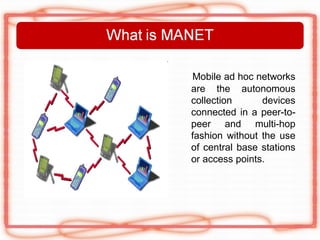
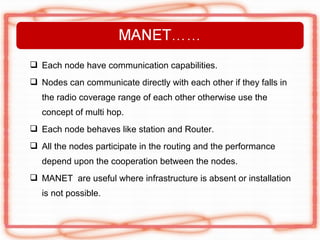
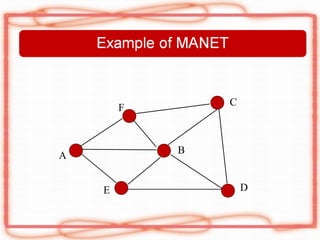
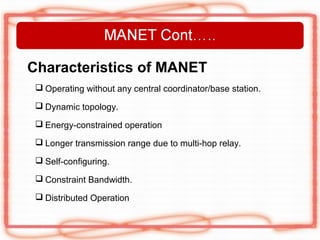
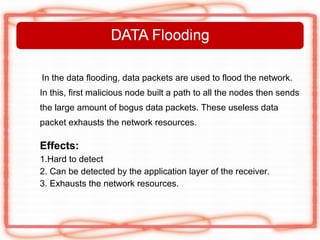
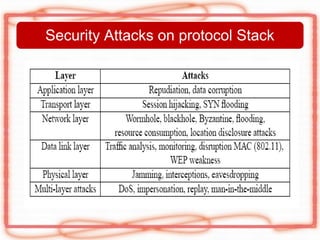
This document discusses security issues and attacks in mobile ad hoc networks (MANETs). It provides an introduction to MANETs and their characteristics. It outlines the general objectives of analyzing flooding attacks on MANETs and preventing such attacks for networks with high node mobility. It describes common attacks on MANETs such as flooding attacks, blackhole attacks, wormhole attacks, and Byzantine attacks. The document also discusses security mechanisms for MANETs including preventive cryptography-based approaches and reactive intrusion detection system approaches. It stresses the need for comprehensive security solutions to deal with the diverse attacks that are facilitated by the open and dynamic nature of MANETs.


















![[1] Manel Guerrero Zapata & N. Asokan “Securing Ad Hoc Routing Protocols” Wise’02 September
28,2002,Atlanta Georgia, USA inedxed in ACM 1-58113-585-8/02/009
[2] Nishu Garg, R.P.Mahapatra. “MANET Security Issues”. IJCSNS International Journal of Computer
Science and Network Security, Volume.9, No.8, 2009.
[3]Mouhcine Guennoun and Khalil El-khatib “A scalable wireless intrusion detection system”,IJCSIS,
Vol 1,No. 1, may 2009.
[4] Abhay Kumar Rai, Rajiv Ranjan Tewari & Saurabh Kant Upadhyay “Different Types of Attacks
on Integrated MANET-Internet Communication” International Journal of Computer Science
and Security (IJCSS) Volume (4): Issue (3)
[5] Malcolm Parsons and Peter Ebinger “Performance Evaluation of the Impact of Attacks on Mobile
Ad hoc Networks”.
[6] H Deng, W. Li, and D. Agrawal, Routing Security in Wireless Ad Hoc Networks.IEEE
Communications Magazine. Vol. 40, No. 10, 2002
[7]Y. Zhang and W. Lee, “Intrusion Detection in Wireless Ad hoc Networks”, In Proc. ACM/IEEE Int’l.
Conf. on Mobile Computing and Networking, pp 275-283, 2000.
[8]Satria Mandala, Md. Asri Ngadi, A.Hanan Abdullah “A Survey on MANET Intrusion Detection”
International Journal of Computer Science and Security, Volume (2) : Issue (1)](https://image.slidesharecdn.com/indirappt-130103031430-phpapp02/85/Attacks-in-MANET-29-320.jpg)
![[9] N.SHANTHI, 2DR.LGANESAN AND 3DR.K.RAMAR” STUDY OF DIFFERENT ATTACKS ON
MULTICAST MOBILE AD HOC NETWORK” Journal of Theoretical and Applied Information
Technology.
[10]Hassen Redwan and Ki-Hyung Kim s “Survey of Security Requirements, Attacks and Network
Integration in Wireless Mesh Networks” 2008 Japan-China Joint Workshop on Frontier of
Computer Science and Technology.
[11]Marianne A. Azer,Sherif M. El-Kassas,Magdy S. El-Soudani “Security in Ad Hoc Networks,From
Vulnerability to Risk Management”2009 Third International Conference on Emerging Security
Information, Systems and Technologies
[12] Marjan Kuchaki Rafsanjani, Ali Movaghar, and Faroukh Koroupi “Investigating Intrusion Detection
Systems in
MANET and Comparing IDSs for Detecting Misbehaving Nodes” World Academy of Science,
Engineering and
Technology, 44, 2008.
[13] Pradip M. Jawandhiya et. Al “A Survey of Mobile Ad Hoc Network Attacks” International
Journal of Engineering Science and Technology Vol. 2(9), 2010, 4063-4071
[14] Adam Burg “ Ad hoc network specific attacks”Seminar Ad hoc networking: concepts,
applications, and security Technische Universität München, 2003
[15] Pradeep rai and Shubha singh “A Review of ‘MANET’s Security Aspects and
Challenges”IJCA Special Issue on “Mobile Ad-hoc Networks”MANETs, 2010 of Information
Technology & Knowledge Management ,Jul – Dec 2010,Vol-II, No2 PP 305-310](https://image.slidesharecdn.com/indirappt-130103031430-phpapp02/85/Attacks-in-MANET-30-320.jpg)
