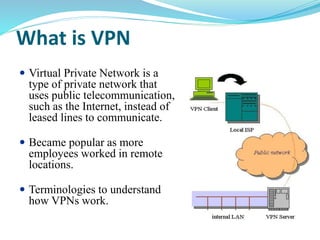
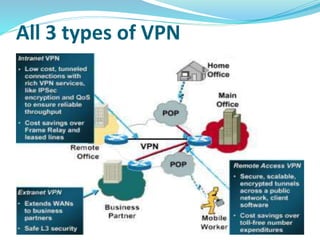
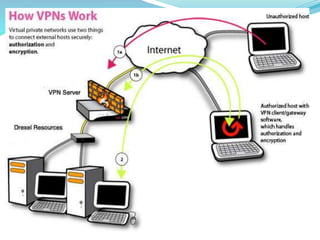
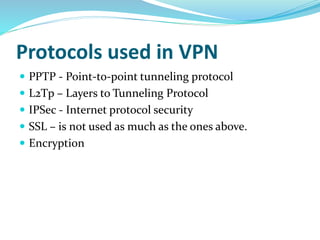
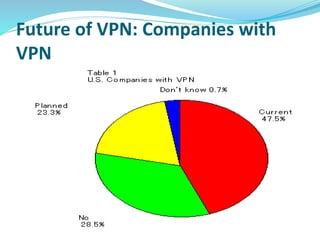
The document provides an overview of Virtual Private Networks (VPNs), including their definition, types, functionalities, and security mechanisms. It discusses remote-access and site-to-site VPNs, their advantages and disadvantages, along with the future of VPN usage in corporate environments. Ultimately, it concludes that VPNs offer a secure and cost-effective option for corporate networking.