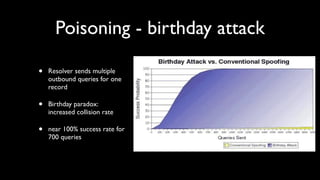
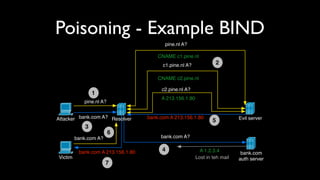
This document discusses DNS cache poisoning vulnerabilities, including:
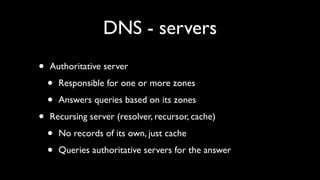
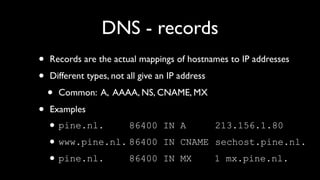
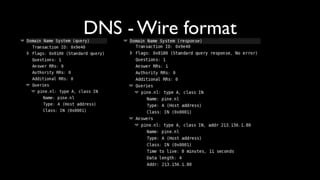
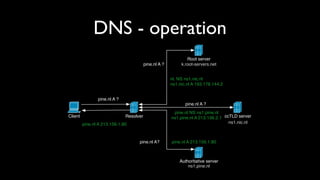
- Explanations of how cache poisoning works by entering non-authoritative records into a resolver's cache.
- A timeline of vulnerabilities discovered from 1993-2008 related to implementation issues that allowed cache poisoning.
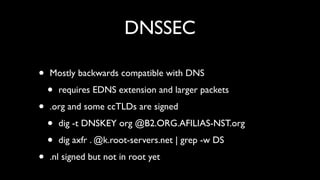
- Countermeasures like DNSSEC that add authentication and integrity to DNS to prevent cache poisoning attacks.