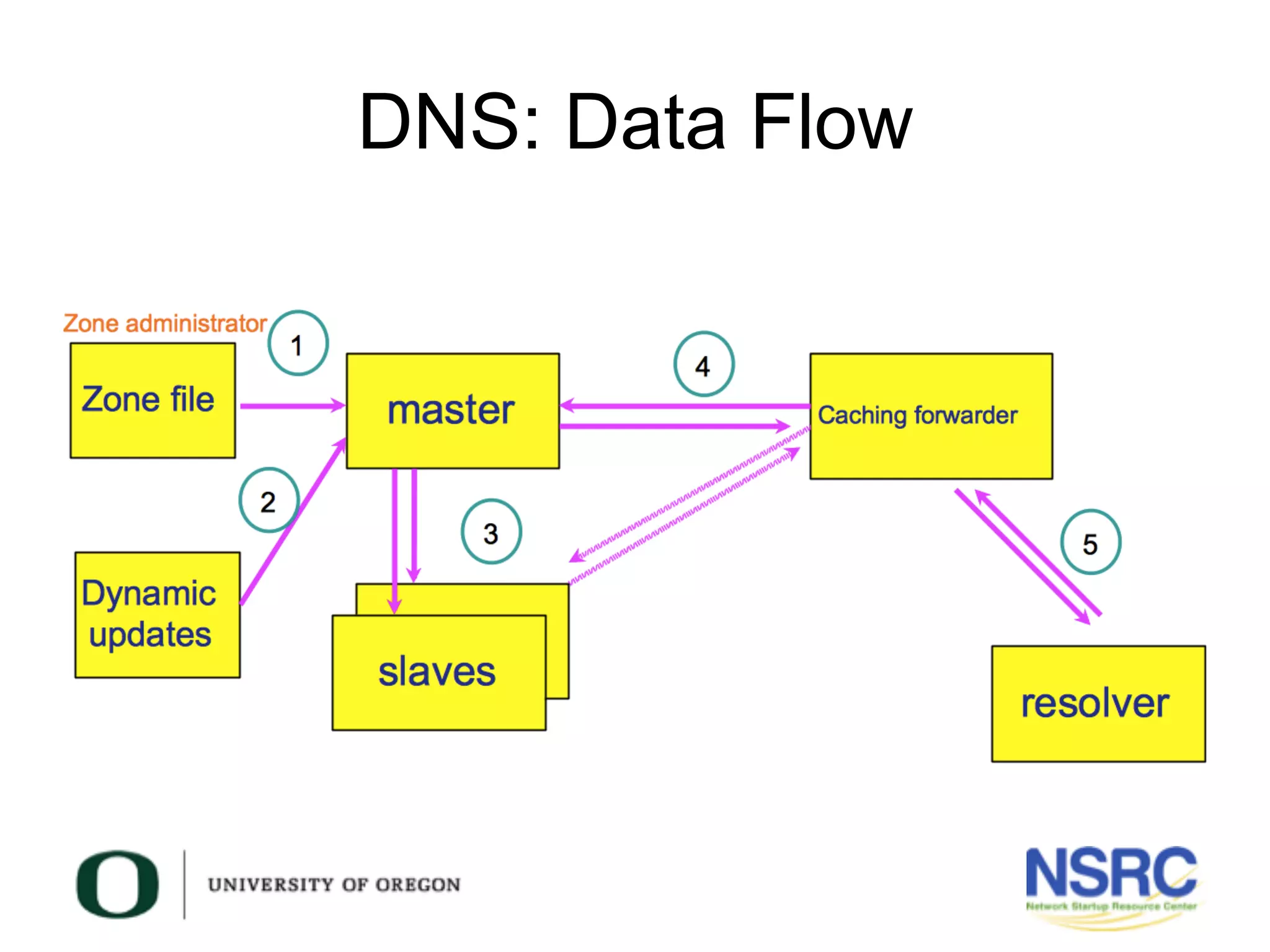
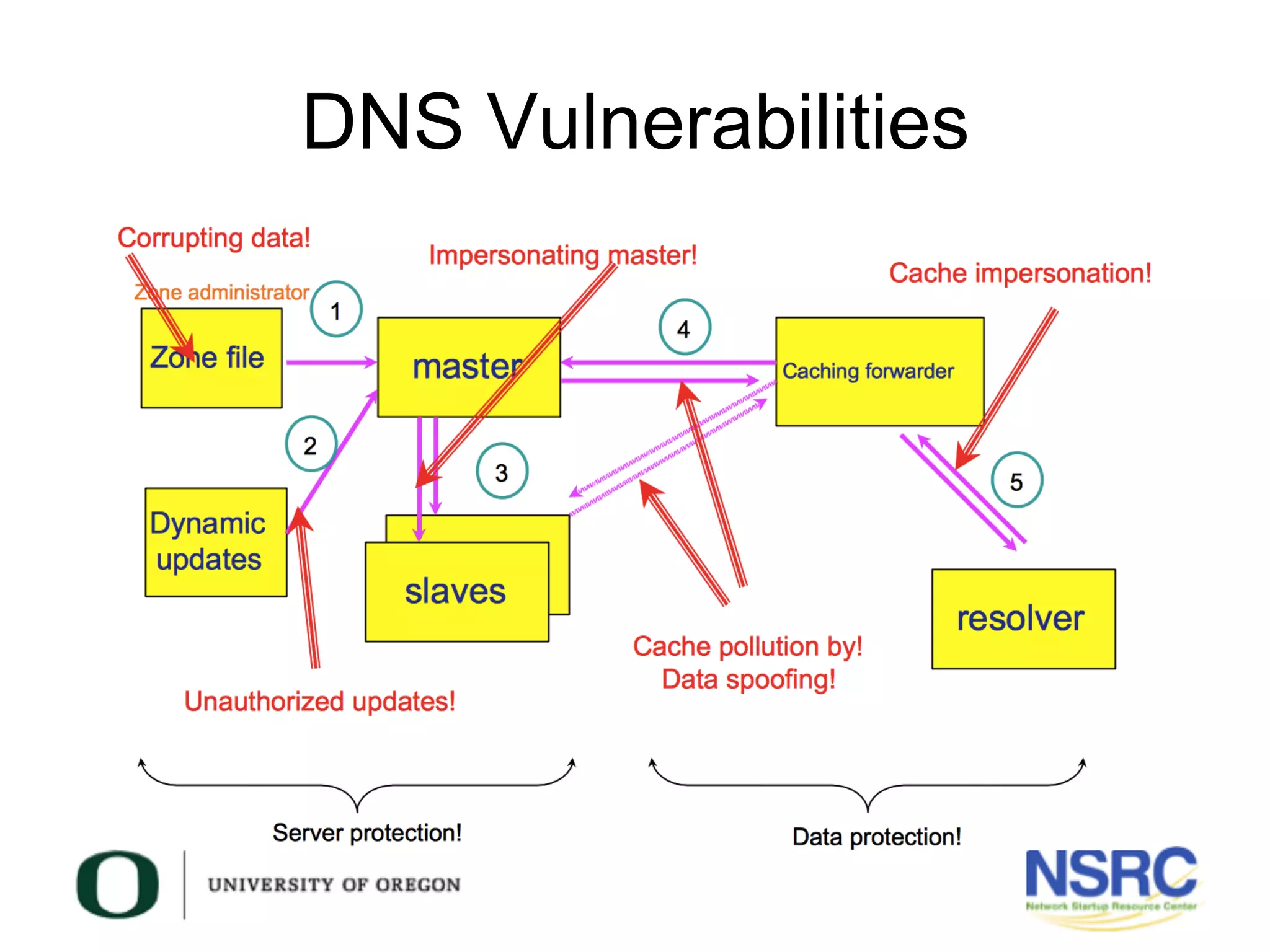
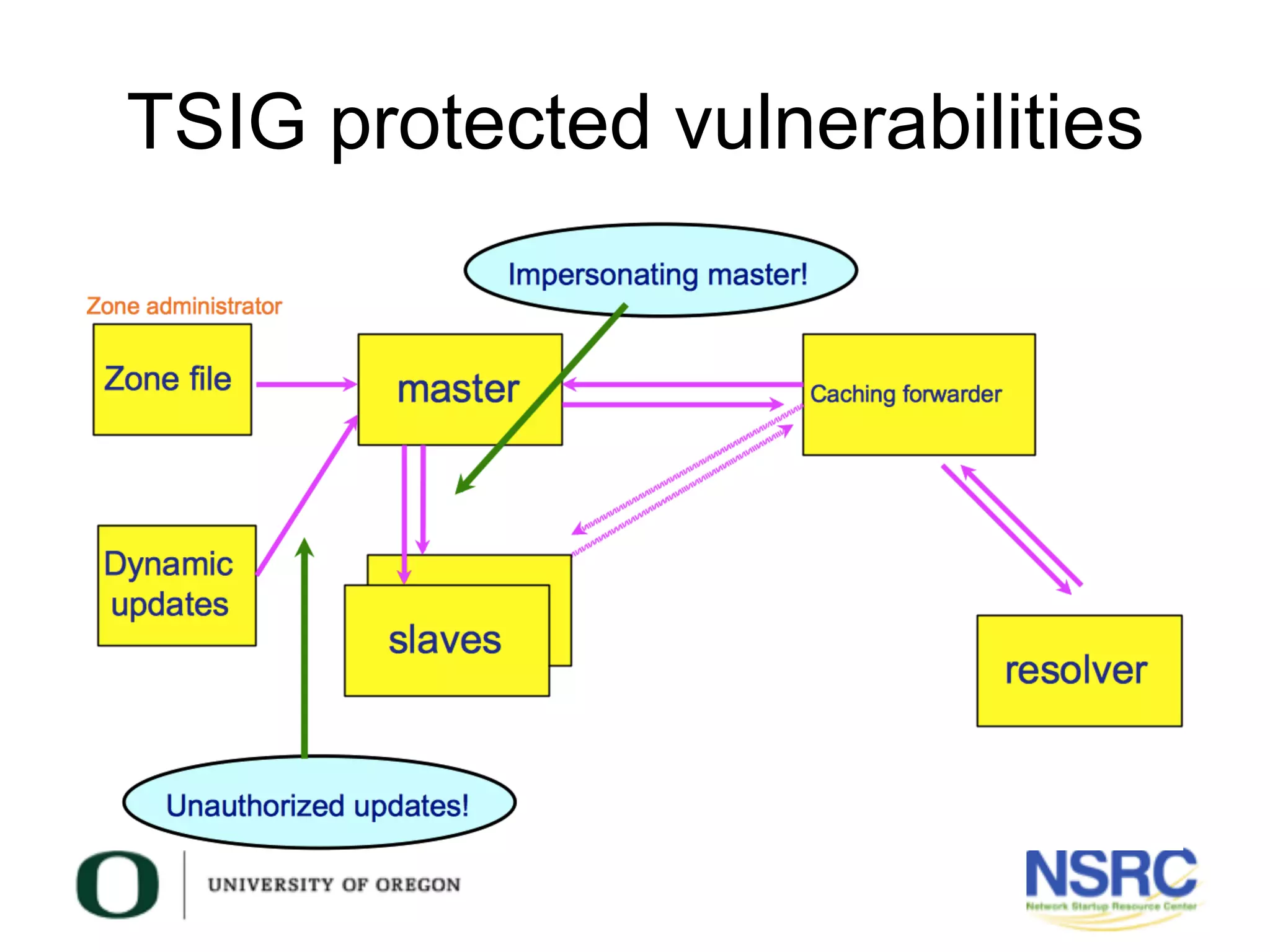
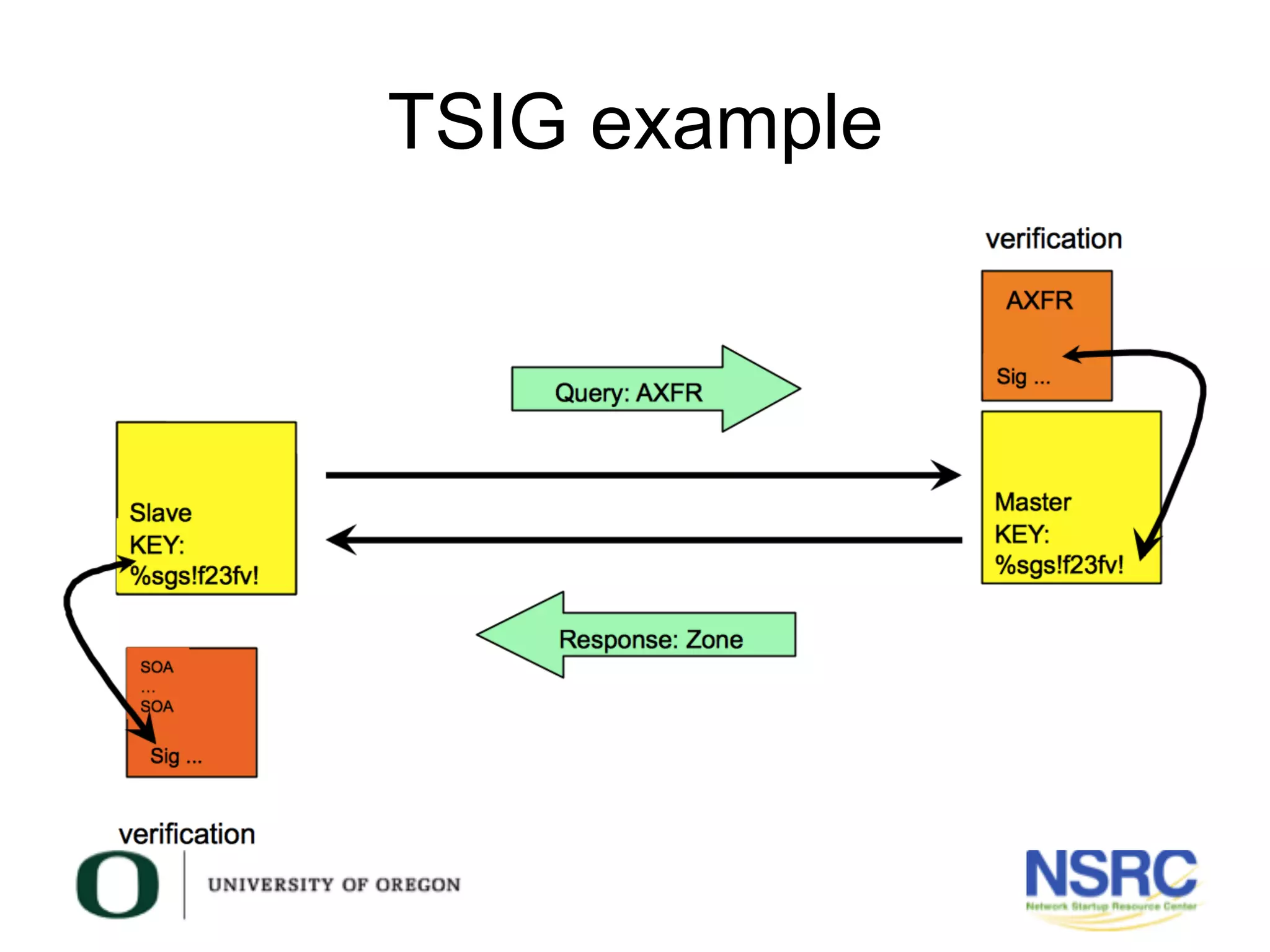
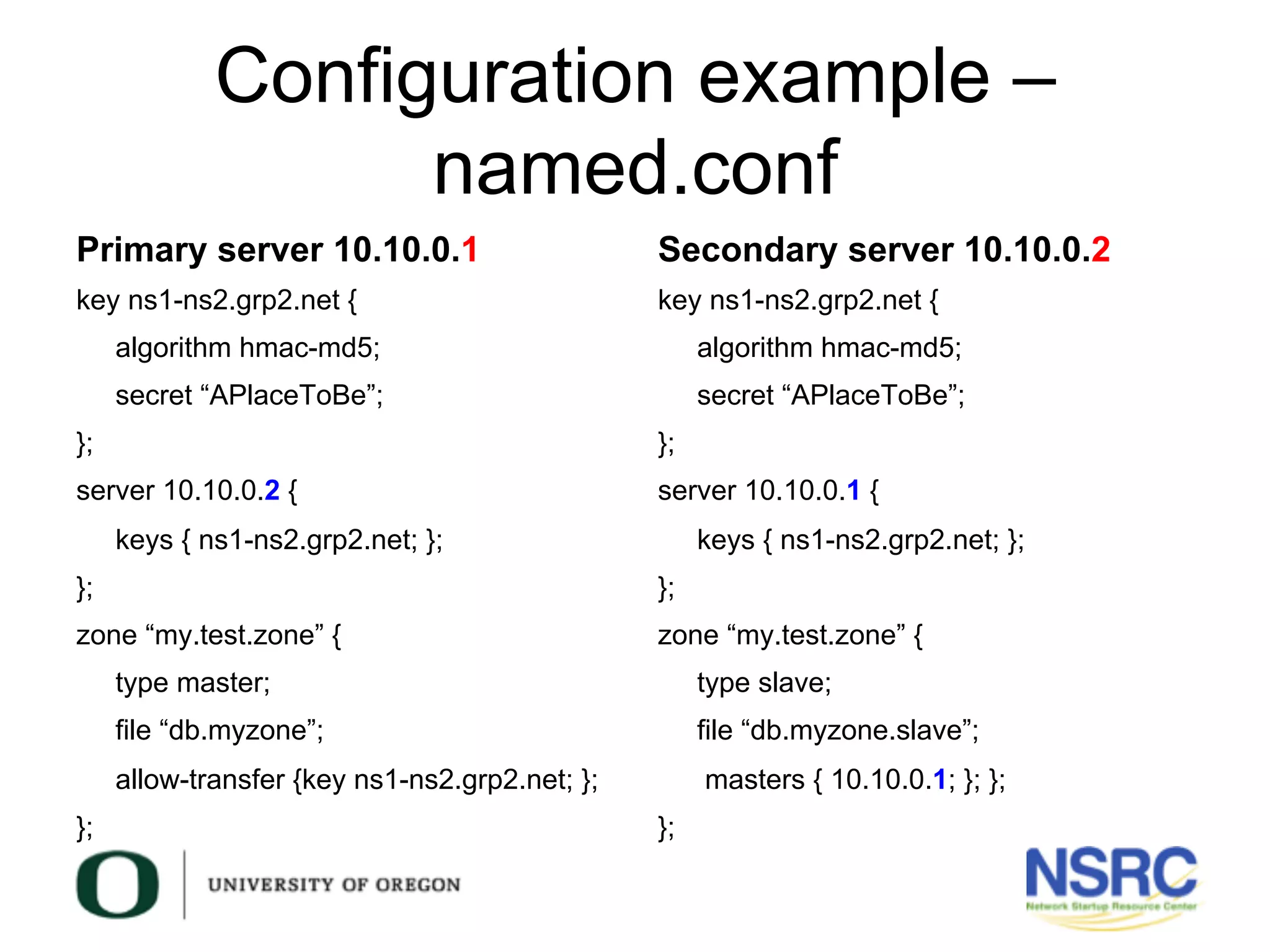
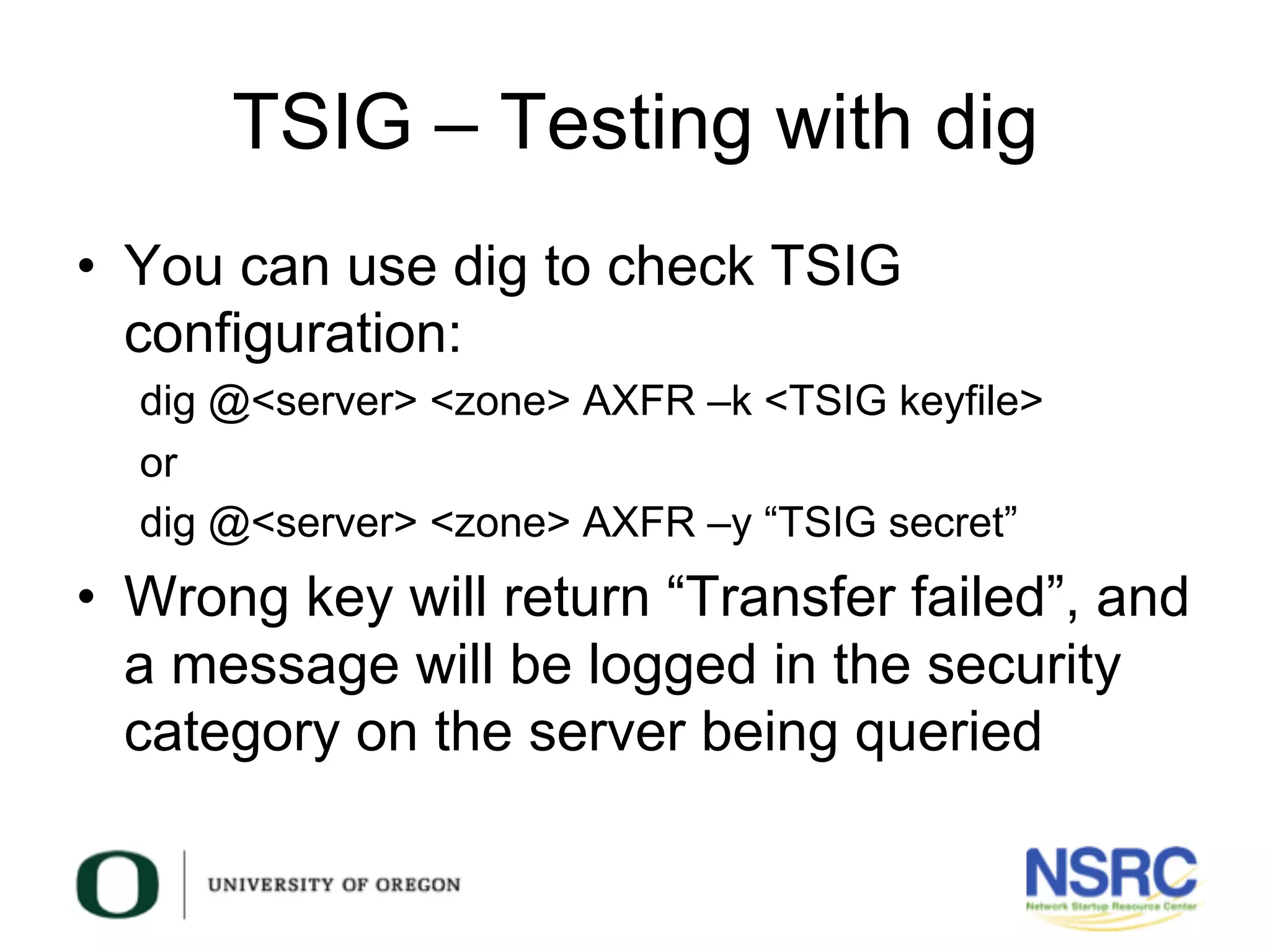
This document discusses TSIG (Transaction Signature), a security mechanism for protecting communication between DNS servers and clients by using a keyed-hash method. It covers the processes for generating TSIG secrets, configuring servers, and testing TSIG functionality, emphasizing the importance of synchronization for time-sensitive operations. The document also provides examples of configuring TSIG keys in DNS server settings and testing them using the dig command.