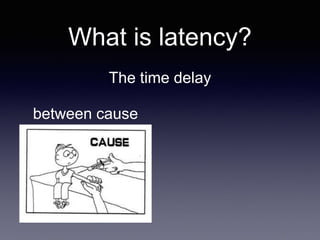
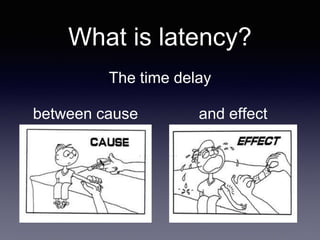
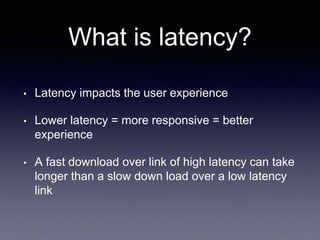
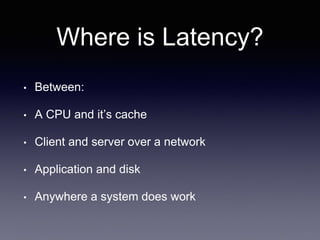
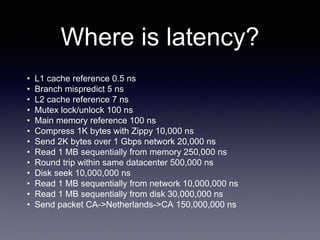
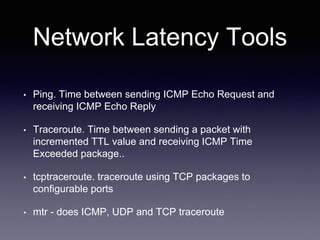
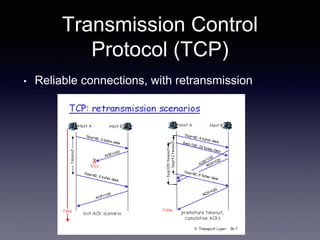
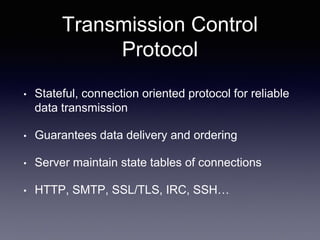
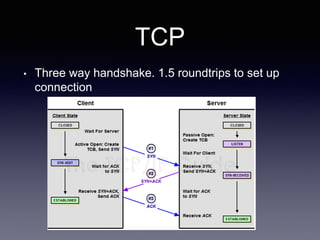
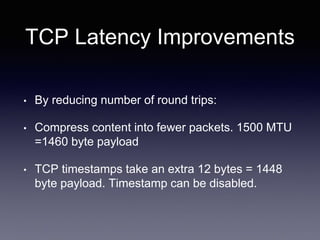
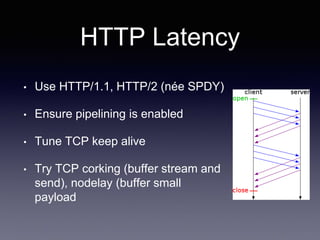
The document discusses network latency, its impact on user experience, and the various causes of latency within systems. It highlights methods for measuring latency, tools for improvement, and best practices to optimize network performance, including the use of TCP and DNS optimizations. Additionally, it recommends leveraging content delivery networks and monitoring tools to further enhance efficiency and user experience.