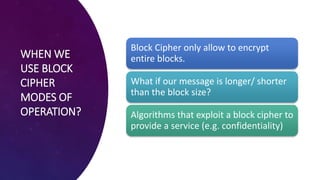
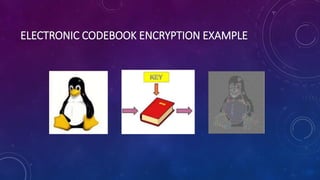
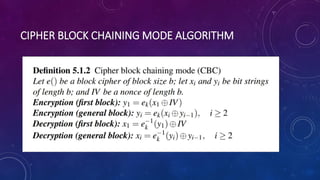
The document discusses block ciphers and their modes of operation, specifically focusing on Electronic Code Book (ECB) and Cipher Block Chaining (CBC) modes. ECB is described as a straightforward method where identical plaintext blocks produce identical cipher text, leading to potential security issues, while CBC enhances security by chaining blocks with an initialization vector. It highlights the importance of not reusing initialization vectors to maintain encryption integrity.