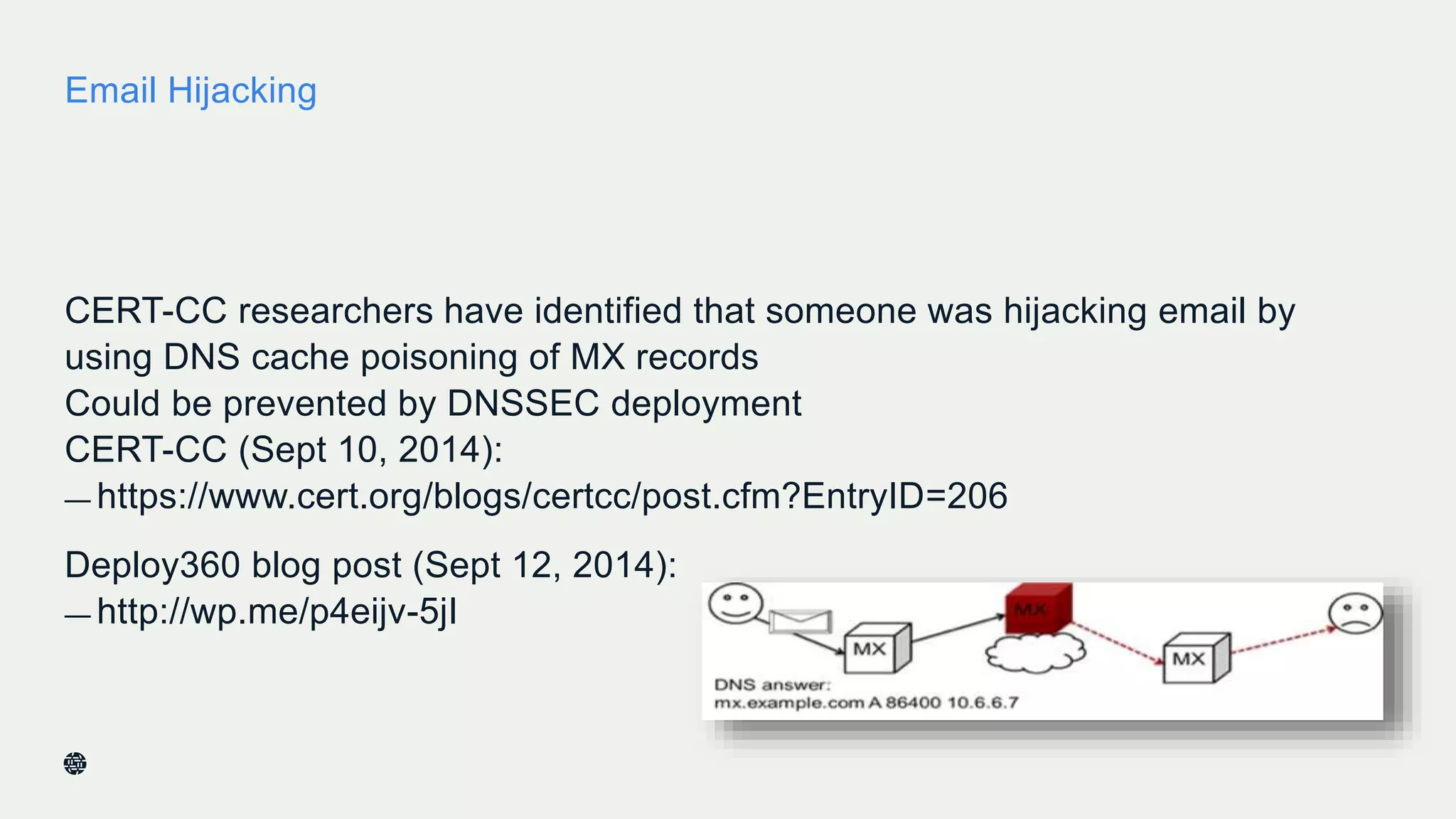
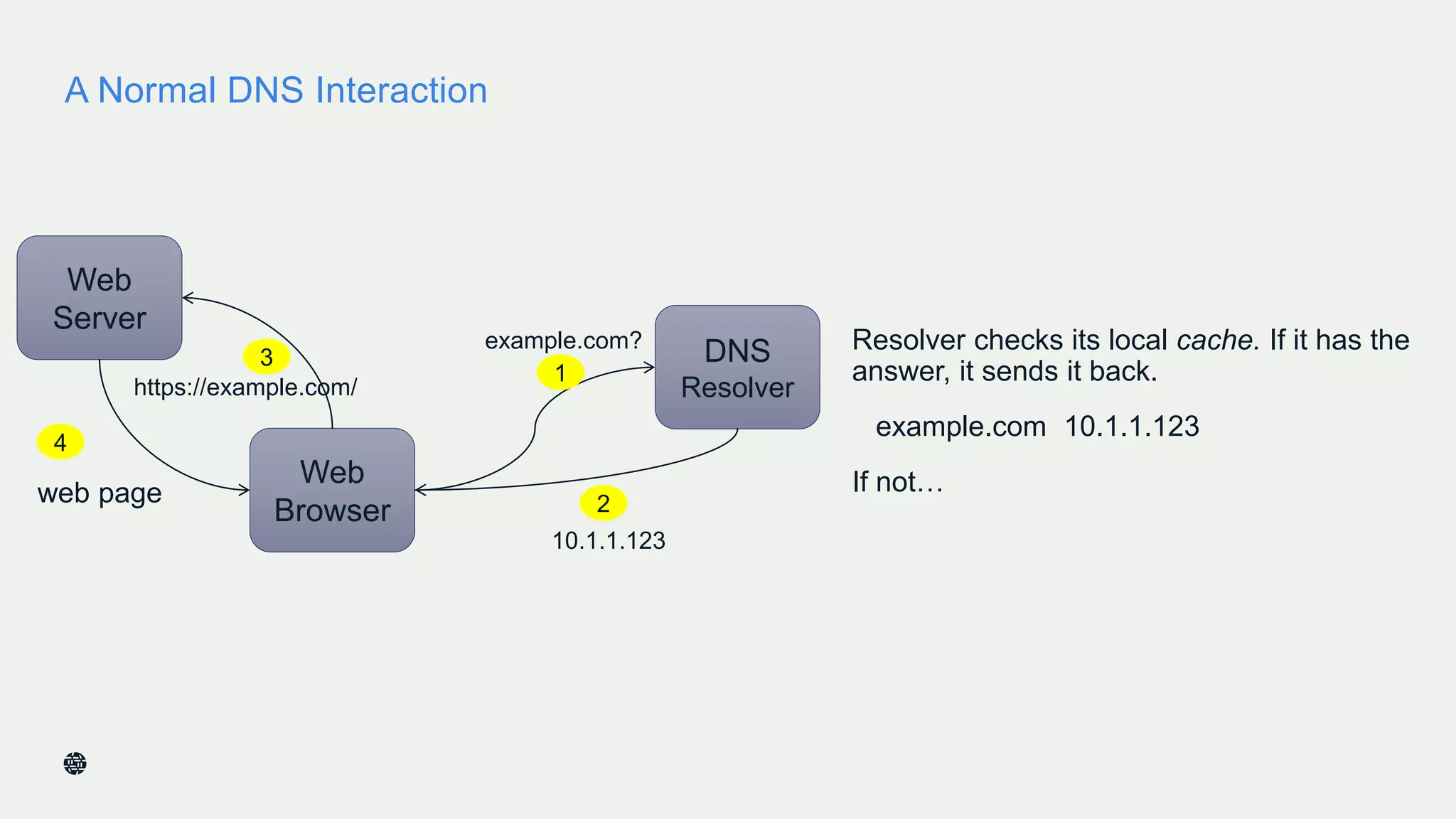
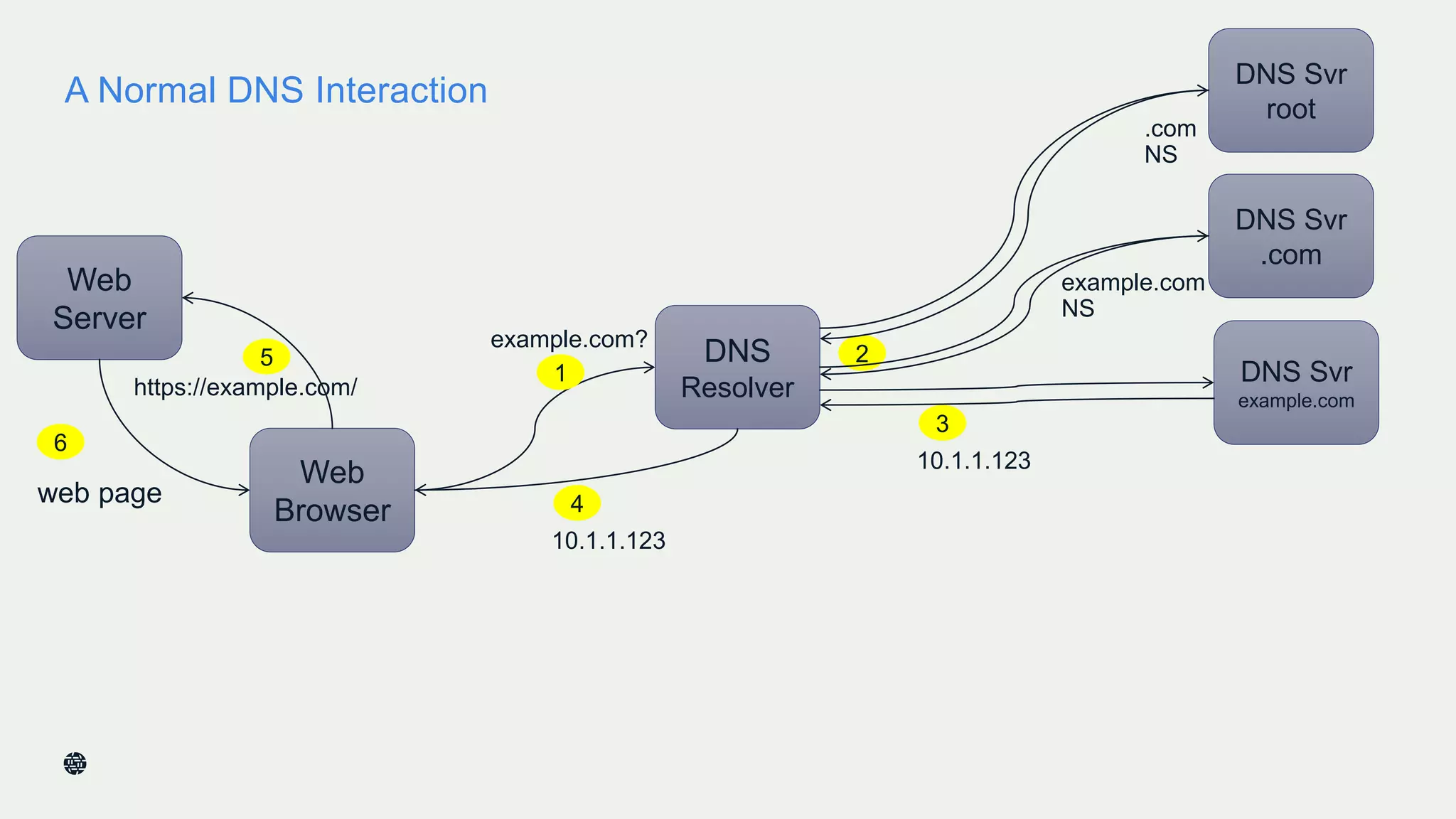
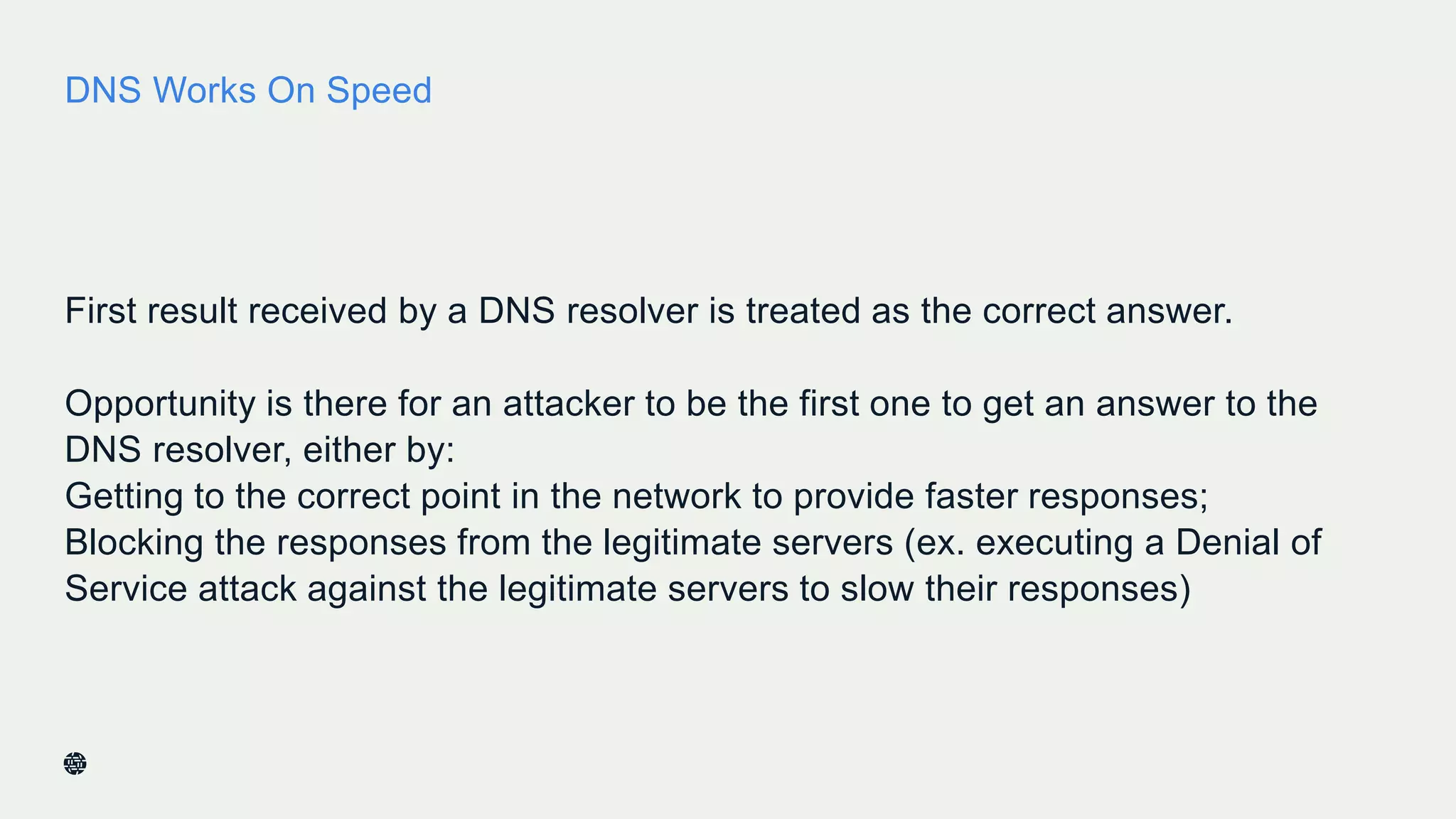
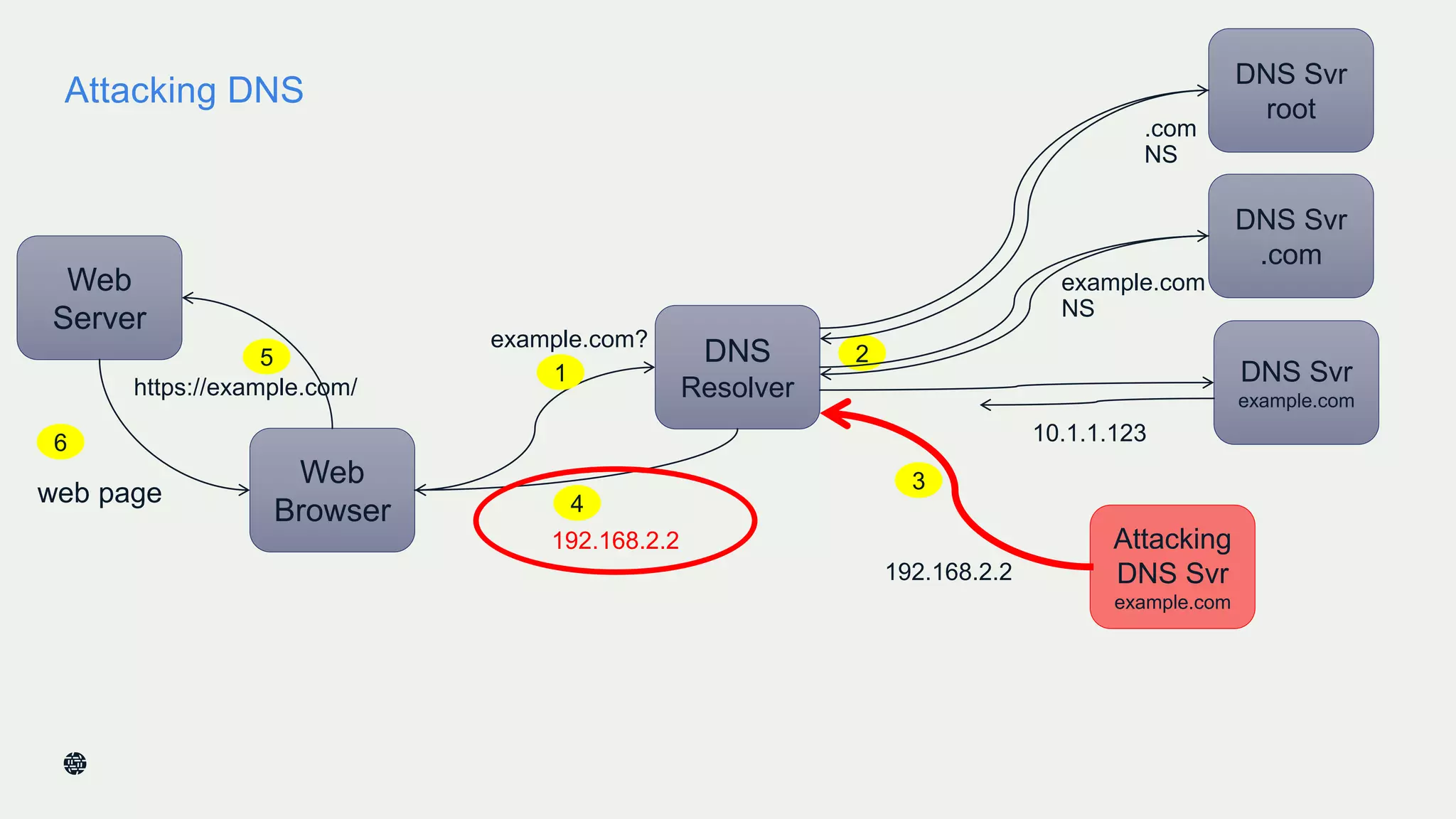
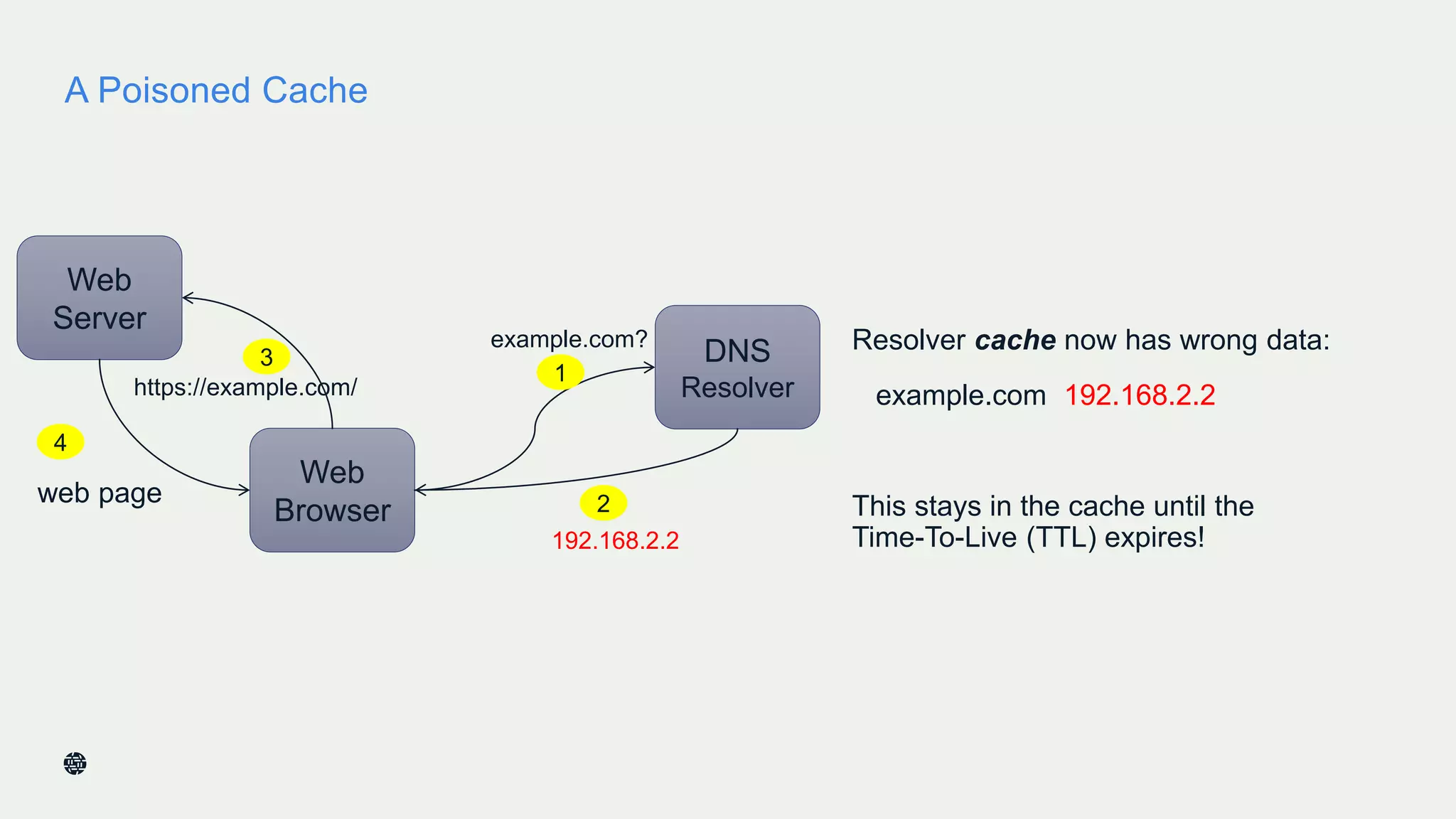
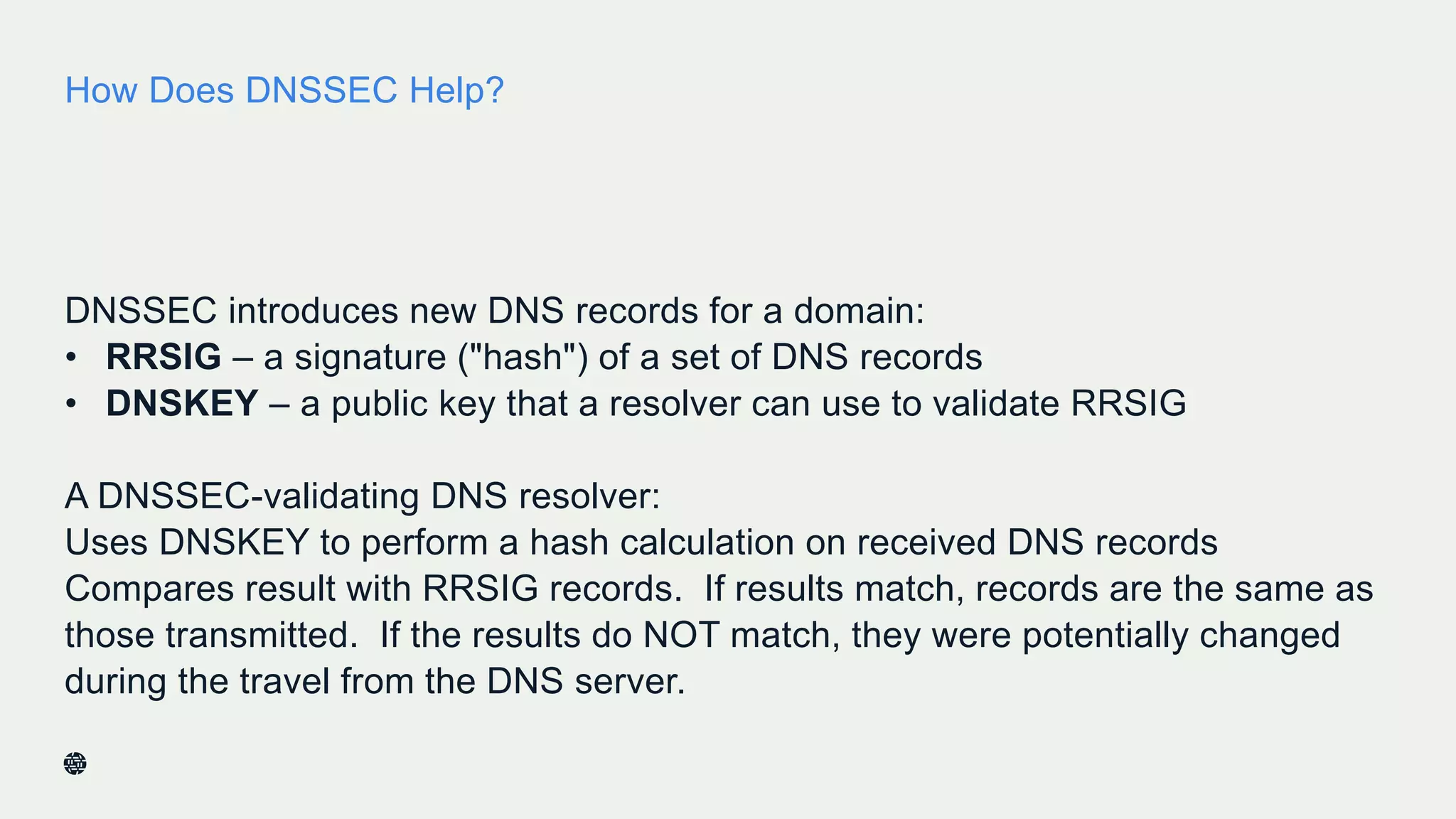
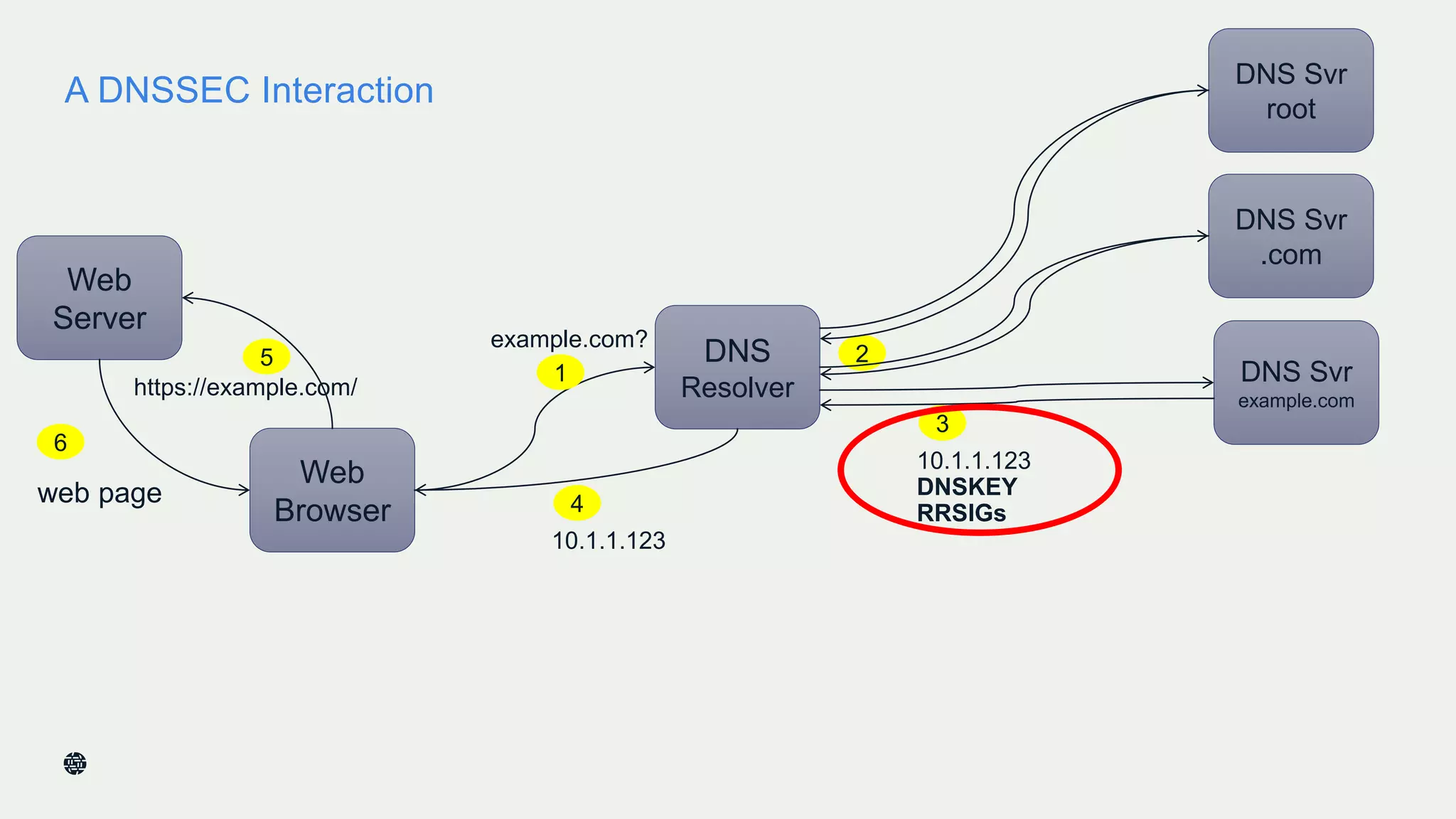
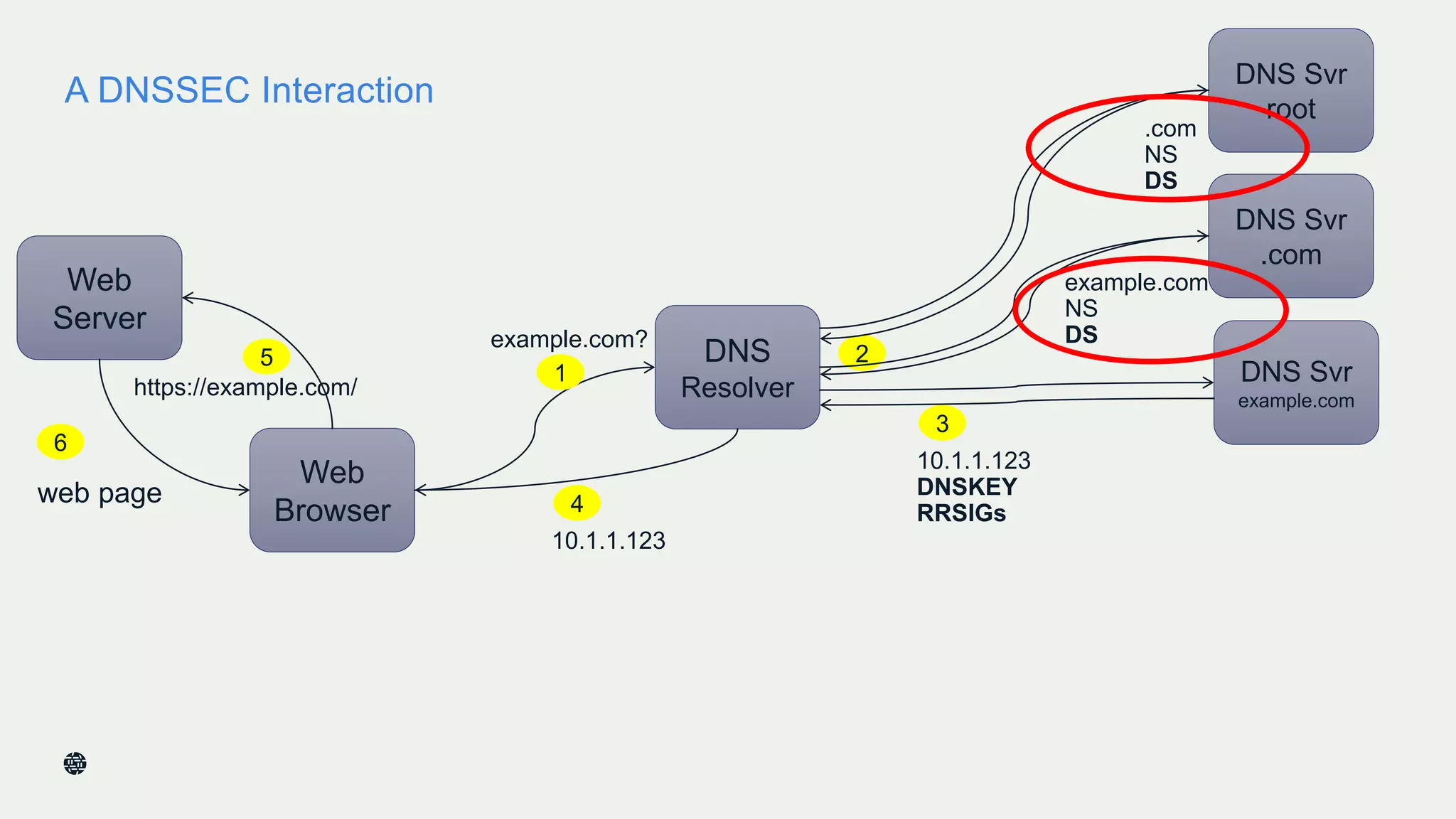
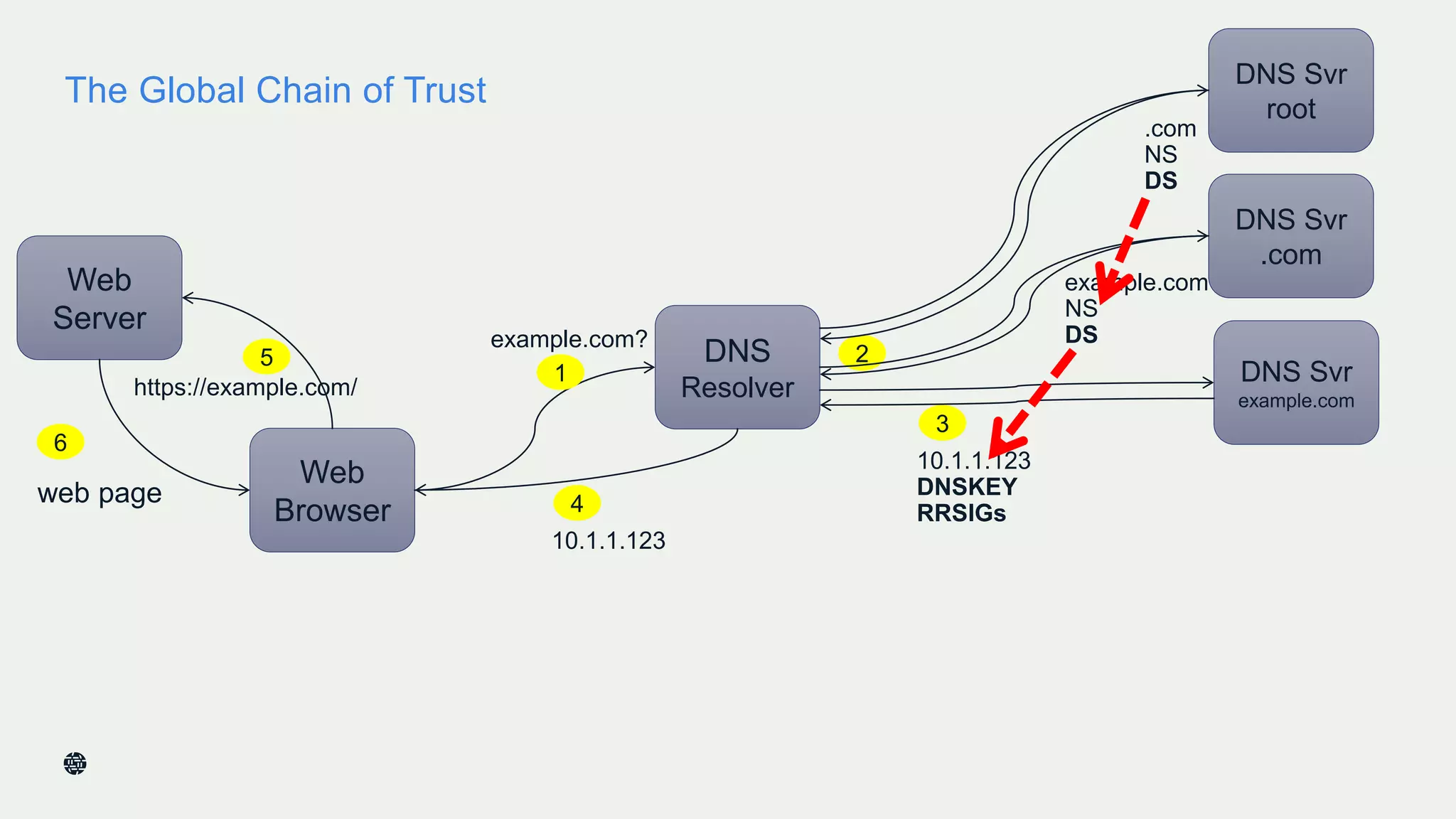
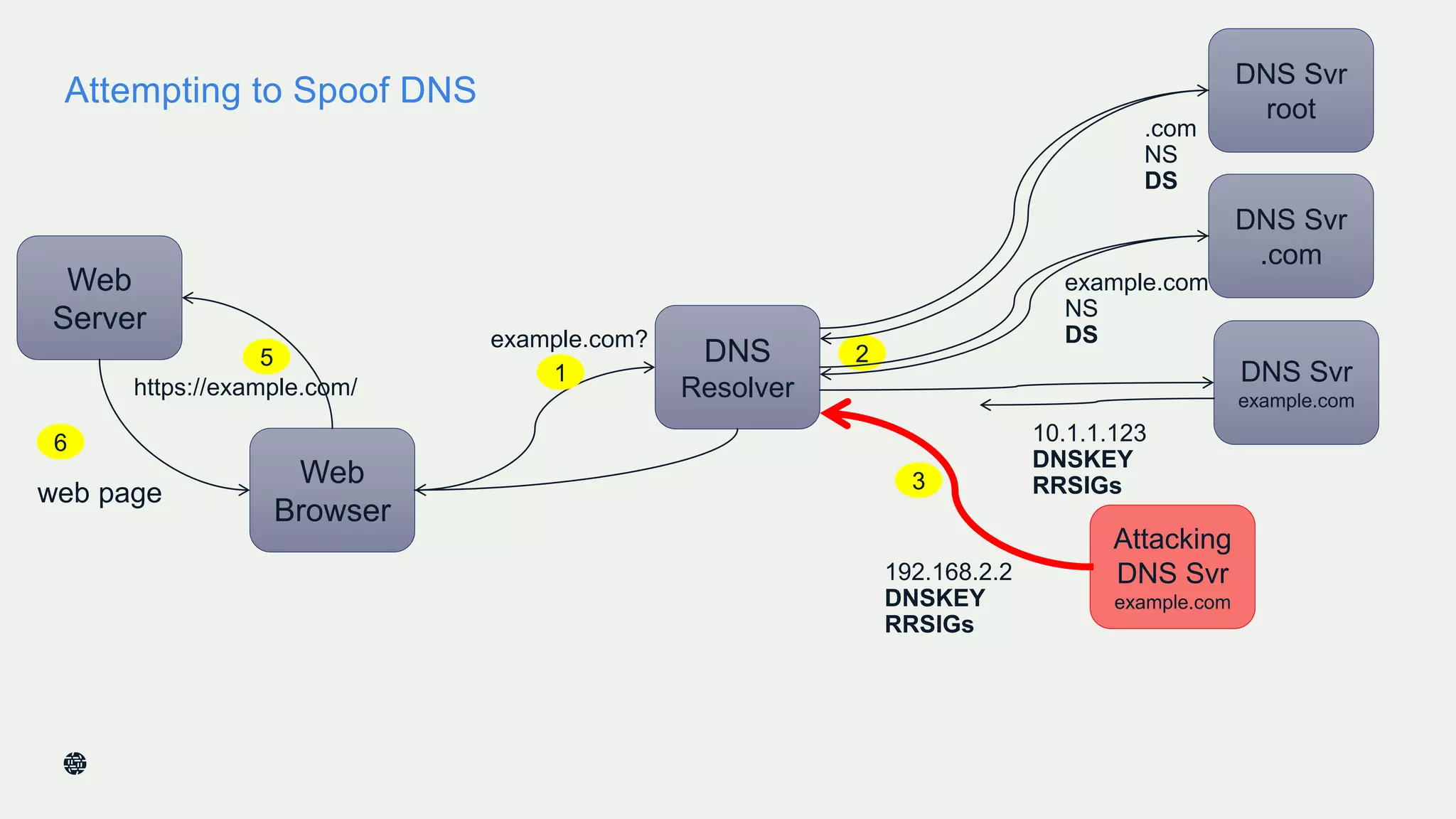
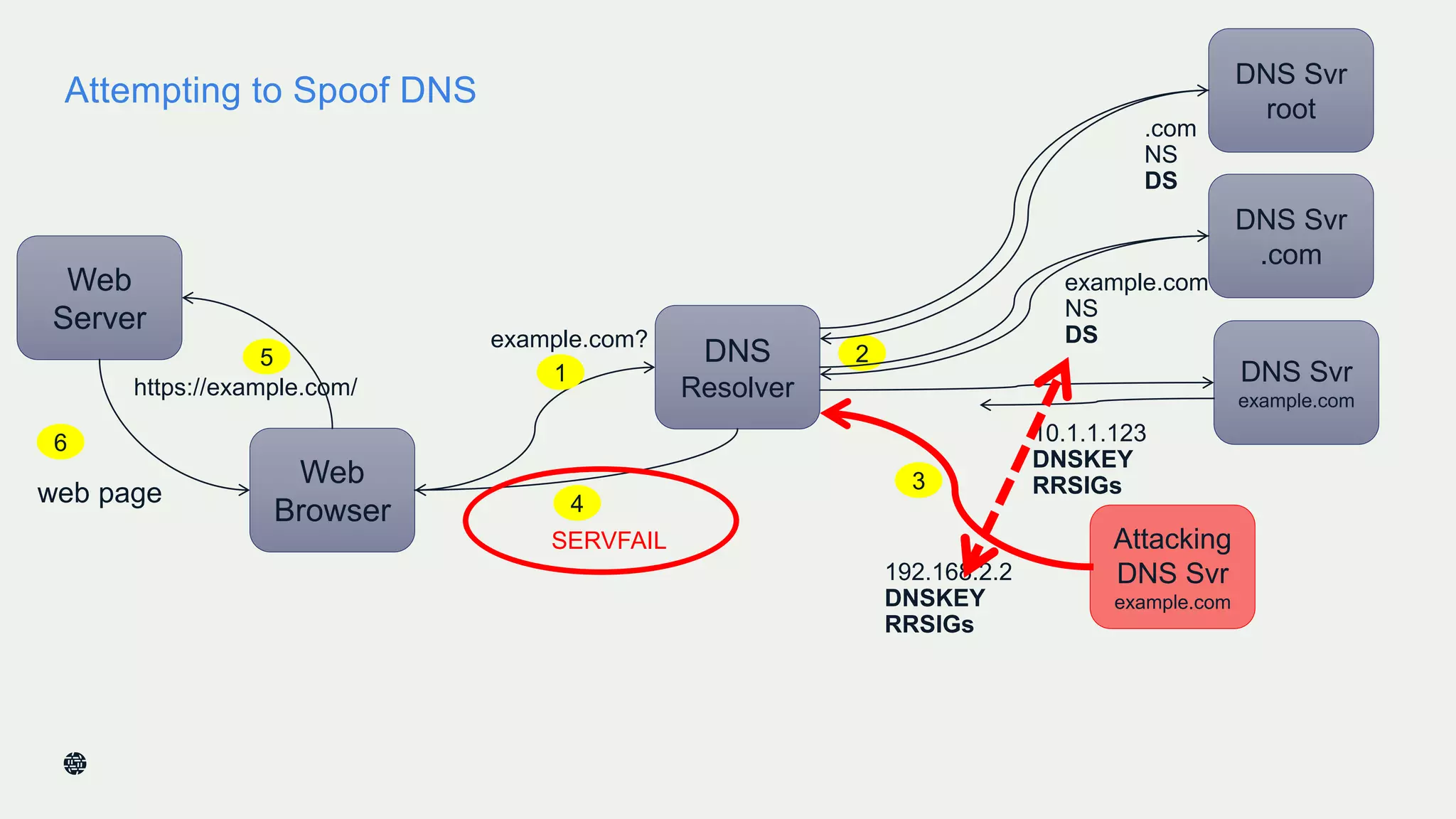
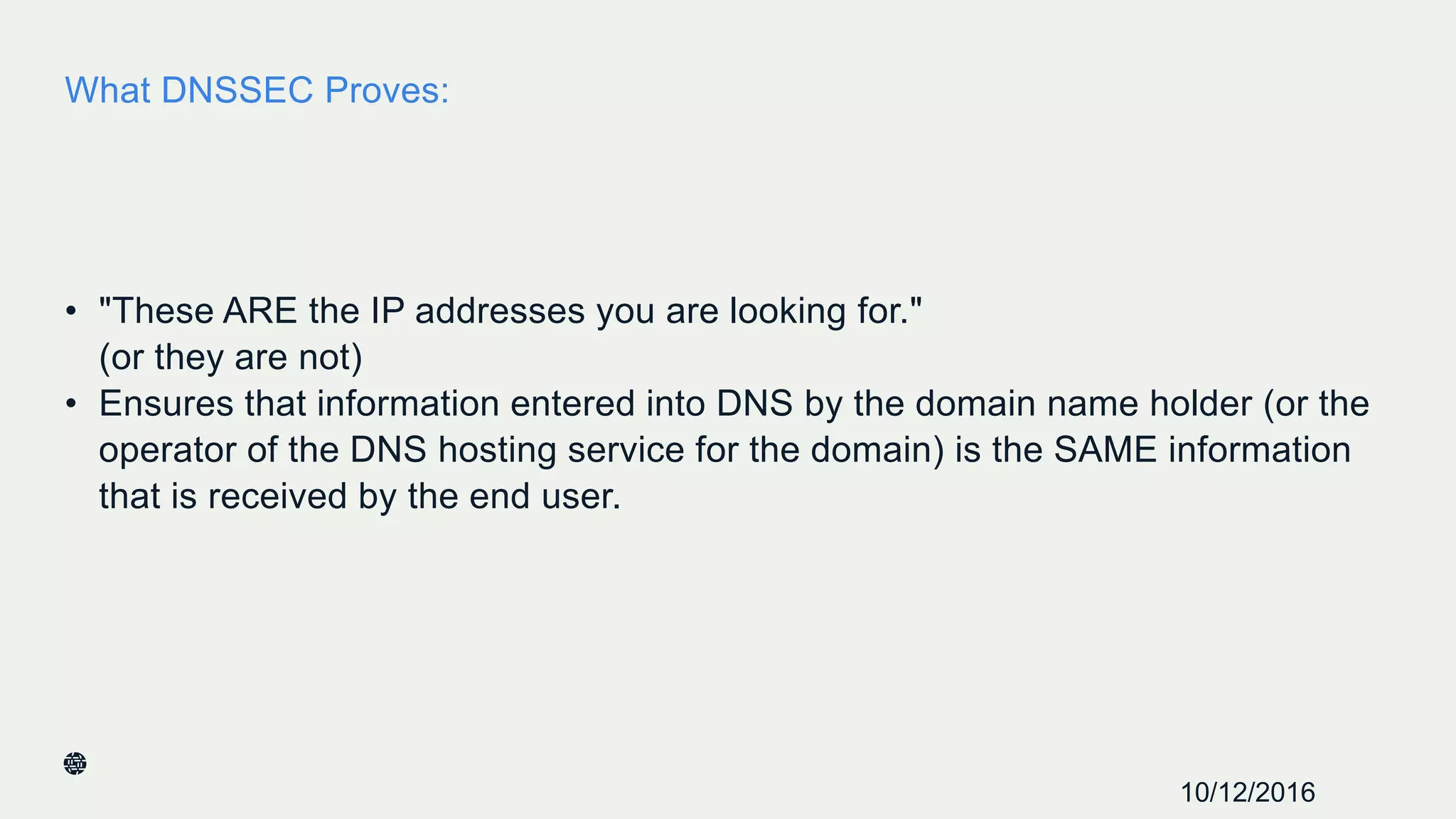
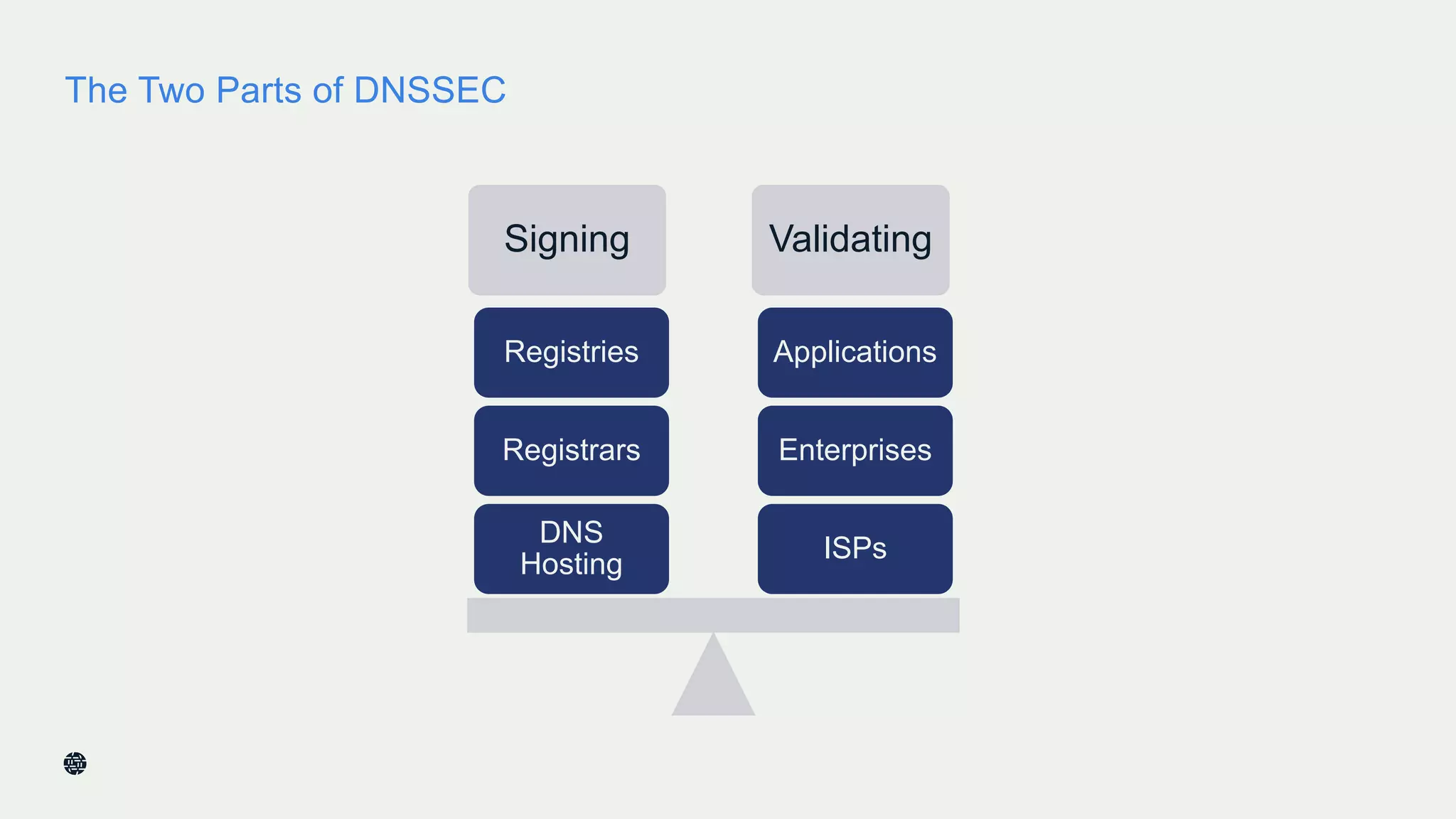
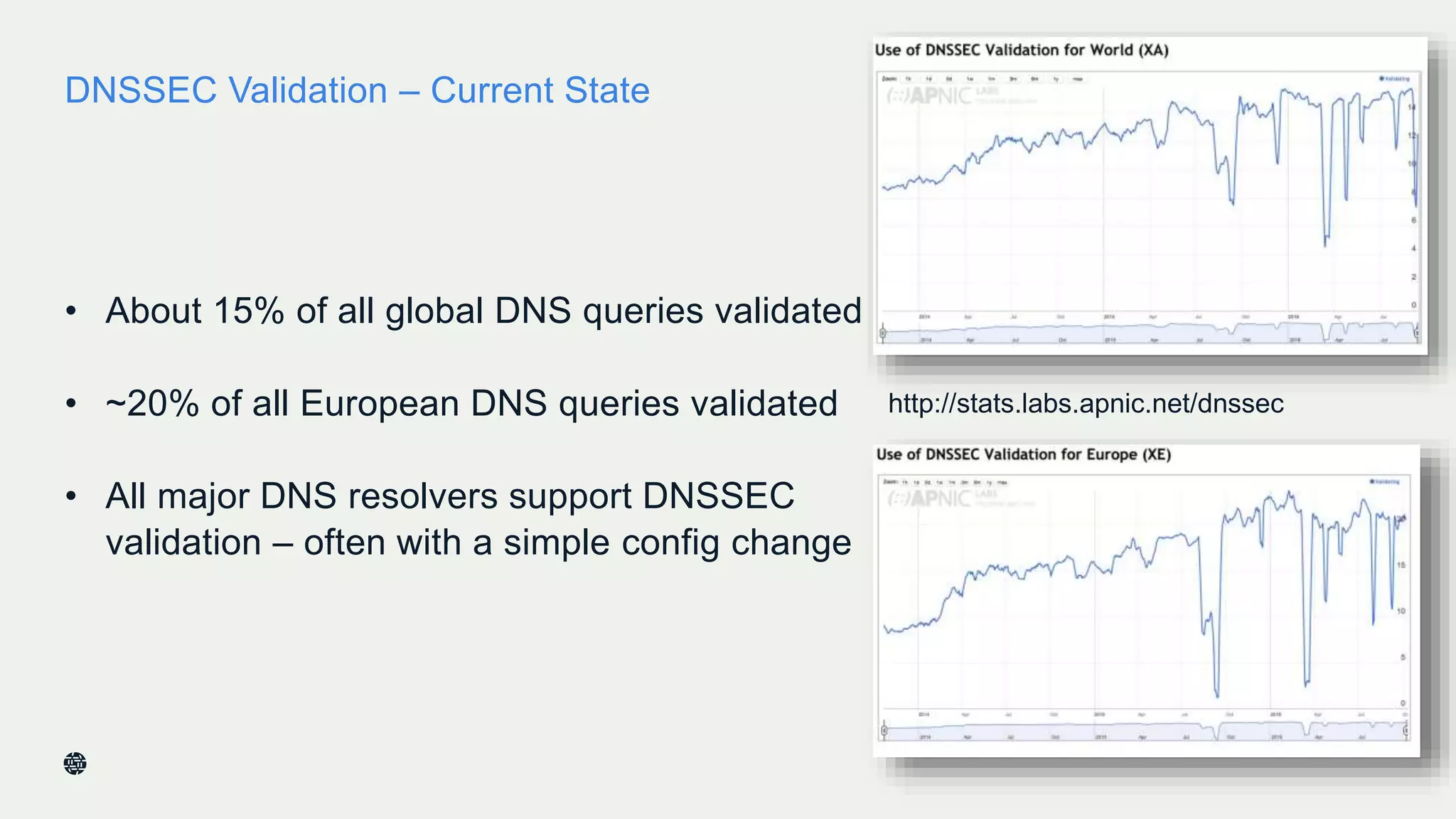
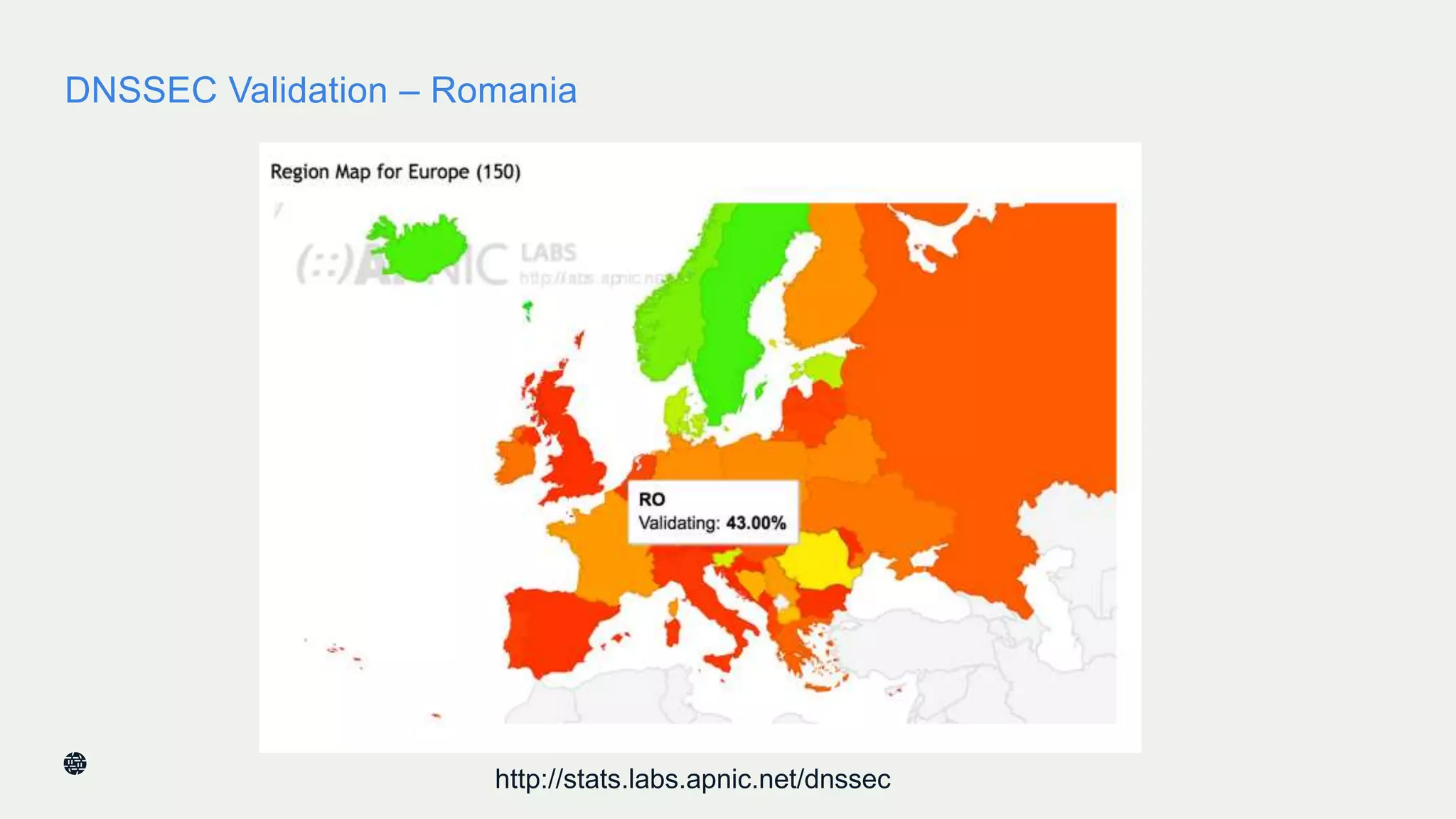
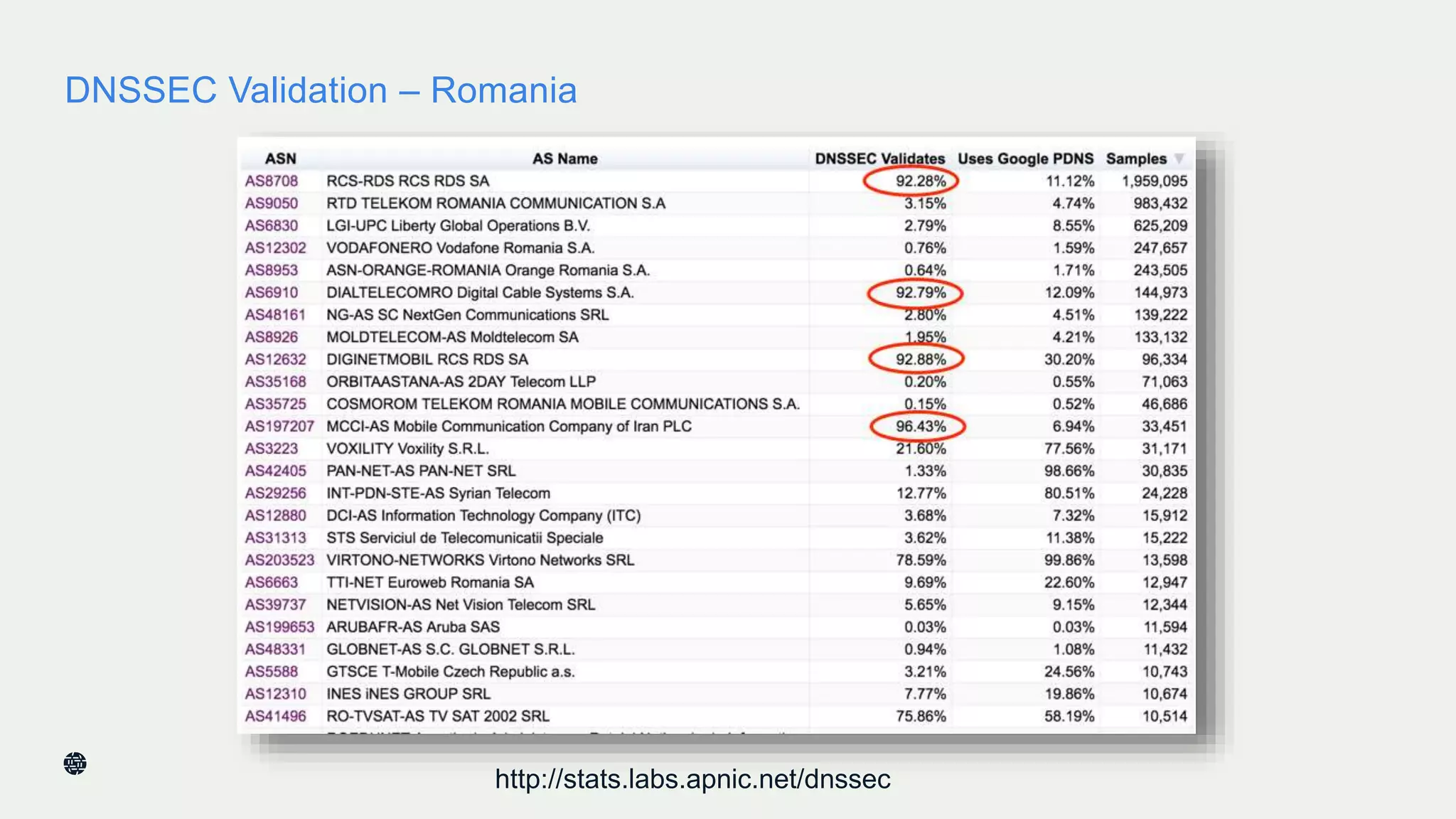
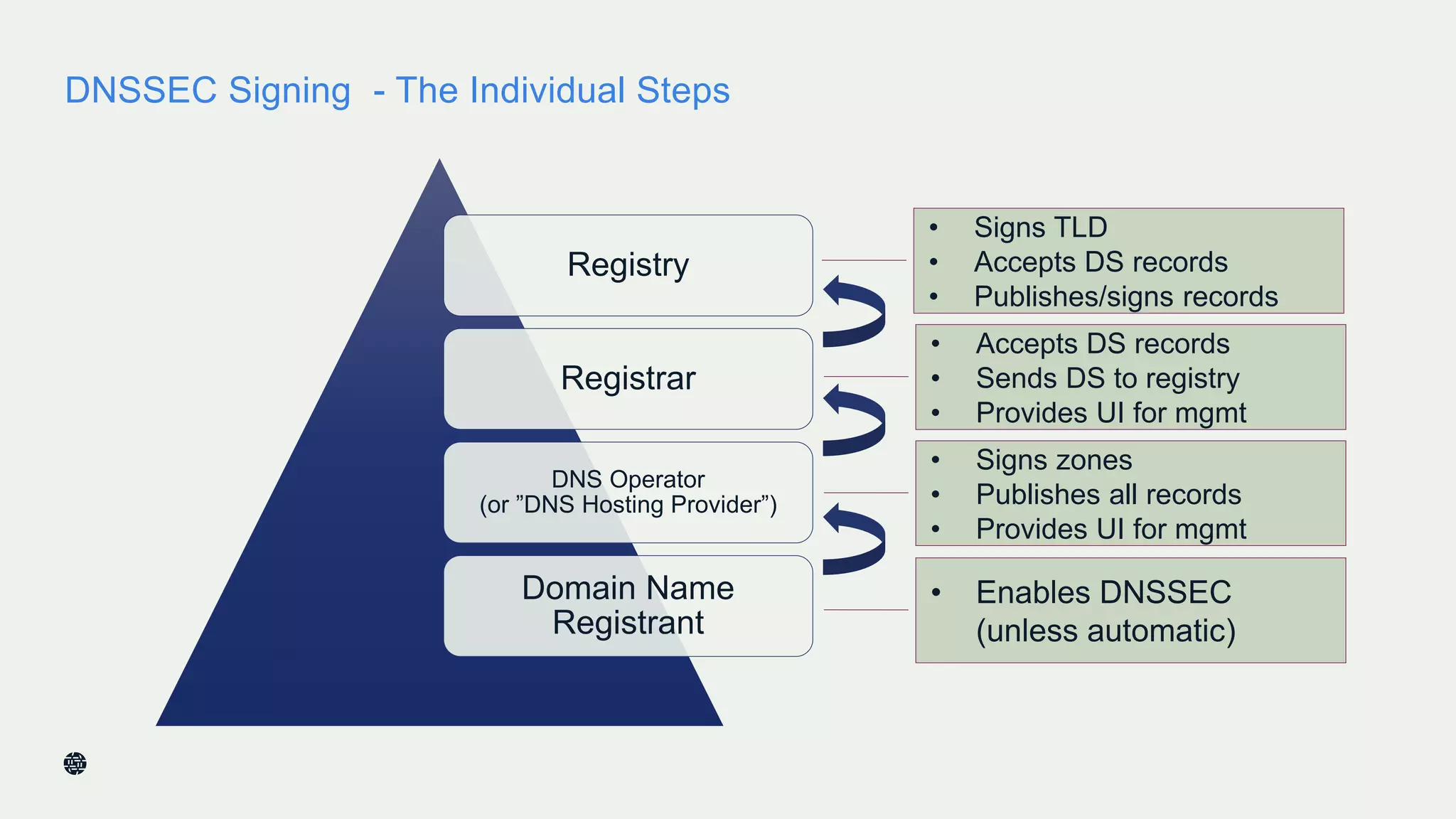
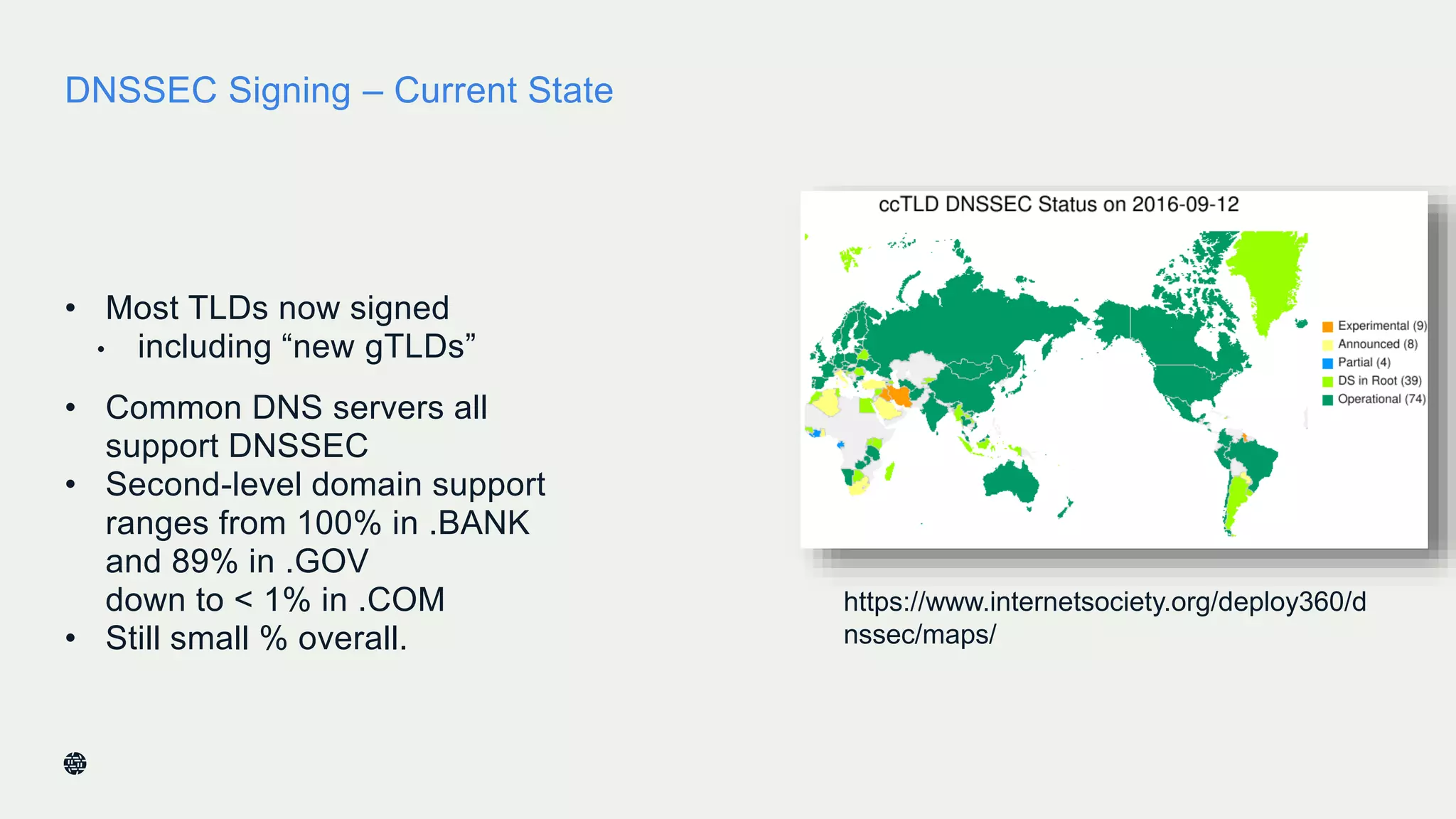
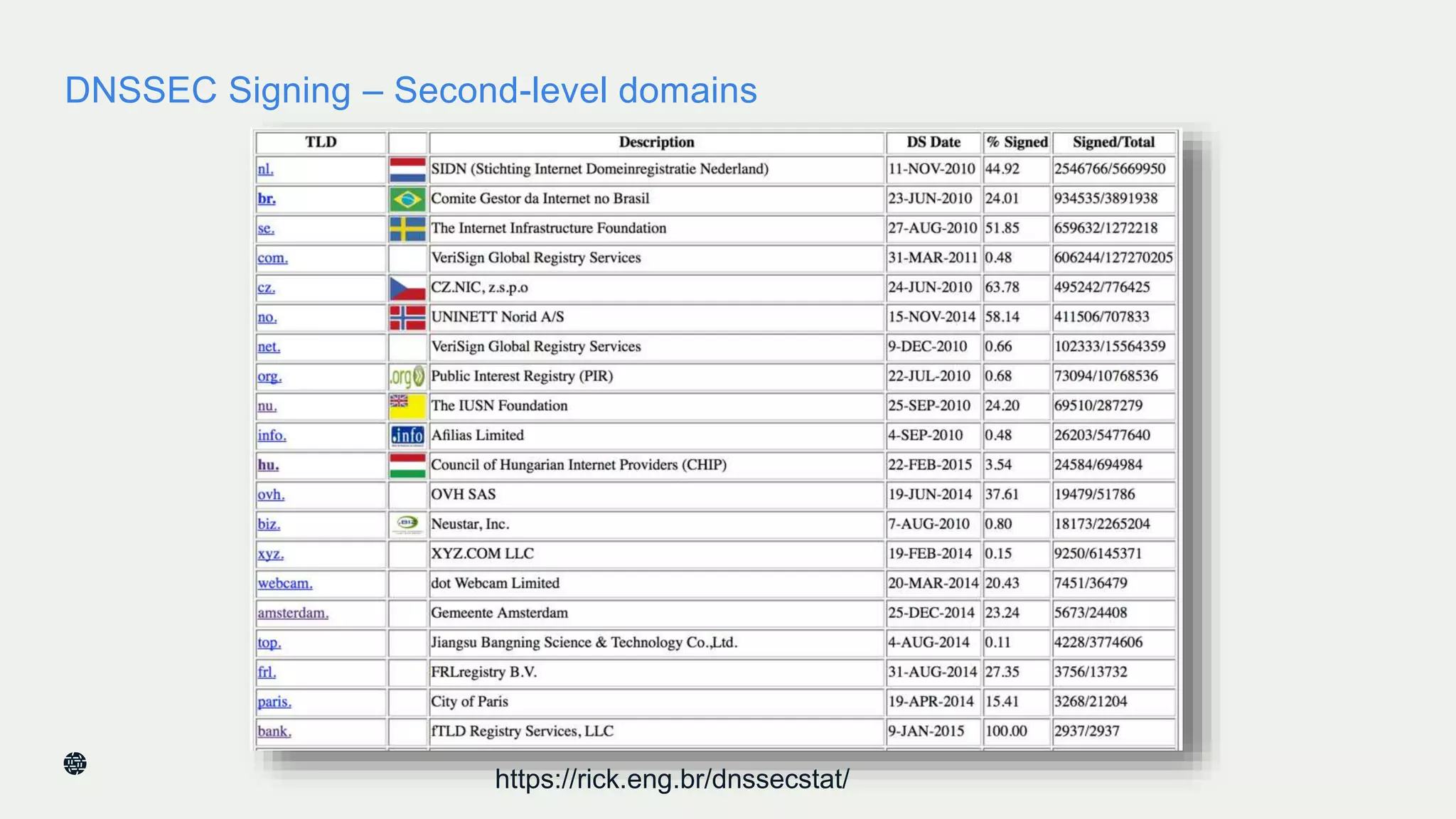
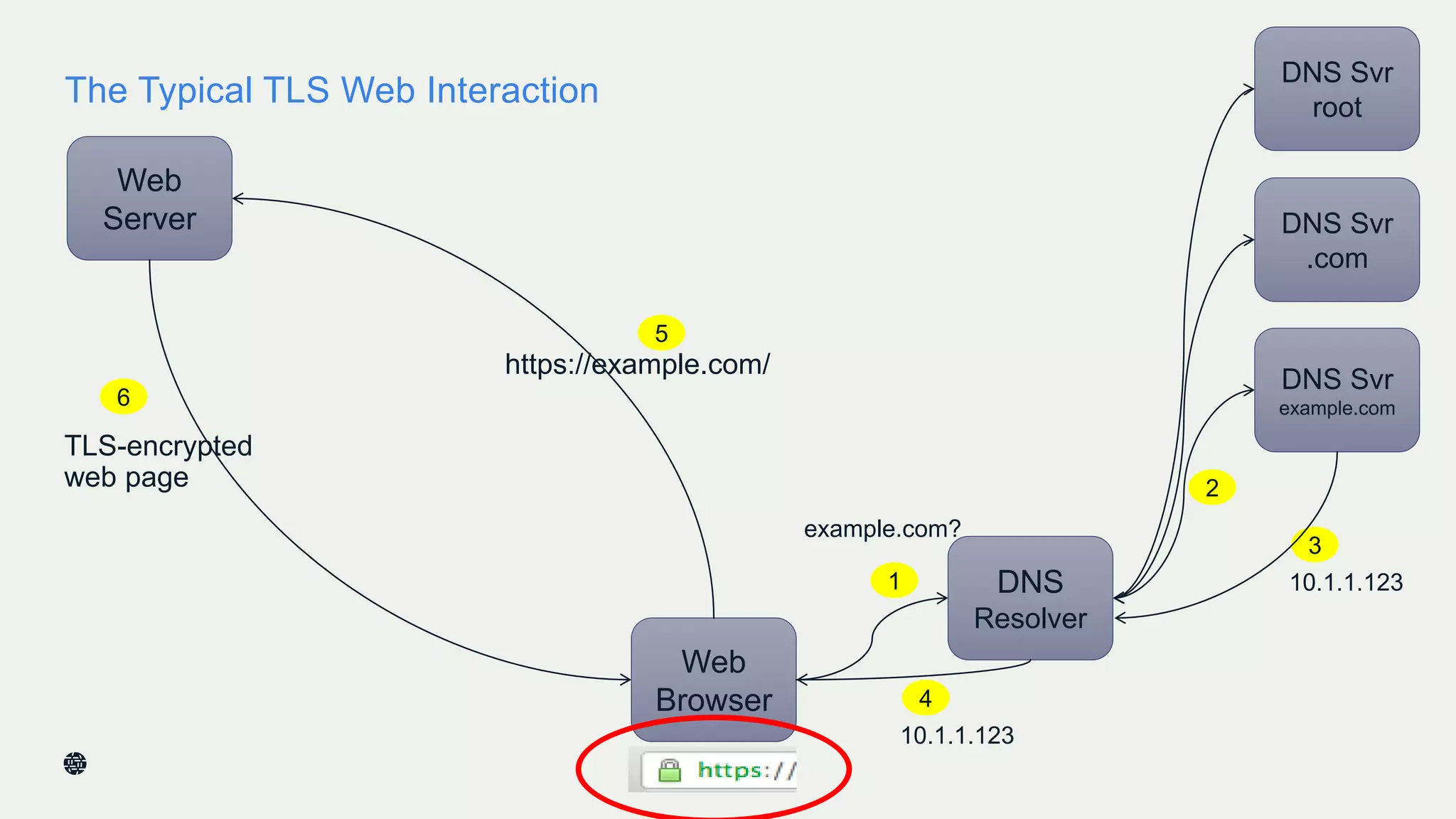
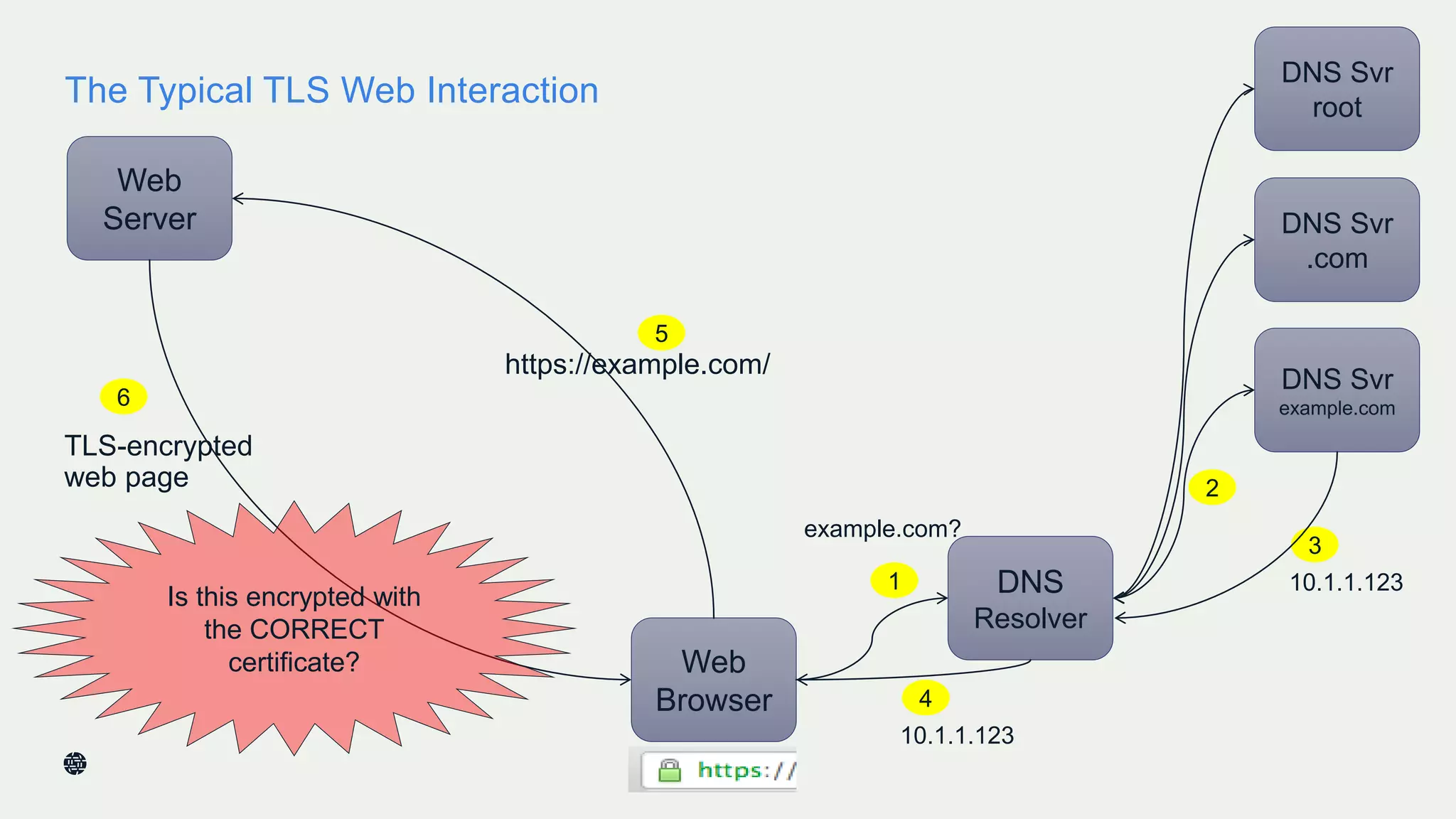
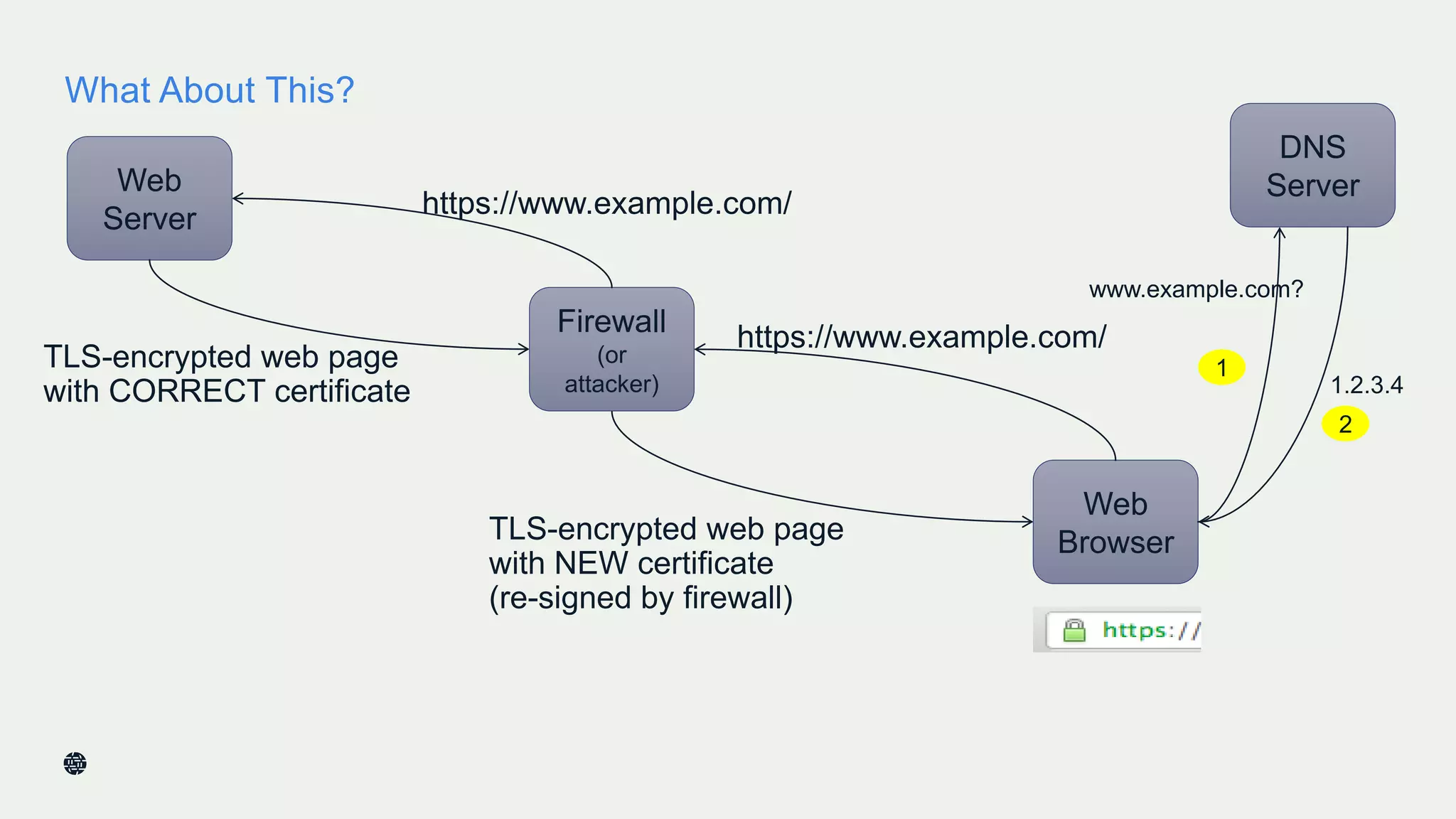
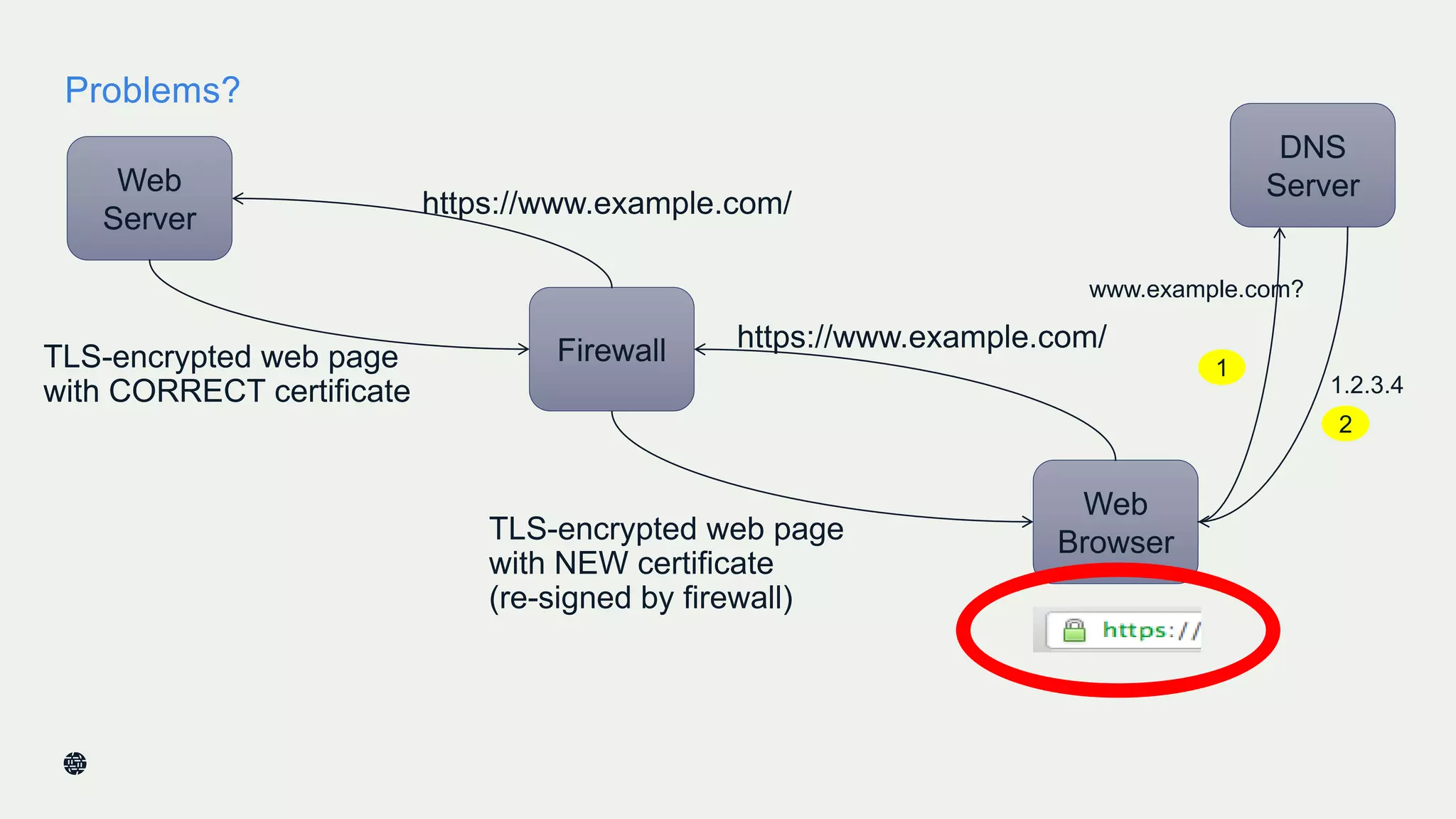
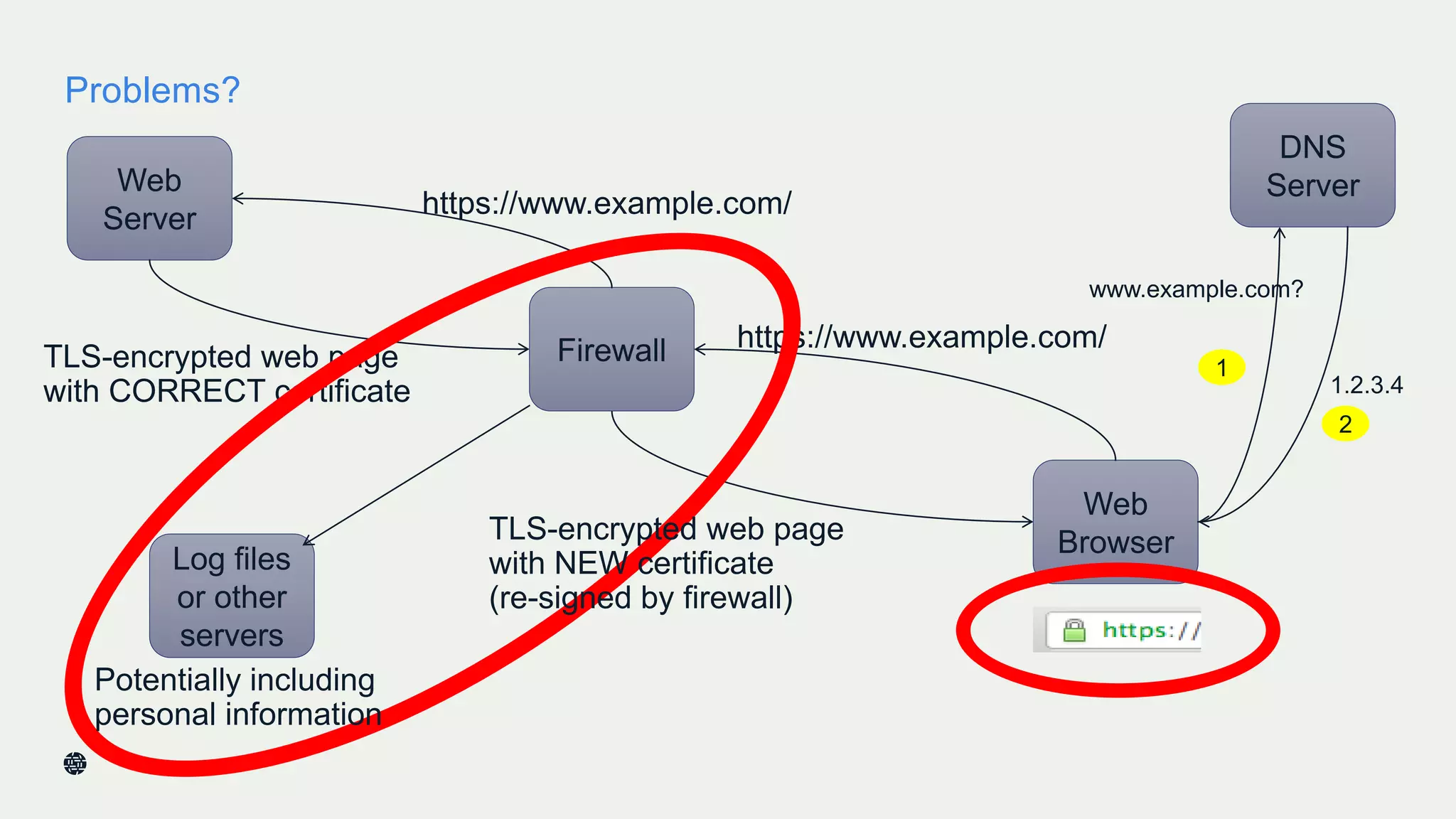
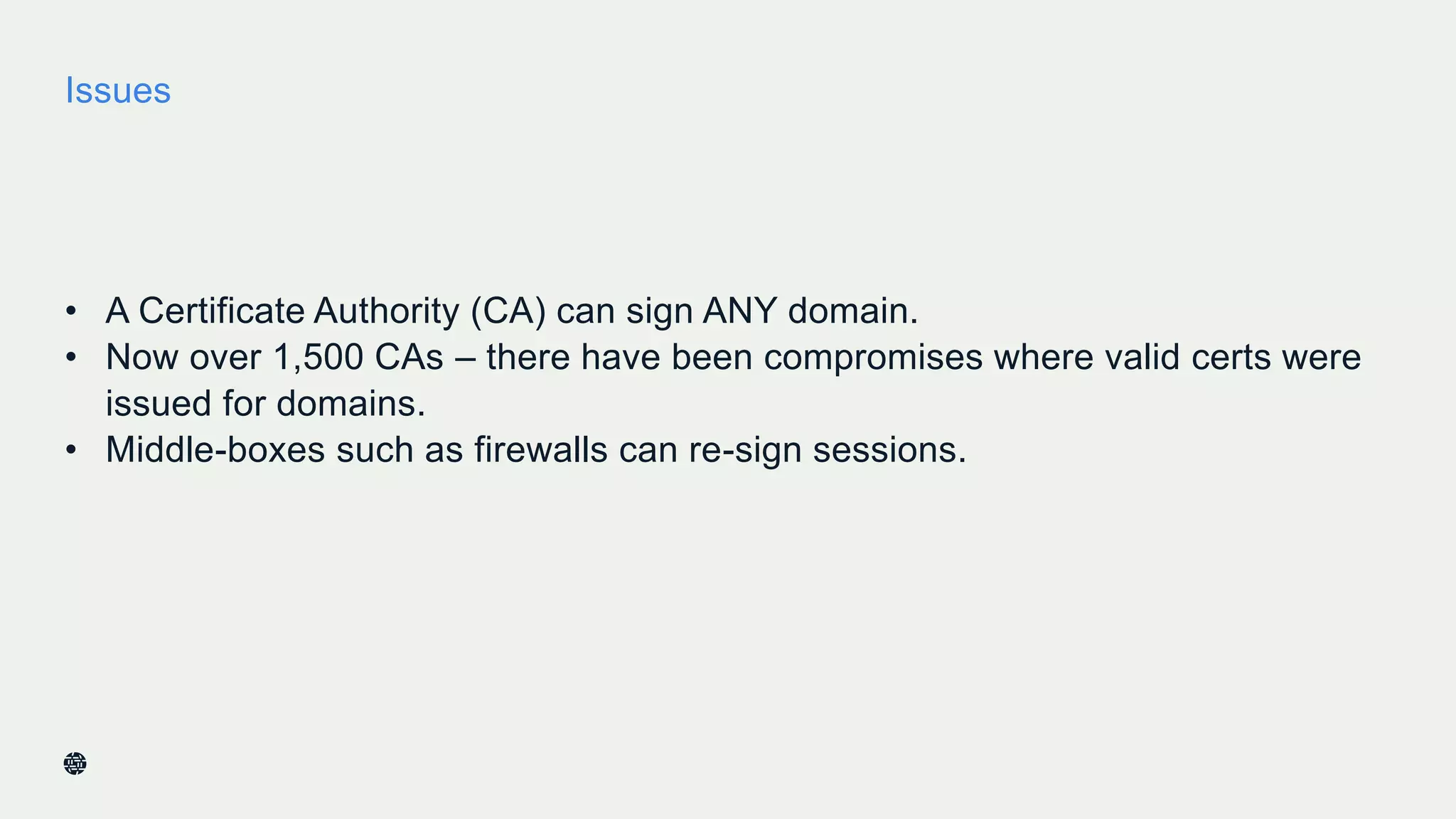
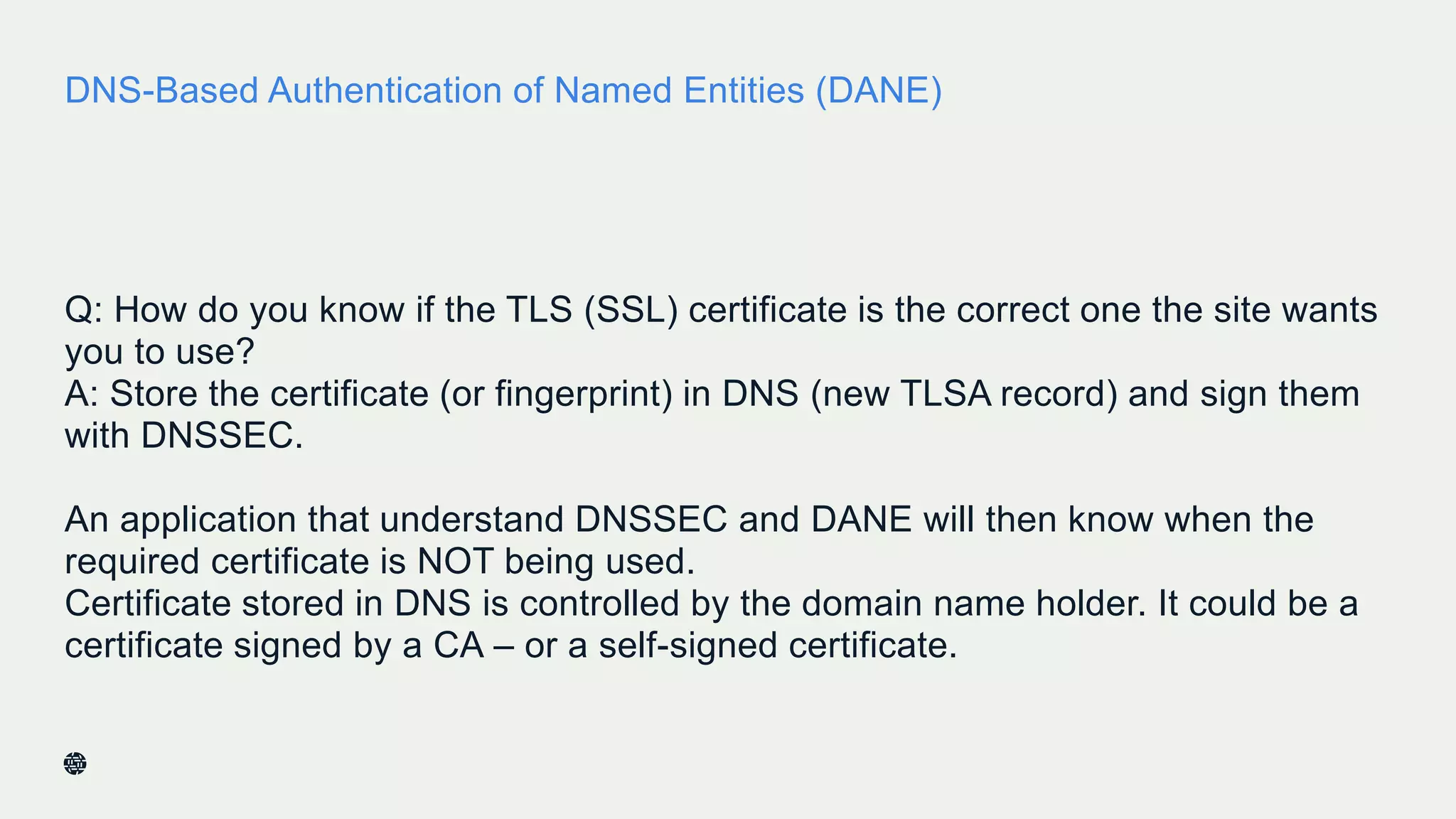
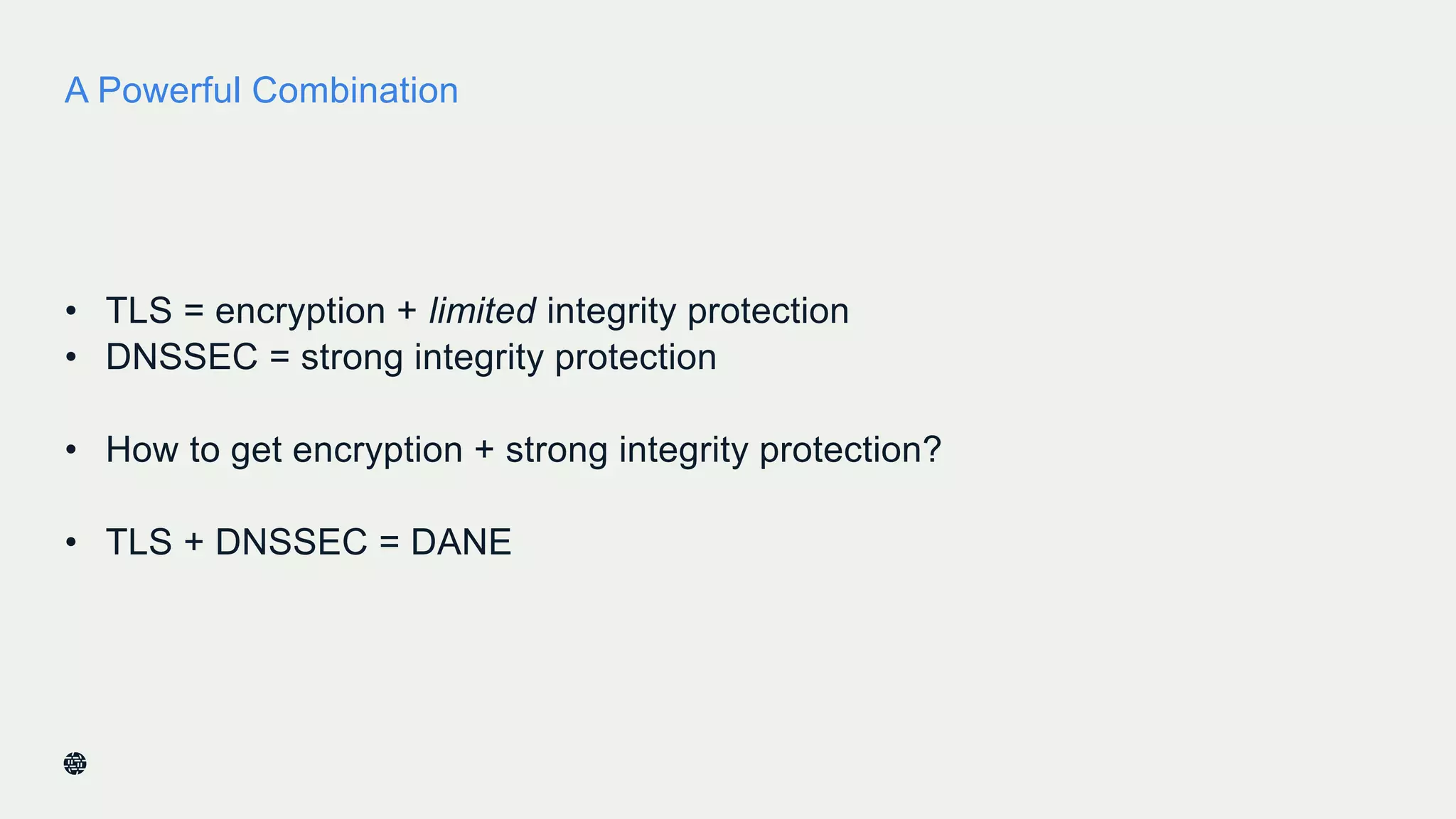
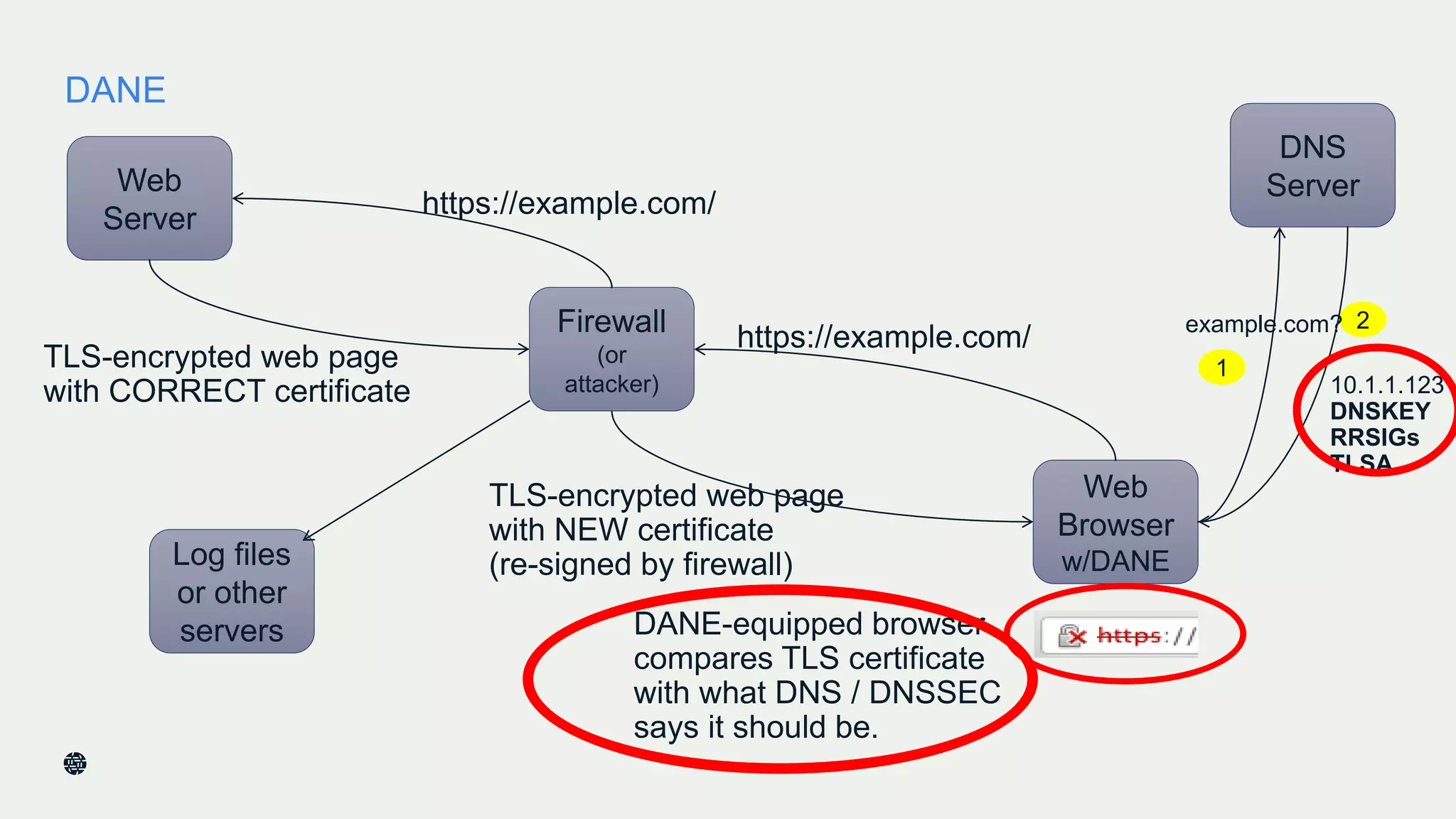
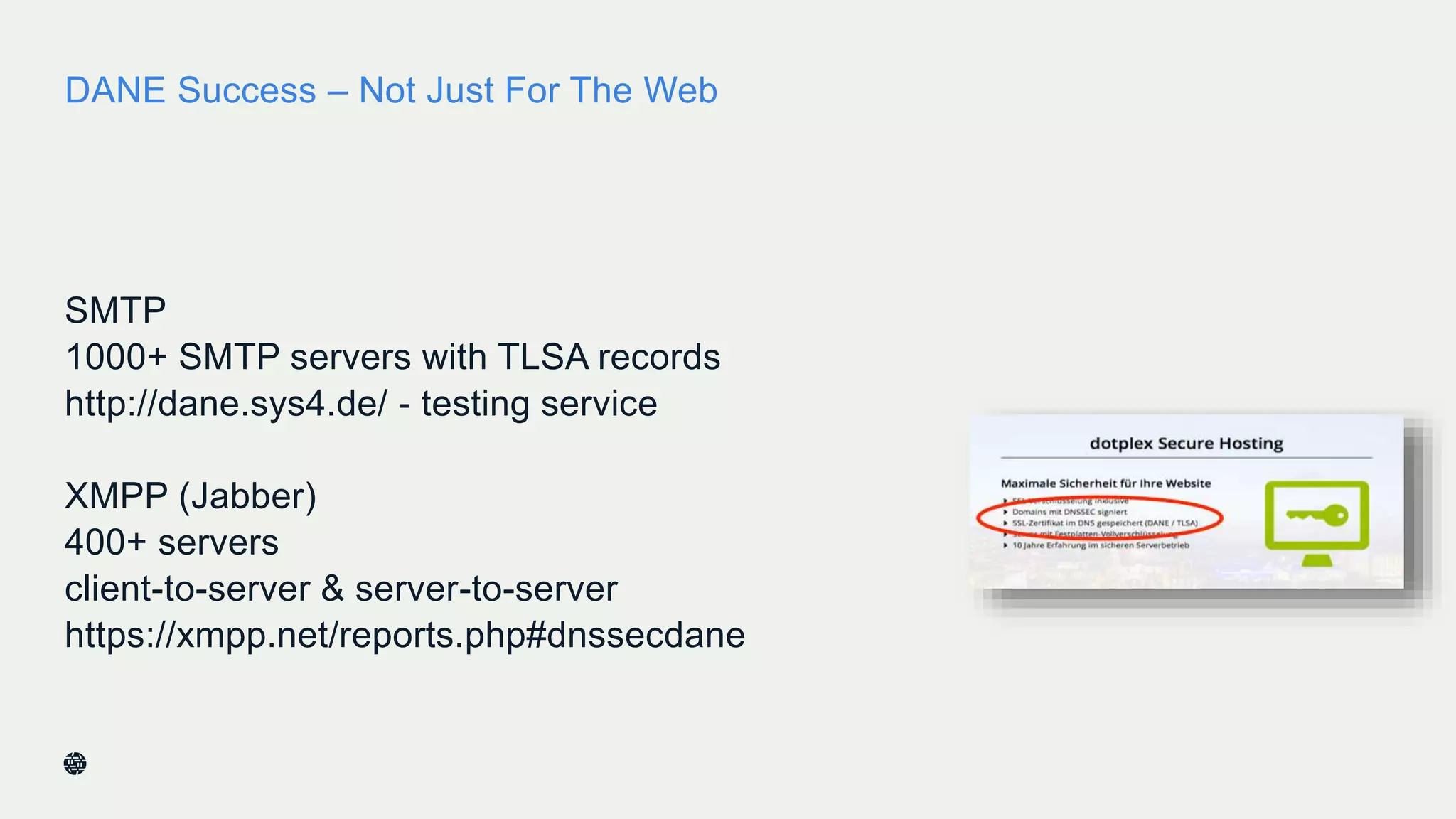
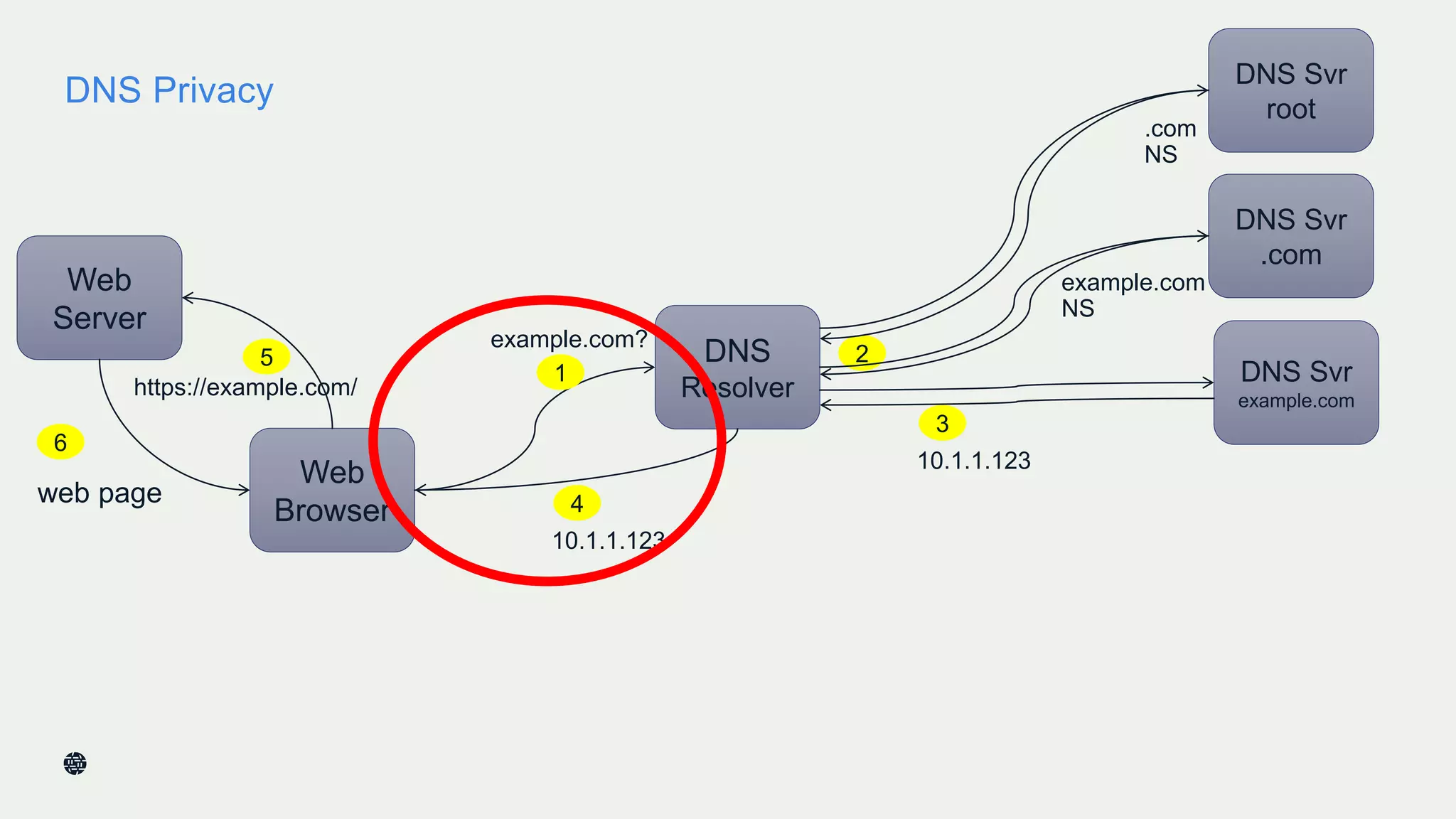
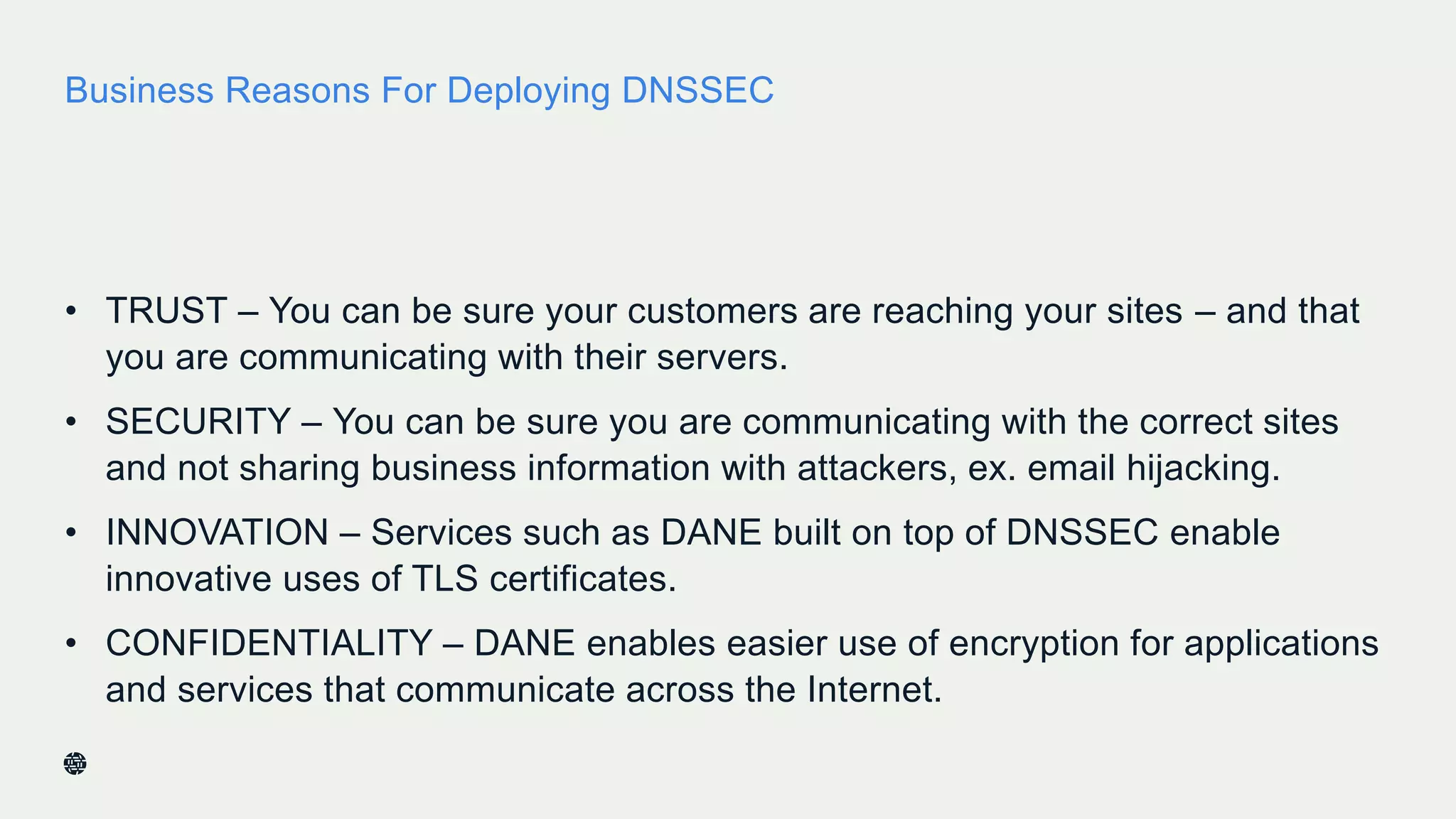
This document summarizes Dan York's presentation on deploying DNSSEC. It discusses how DNSSEC helps ensure the integrity of DNS data by using digital signatures to authenticate DNS responses, preventing cache poisoning and man-in-the-middle attacks. It provides examples of normal DNS interactions versus attacks, and how DNSSEC establishes a chain of trust. The presentation also covers the current state of DNSSEC deployment, how it works in combination with TLS/SSL through DANE, and business reasons for organizations to deploy DNSSEC.