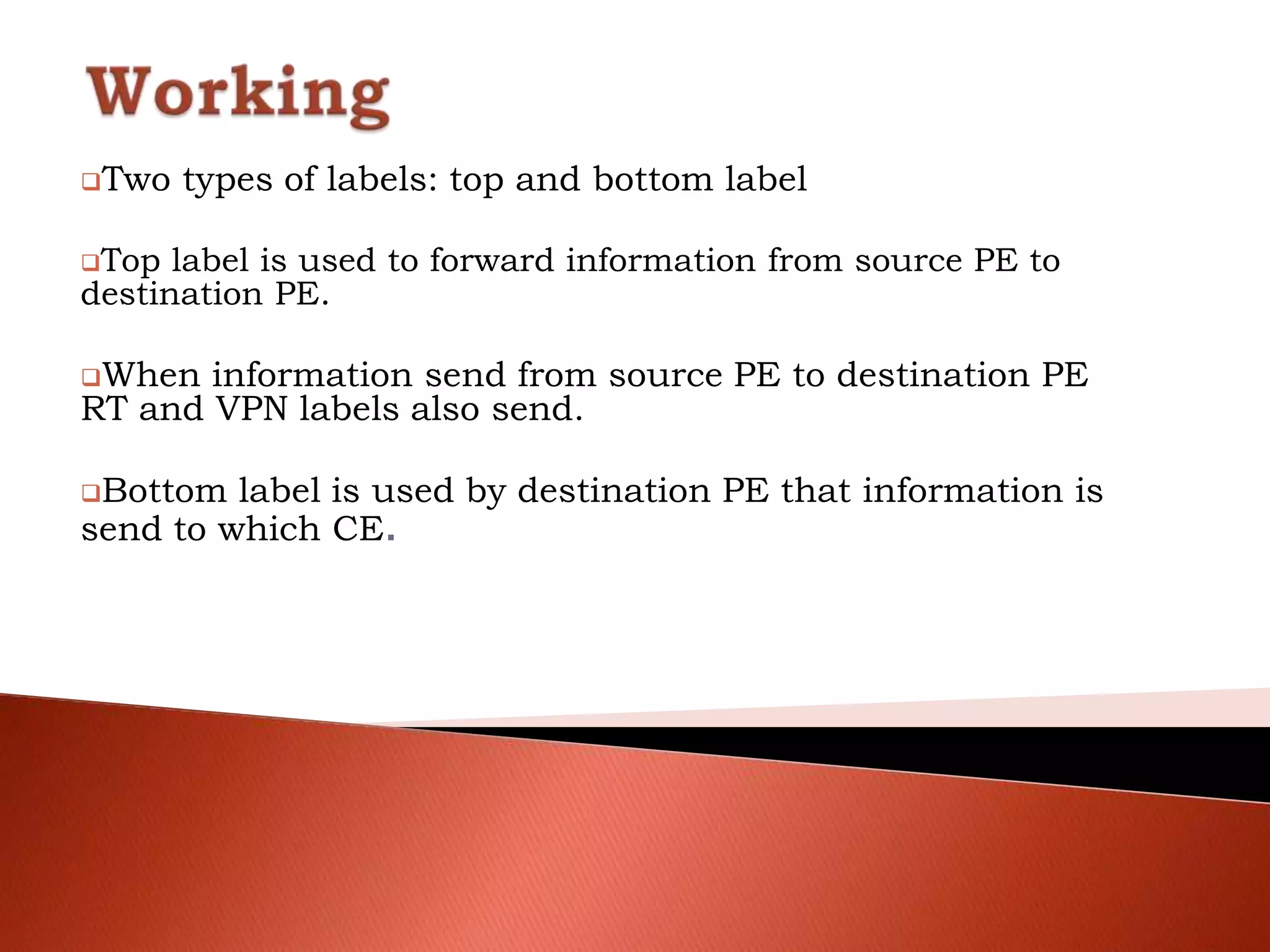
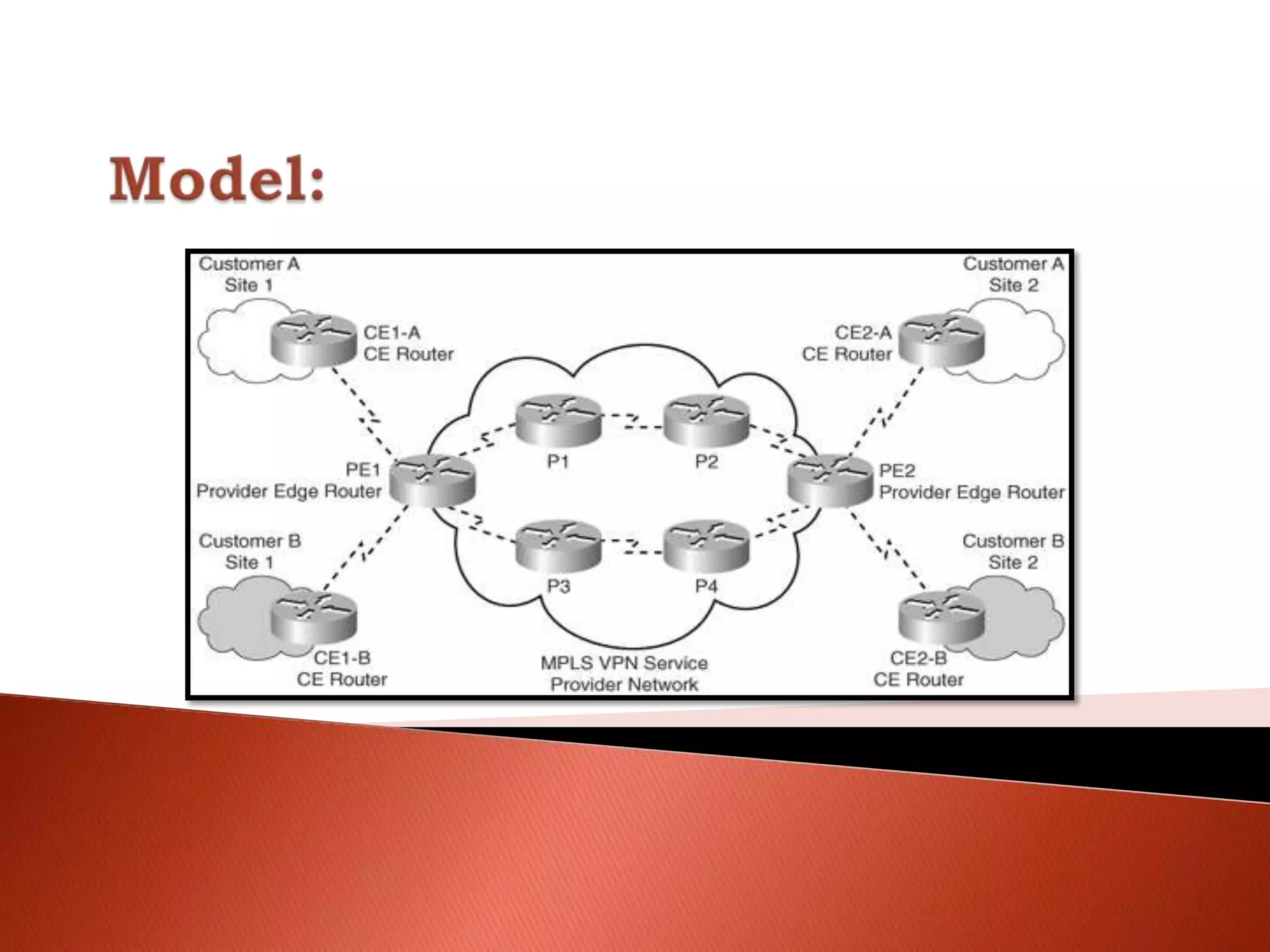
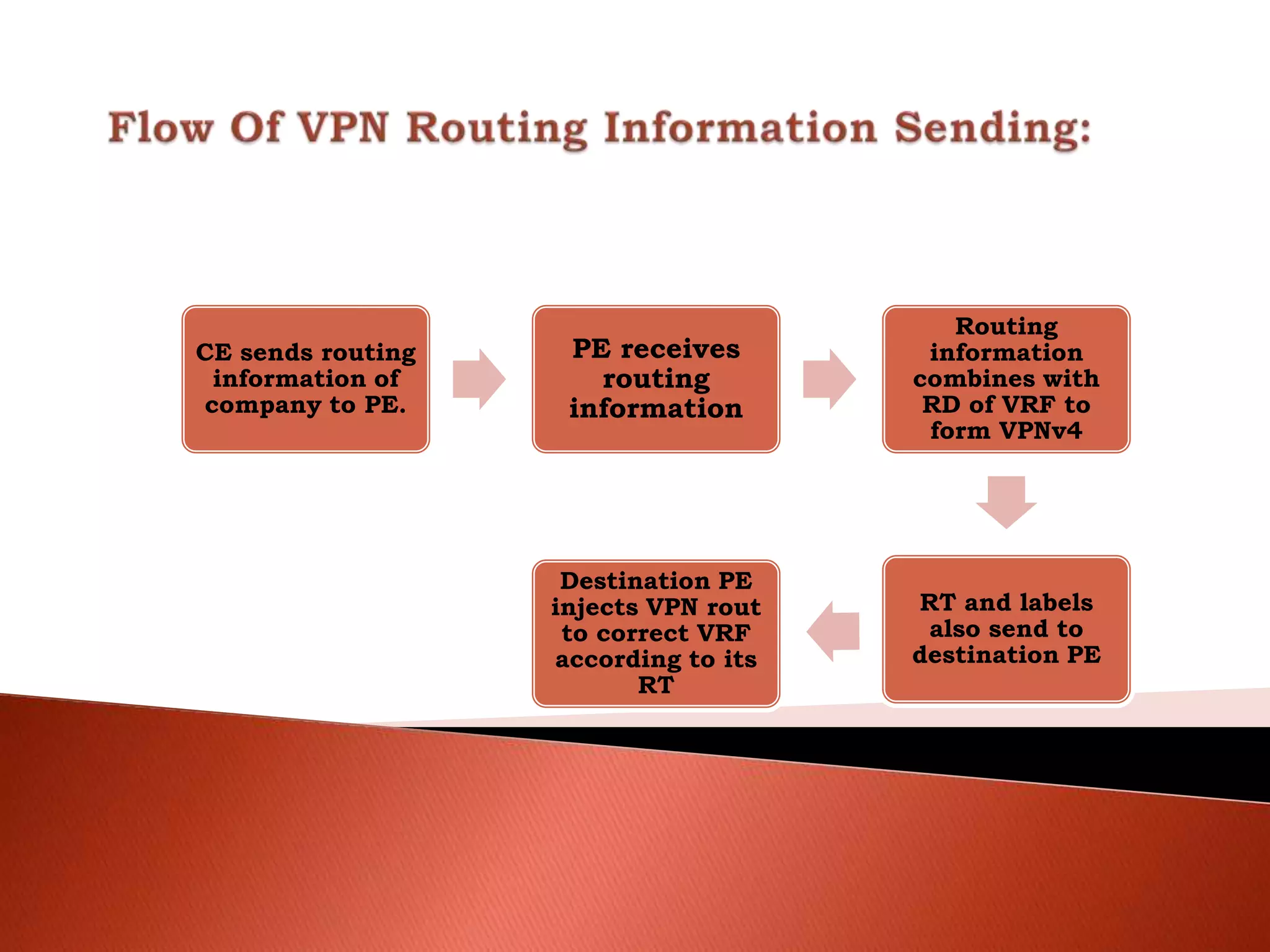
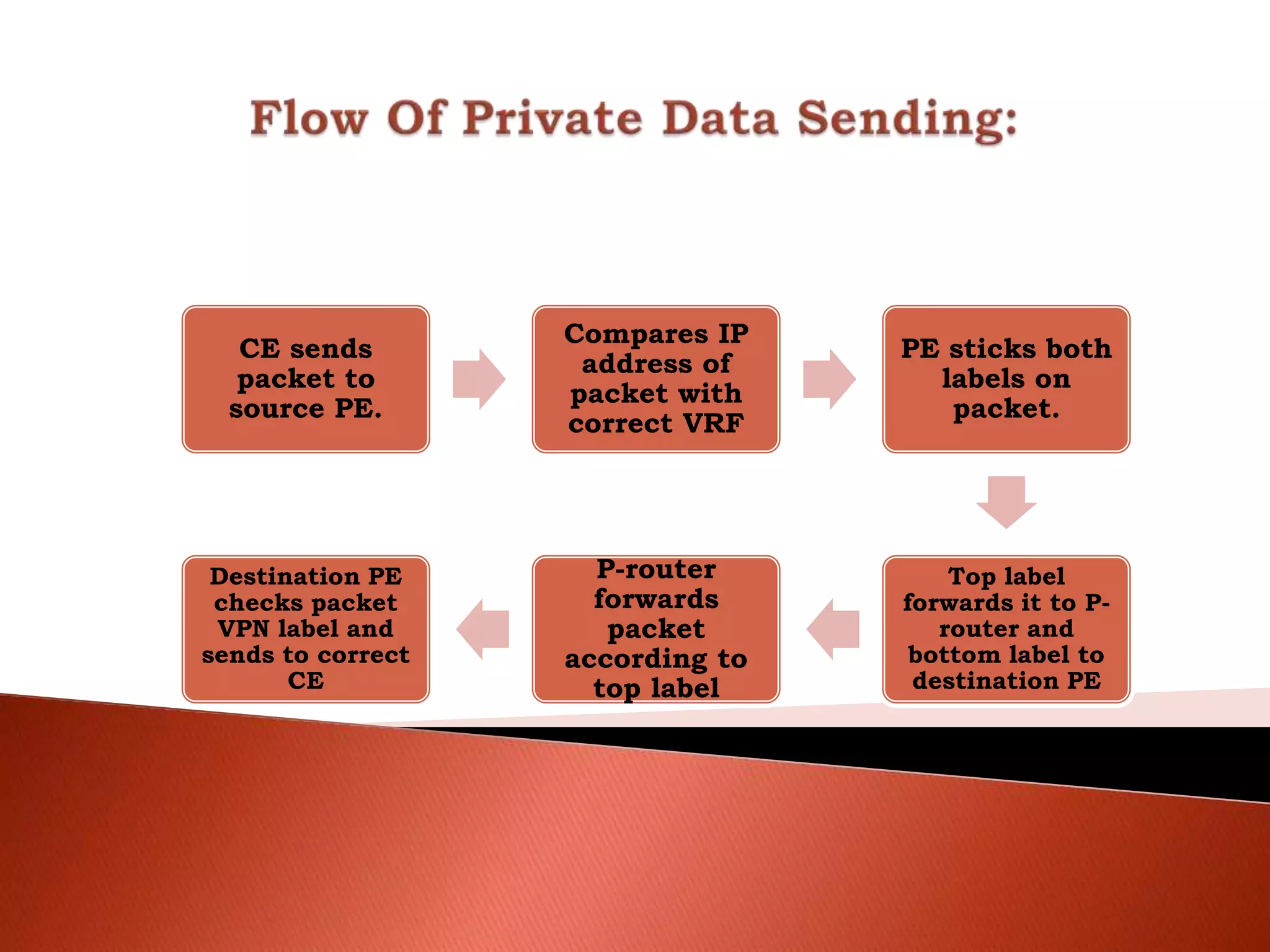
The document discusses different types of traditional VPNs including overlay VPNs, peer-to-peer VPNs, and MPLS VPNs. Overlay VPNs use virtual circuits to connect sites but have high costs and difficult management. Peer-to-peer VPNs improve on this by exchanging routing information directly with the service provider. MPLS VPNs are considered the new standard as they use MPLS to label and route traffic, solving issues like address overlapping and data leakage while allowing for easy management and lower costs compared to traditional VPNs. The document concludes that MPLS VPN provides a secure and cost-effective solution for connecting company sites worldwide.