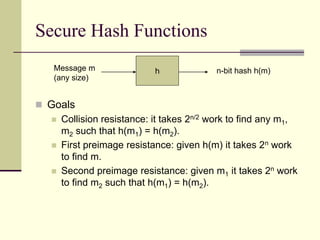
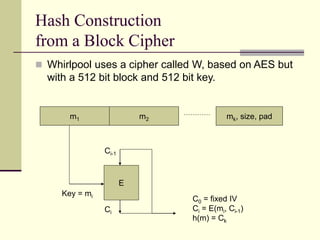
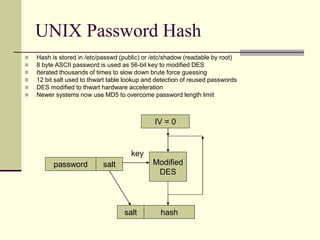
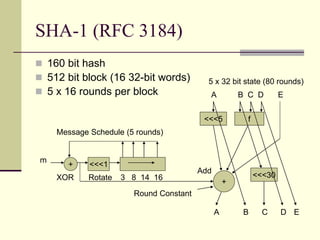
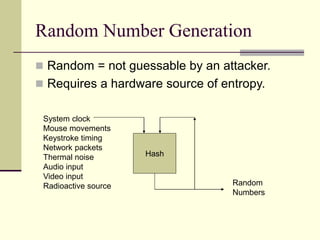
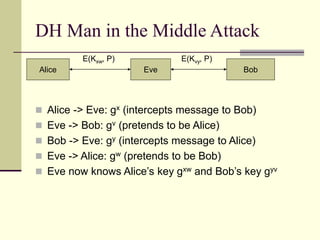
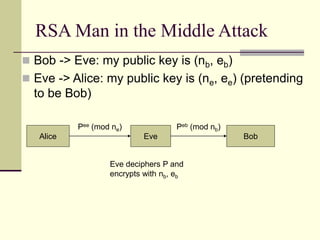
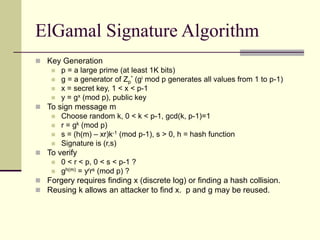
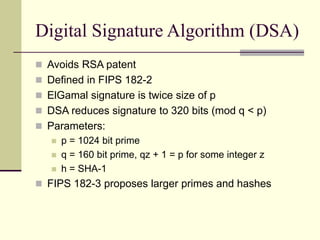
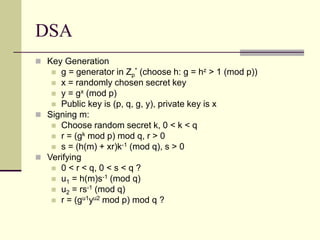
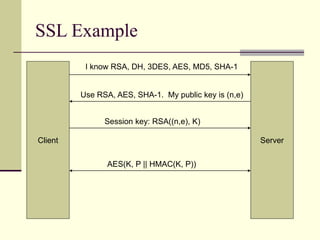
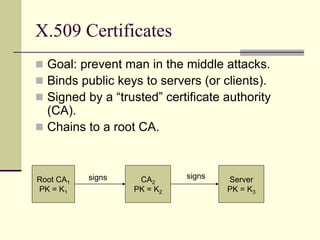
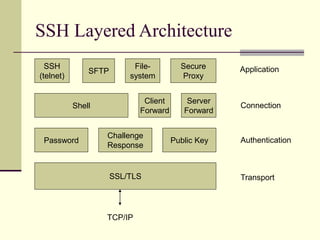
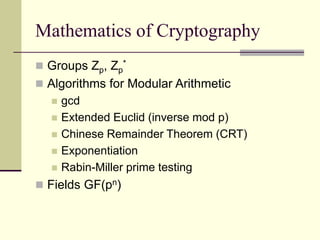
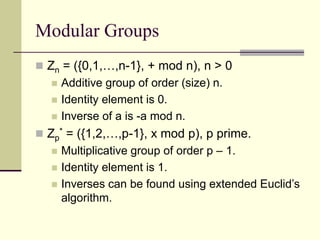
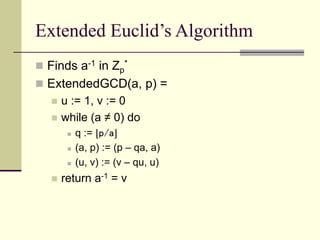
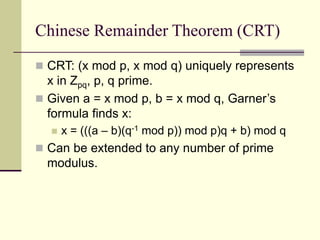
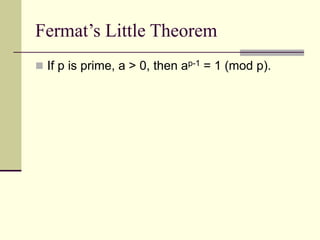
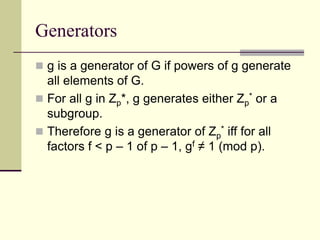
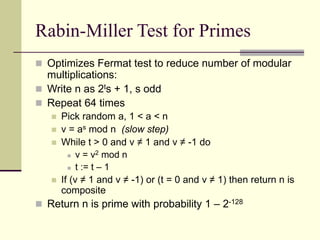
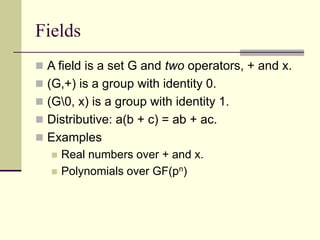
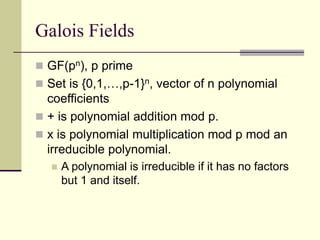
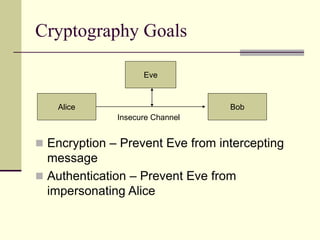
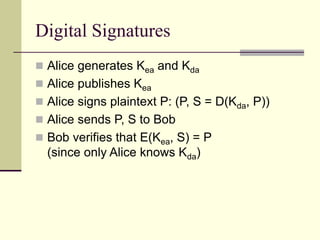
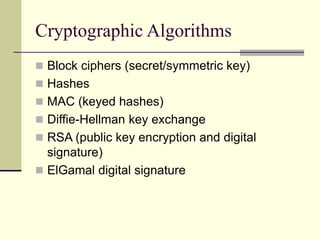
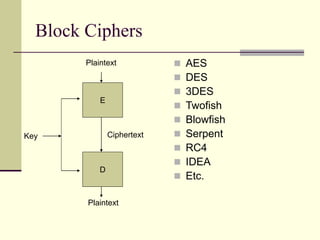
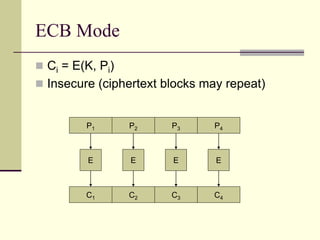
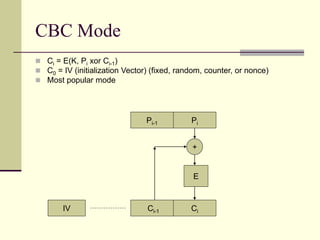
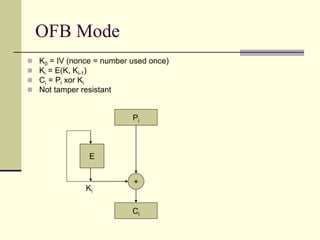
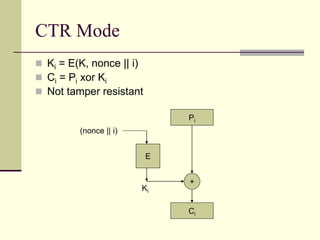
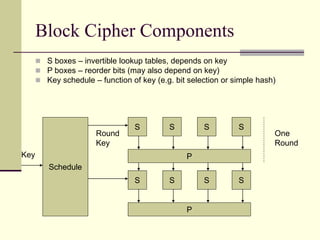
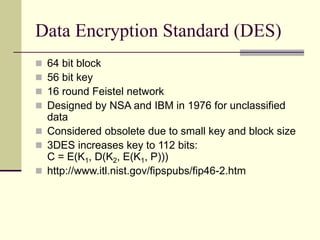
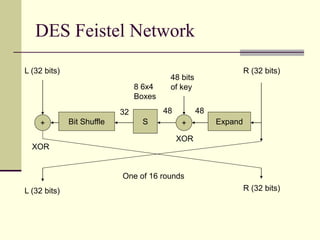
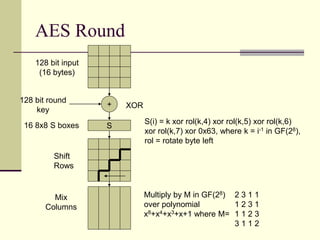
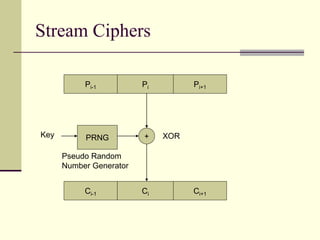
This document provides an introduction to cryptography. It defines key terms like cryptography, cryptanalysis, and cryptology. It describes the goals of encryption and authentication. It explains symmetric key cryptography where a shared secret key is used for both encryption and decryption. It also covers public key cryptography using key pairs, digital signatures to provide authentication, and how public key encryption and signatures can be combined. It discusses cryptographic attacks and the importance of Kerckhoffs' principle. It provides an overview of common cryptographic algorithms like block ciphers, stream ciphers, hash functions, and key exchange methods. It also discusses concepts like encryption modes, password hashing, random number generation, and the security of algorithms like RSA and Diffie-











![RC4 Stream Cipher
Key Schedule
for i from 0 to 255 S[i] := i
j := 0
for i from 0 to 255
j := (j + S[i] + key[i mod keylength]) mod 256
swap(S[i],S[j])
Keystream Generation
i := 0, j := 0
while GeneratingOutput:
i := (i + 1) mod 256
j := (j + S[i]) mod 256
swap(S[i],S[j])
output S[(S[i] + S[j]) mod 256]](https://image.slidesharecdn.com/needed-240209211951-536dd21c/85/needed-ppt-26-320.jpg)