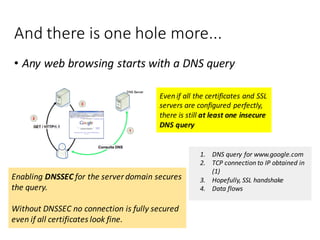
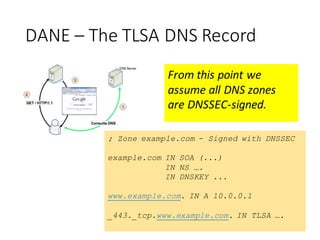
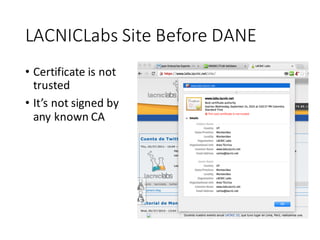
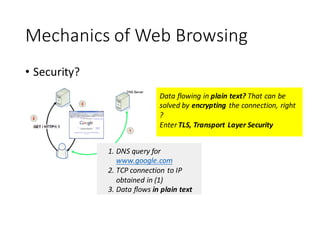
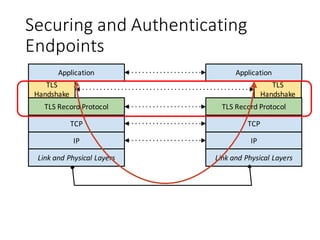
The document provides an introduction to the mechanics of web browsing security, emphasizing the importance of TLS for encrypting data and the role of digital certificates in establishing trust. It discusses the shortcomings of the traditional Certificate Authority (CA) model and presents DANE (DNS-Based Authentication of Named Entities) as a solution for securely publishing digital certificates in DNS. The tutorial outlines the steps for implementing DANE and highlights the potential advantages and current limitations of this approach in web security.

![TLS
Handshake
ClientHello
ServerHello
ServerCertificate
ServerKeyExchange
ServerHelloDone
[ClientCertificate]
ClientKeyExchange
ChangeCipherSpec
ChangeCipherSpec
Client Server](https://image.slidesharecdn.com/dane-intro-lacnog-bogota-v4slideshare-151012182212-lva1-app6892/85/An-Introduction-to-DANE-Securing-TLS-using-DNSSEC-4-320.jpg)

![Digital
Certificates
(2)
• Fields
and
flags
in
a
certificate
define
how,
where
and
when
the
certificate
can
be
used
and
define
is
valid
to
be
used
• Valid-‐from,
Valid-‐until
times
• Express
constraints
on
usage
• Extensions
• Lists
of
[type-‐value-‐critical_flag]
• Examples
• Key
usage
• Extended
key
usage
(clientAuth,
serverAuth,
emailProtection,
...
)
• RFC
3779
(Internet
number
resources)](https://image.slidesharecdn.com/dane-intro-lacnog-bogota-v4slideshare-151012182212-lva1-app6892/85/An-Introduction-to-DANE-Securing-TLS-using-DNSSEC-6-320.jpg)
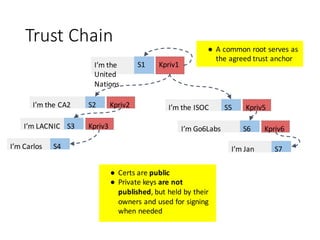
![Drawbacks
of
the
CA-‐Based
Chain
• Trust
anchors
can
(and
have
been)
successfully
attacked
• DigiNotar,
GlobalSign,
DigiCert Malaysia
are
just
some
examples
• The
process
that
CAs
use
to
validate
information
provided
by
customers
can
be
subverted
• CAs
are
slow
to
react
when
a
certificate
is
compromised
• The
revocation
process
can
be
slow
and
is
based
on
the
concept
of
CRLs
that
have
to
be
downloaded
and
are
re-‐
created
every
few
hours
• [Check
https://tools.ietf.org/html/draft-‐housley-‐web-‐pki-‐
problems-‐00 ]](https://image.slidesharecdn.com/dane-intro-lacnog-bogota-v4slideshare-151012182212-lva1-app6892/85/An-Introduction-to-DANE-Securing-TLS-using-DNSSEC-8-320.jpg)
![The
DigiNotar Debacle
• [https://www.enisa.europa.eu/media/news-‐
items/operation-‐black-‐tulip]](https://image.slidesharecdn.com/dane-intro-lacnog-bogota-v4slideshare-151012182212-lva1-app6892/85/An-Introduction-to-DANE-Securing-TLS-using-DNSSEC-9-320.jpg)