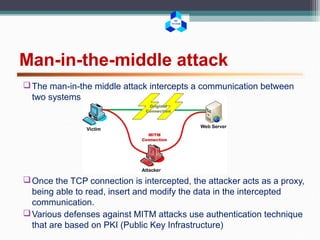
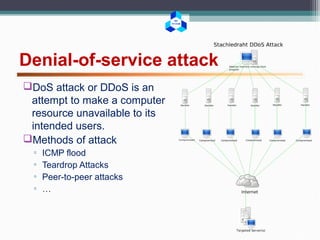
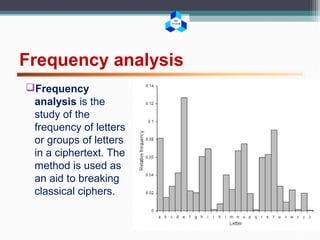
This document outlines various cryptographic and network attacks including frequency analysis, brute force attacks, meet-in-the-middle attacks, birthday attacks, replay attacks, man-in-the-middle attacks, and denial-of-service attacks. It provides details on how each attack works and potential defenses against attacks like using authentication, random session tokens, and timestamping.





![BK
TP.HCM
Birthday attack (1/6)
exploits the mathematics behind the birthday problem in
probability theory.
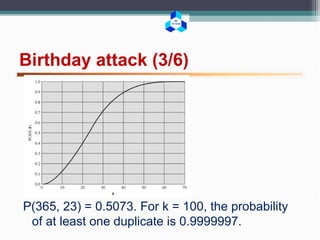
What is the minimum value of k such that the probability
is greater than 0.5 that at least two people in a group of
k people have the same birthday?
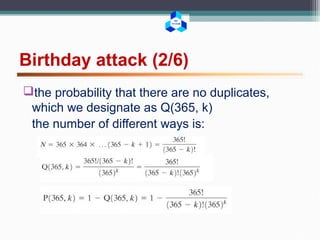
P(n, k) = Pr[at least one duplicate in k items, with each
item able to take on one of n equally likely values
between 1 and n]
we are looking for the smallest value of k such that
P(365, k) 0.5](https://image.slidesharecdn.com/networksecurityattacks-160504174432/85/Network-security-attacks-7-320.jpg)