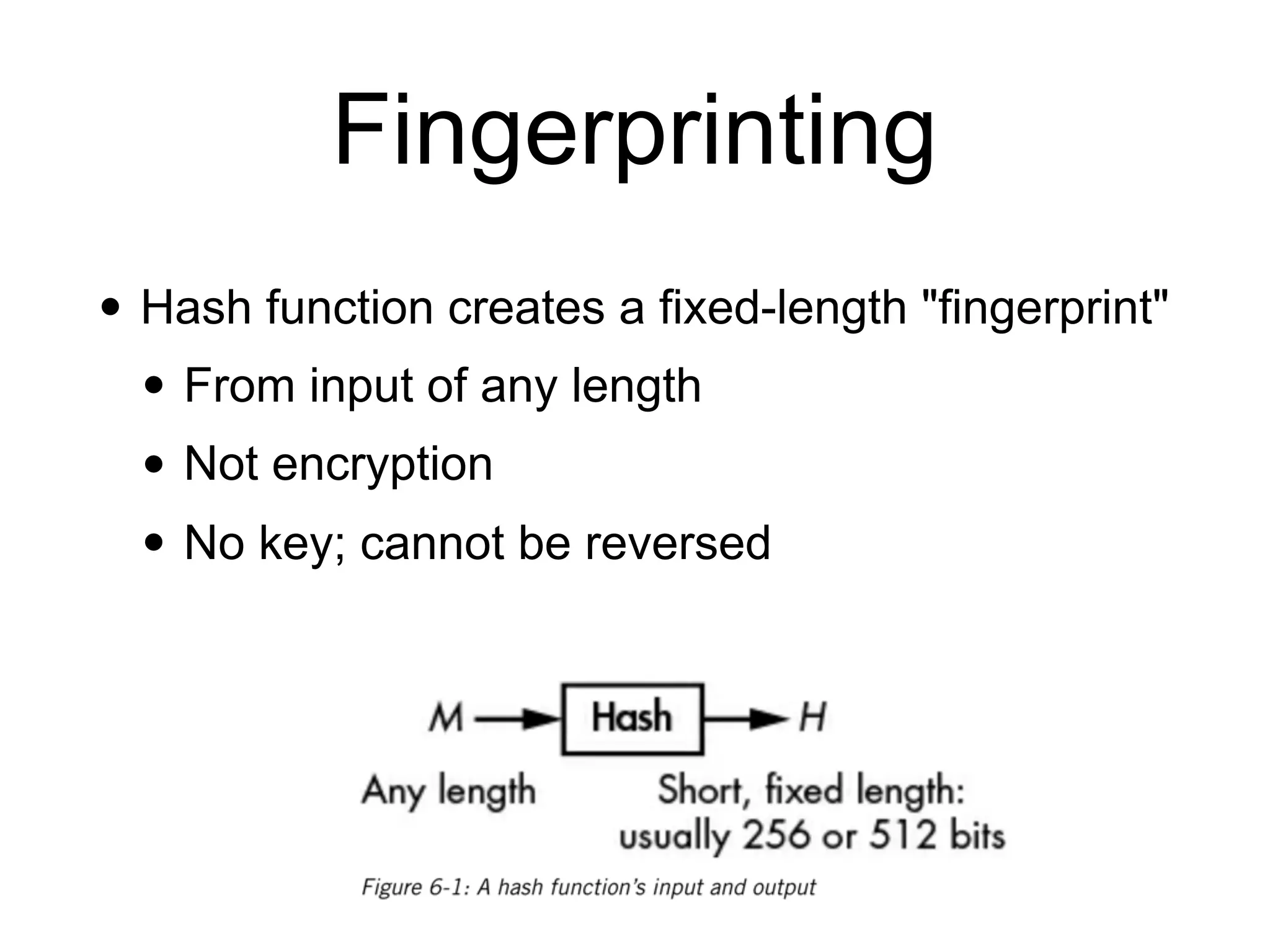
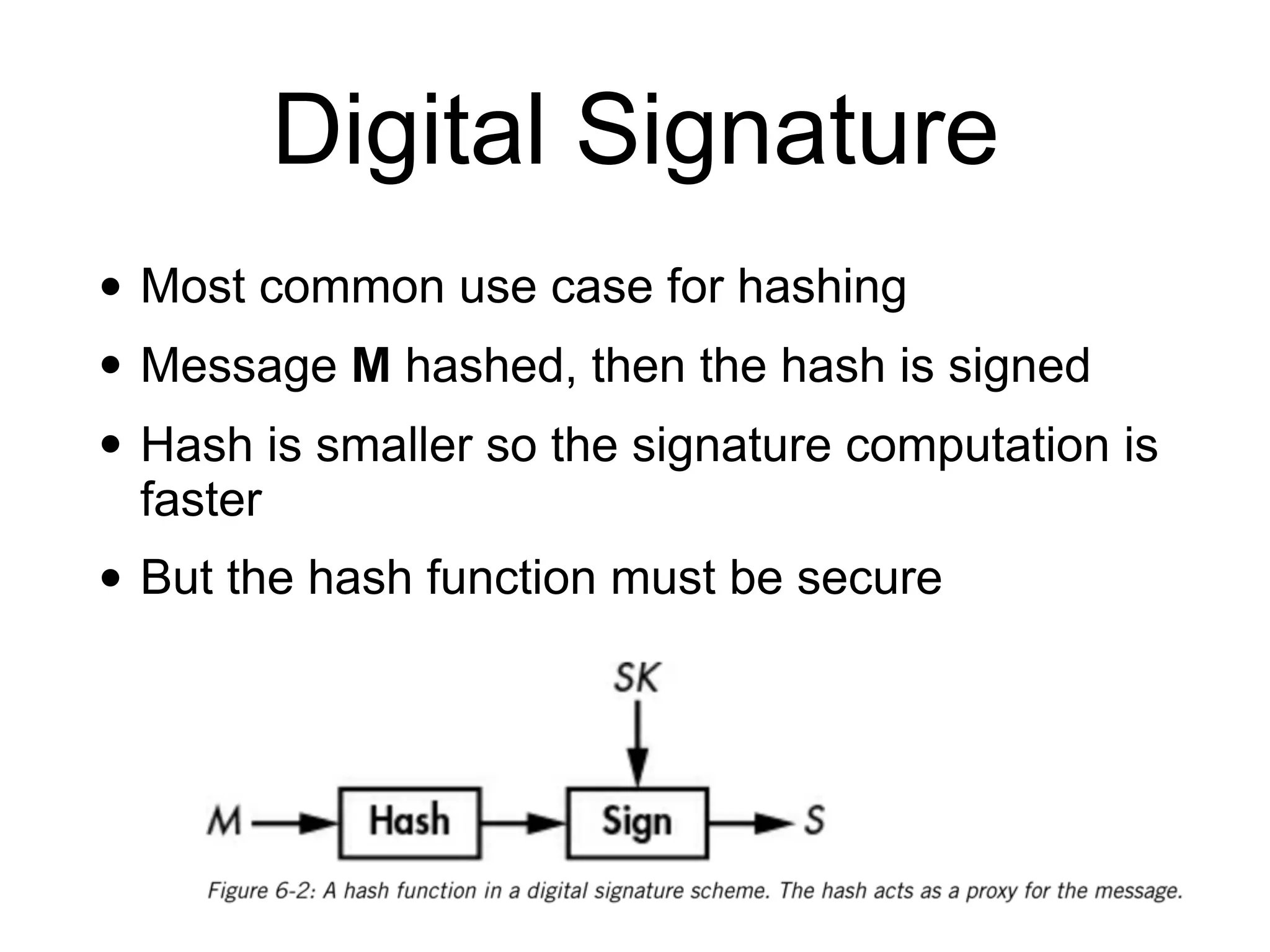
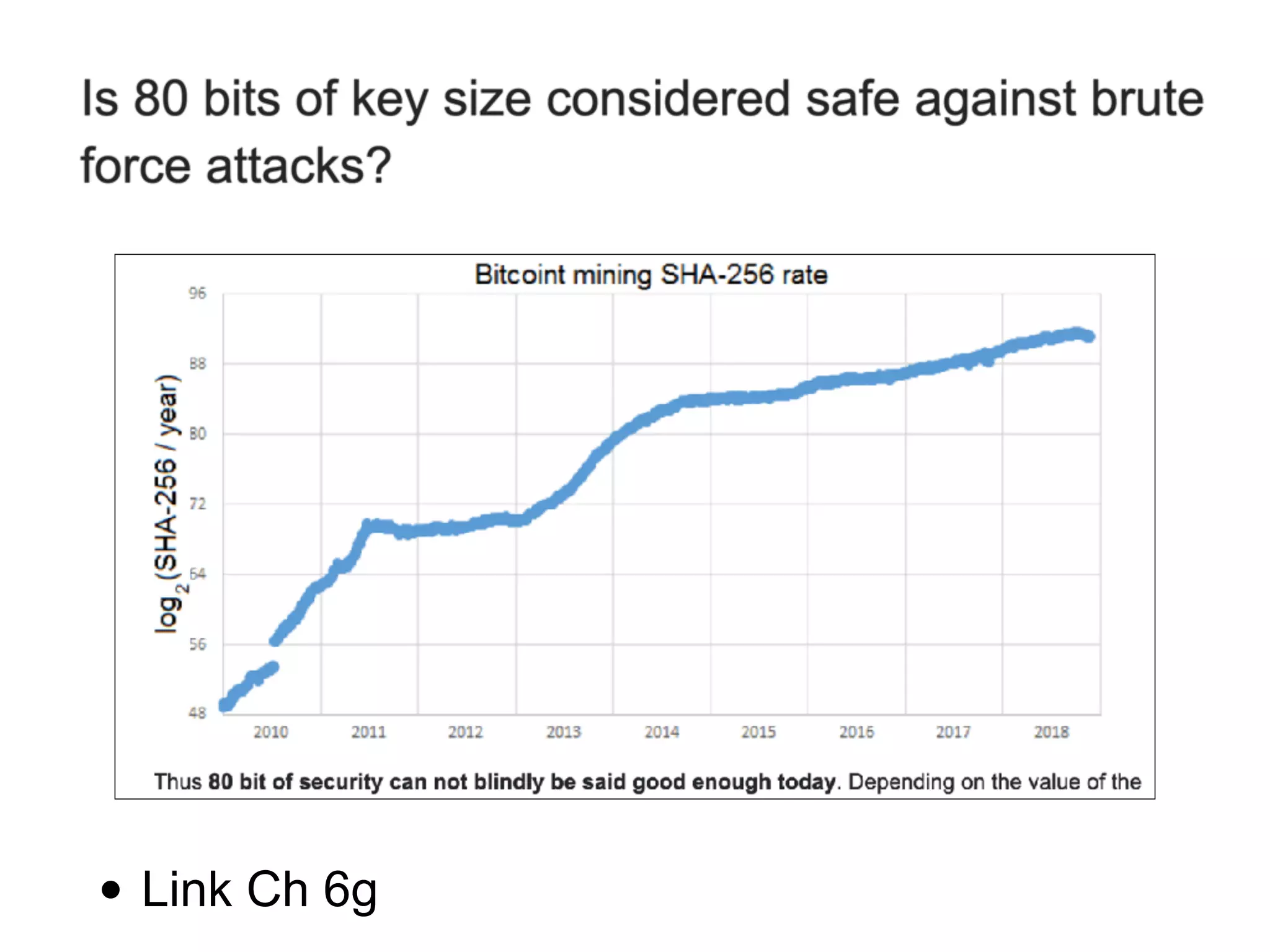
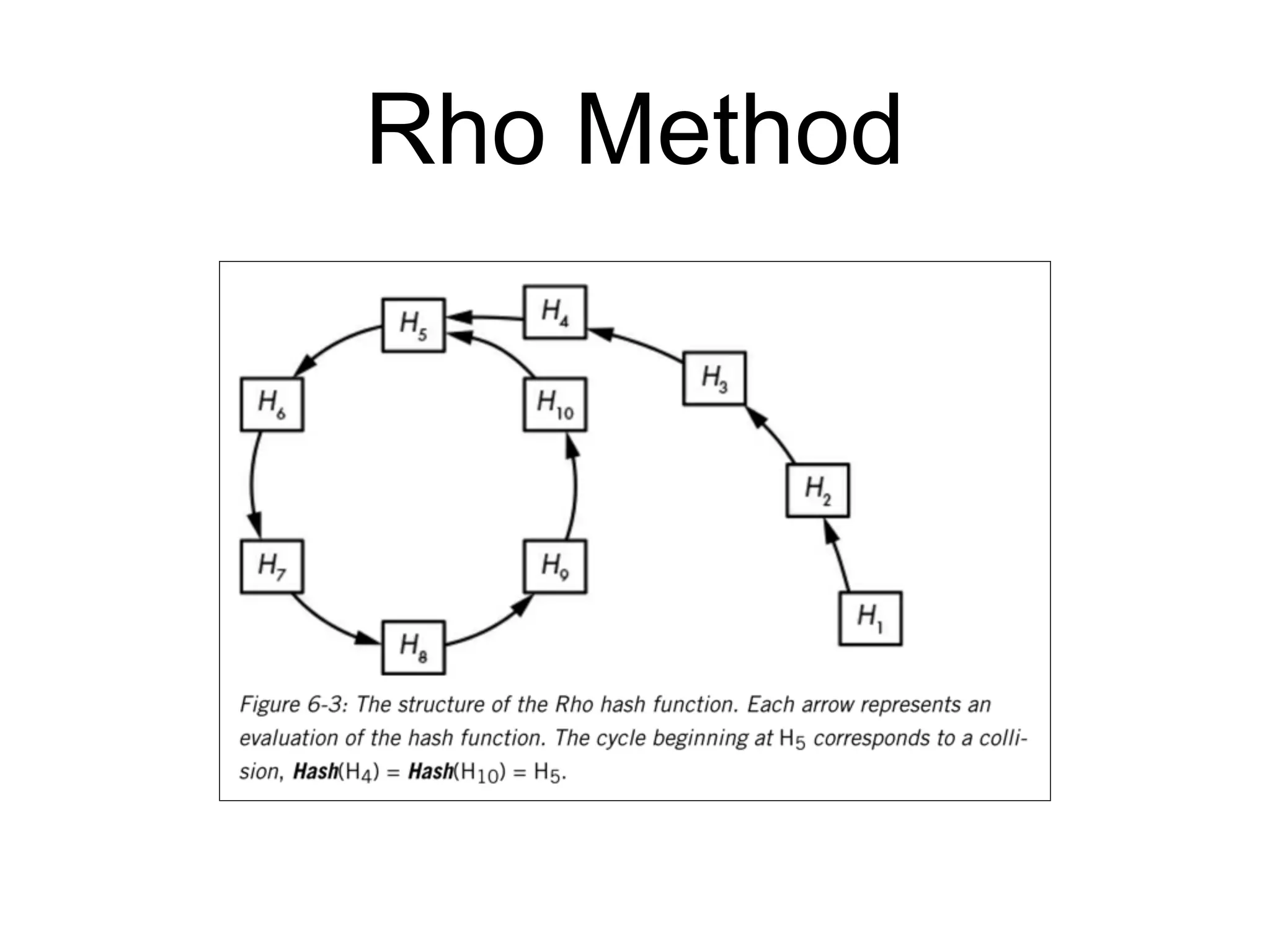
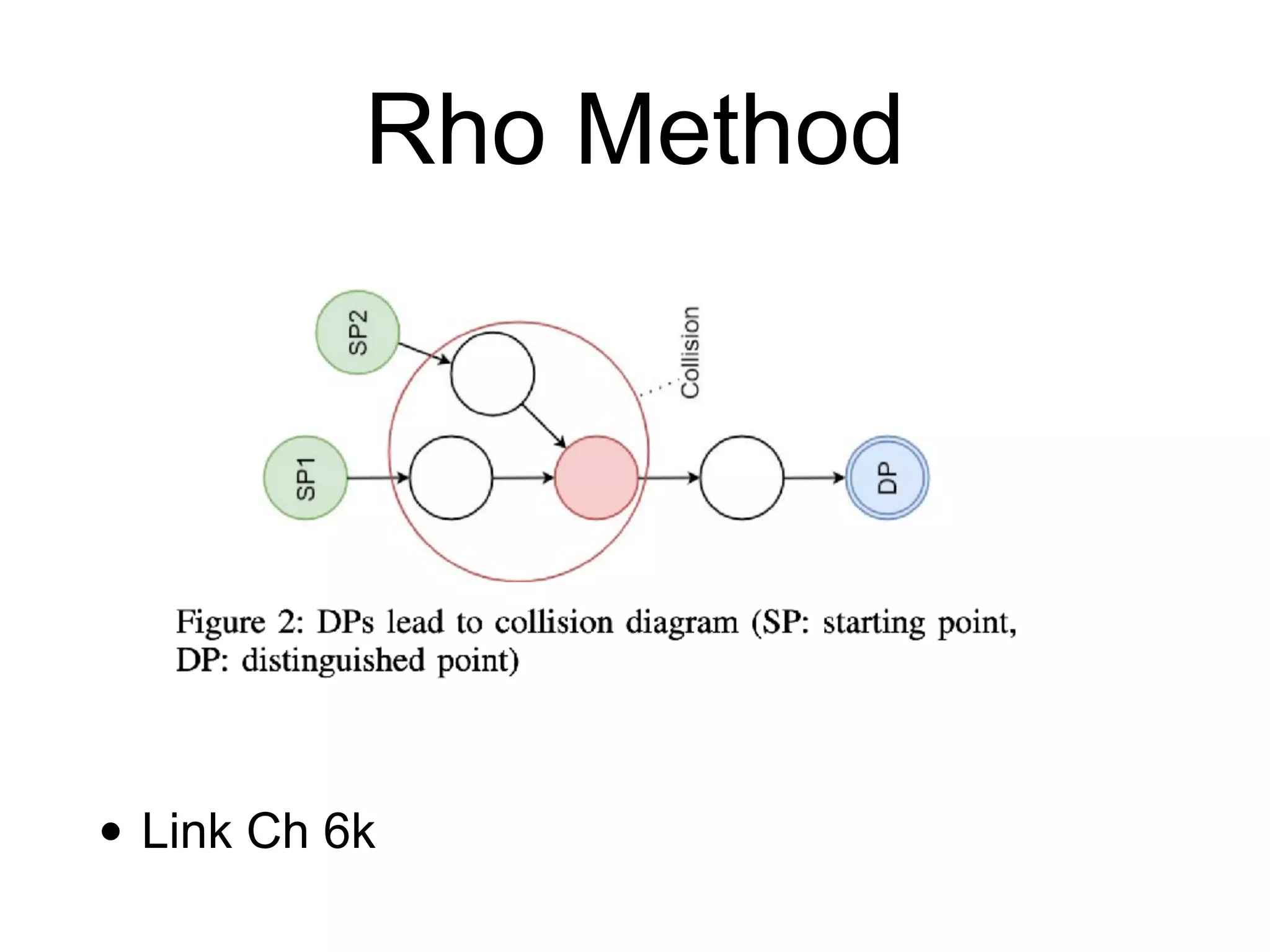
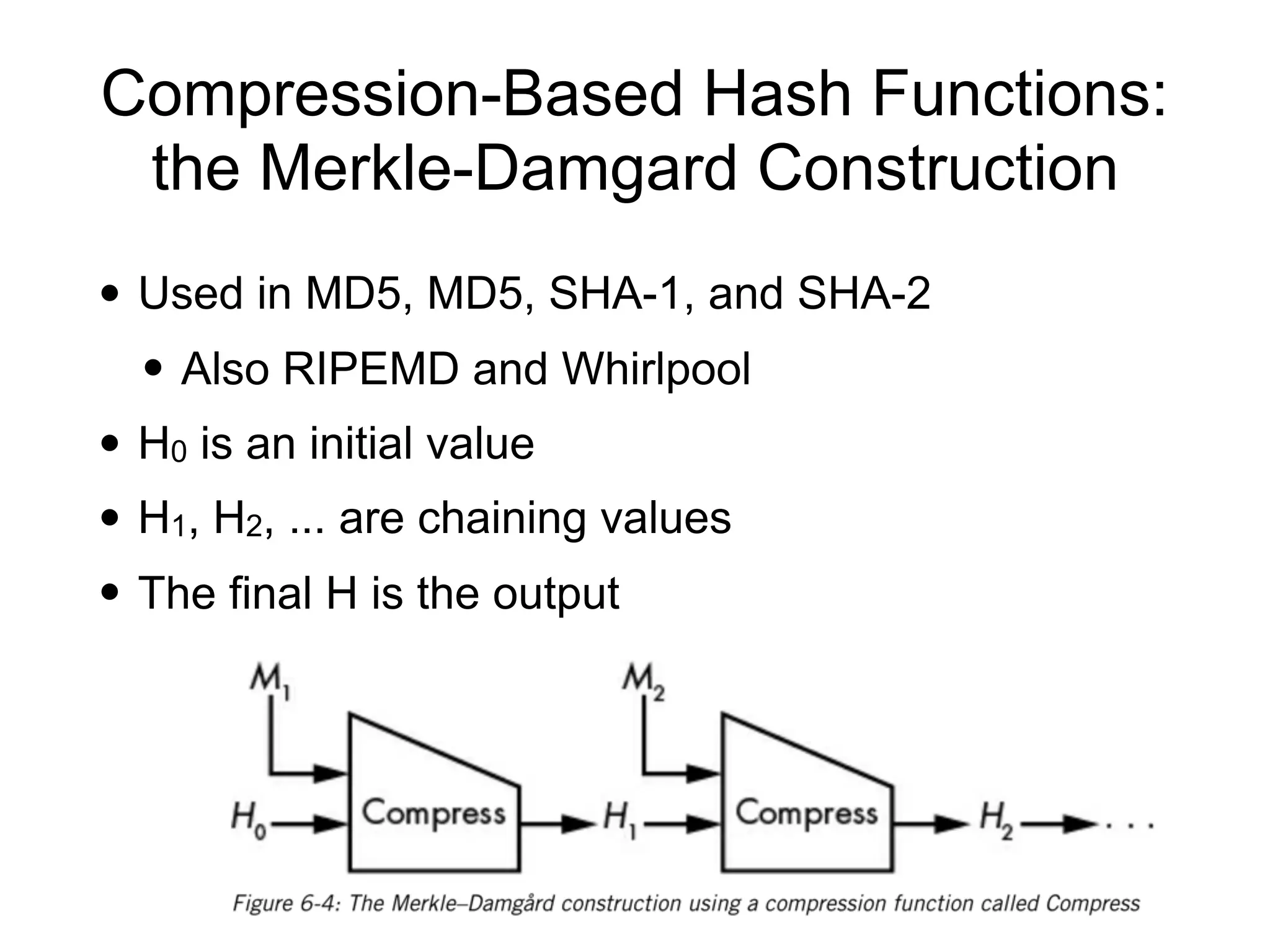
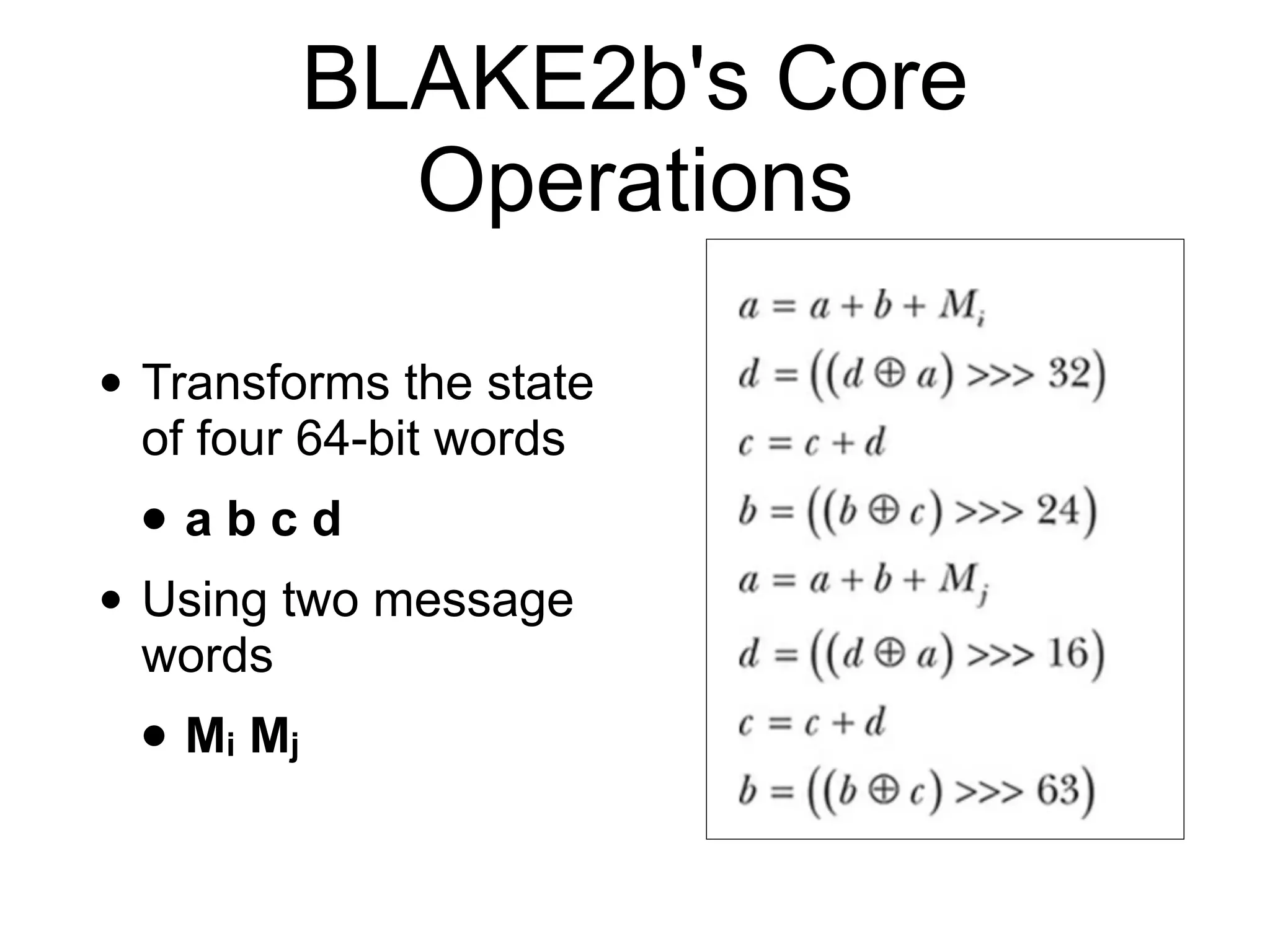
This document discusses hash functions and their uses in cryptography. It covers secure hash functions like SHA-1, SHA-2, SHA-3/Keccak, and BLAKE2. It describes how hash functions work, including properties like preimage and collision resistance. It also discusses attacks on hash functions like MD5 and SHA-1. Finally, it covers issues like length extension attacks and how hash functions can be misused or vulnerabilities exploited.