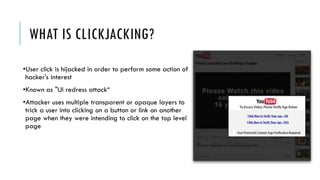
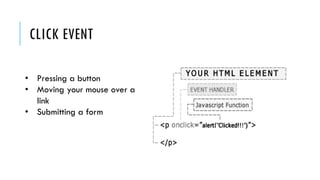
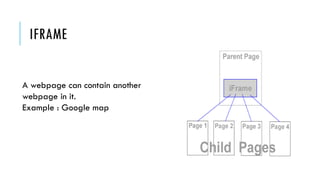
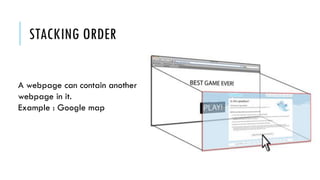
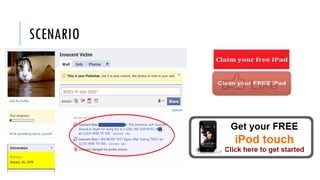
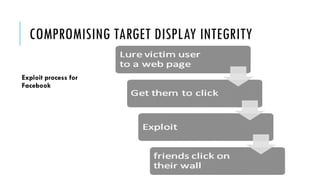
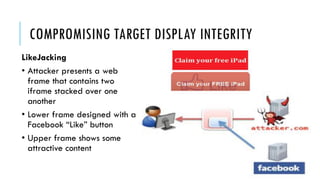
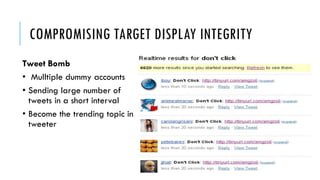
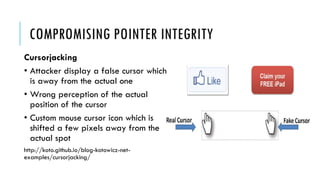
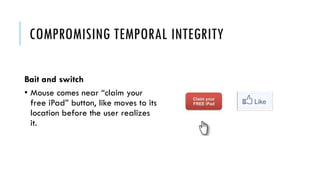
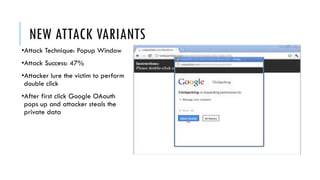
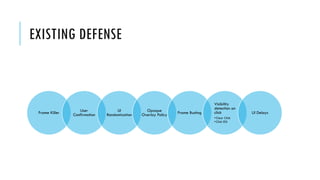
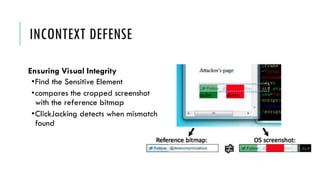
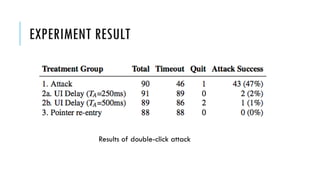
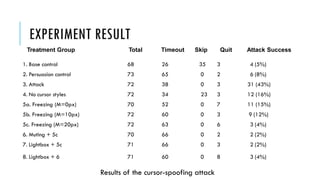
This document summarizes clickjacking attacks and proposes a new defense mechanism called InContext. Clickjacking tricks users into clicking on hidden elements by using transparent overlays. Existing defenses have drawbacks. InContext ensures visual and temporal integrity by freezing the screen, muting audio, and adding delays when sensitive elements are interacted with. An experiment shows InContext defense reduces clickjacking success from 43% to 2%. The paper concludes InContext is effective but new attack variants still need to be addressed.