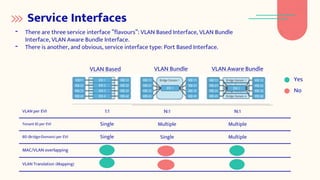
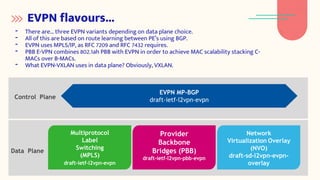
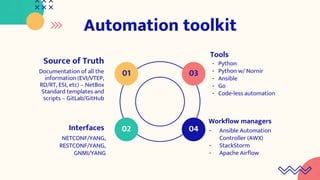
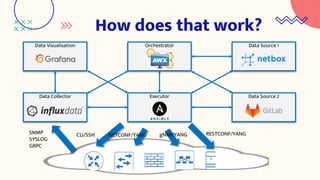
EVPN is a network virtualization technology that allows Ethernet services to be delivered across MPLS or IP networks. It uses BGP for the control plane to distribute MAC and IP addresses and can support both single-active and all-active multi-homing topologies. EVPN provides flexibility in service delivery and has been widely adopted by major service providers and cloud providers for a variety of use cases including data center interconnect and virtual machine mobility. Automation of EVPN configuration can simplify provisioning and management through the use of tools like NetBox, Python scripts, Ansible, and workflow managers.









![Control and data plane in EVPN
- MAC/IP tuple routing it’s introduced using MP-BGP.
- Flood-and-learn method are kept between PE-CE (in data plane).
- MP-BGP use between PEs enable routing and MAC policy, TE criteria's, etc...
- EVPN it’s using MP-BGP AFI 25 (VPLS) and SAFI 70 (EVPN), and includes Route
Distinguisher (RD), Route Targets (RT), BGP communities, etc…
BGP Routes
Route Types:
[1] Ethernet Auto-Discovery (AD) Route
[2] MAC Advertisement Route
[3] Inclusive Multicast Route
[4] Ethernet Segment Route
[5] IP Prefix Route
BGP Route Attributes
Extended Communities:
- ESI-MPLS Label
- ES-Import RT
- MAC Mobility
- Default Gateway](https://image.slidesharecdn.com/1125evpncatnix-211126182730/85/Ethernet-VPN-EVPN-EVerything-Provider-Needs-12-320.jpg)