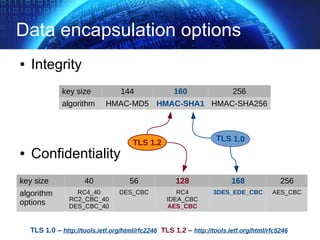
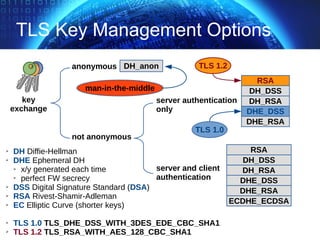
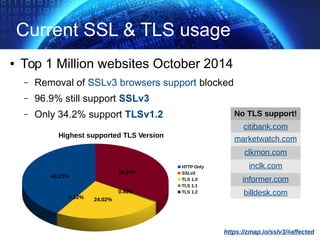
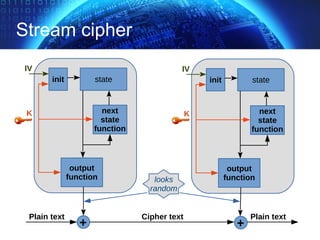
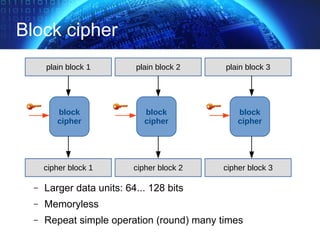
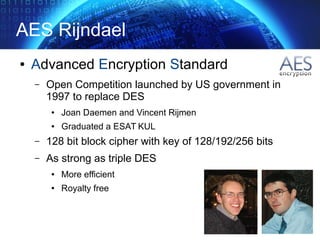
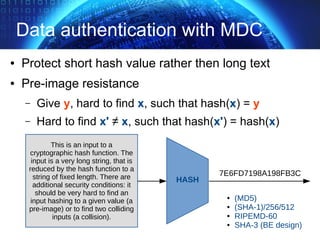
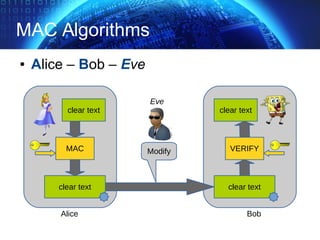
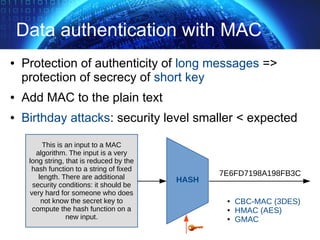
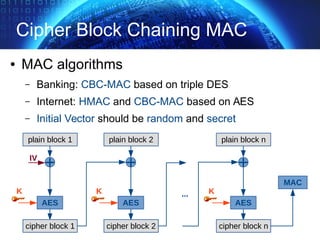
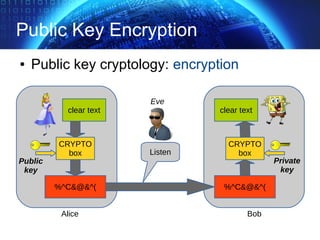
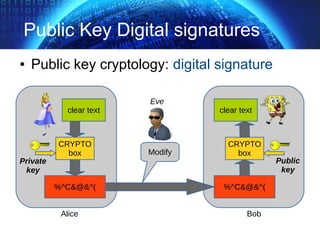
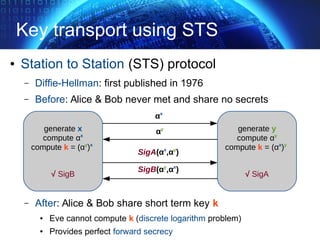
The document provides an extensive overview of cryptographic concepts, including cryptographic algorithms, entity authentication, and network security. It discusses various encryption methods, such as symmetric and public-key cryptography, along with the importance of data authentication and integrity. Additionally, it covers practical implementations and protocols for secure communications, emphasizing the critical role of secure key management and transport layer security.













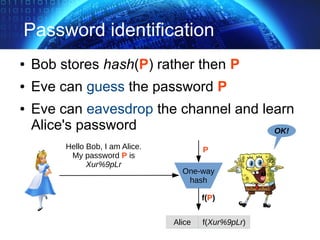
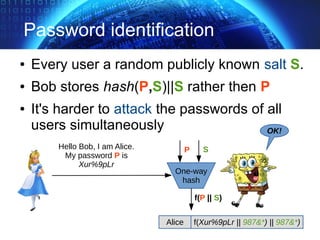





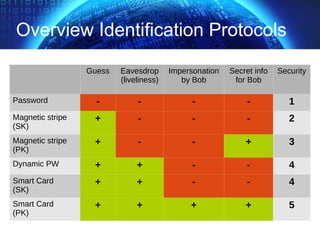


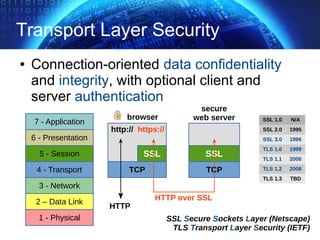
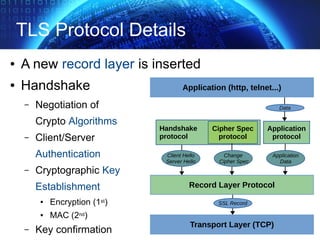
![TLS Handshake Overview
✔ start handshake, protocol version, algorithms
✔ authentication server + exchange (pre)master secret
✔ client authentication
✔ end handshake, integrity verification (*)
Hello Request
Server Hello
Certificate
Server Key Exchange
Certificate Request
Server Hello Done
[change cipher spec]
Finished
Client Hello
Certificate
Client Key Exchange
Certificate Verify
[change cipher spec]
Finished
CLIENT SERVER
MAC*
MAC*](https://image.slidesharecdn.com/allbitspresentation-securityintheory-150128185632-conversion-gate01/85/AllBits-presentation-Security-in-Theory-39-320.jpg)