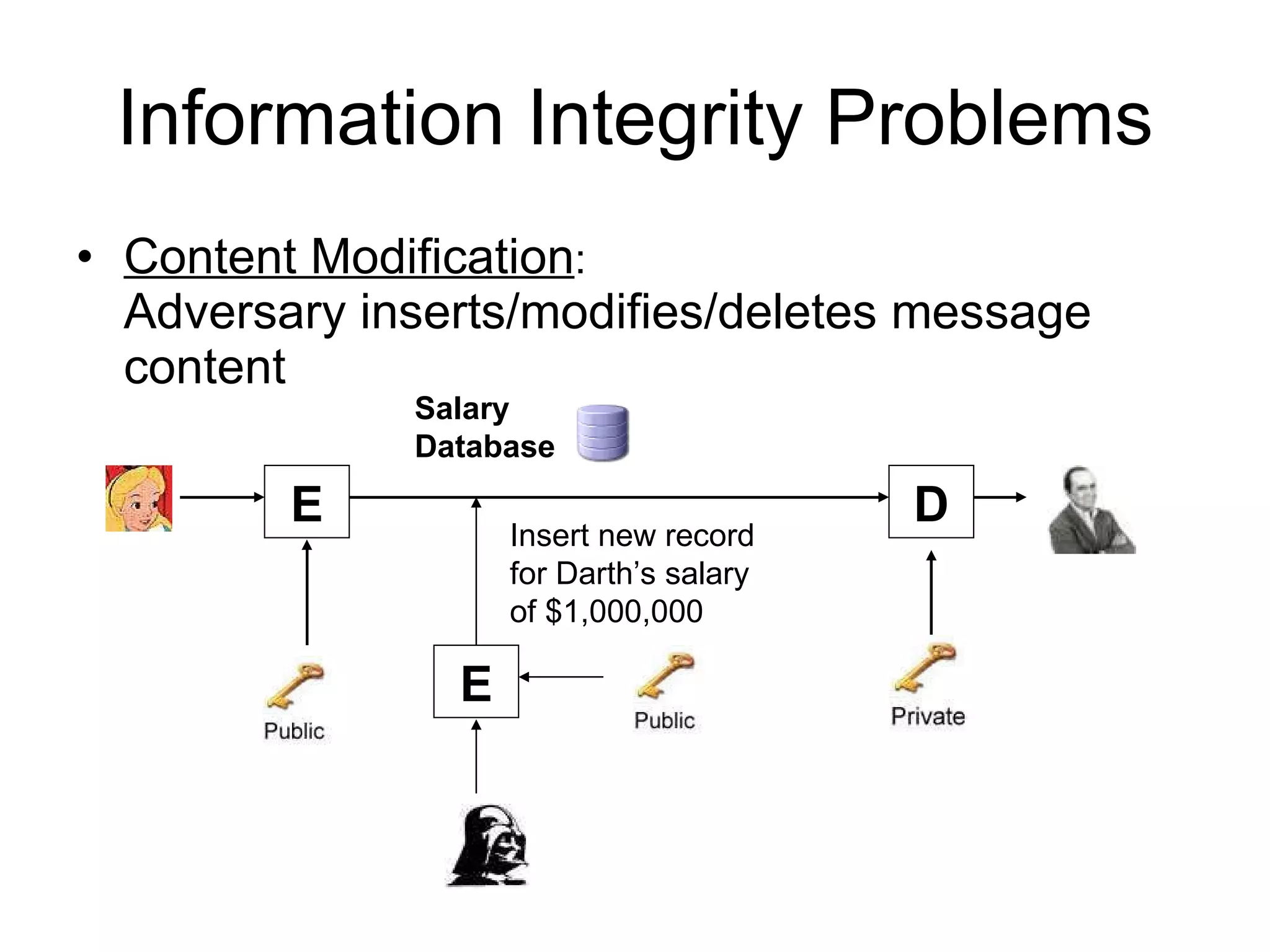
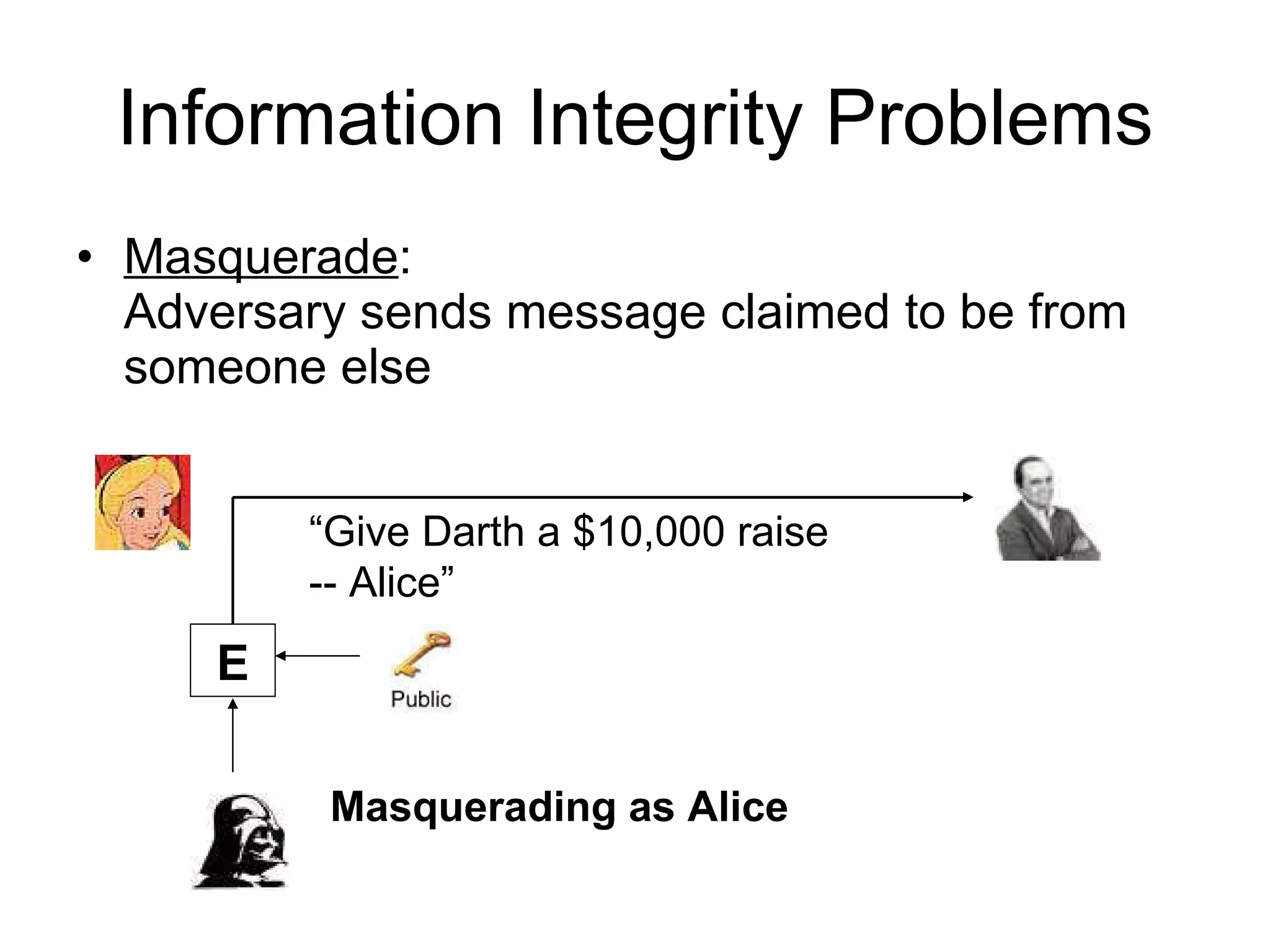
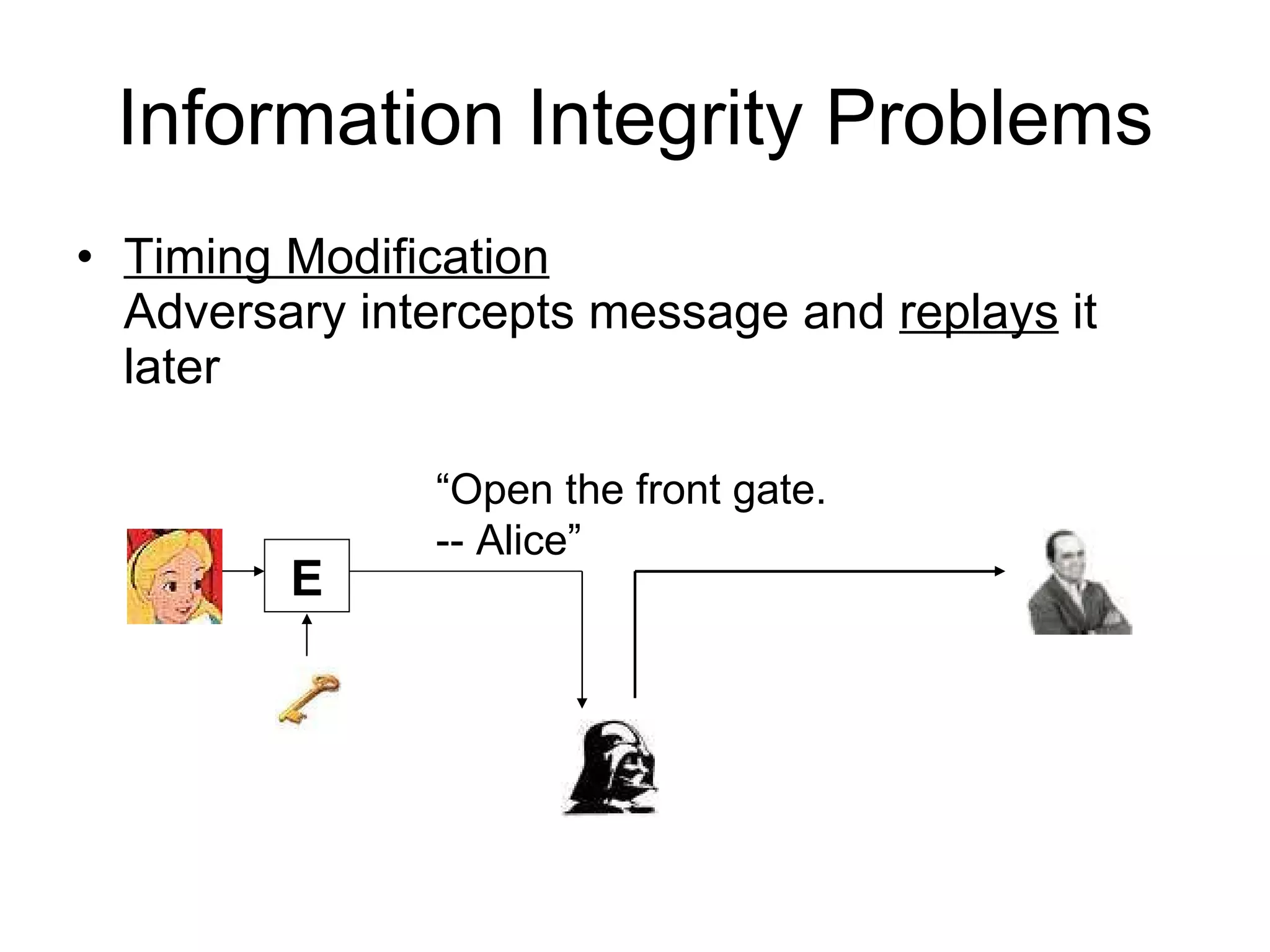
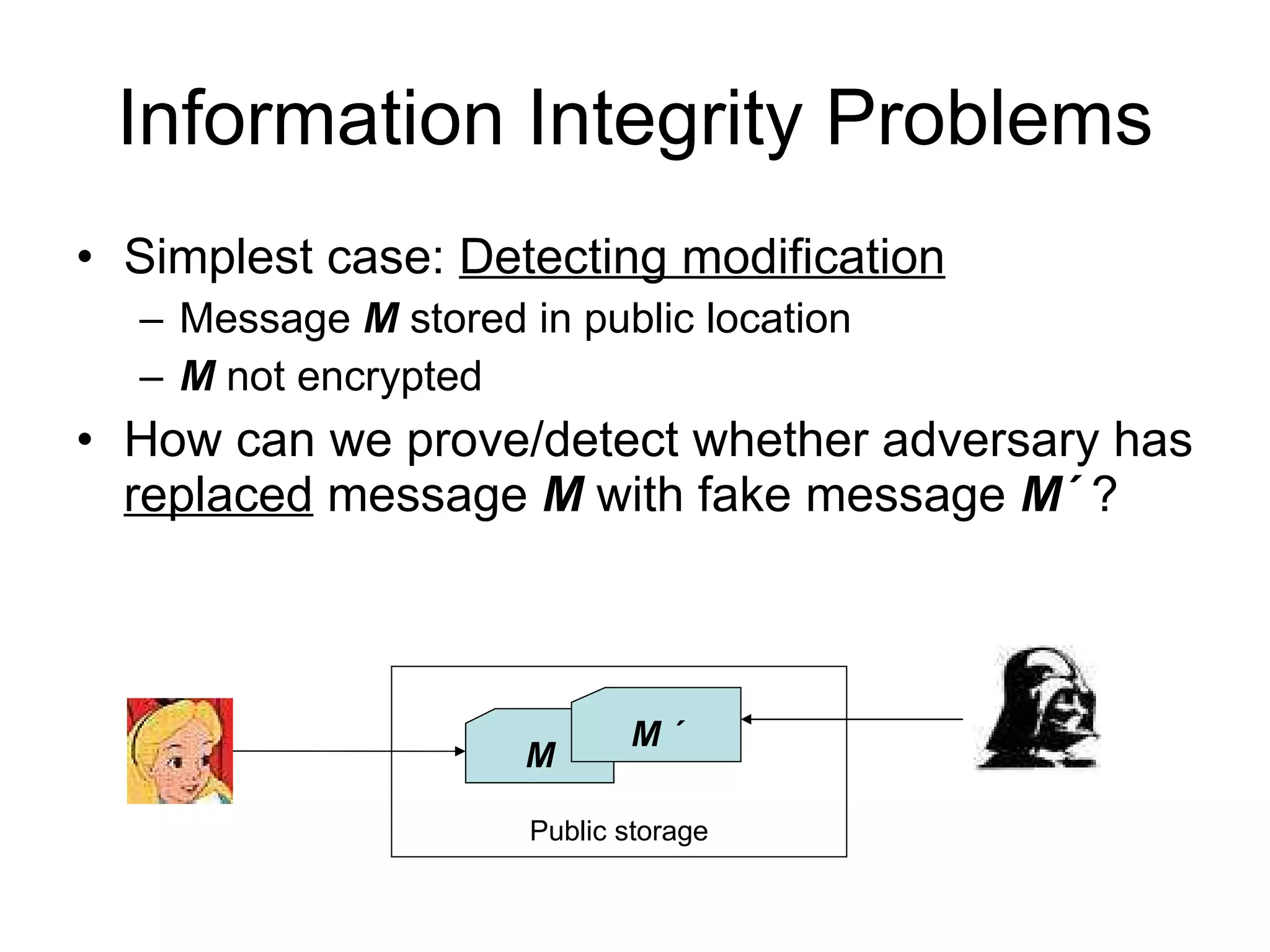
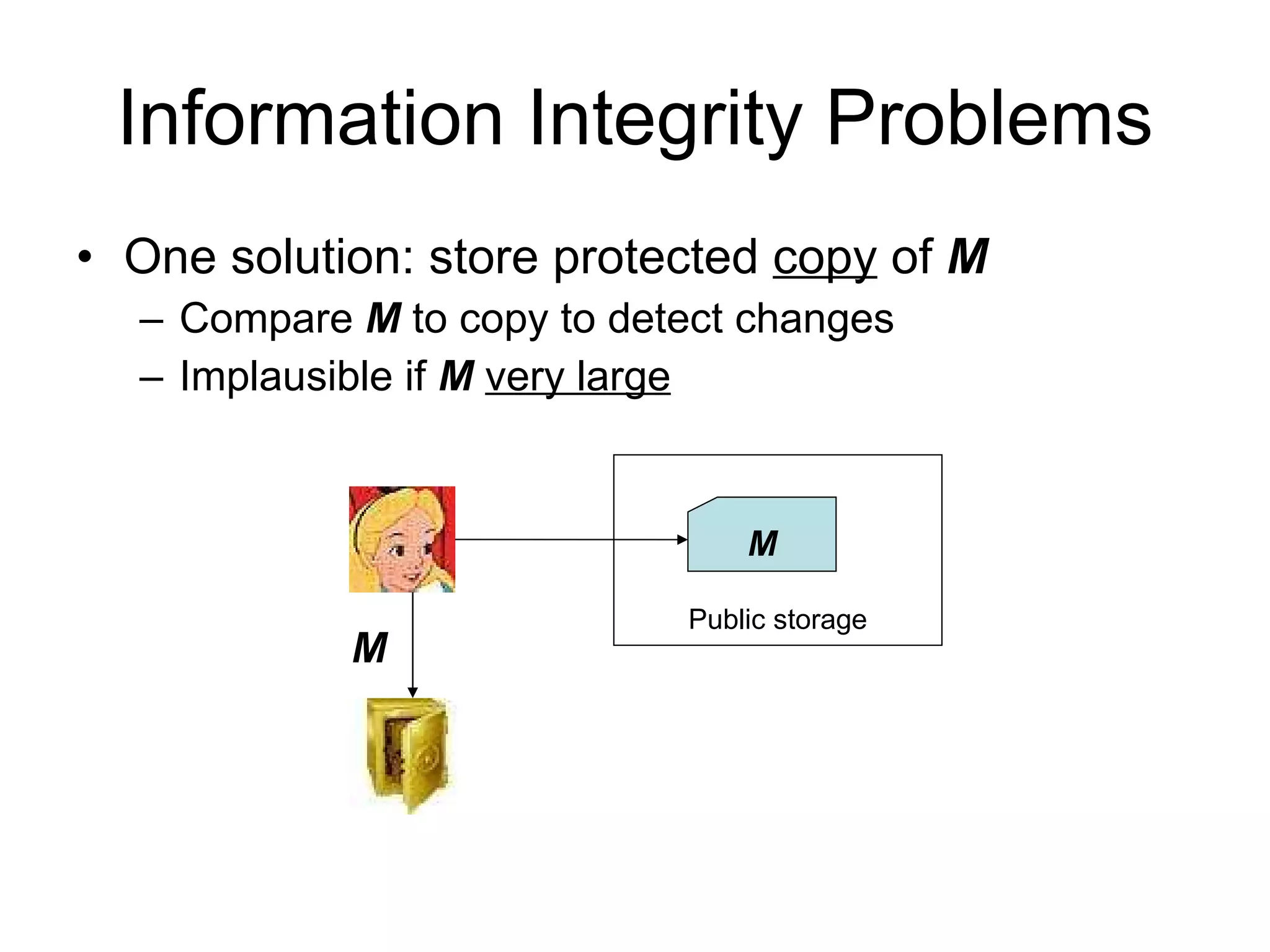
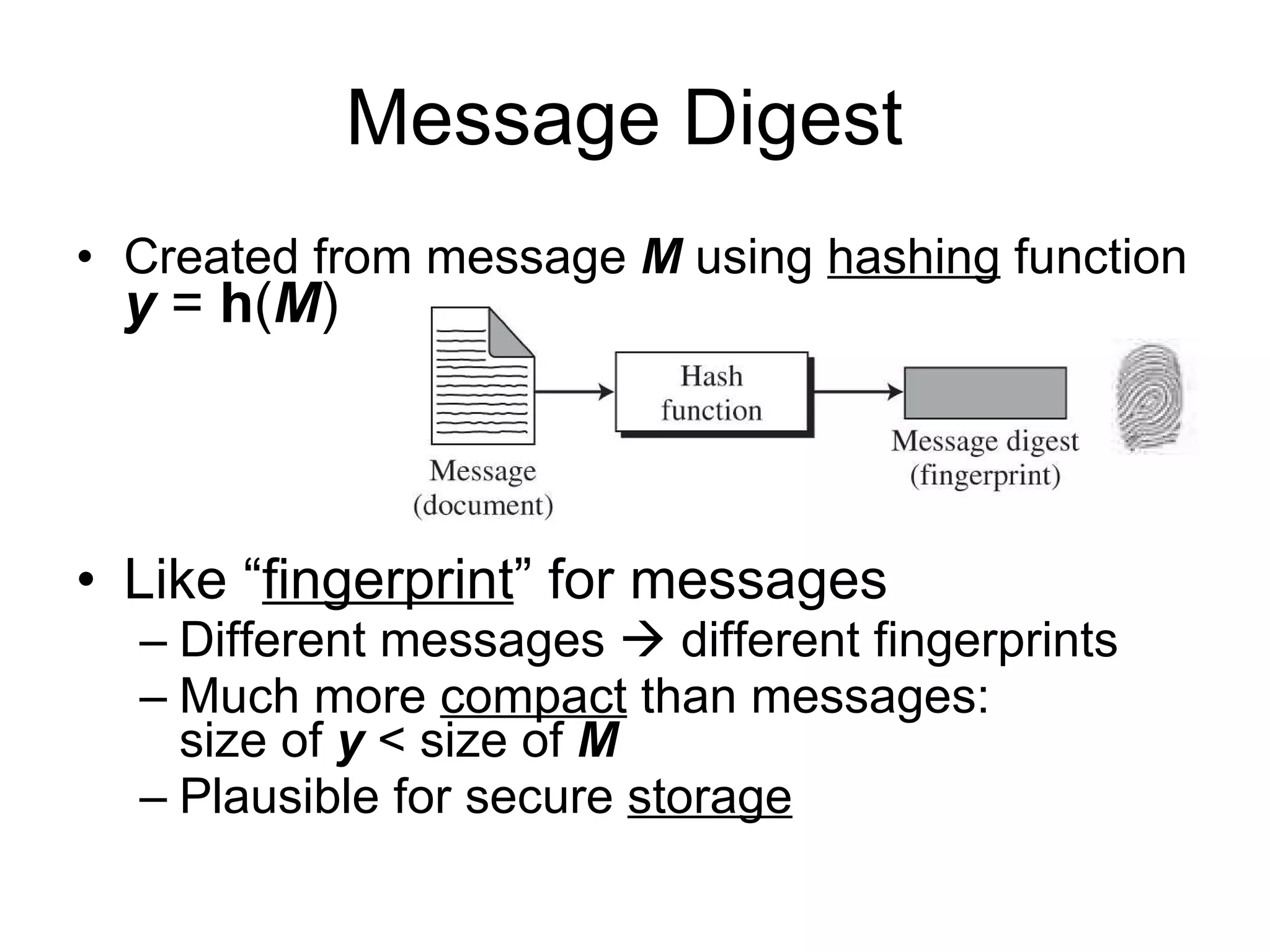
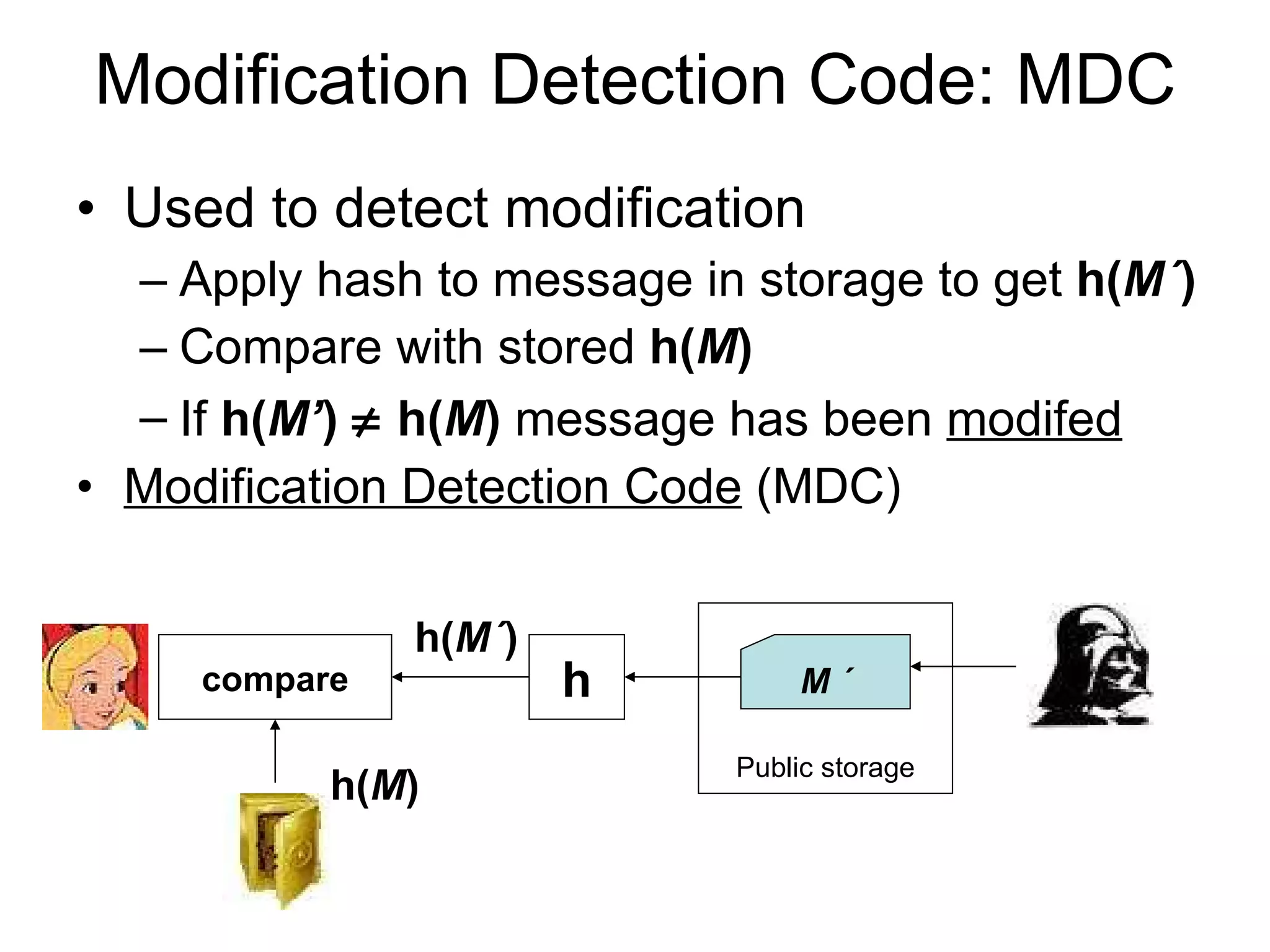
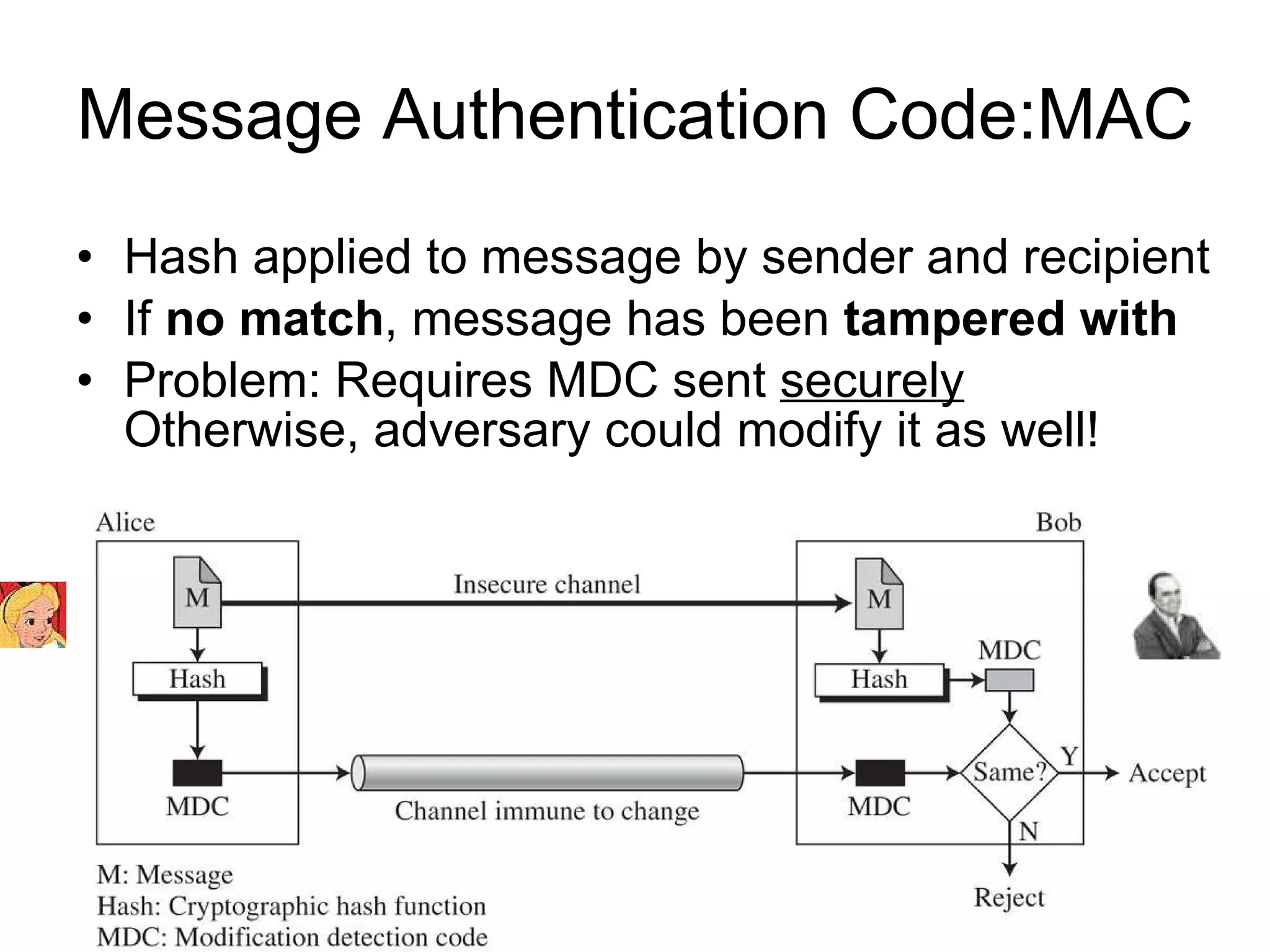
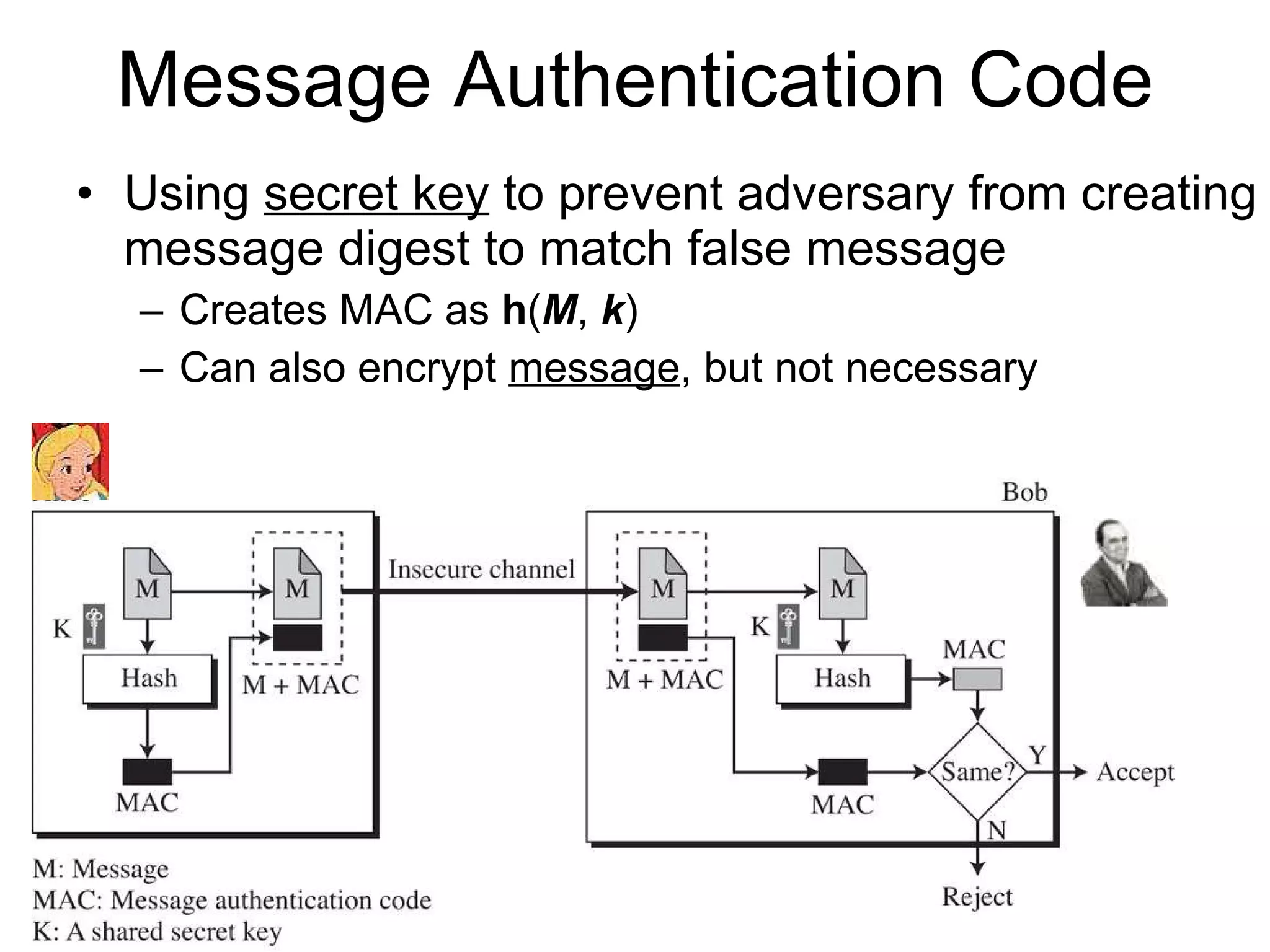
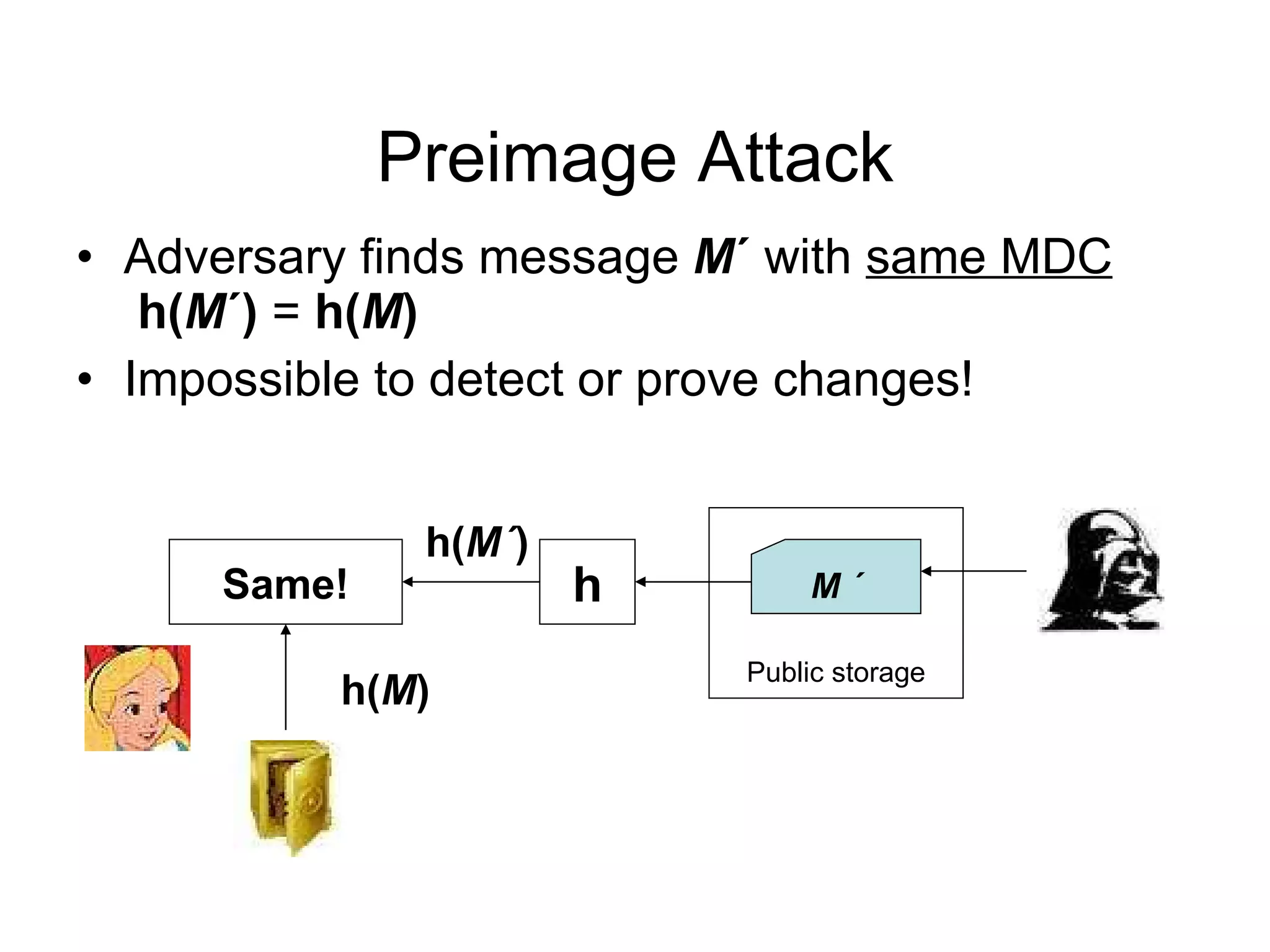
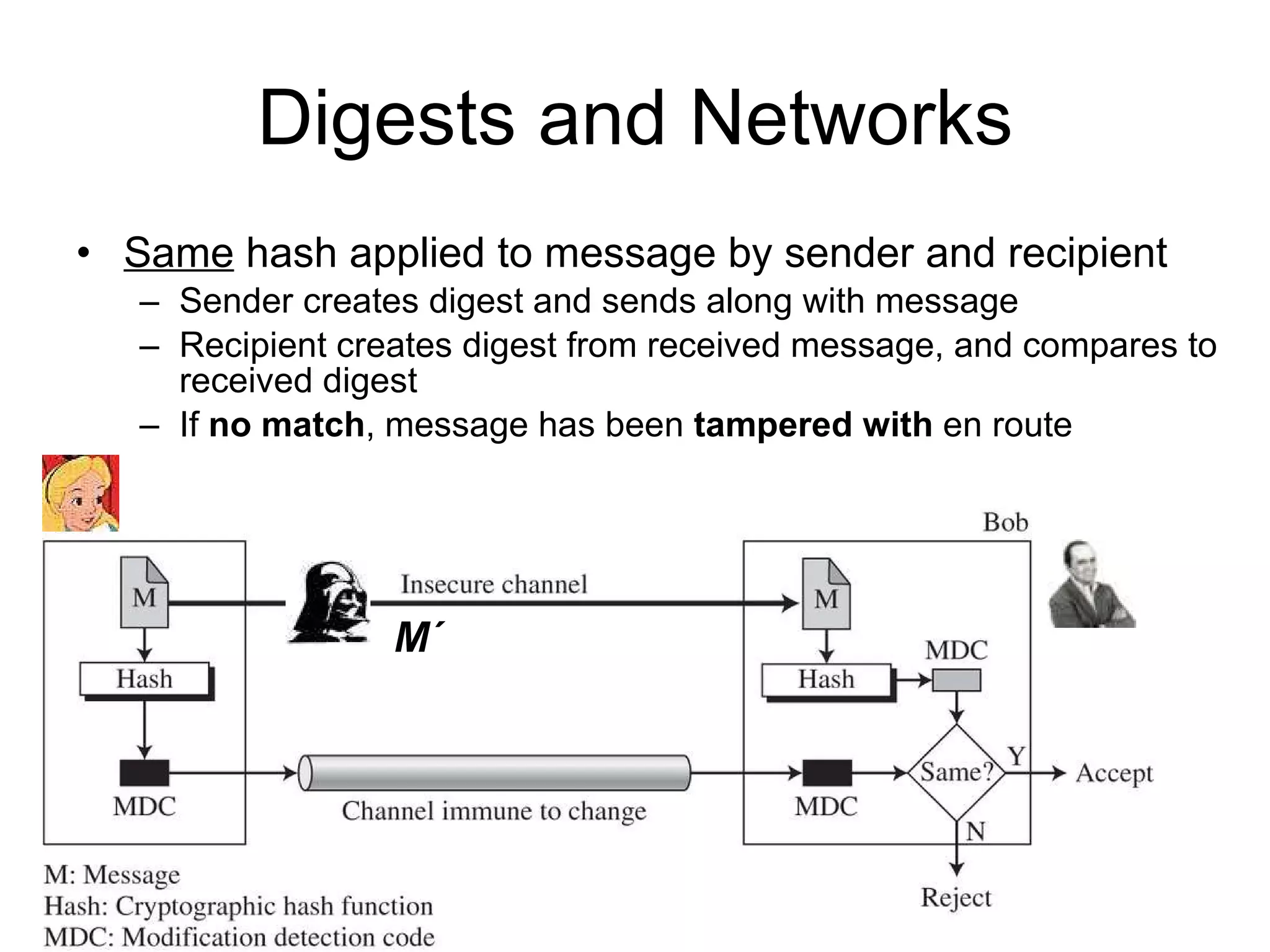
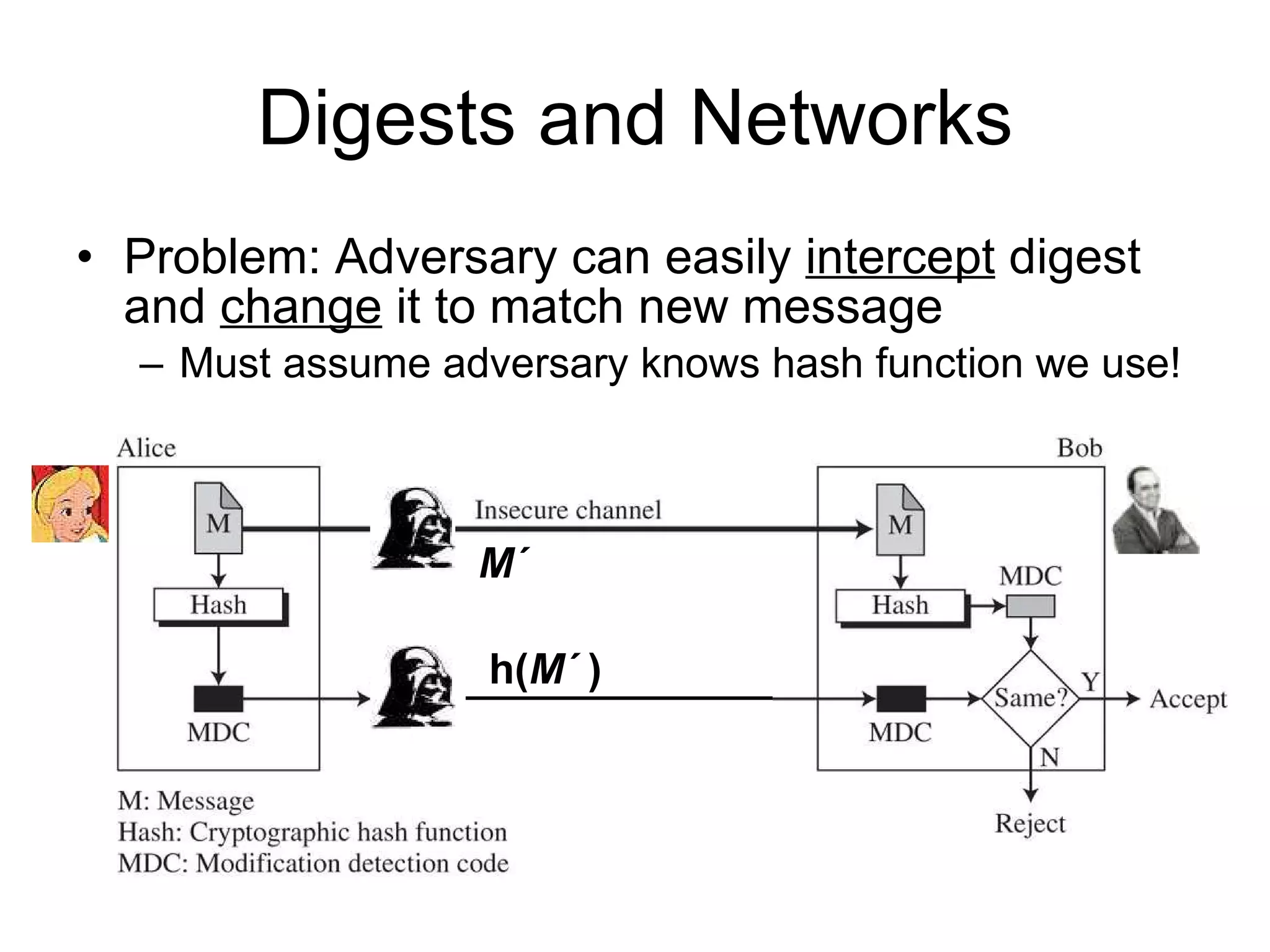
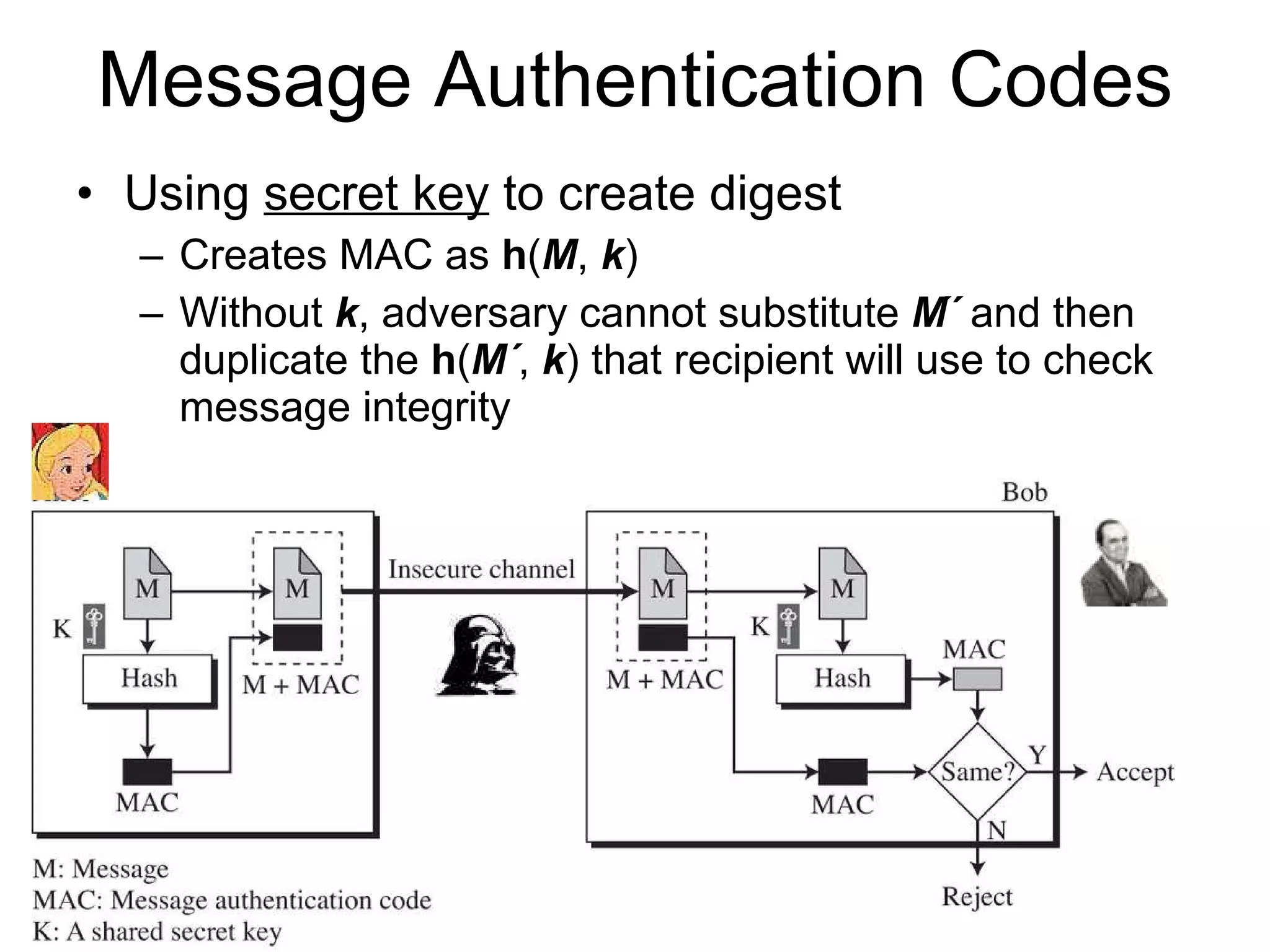
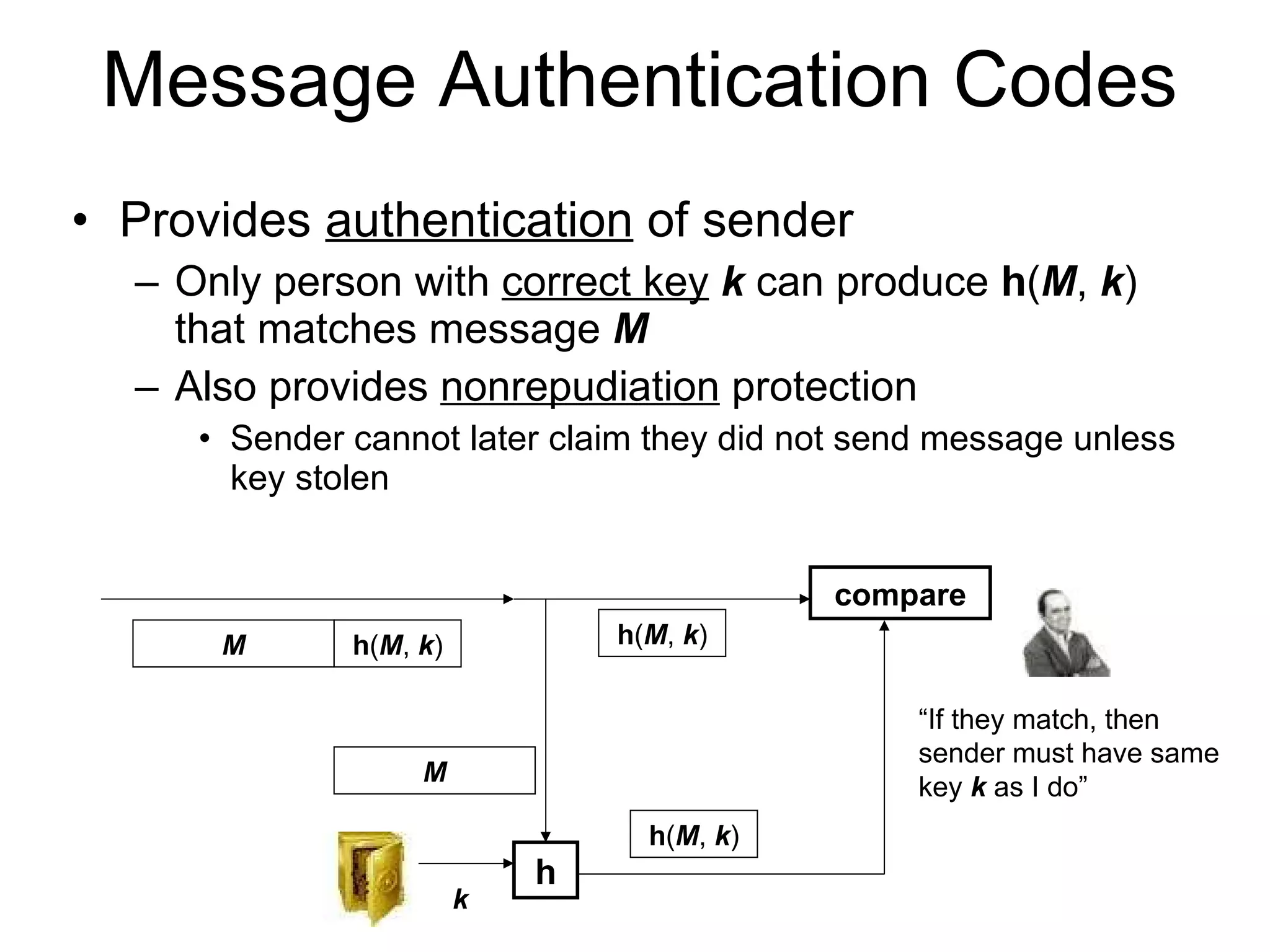
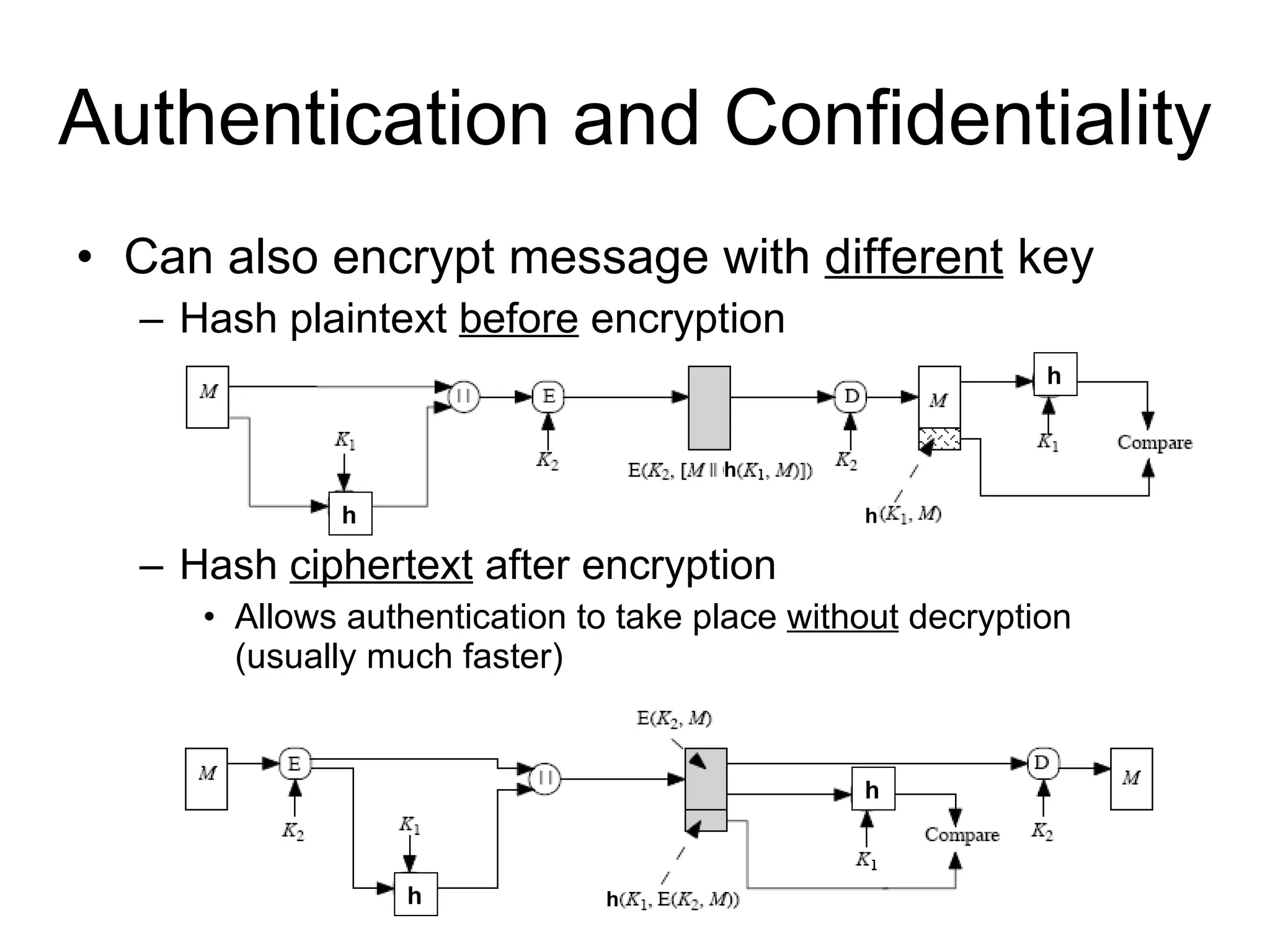
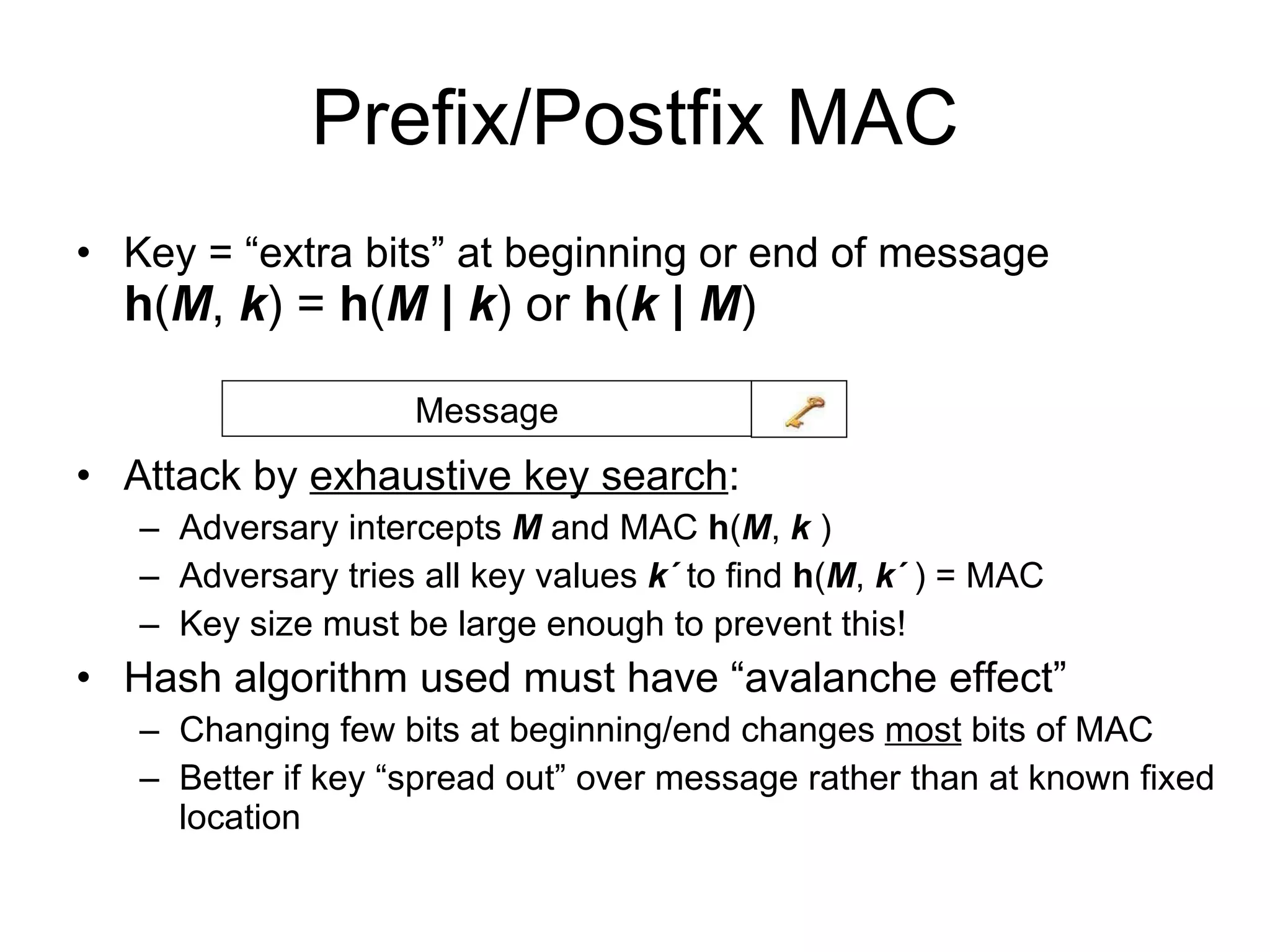
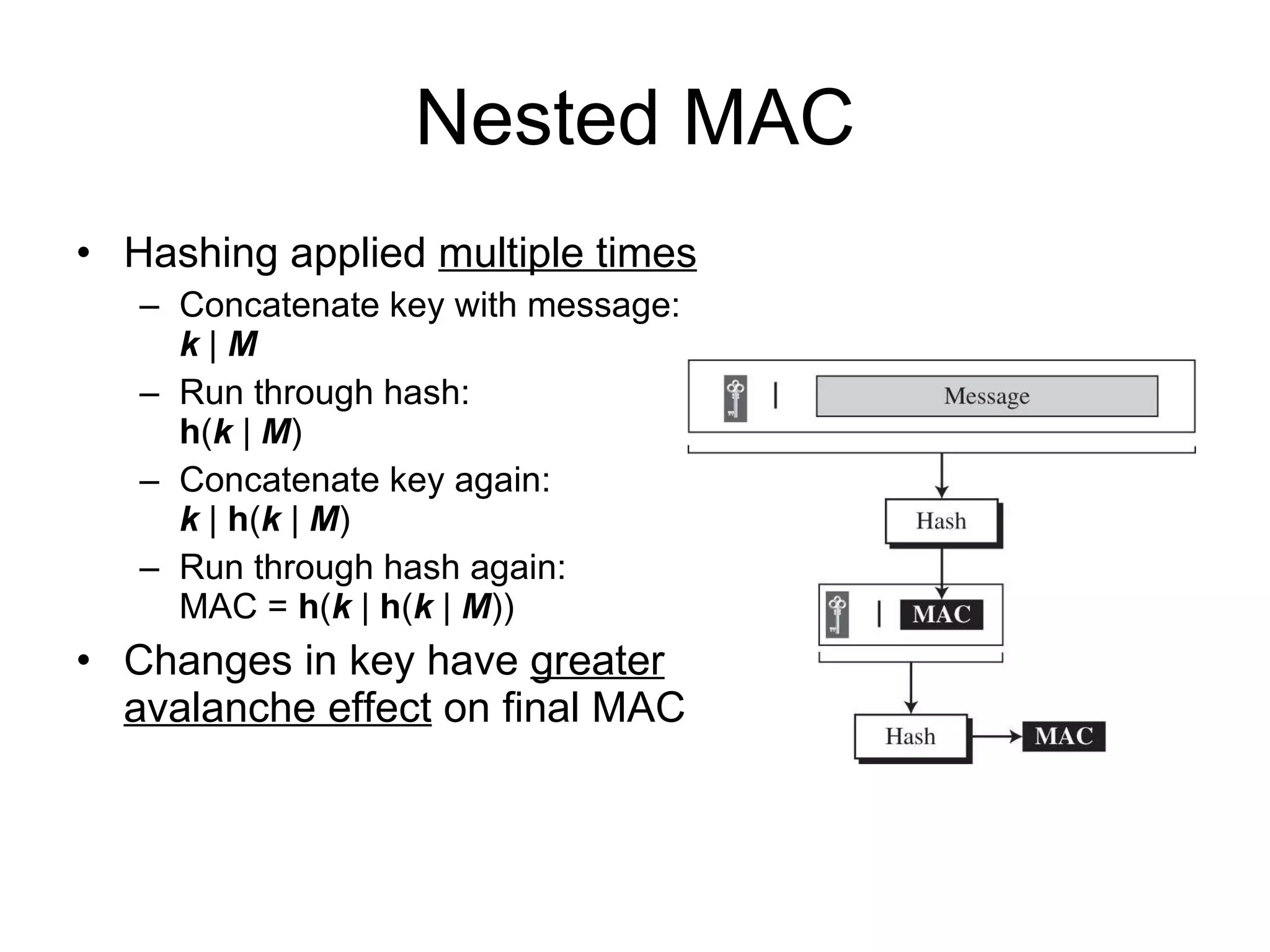
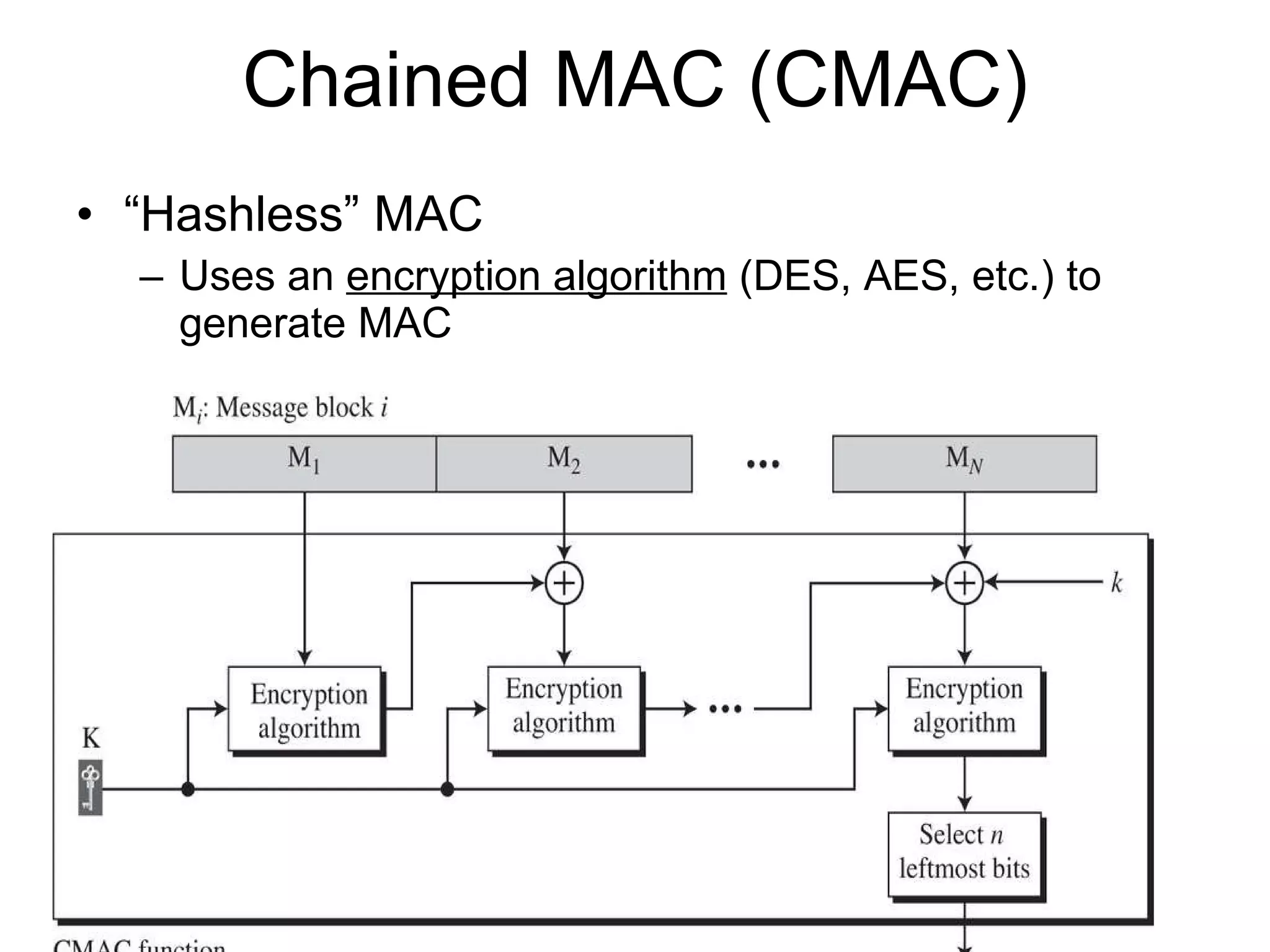
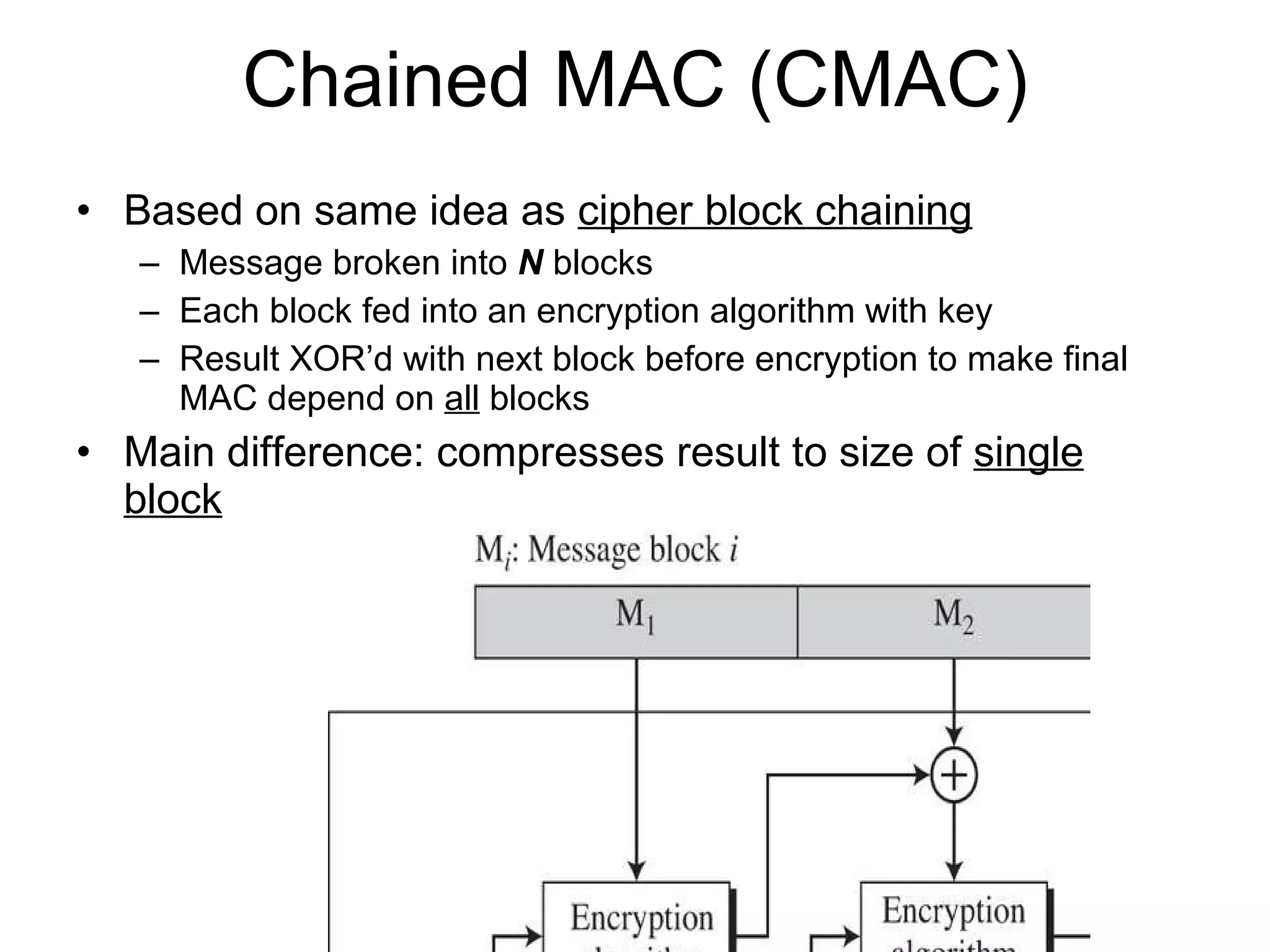
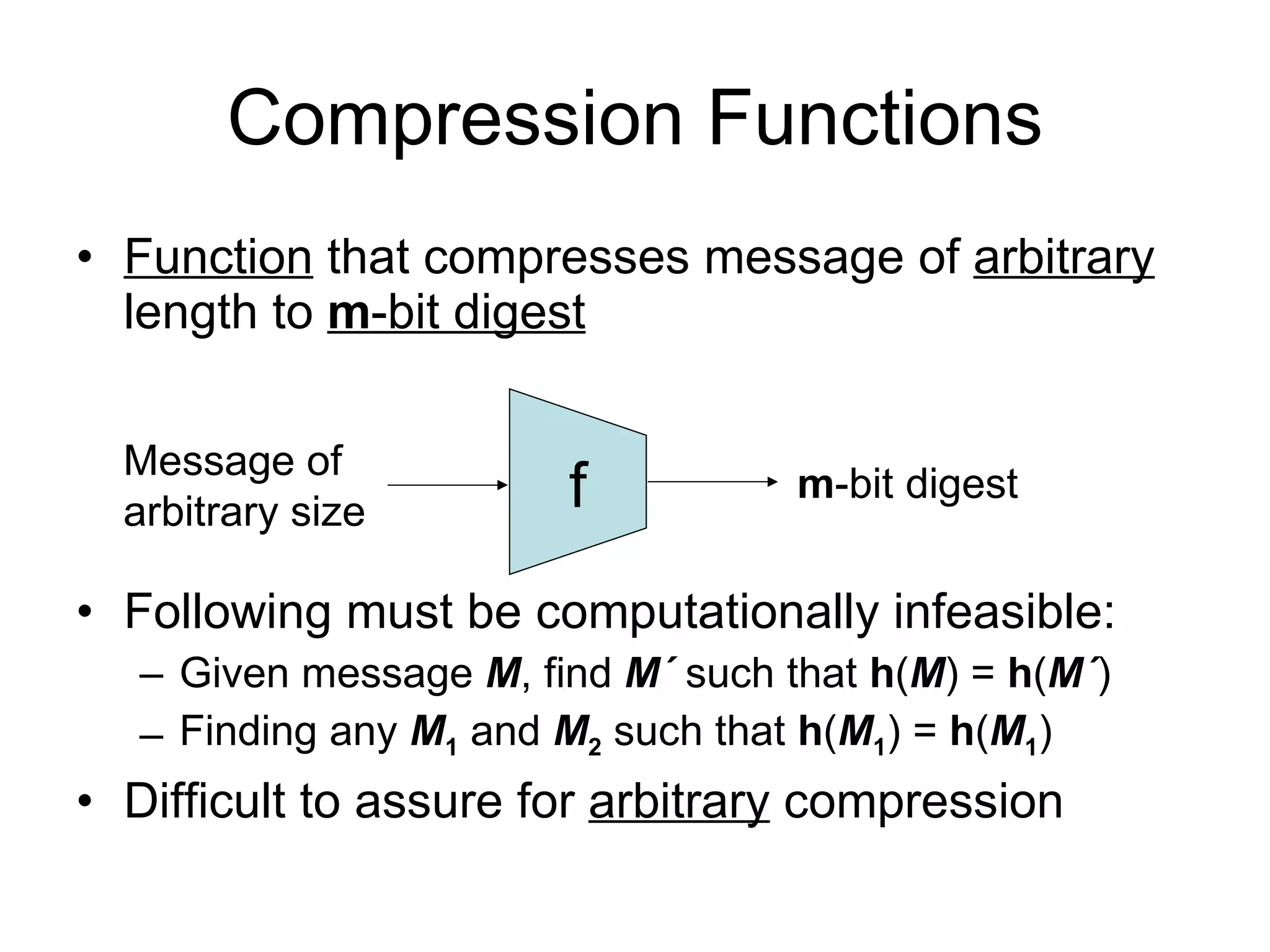
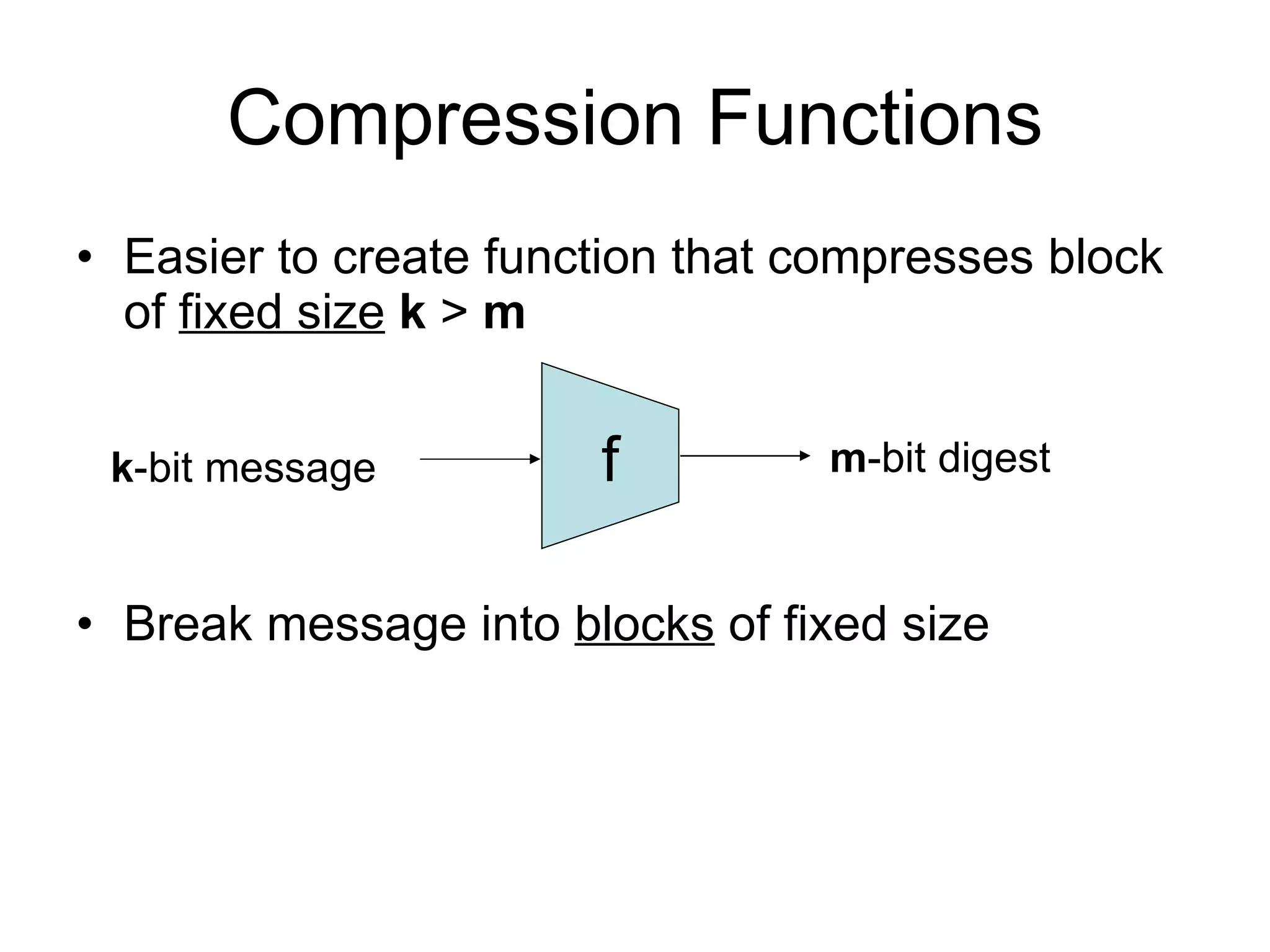
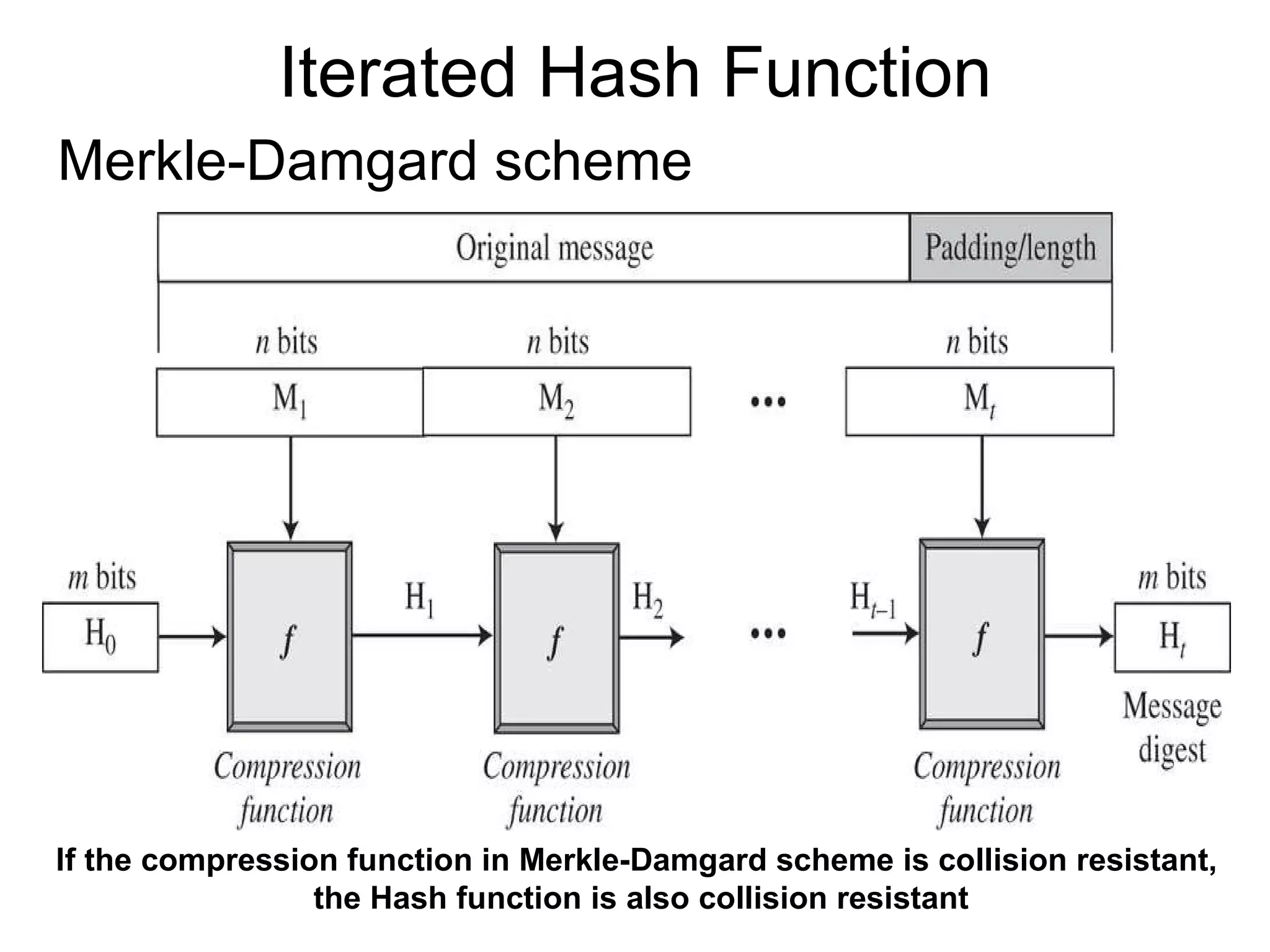
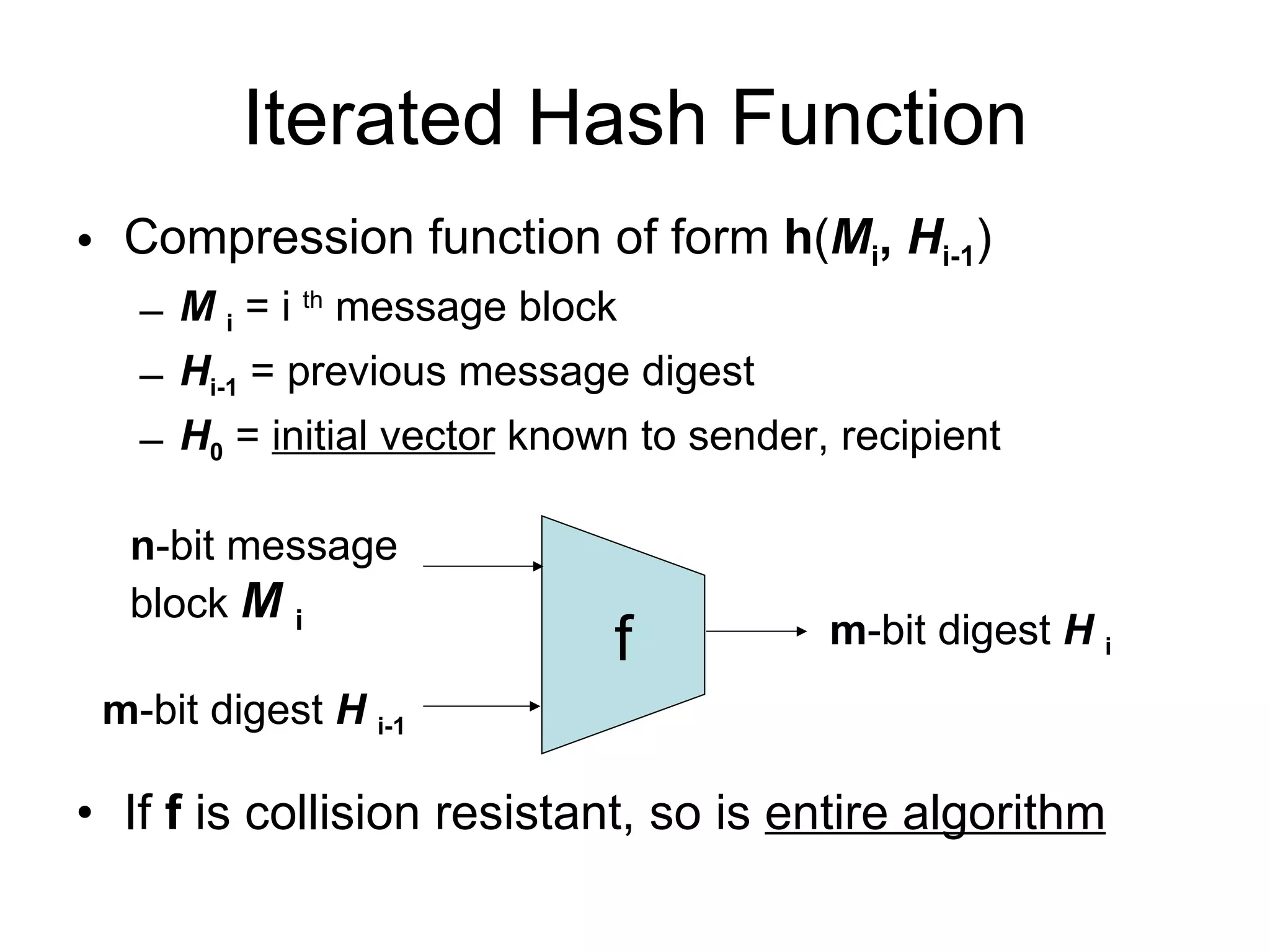
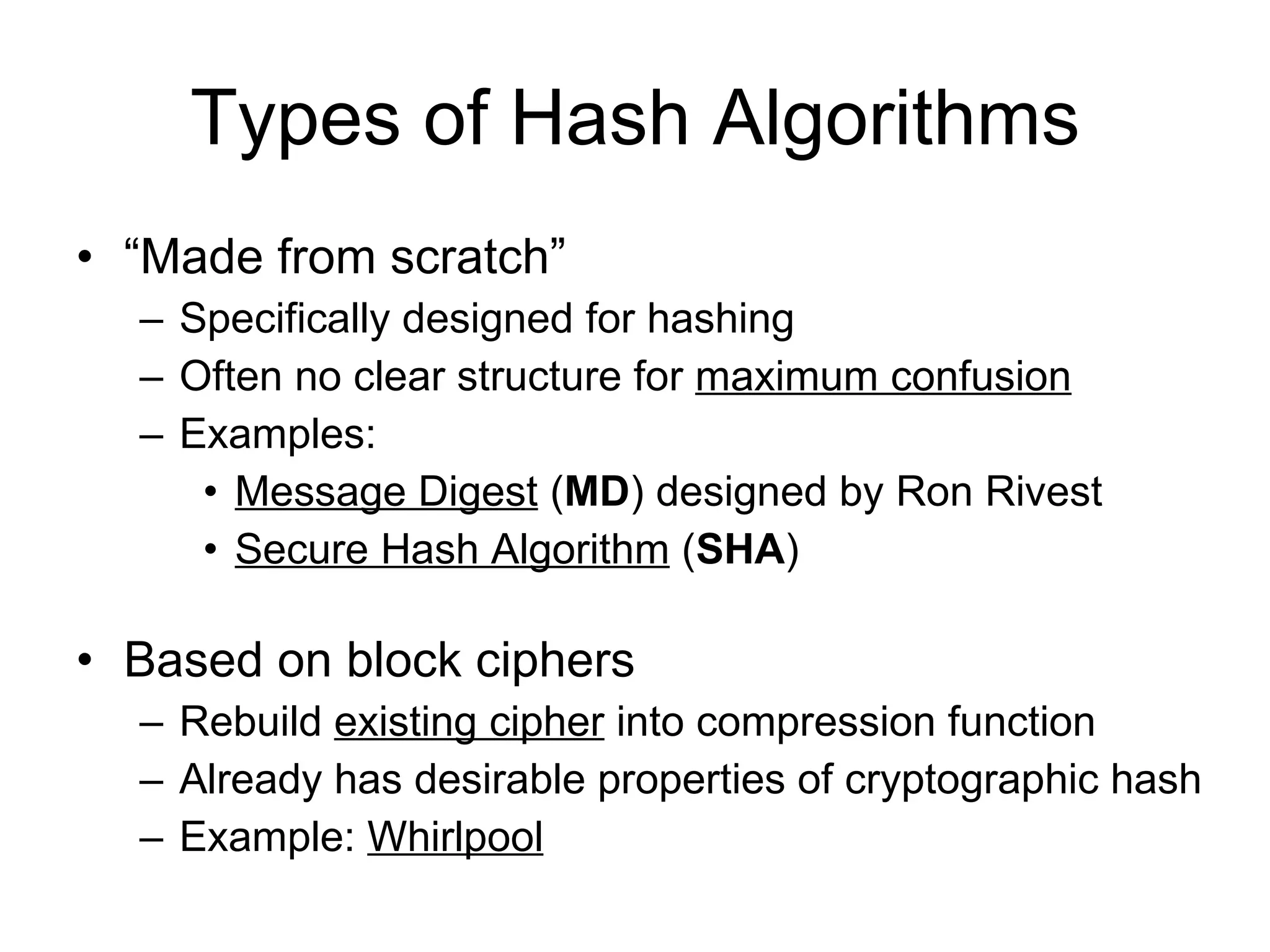
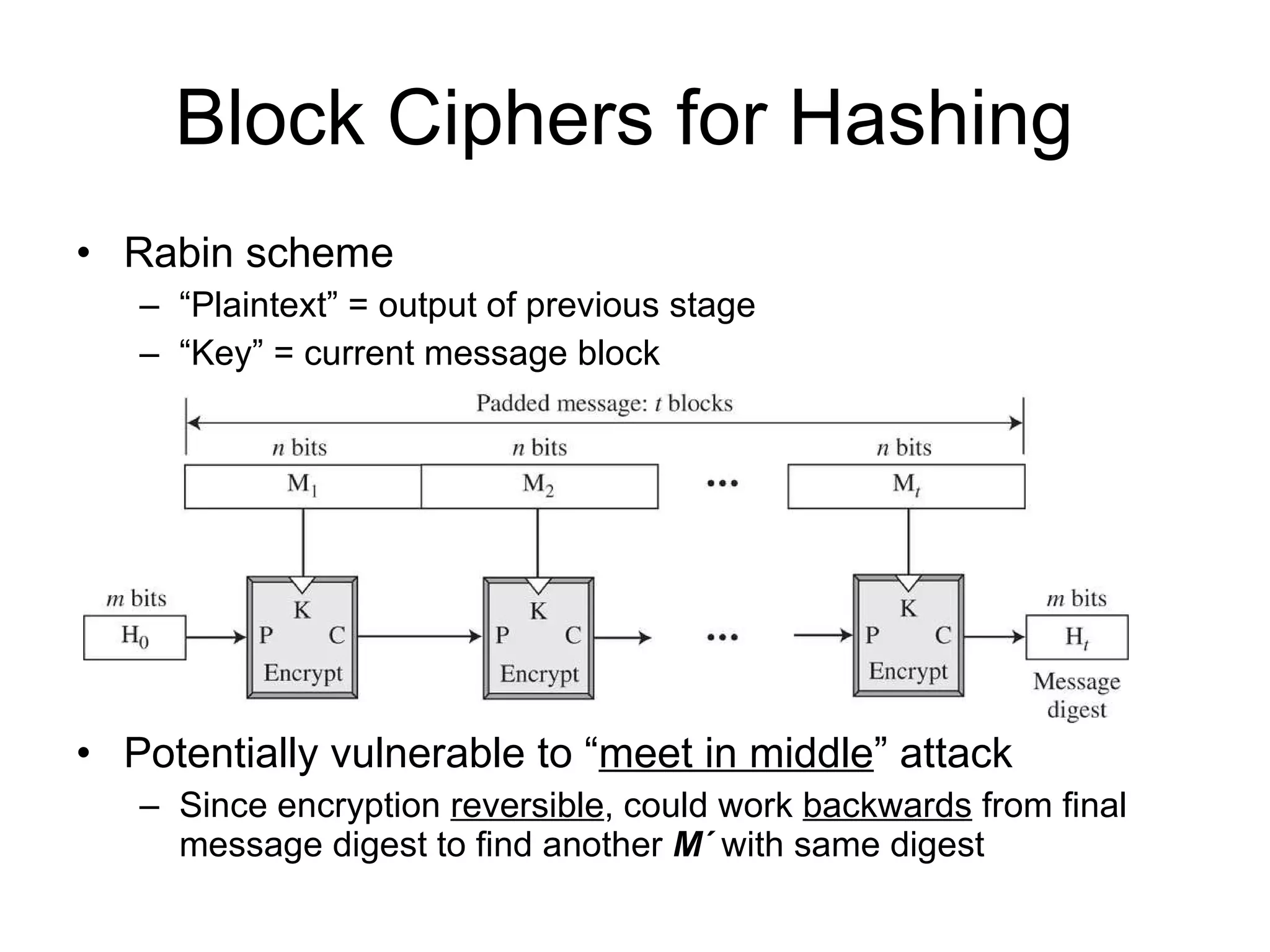
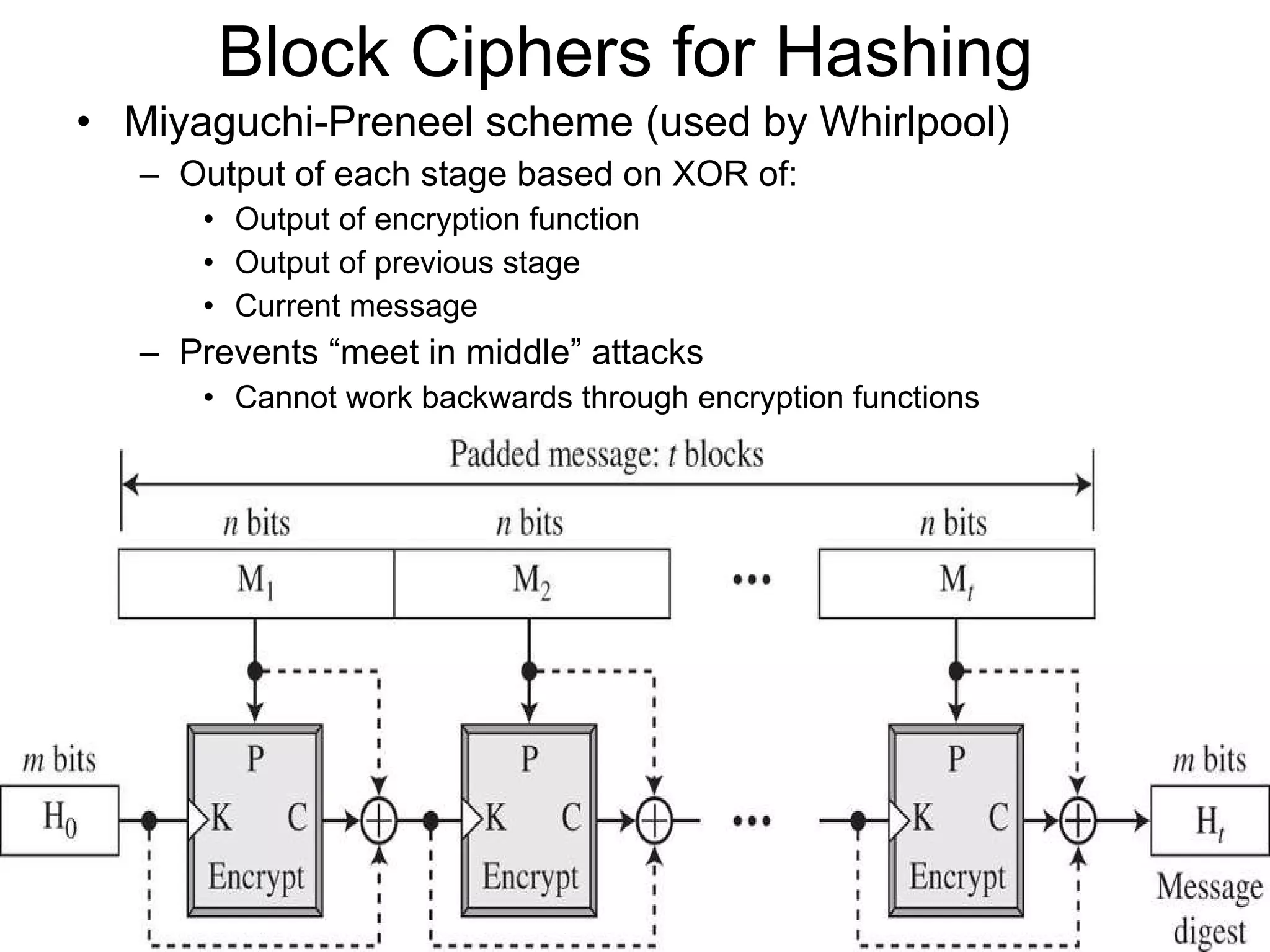
The document discusses network security and techniques for providing message authentication and integrity, including message digests, message authentication codes, and hash functions. It describes how message digests and MACs can detect modifications to messages and prevent masquerading by using secret keys. It also covers attacks like preimage attacks and collision attacks that aim to undermine these integrity protections.