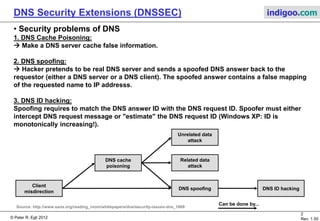
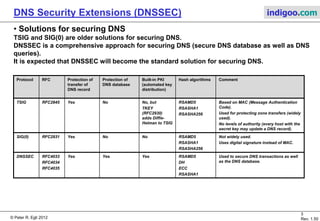
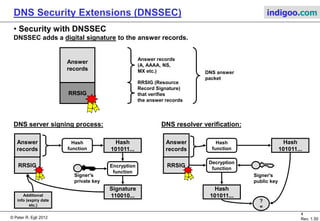
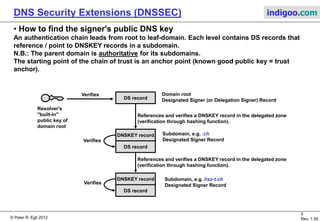
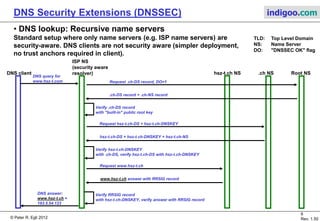
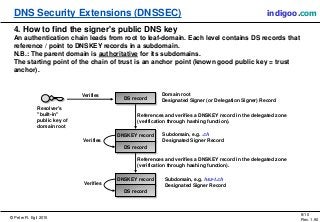
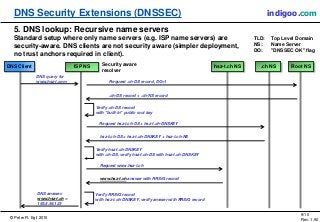
This document introduces DNS Security Extensions (DNSSEC) which aims to secure DNS queries and information by adding digital signatures to DNS response records. It discusses security problems with the current DNS system like cache poisoning and spoofing attacks. DNSSEC uses cryptographic keys and signatures to authenticate DNS responses and establish a chain of trust. While DNSSEC adds security, its deployment has been gradual due to complexity and the need for widespread implementation to provide full benefits.