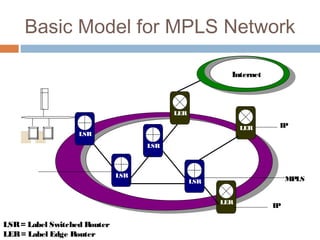
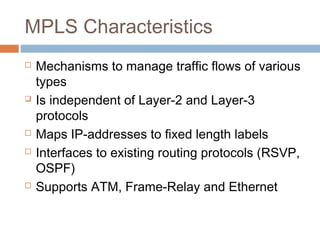
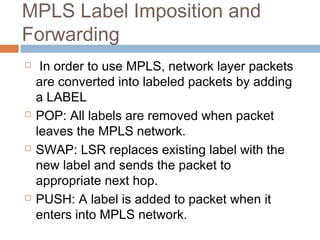
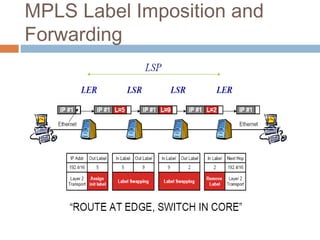
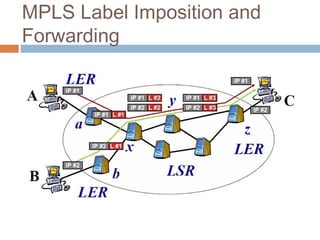
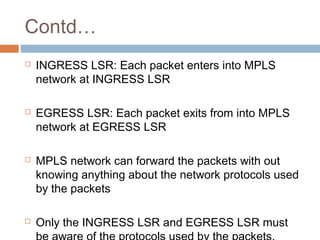
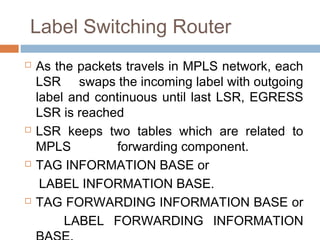
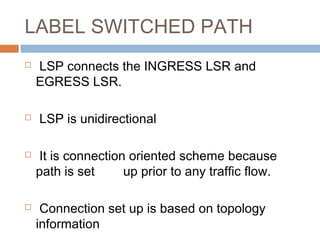
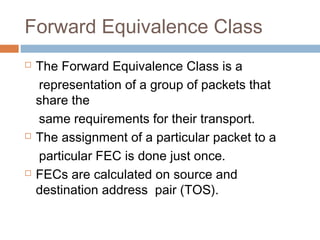
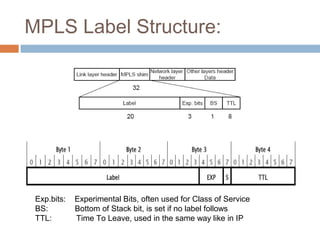
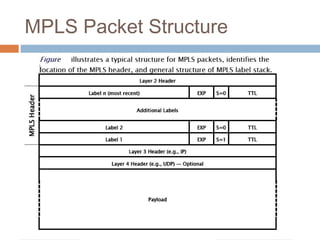
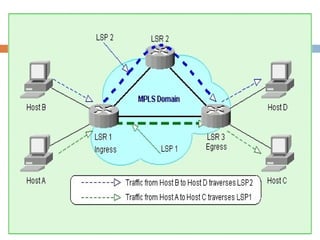
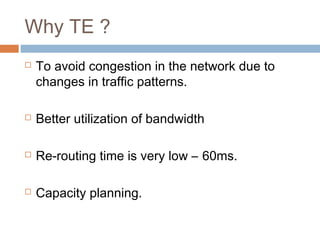
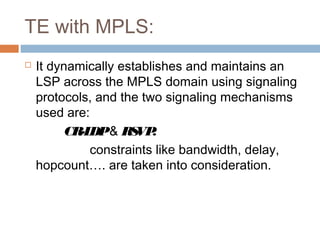
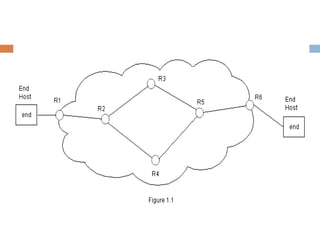
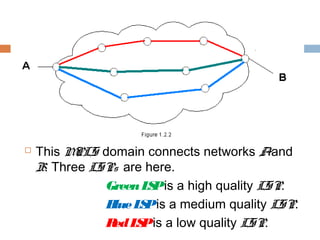
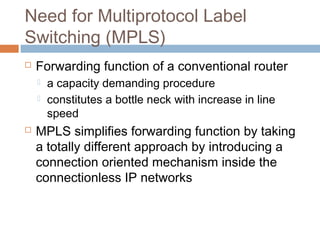
MPLS (Multi-Protocol Label Switching) simplifies packet forwarding by assigning labels to packets and using these labels for forwarding instead of long network addresses. It allows for traffic engineering and quality of service by establishing Label Switched Paths (LSPs) to direct different types of traffic over specific paths. MPLS supports various Layer 2 and Layer 3 protocols and improves network performance and scalability compared to traditional IP routing. It is widely used to implement virtual private networks (VPNs) across shared infrastructures.

![MPLS Basics
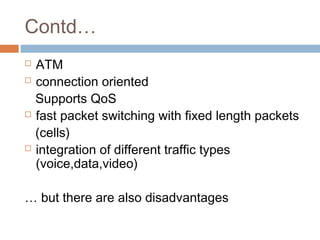
A Label Switched Path (LSP) is set up for each
route
A LSP for a particular packet P is a sequence of
routers,
<R1,R2………..Rn>
for all i, 1< i < n: Ri transmits P to R[i+1] by means
of a label
Edge routers
analyze the IP header to decide which LSP to use
add a corresponding local Label Switched Path
Identifier, in the form of a label
forward the packet to the next hop](https://image.slidesharecdn.com/mpls-151022082821-lva1-app6892/85/Mpls-8-320.jpg)