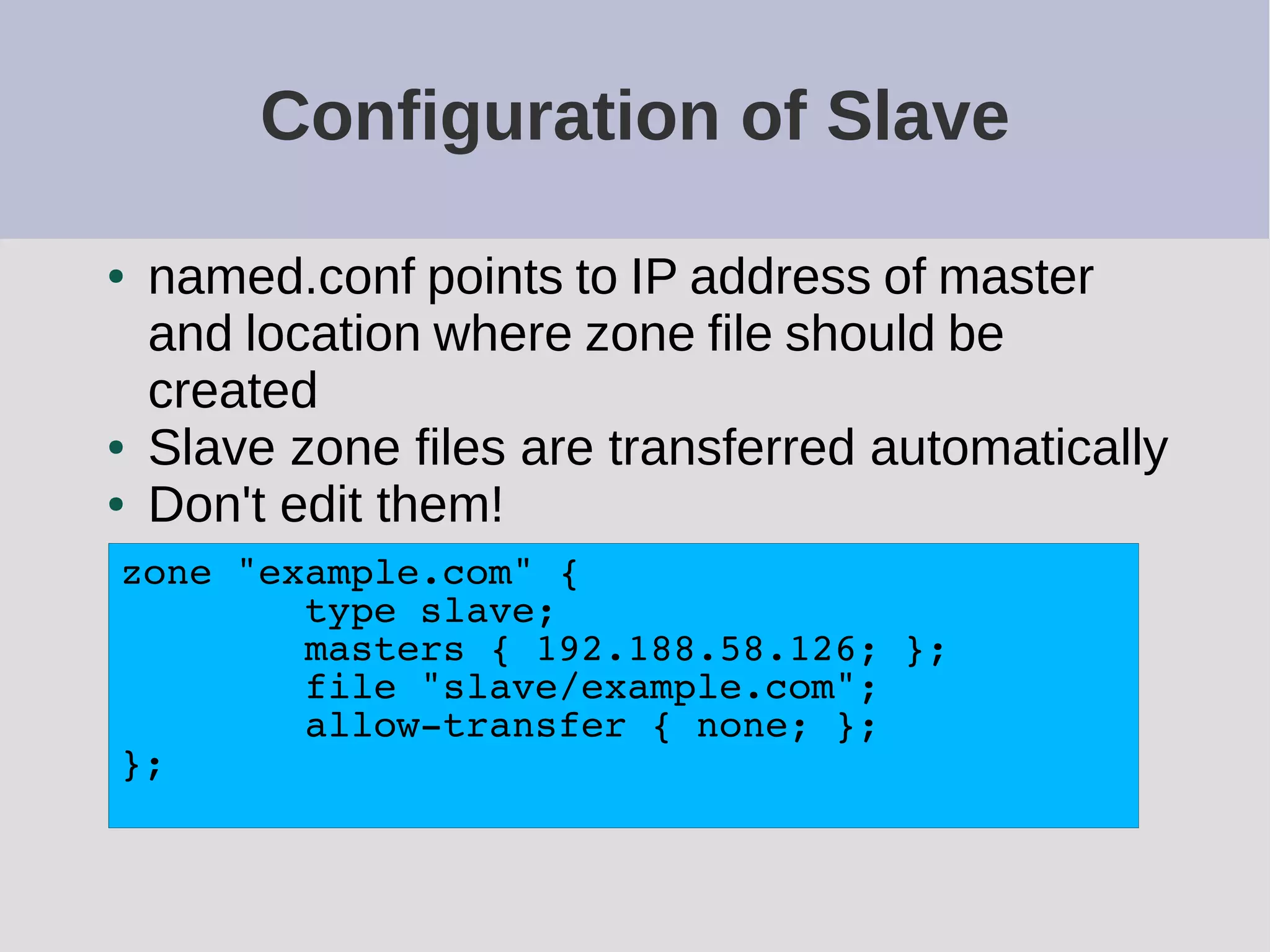
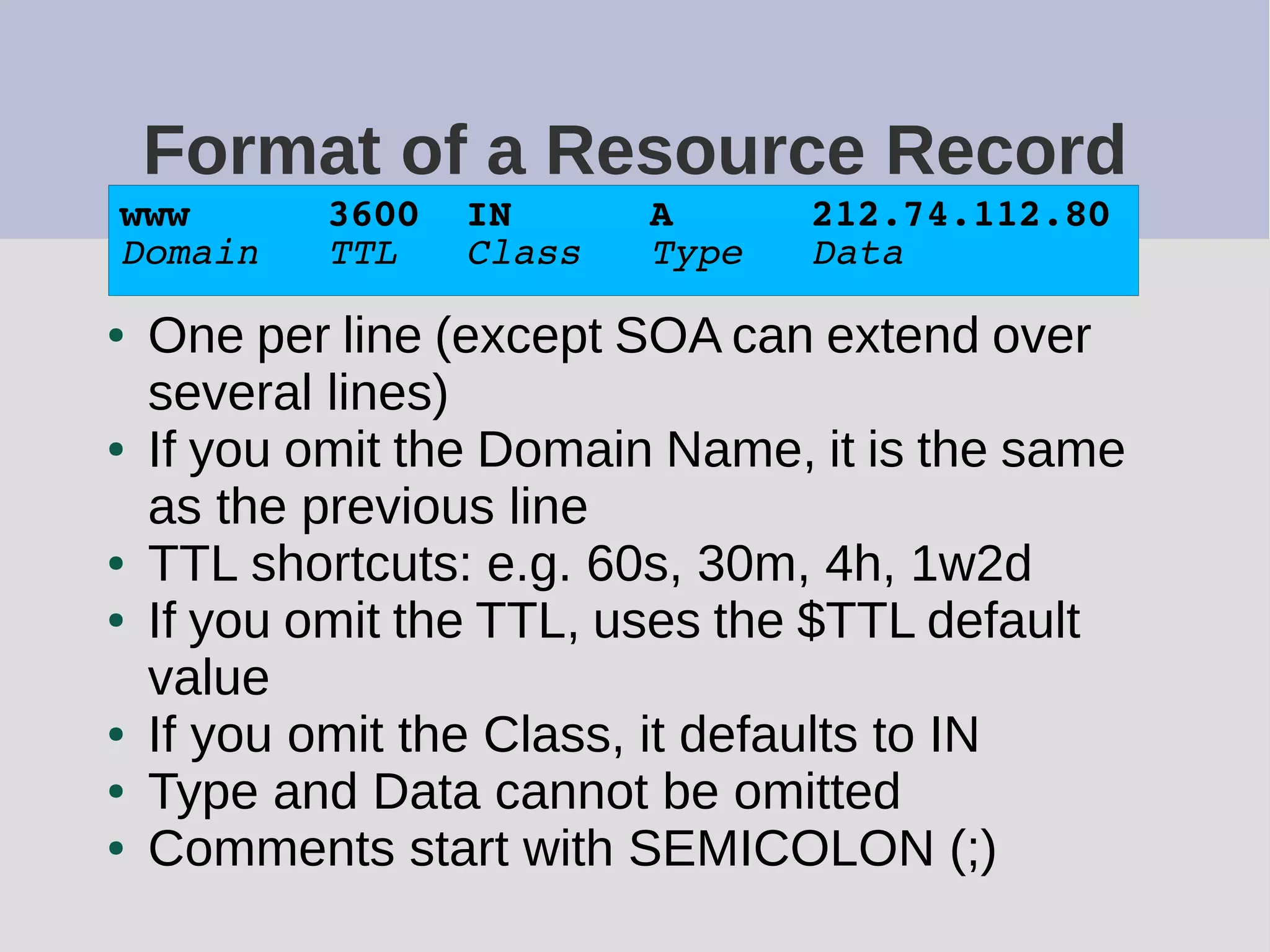
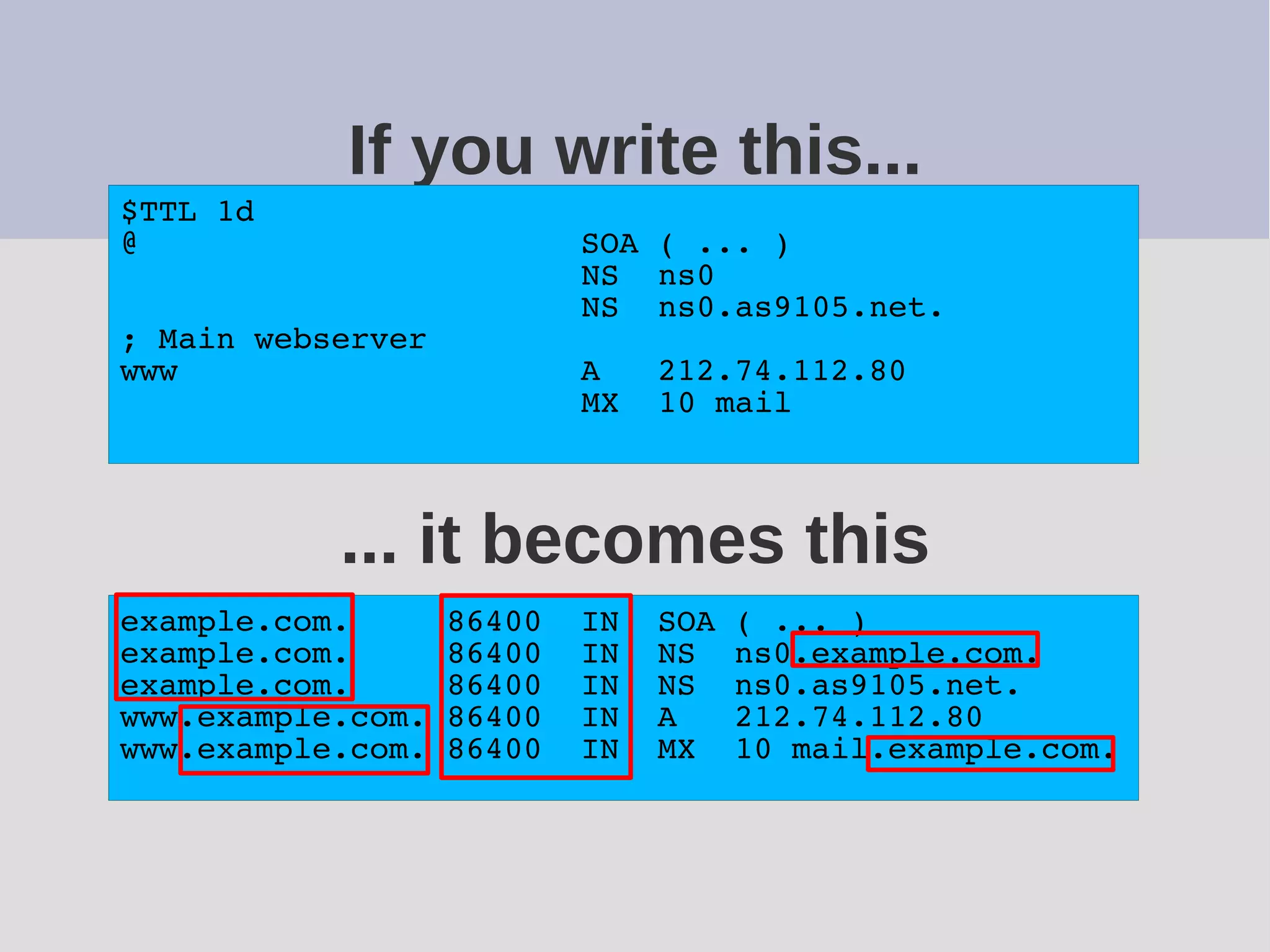
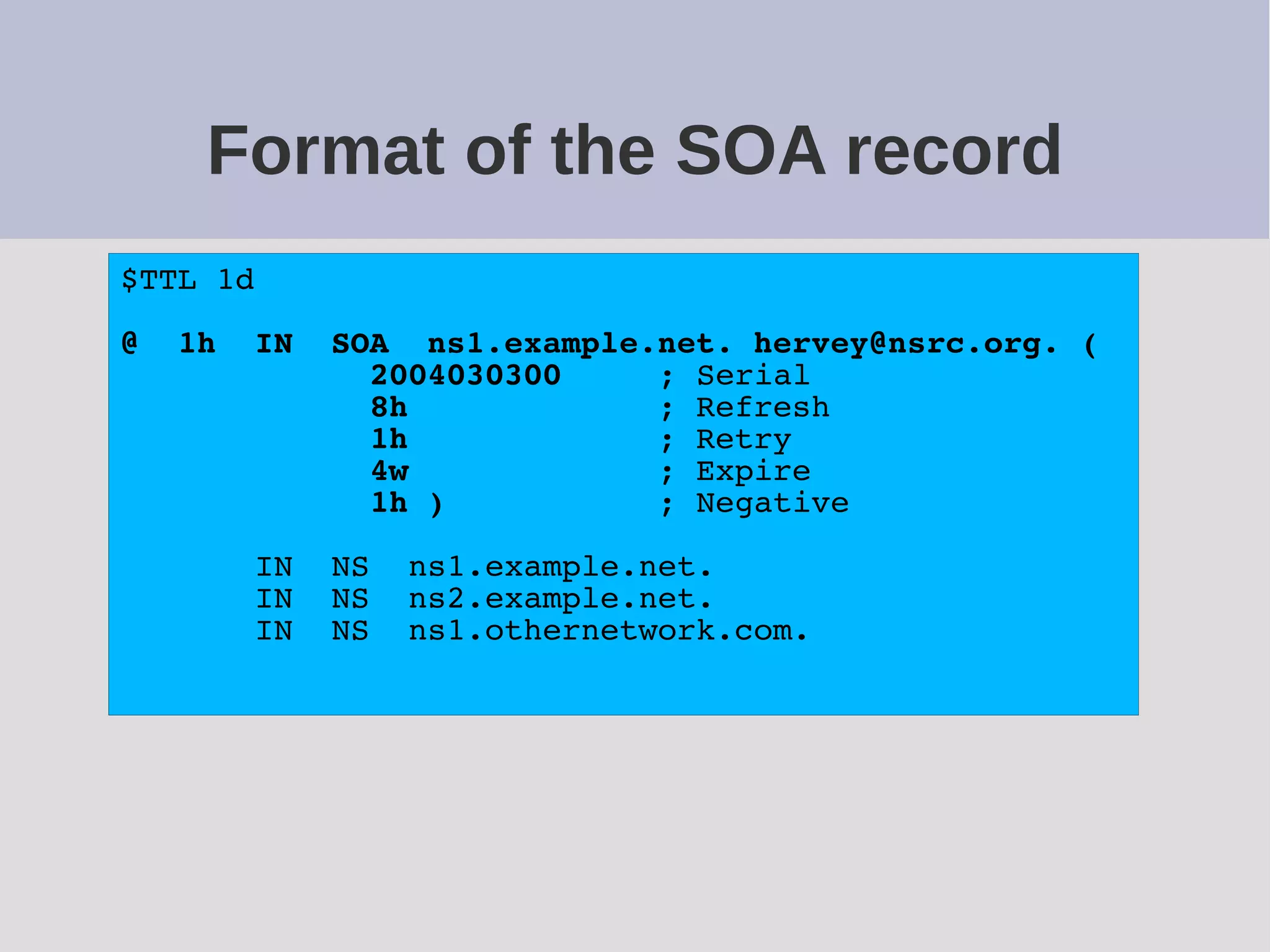
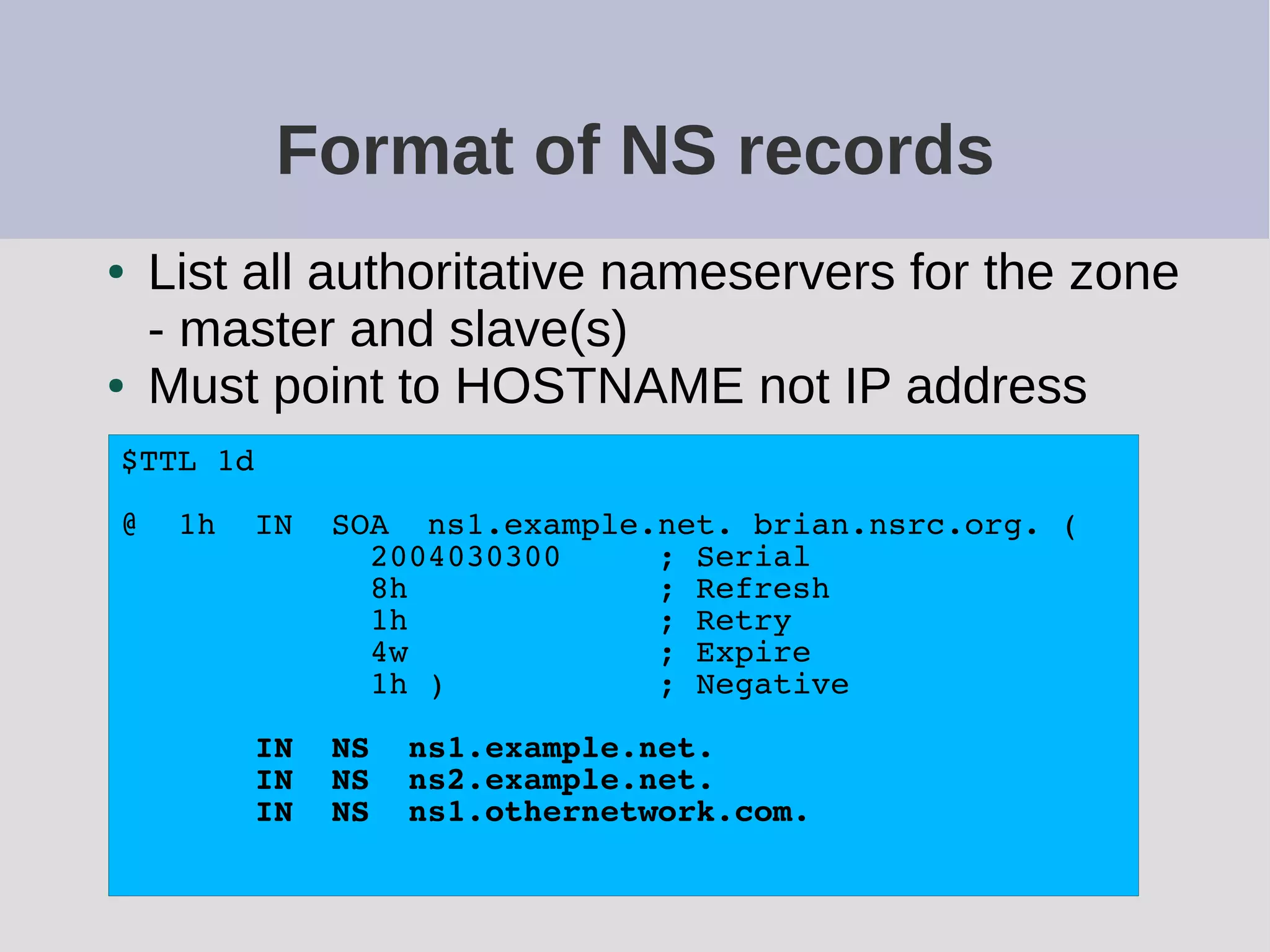
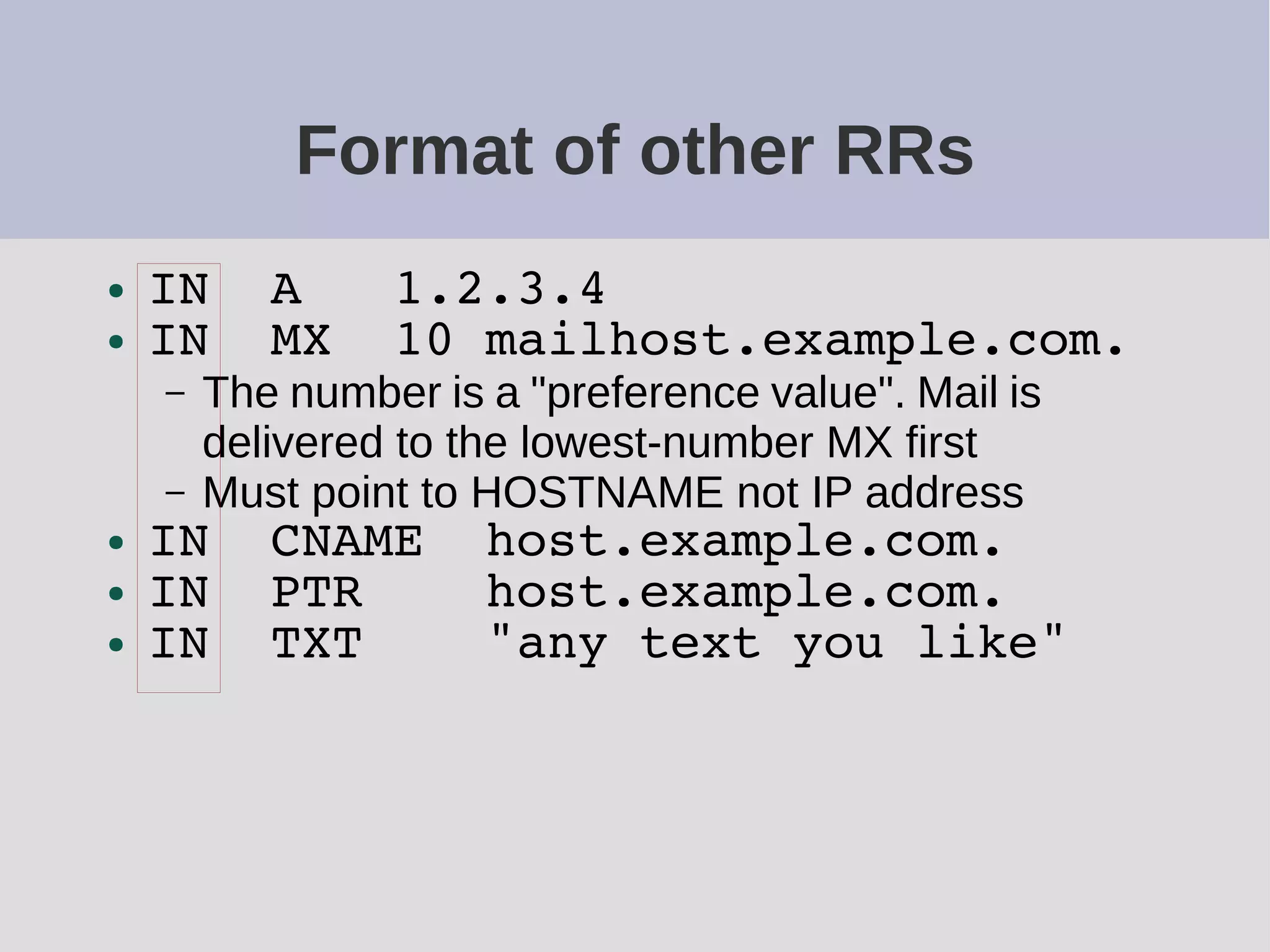
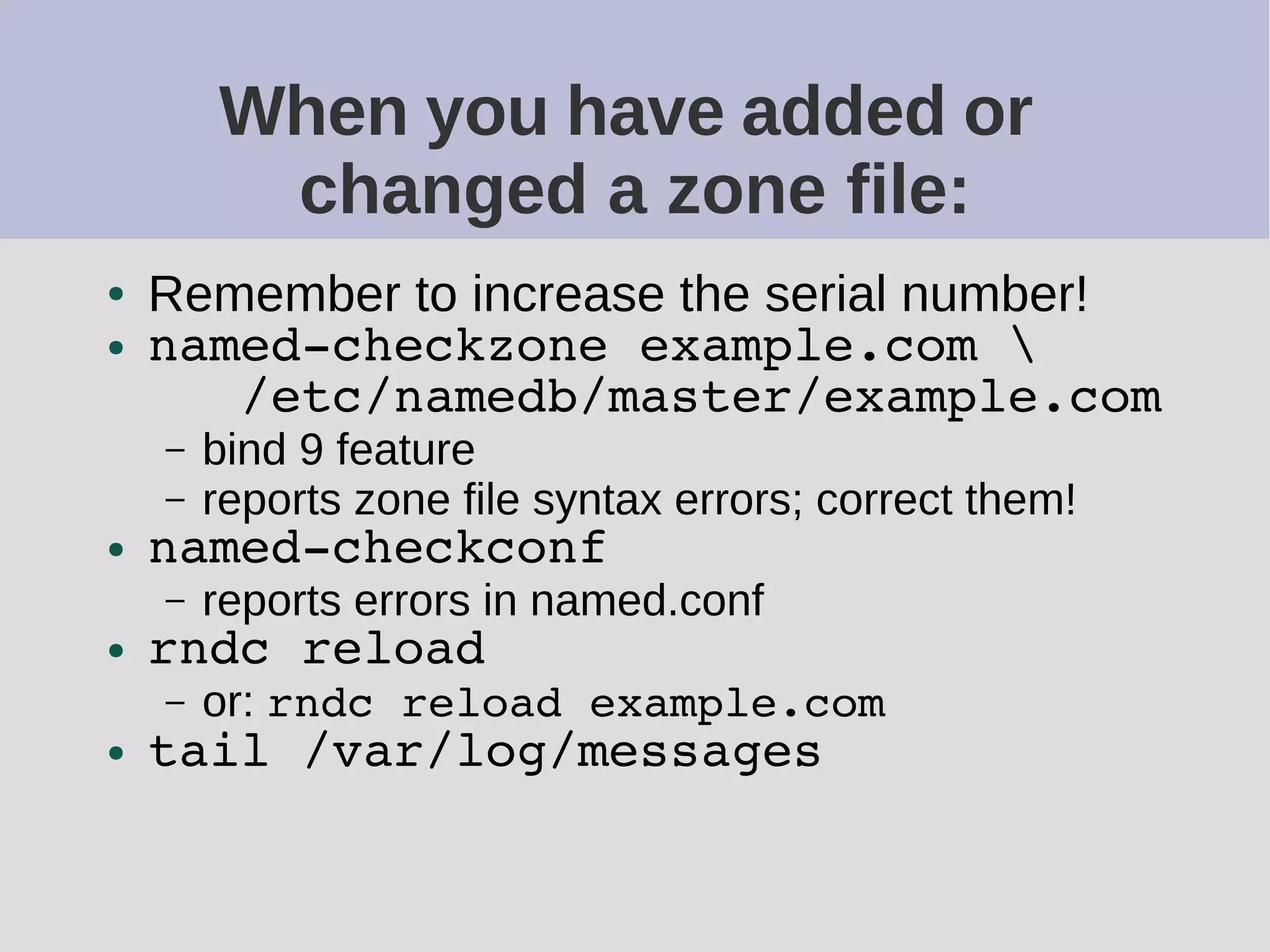
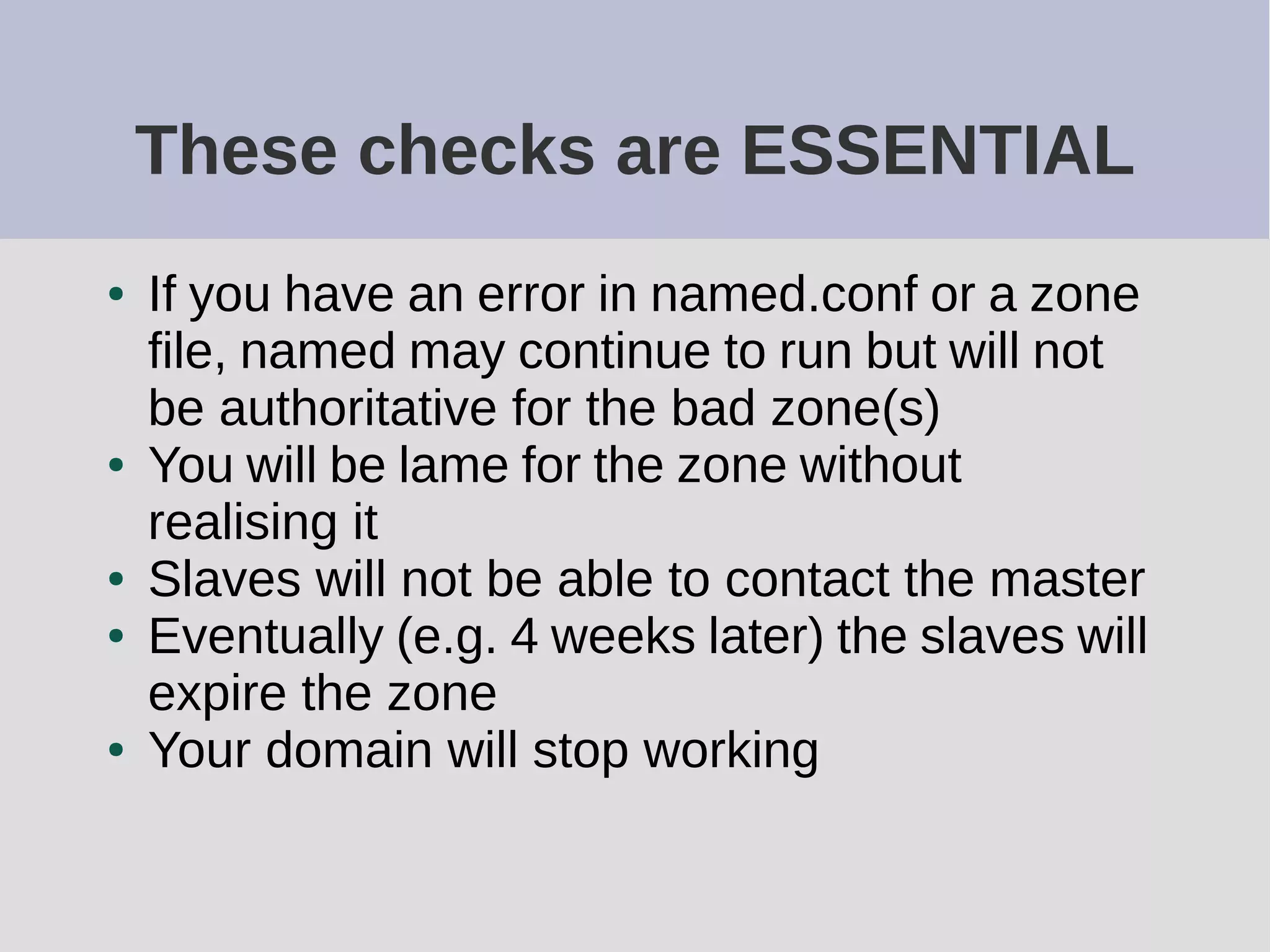
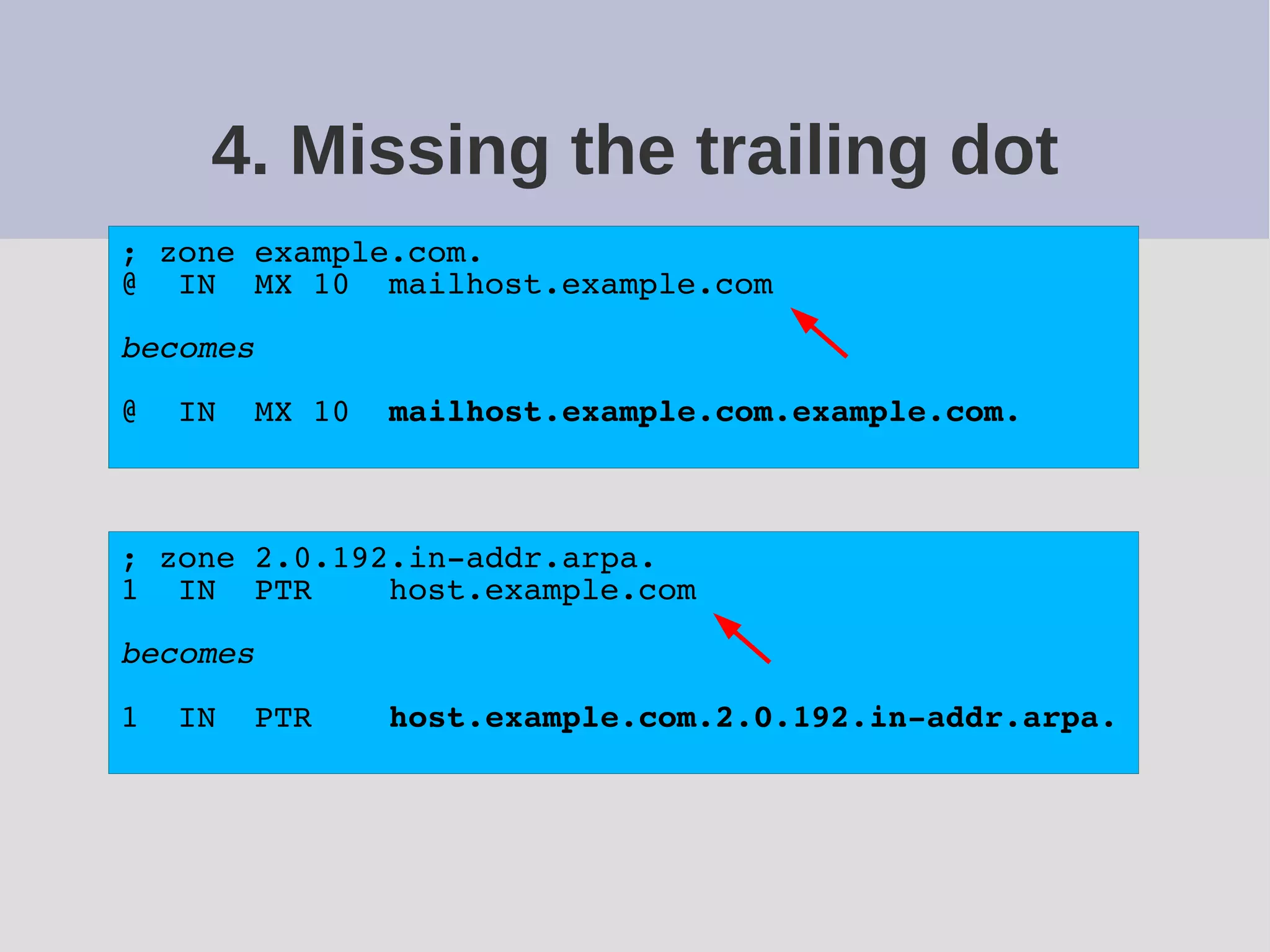
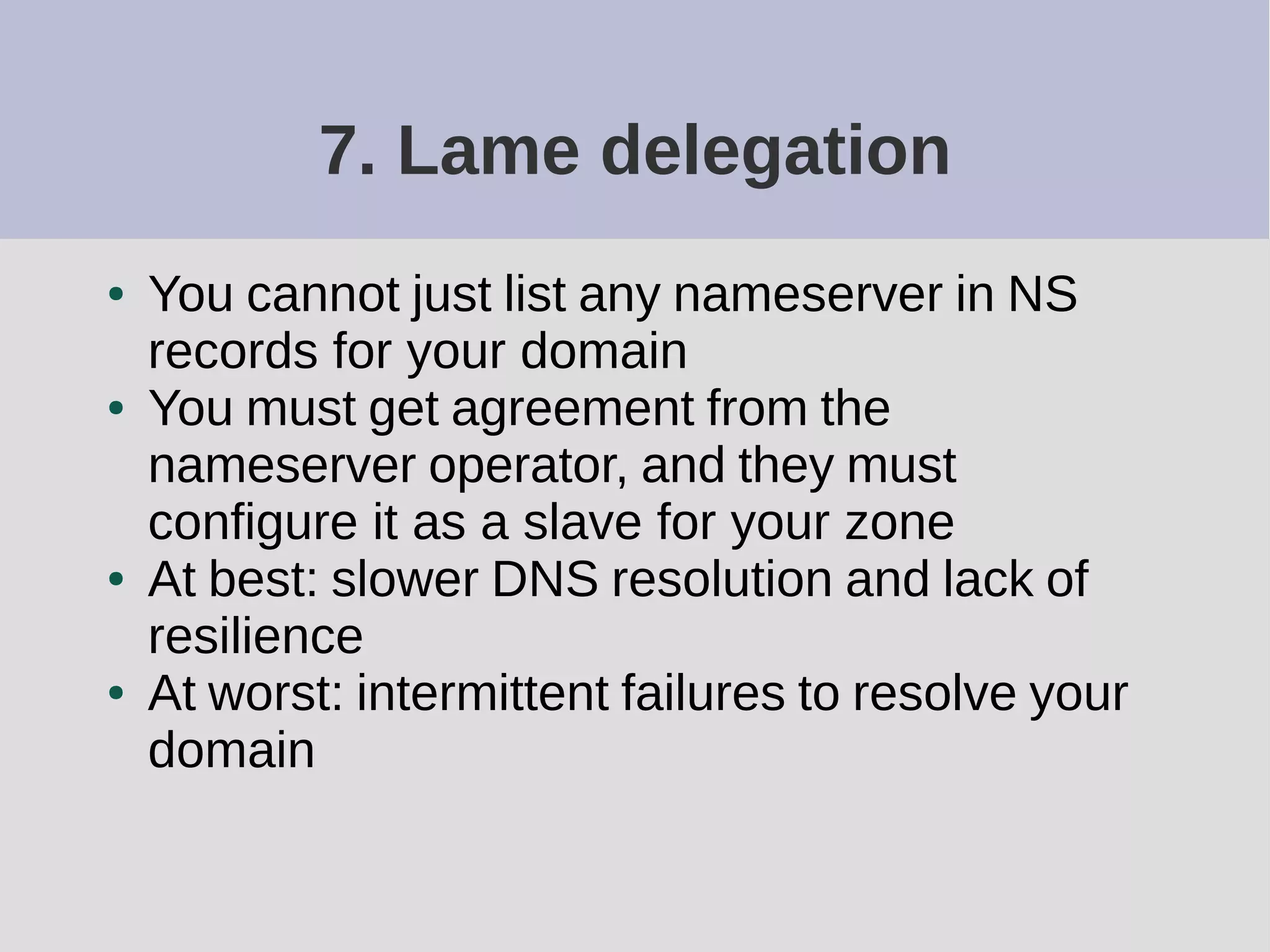
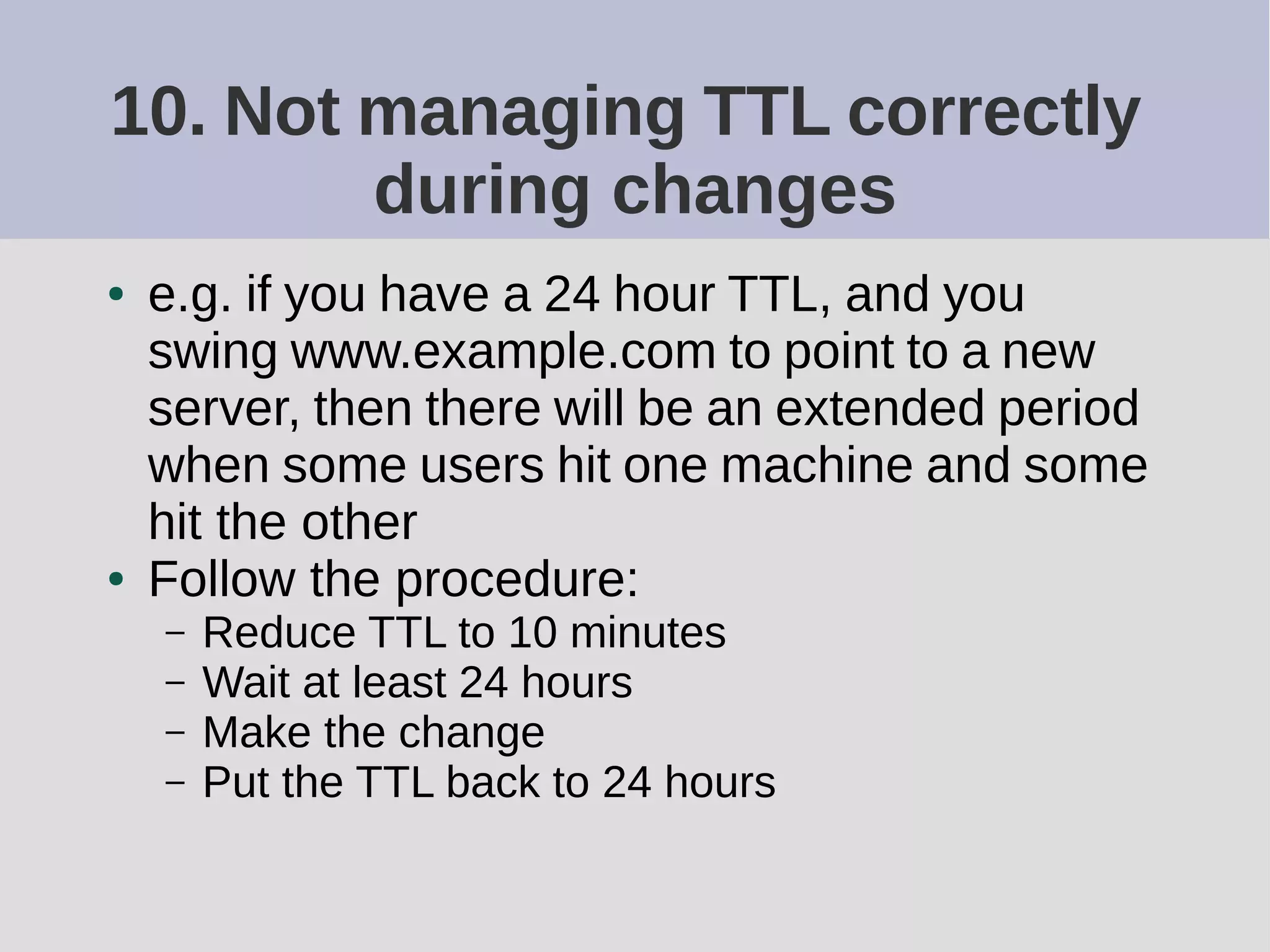
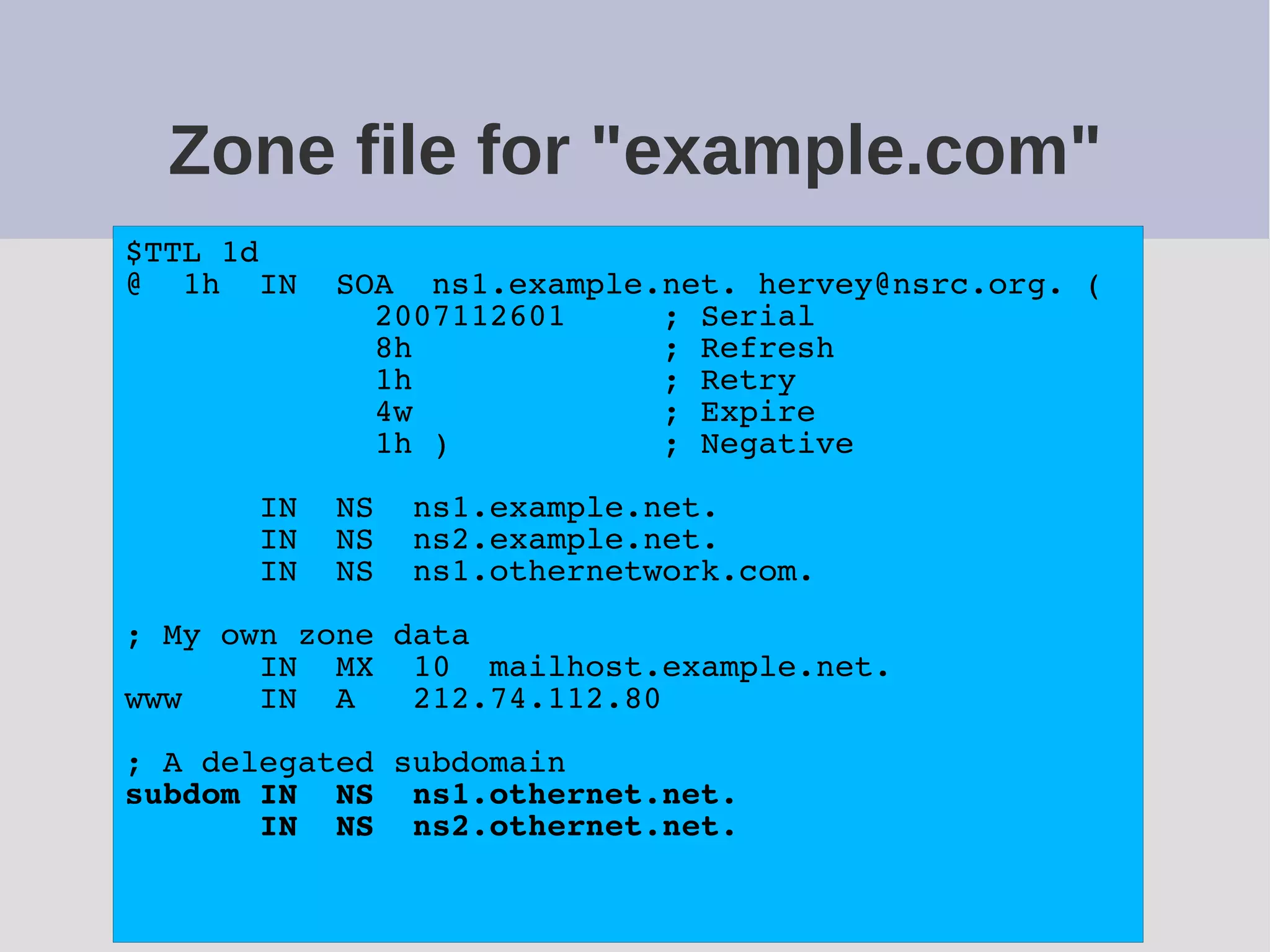
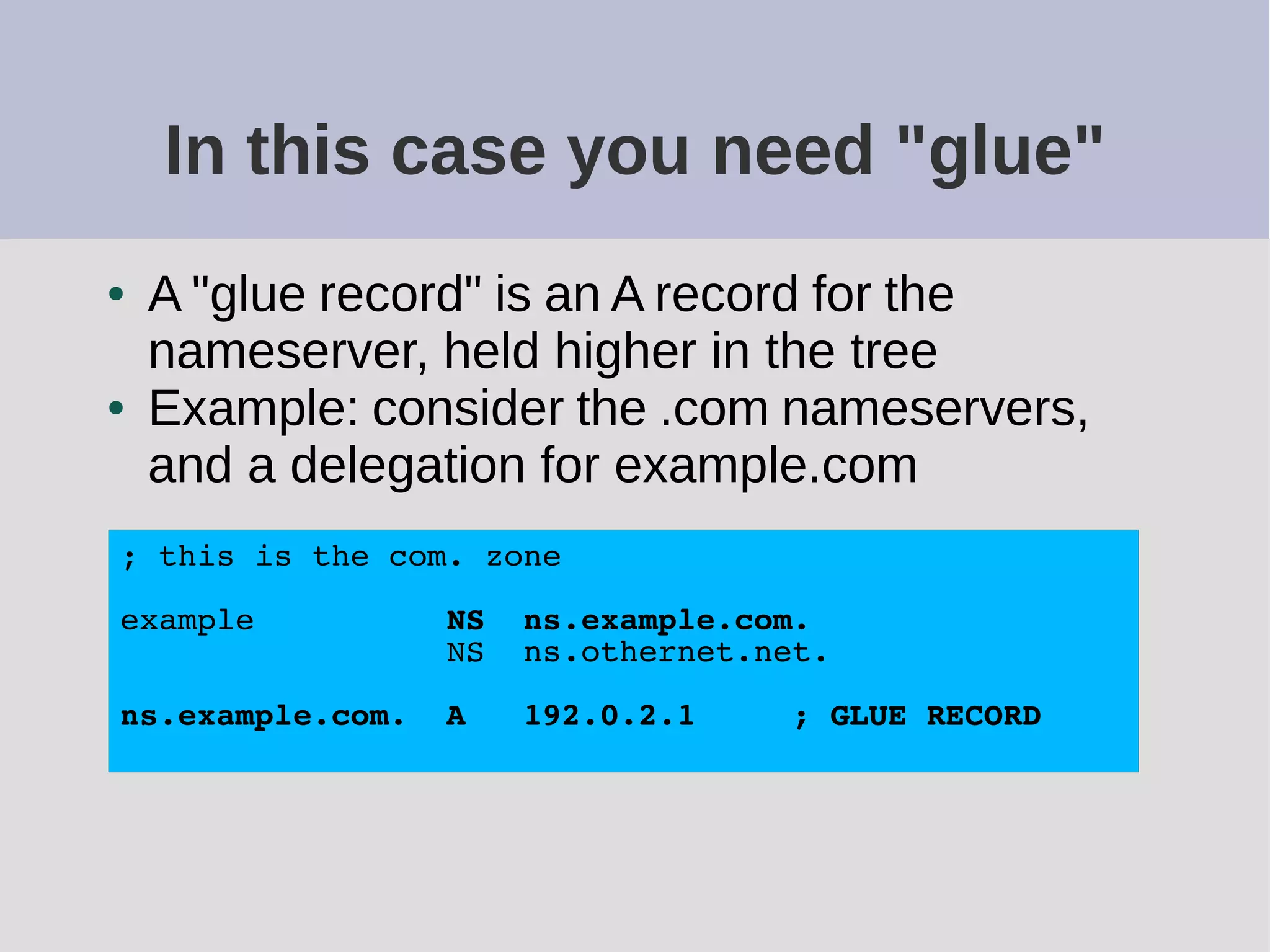
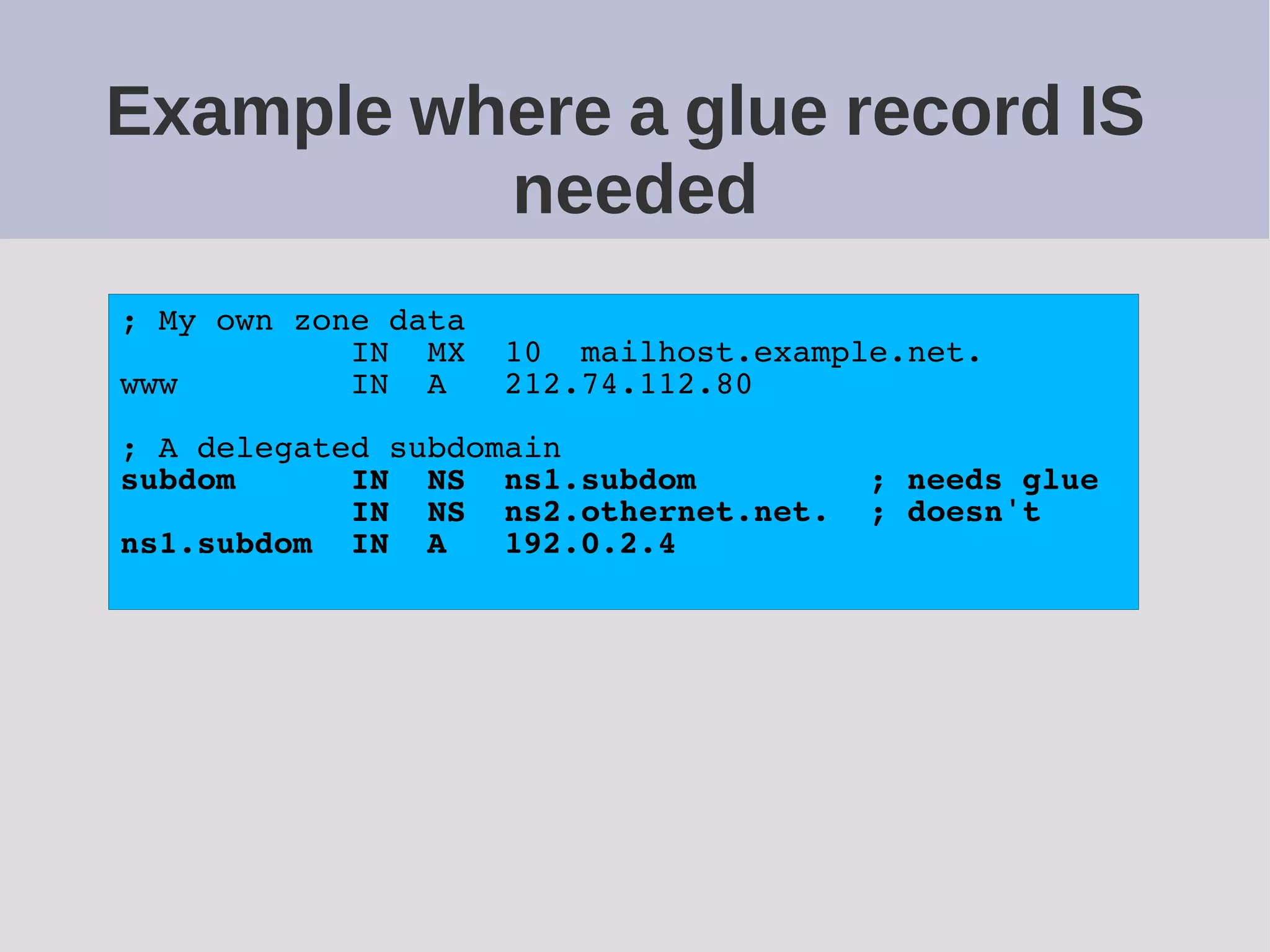
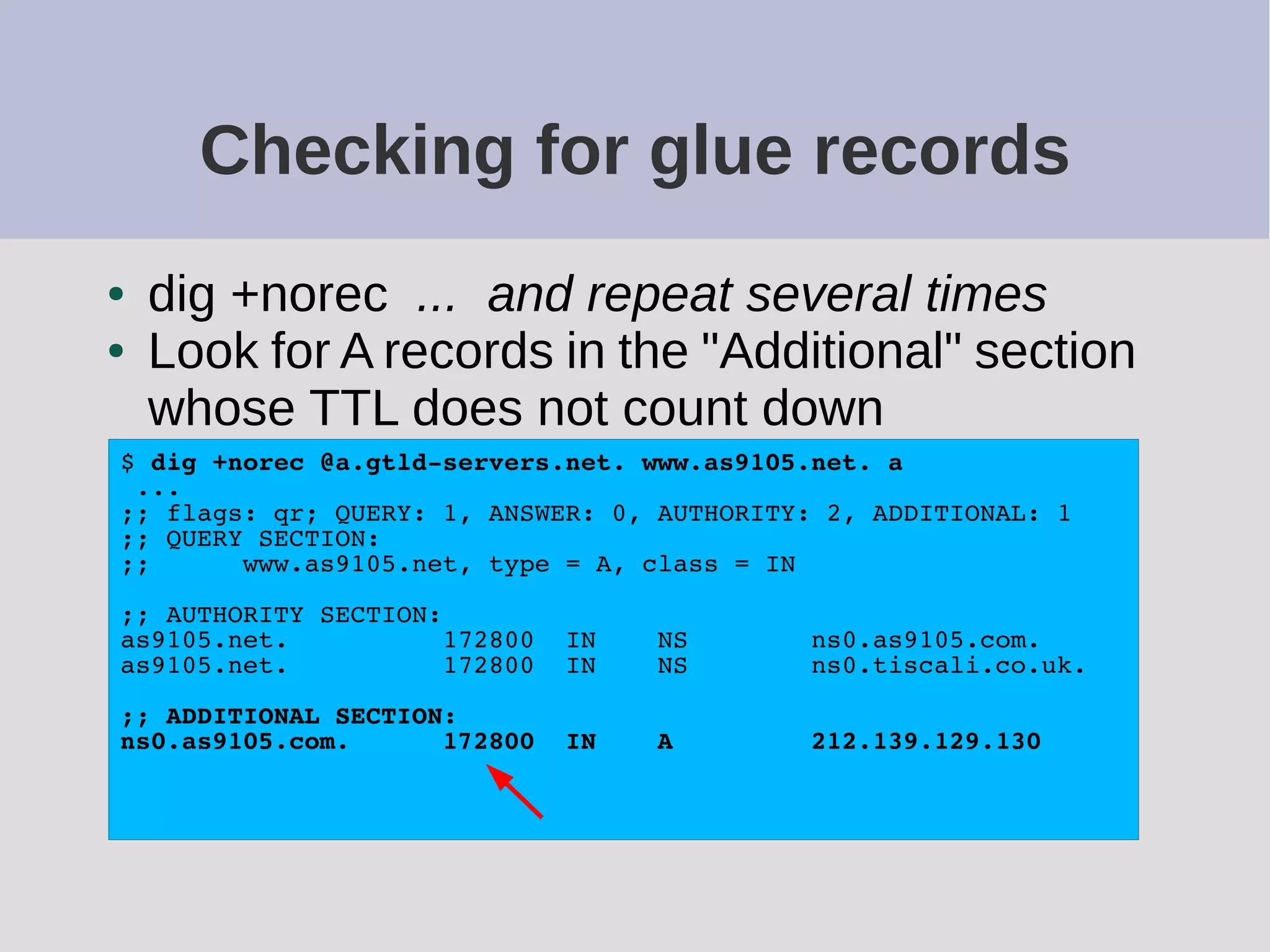
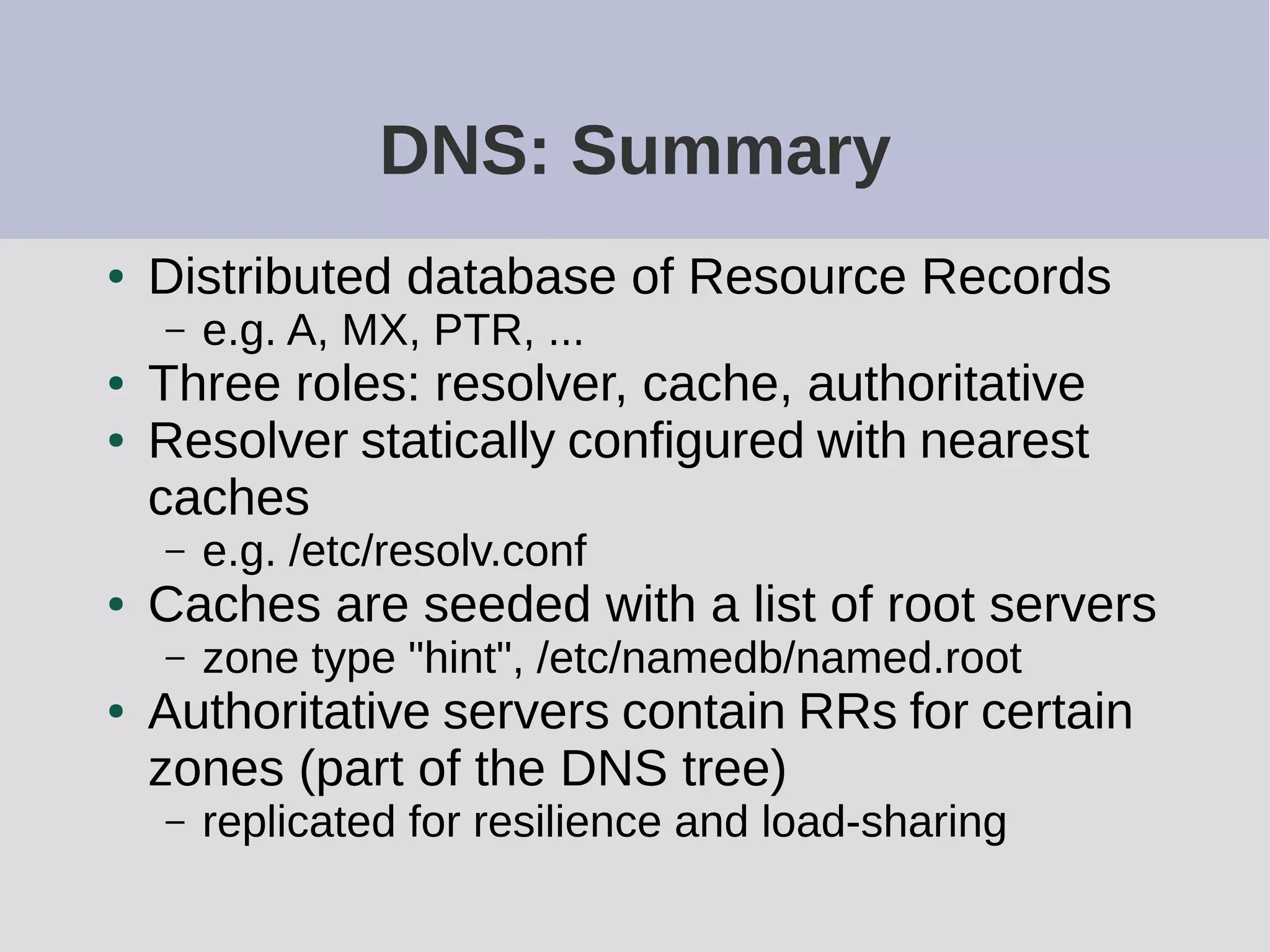
The document provides a comprehensive overview of DNS (Domain Name System) configuration and operation for authoritative nameservers, emphasizing the importance of proper serial number management, replication processes, and zone file structures. It outlines common errors encountered in DNS setup and offers practical guidance for configuring master and slave servers, including delegation of subdomains and handling glue records. Recommended practices and references to relevant RFCs ensure optimal performance and reliability of DNS services.