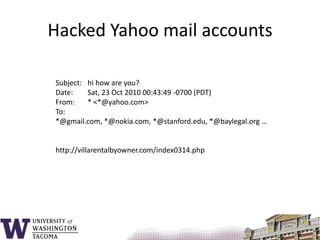
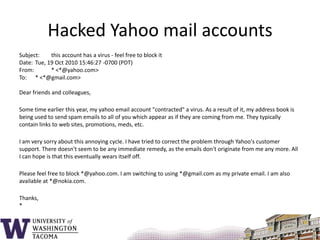
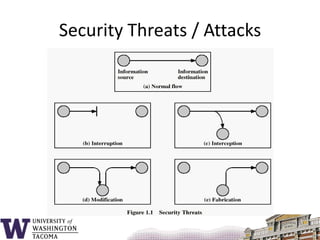
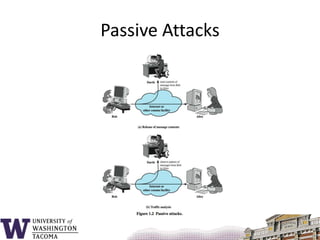
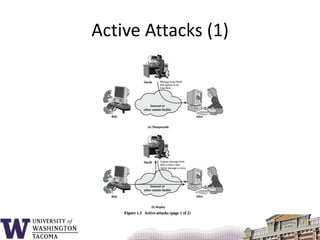
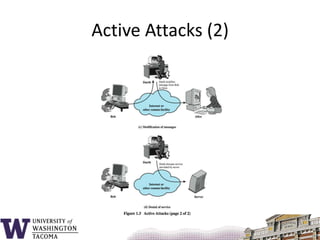
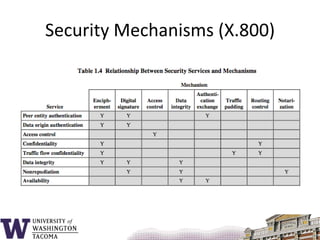
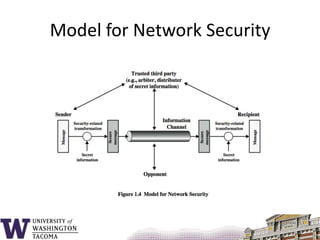
This document summarizes the key topics covered in a class on network security. It introduces common security concepts like authentication, access control, data confidentiality and integrity. It also discusses common security threats like passive attacks, active attacks, and security services defined by the ITU-T standard X.800. The document provides examples of security mechanisms and an outline of the topics to be covered, including a whirlwind tour of computer networks and an anatomy of an attack in five phases.