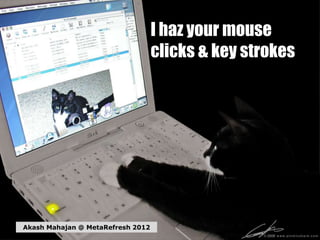
I haz your mouse clicks and key strokes
•Download as PPTX, PDF•
1 like•1,650 views
This technically light talk+demo will show you how and what are User Interface Redressing Attacks. Web Applications using HTML5 + JavaScript + CSS + Modern Browsers are vulnerable to attacks such as Clickjacking, Strokejacking, Cursor Tracking, Unxploitable XSS and Facebook Like attacks. TL;DR Cool demo and simple to understand explaination of ClickJacking
Report
Share
Report
Share
Recommended
Meryliza muabbad how_to_use-jing

Jing is a software that allows users to capture anything on their computer screen as an image or short video. The tutorial explains how to download and install Jing, then create an account. It demonstrates how to use Jing's capture button to take screenshots or record videos and share them on Screencast.com by copying the link. The tutorial concludes by thanking the viewer for learning how to use Jing's basic screenshot and recording features.
Co hs sub instructions

This document provides step-by-step instructions for substitute teachers to sign into the computer-based attendance system at Colony High School, including entering the username and password, locating the Aeries.net icon or website, and entering attendance codes for each class period. Contact information is provided for Lisa Revell and Blanca Ruiz if any assistance is needed.
Selfhelp Online class Google Hangouts Capture App (blue camera)

This slides for Basic Computer Online Class for Senior to teach how to capture screenshot of Google Hangouts / Online Class photos
Ernesto samonte how to use spybot-s&d

The document provides step-by-step instructions for downloading and using Spybot Search & Destroy, a free program that scans for and removes malware from computers. It describes how to access the program's website using a web browser, download the installer, select a destination folder, complete installation, and perform an initial scan and update of the program. Key steps include selecting a download link, waiting for downloads to finish, accepting license agreements, and clicking through the installation wizard.
Topic 12 internet security

The document discusses different types of spyware like adware and trojan horses. It explains how to identify spyware through slowed computers and popups. Steps are provided to remove spyware using programs like Spybot Search and Destroy. The document advises being cautious of downloads and popups while providing safer alternatives for screensavers and software.
An analysis of a facebook spam exploited through browser addons

This paper aims to analyse a newly appeared facebook spam that spreads through installation of browser add-ons
App sec in the time of docker containers

A look at how application security needs to evolve to keep up with applications that are containerised. Delivered first at c0c0n 2016, the audience got a ready checklist to go with the talk.
Secure passwords-theory-and-practice

A look at the risks of not encrypting passwords in your web applications. Also a basic introduction to hashing passwords with salts.
Recommended
Meryliza muabbad how_to_use-jing

Jing is a software that allows users to capture anything on their computer screen as an image or short video. The tutorial explains how to download and install Jing, then create an account. It demonstrates how to use Jing's capture button to take screenshots or record videos and share them on Screencast.com by copying the link. The tutorial concludes by thanking the viewer for learning how to use Jing's basic screenshot and recording features.
Co hs sub instructions

This document provides step-by-step instructions for substitute teachers to sign into the computer-based attendance system at Colony High School, including entering the username and password, locating the Aeries.net icon or website, and entering attendance codes for each class period. Contact information is provided for Lisa Revell and Blanca Ruiz if any assistance is needed.
Selfhelp Online class Google Hangouts Capture App (blue camera)

This slides for Basic Computer Online Class for Senior to teach how to capture screenshot of Google Hangouts / Online Class photos
Ernesto samonte how to use spybot-s&d

The document provides step-by-step instructions for downloading and using Spybot Search & Destroy, a free program that scans for and removes malware from computers. It describes how to access the program's website using a web browser, download the installer, select a destination folder, complete installation, and perform an initial scan and update of the program. Key steps include selecting a download link, waiting for downloads to finish, accepting license agreements, and clicking through the installation wizard.
Topic 12 internet security

The document discusses different types of spyware like adware and trojan horses. It explains how to identify spyware through slowed computers and popups. Steps are provided to remove spyware using programs like Spybot Search and Destroy. The document advises being cautious of downloads and popups while providing safer alternatives for screensavers and software.
An analysis of a facebook spam exploited through browser addons

This paper aims to analyse a newly appeared facebook spam that spreads through installation of browser add-ons
App sec in the time of docker containers

A look at how application security needs to evolve to keep up with applications that are containerised. Delivered first at c0c0n 2016, the audience got a ready checklist to go with the talk.
Secure passwords-theory-and-practice

A look at the risks of not encrypting passwords in your web applications. Also a basic introduction to hashing passwords with salts.
Algae Renewable Energy Carbon Credit First Timer

The interest in algae farming also includes implementing Carbon Capture, Biofuel Production, Power Generation, and other industrial flue gasses for use in Photo bioreactors for algae cultivation.
Web application security

The document discusses web application security threats. It notes that 95% of attacks target web servers and applications, with the top compromised industries being financial services, hospitality, and retail. SQL injection is the most common attack vector, allowing customized malware to be installed. Other threats mentioned include cross-site scripting, cross-site request forgery, clickjacking, and insecure cryptographic storage. The document recommends training developers in secure coding, conducting code reviews and log analysis, and establishing a security practice to help mitigate these risks.
Web application security

95% of attacks target web servers and applications through SQL injection and other injection attacks, which were used to install malware over 60% of the time. Solutions include secure coding training, code reviews, log monitoring, and awareness of new attacks.
Secure HTTP Headers c0c0n 2011 Akash Mahajan

Web site users are facing new and improved threats nowadays. These range from clickjacking, json injection to likejacking among others. Companies like Google, Mozilla, Microsoft etc. have started implementing new HTTP response headers to counter some of the advanced attacks against their website users. Some of the new attacks aren't well understood by the application developers and hence they aren’t using the new secure headers supported by the new browsers. This is either due to ignorance or in order to keep supporting older insecure browsers versions of Internet Explorer.
This talk we will walkthrough what these attacks are, how this various security headers protect the web application users and what is the status of compatibility currently.
INCOMPLETE - OUTLINE for RootConf 2014 - The little-servcie-which-wasn't-there

INCOMPLETE SLIDES - For Rootconf 2014
How do you setup SSH as a TOR hidden service and run a SSH honey pot on port 22
The real incident of stealing a droid app+data

This is a beginner level talk/lecture about how we managed to steal data, bypass security controls and steal the source code of an Android application which was supposed to be secure.
Technically what we managed to do isn't ground breaking, but due to a combination of reasons we were able to radically change the security of the Android app for the better.
Hackers versus Developers and Secure Web Programming

This document discusses hackers and developers and their different perspectives. Hackers try to find weaknesses and gain access in unintended ways, while developers aim to create secure systems. It notes that hackers only need one opening to exploit a system, while developers must constantly work to maintain security. The good fight is about making secure apps and safeguarding data, and hackers play a necessary role in incentivizing developers. Web app security risks include injection attacks and compromising user data. Developers must validate all untrusted input and encode output to build integrity.
20 Hailu Tefera Objective7 Soybean

The document summarizes the progress of the TL II Project aimed at enhancing soybean production in drought-prone areas of Sub-Saharan Africa. Key accomplishments include: fast-tracking high-yielding and stress-tolerant soybean varieties for release; on-farm testing of varieties to demonstrate yields; breeding segregating populations; developing value chains and linking farmers to processors; and strengthening capacity through graduate training. Challenges remain around developing more drought-tolerant varieties and expanding value addition and market access.
Believe It Or Not SSL Attacks

A talk about attacks against SSL that have been uncovered in the last 3-4 years. This talk delves into about what exactly was attacked and how it was attacked and how SSL is still a pretty useful piece of technology.
This was given at null Bangalore April Meeting.
Web application security

95% of attacks target web servers and applications through SQL injection and other injection attacks, which were used to install malware over 60% of the time. Solutions include secure coding training, code reviews, log monitoring, and awareness of new attacks.
Venom vulnerability Overview and a basic demo

This vulnerability, called VENOM, allows an attacker to escape from a virtual machine guest into the host system. It affects virtualization platforms that use Xen, Qemu, KVM, or VirtualBox as their hypervisor. The vulnerability is in the virtual floppy disk controller code, which contains a buffer overflow issue. This allows an attacker to potentially gain code execution on the host machine. It is a serious issue because many cloud providers use these vulnerable virtualization platforms.
Top 10 web application security risks akash mahajan

The document discusses the OWASP Top 10, which lists the top 10 most critical web application security risks. It provides an overview of OWASP, an organization dedicated to web application security, and their Top 10 project. For each of the top 10 risks, it briefly explains the technical impact, such as allowing SQL injection, cross-site scripting attacks, or unauthorized access to user data. It emphasizes the importance of addressing these risks to help secure web applications.
My 'Technopreneurship' presentation @ SCIT Pune!!!

The document discusses the scope of entrepreneurship, or "technopreneurship", in the technology sector. It notes that the web now encompasses most IT areas like websites, portals, mobile, social media, software as a service, and more. It outlines opportunities in areas like cloud computing, mobile apps, and social/collaboration tools. The document encourages starting up now despite risks and difficulties, noting many successful entrepreneurs succeeded due to circumstances rather than choice. Passion, perseverance, and persistence are key to becoming a successful technopreneur according to the document.
Php security

A different look at what PHP developers should be looking at. Not in terms of security but in terms of the data flow of the web application. The concepts of security are tied into that itself.
inhertance c++

Inheritance allows classes to derive from existing classes, promoting code reuse. There are different types of inheritance like single, multilevel, multiple, and hierarchical. Constructors and destructors are called in the reverse order in inheritance, with base class constructors called before derived class constructors, and base class destructors called after derived class destructors.
Security in the cloud Workshop HSTC 2014

A broad overview of what it takes to be secure. This is more of an introduction where we introduce the basic terms around Cloud Computing and how do we go about securing our information assets(Data, Applications and Infrastructure)
The workshop was fun because all the slides were paired with real world examples of security breaches and attacks.
UI Redressing

Jovin Lobo presented on UI redressing and clickjacking attacks. He began with an introduction to clickjacking, demonstrating basic techniques like using iframes and adjusting opacity to trick users. More advanced demos showed how clicks and text input could be hijacked. Framebusting code is commonly used for prevention but has limitations. The most effective prevention is using the X-Frame-Options HTTP header to control whether pages can be framed or displayed in iframes.
Clickjacking

This document discusses clickjacking, a technique where an attacker uses multiple transparent or invisible layers to trick a user into clicking on a button or link on another page while thinking they are clicking on the visible page content. The summary discusses the history and types of clickjacking attacks, including basic positioning using CSS and invisible frames, as well as more advanced techniques combining with XSS, CSRF, or HTML5 drag and drop APIs. Mitigation techniques are also provided, including framebusting JavaScript, X-Frame-Options headers, and Content Security Policy headers.
Make profit with UI-Redressing attacks.

This document discusses how to profit from UI-redressing (changing the user interface in a browser). It describes server-side mitigations like X-Frame-Options headers. It recommends targeting CSRF-protected actions and pages with tokens. Various CSS techniques and exploitation methods are outlined, like simple clickjacking and fake captchas. The conclusion encourages profiting from bug bounties by imagining new attack techniques on sites without adequate protections.
Javascript Security - Three main methods of defending your MEAN stack

How attacks works? Learn how XSS, CSRF and NoSQL injection are working and secure your app on MEAN (MongoDB, Express.js, Angular.js, Node,js) stack.
Clickjacking DevCon2011

The document summarizes techniques for preventing clickjacking attacks, including frame busting code, the X-Frame-Options HTTP header, and Content Security Policy. It provides examples of how to implement these techniques and their limitations. It encourages attendees to check their own websites and applications for clickjacking vulnerabilities and ways to secure them against these risks.
More Related Content
Viewers also liked
Algae Renewable Energy Carbon Credit First Timer

The interest in algae farming also includes implementing Carbon Capture, Biofuel Production, Power Generation, and other industrial flue gasses for use in Photo bioreactors for algae cultivation.
Web application security

The document discusses web application security threats. It notes that 95% of attacks target web servers and applications, with the top compromised industries being financial services, hospitality, and retail. SQL injection is the most common attack vector, allowing customized malware to be installed. Other threats mentioned include cross-site scripting, cross-site request forgery, clickjacking, and insecure cryptographic storage. The document recommends training developers in secure coding, conducting code reviews and log analysis, and establishing a security practice to help mitigate these risks.
Web application security

95% of attacks target web servers and applications through SQL injection and other injection attacks, which were used to install malware over 60% of the time. Solutions include secure coding training, code reviews, log monitoring, and awareness of new attacks.
Secure HTTP Headers c0c0n 2011 Akash Mahajan

Web site users are facing new and improved threats nowadays. These range from clickjacking, json injection to likejacking among others. Companies like Google, Mozilla, Microsoft etc. have started implementing new HTTP response headers to counter some of the advanced attacks against their website users. Some of the new attacks aren't well understood by the application developers and hence they aren’t using the new secure headers supported by the new browsers. This is either due to ignorance or in order to keep supporting older insecure browsers versions of Internet Explorer.
This talk we will walkthrough what these attacks are, how this various security headers protect the web application users and what is the status of compatibility currently.
INCOMPLETE - OUTLINE for RootConf 2014 - The little-servcie-which-wasn't-there

INCOMPLETE SLIDES - For Rootconf 2014
How do you setup SSH as a TOR hidden service and run a SSH honey pot on port 22
The real incident of stealing a droid app+data

This is a beginner level talk/lecture about how we managed to steal data, bypass security controls and steal the source code of an Android application which was supposed to be secure.
Technically what we managed to do isn't ground breaking, but due to a combination of reasons we were able to radically change the security of the Android app for the better.
Hackers versus Developers and Secure Web Programming

This document discusses hackers and developers and their different perspectives. Hackers try to find weaknesses and gain access in unintended ways, while developers aim to create secure systems. It notes that hackers only need one opening to exploit a system, while developers must constantly work to maintain security. The good fight is about making secure apps and safeguarding data, and hackers play a necessary role in incentivizing developers. Web app security risks include injection attacks and compromising user data. Developers must validate all untrusted input and encode output to build integrity.
20 Hailu Tefera Objective7 Soybean

The document summarizes the progress of the TL II Project aimed at enhancing soybean production in drought-prone areas of Sub-Saharan Africa. Key accomplishments include: fast-tracking high-yielding and stress-tolerant soybean varieties for release; on-farm testing of varieties to demonstrate yields; breeding segregating populations; developing value chains and linking farmers to processors; and strengthening capacity through graduate training. Challenges remain around developing more drought-tolerant varieties and expanding value addition and market access.
Believe It Or Not SSL Attacks

A talk about attacks against SSL that have been uncovered in the last 3-4 years. This talk delves into about what exactly was attacked and how it was attacked and how SSL is still a pretty useful piece of technology.
This was given at null Bangalore April Meeting.
Web application security

95% of attacks target web servers and applications through SQL injection and other injection attacks, which were used to install malware over 60% of the time. Solutions include secure coding training, code reviews, log monitoring, and awareness of new attacks.
Venom vulnerability Overview and a basic demo

This vulnerability, called VENOM, allows an attacker to escape from a virtual machine guest into the host system. It affects virtualization platforms that use Xen, Qemu, KVM, or VirtualBox as their hypervisor. The vulnerability is in the virtual floppy disk controller code, which contains a buffer overflow issue. This allows an attacker to potentially gain code execution on the host machine. It is a serious issue because many cloud providers use these vulnerable virtualization platforms.
Top 10 web application security risks akash mahajan

The document discusses the OWASP Top 10, which lists the top 10 most critical web application security risks. It provides an overview of OWASP, an organization dedicated to web application security, and their Top 10 project. For each of the top 10 risks, it briefly explains the technical impact, such as allowing SQL injection, cross-site scripting attacks, or unauthorized access to user data. It emphasizes the importance of addressing these risks to help secure web applications.
My 'Technopreneurship' presentation @ SCIT Pune!!!

The document discusses the scope of entrepreneurship, or "technopreneurship", in the technology sector. It notes that the web now encompasses most IT areas like websites, portals, mobile, social media, software as a service, and more. It outlines opportunities in areas like cloud computing, mobile apps, and social/collaboration tools. The document encourages starting up now despite risks and difficulties, noting many successful entrepreneurs succeeded due to circumstances rather than choice. Passion, perseverance, and persistence are key to becoming a successful technopreneur according to the document.
Php security

A different look at what PHP developers should be looking at. Not in terms of security but in terms of the data flow of the web application. The concepts of security are tied into that itself.
inhertance c++

Inheritance allows classes to derive from existing classes, promoting code reuse. There are different types of inheritance like single, multilevel, multiple, and hierarchical. Constructors and destructors are called in the reverse order in inheritance, with base class constructors called before derived class constructors, and base class destructors called after derived class destructors.
Security in the cloud Workshop HSTC 2014

A broad overview of what it takes to be secure. This is more of an introduction where we introduce the basic terms around Cloud Computing and how do we go about securing our information assets(Data, Applications and Infrastructure)
The workshop was fun because all the slides were paired with real world examples of security breaches and attacks.
Viewers also liked (17)
INCOMPLETE - OUTLINE for RootConf 2014 - The little-servcie-which-wasn't-there

INCOMPLETE - OUTLINE for RootConf 2014 - The little-servcie-which-wasn't-there
Hackers versus Developers and Secure Web Programming

Hackers versus Developers and Secure Web Programming
Top 10 web application security risks akash mahajan

Top 10 web application security risks akash mahajan
My 'Technopreneurship' presentation @ SCIT Pune!!!

My 'Technopreneurship' presentation @ SCIT Pune!!!
Similar to I haz your mouse clicks and key strokes
UI Redressing

Jovin Lobo presented on UI redressing and clickjacking attacks. He began with an introduction to clickjacking, demonstrating basic techniques like using iframes and adjusting opacity to trick users. More advanced demos showed how clicks and text input could be hijacked. Framebusting code is commonly used for prevention but has limitations. The most effective prevention is using the X-Frame-Options HTTP header to control whether pages can be framed or displayed in iframes.
Clickjacking

This document discusses clickjacking, a technique where an attacker uses multiple transparent or invisible layers to trick a user into clicking on a button or link on another page while thinking they are clicking on the visible page content. The summary discusses the history and types of clickjacking attacks, including basic positioning using CSS and invisible frames, as well as more advanced techniques combining with XSS, CSRF, or HTML5 drag and drop APIs. Mitigation techniques are also provided, including framebusting JavaScript, X-Frame-Options headers, and Content Security Policy headers.
Make profit with UI-Redressing attacks.

This document discusses how to profit from UI-redressing (changing the user interface in a browser). It describes server-side mitigations like X-Frame-Options headers. It recommends targeting CSRF-protected actions and pages with tokens. Various CSS techniques and exploitation methods are outlined, like simple clickjacking and fake captchas. The conclusion encourages profiting from bug bounties by imagining new attack techniques on sites without adequate protections.
Javascript Security - Three main methods of defending your MEAN stack

How attacks works? Learn how XSS, CSRF and NoSQL injection are working and secure your app on MEAN (MongoDB, Express.js, Angular.js, Node,js) stack.
Clickjacking DevCon2011

The document summarizes techniques for preventing clickjacking attacks, including frame busting code, the X-Frame-Options HTTP header, and Content Security Policy. It provides examples of how to implement these techniques and their limitations. It encourages attendees to check their own websites and applications for clickjacking vulnerabilities and ways to secure them against these risks.
javascript-gone-wild-withreferences-attributions-111003035611-php

The document discusses using JavaScript in unexpected ways that could have unintended consequences. It provides examples like stealing session cookies or redirecting users to malicious sites. It warns that allowing untrusted code to run in browsers poses risks, but also discusses how JavaScript was once used by Samy Kamkar to rapidly gain friends on MySpace. Overall it suggests JavaScript's capabilities could be exploited if it appears where users don't expect.
Phishing with Super Bait

Phishing with Super Bait
Jeremiah Grossman, Founder and CTO, WhiteHat Security
The use of phishing/cross-site scripting (XSS) hybrid attacks for financial gain is spreading. ItÕs imperative that security professionals familiarize themselves with these new threats to protect their websites and confidential corporate information.
This isn't just another presentation about phishing scams or cross-site scripting. WeÕre all very familiar with each of those issues. Instead, weÕll discuss the potential impact when the two are combined to form new attack techniques. Phishers are beginning to exploit these techniques, creating new phishing attacks that are virtually impervious to conventional security measures. Secure sockets layer (SSL), blacklists, token-based authentication, browser same-origin policy, and monitoring / take-down services offer little protection. Even eyeballing the authenticity of a URL is unlikely to help.
By leveraging cross-site scripting, the next level of phishing scams will be launched not from look-alike web pages, but instead from legitimate websites! This presentation will demonstrate how these types of attacks are being achieved. We'll also demonstrate the cutting edge exploits that can effectively turn your browser into spyware with several lines of JavaScript. And, we'll give you the steps you need to take to protect your websites from these attacks.
HalfStack fast but not furious

This document discusses debugging user interaction performance issues in web pages. It begins by explaining how the browser renders frames and what happens during each step of the rendering process. It then covers the different types of changes that can trigger layout, paint, or compositing updates. Potentially problematic UI patterns like animations, parallax effects, scrolling events and appending elements are described. The document provides tips on using tools like the Performance tab to test for interaction issues and recommends techniques like using will-change to avoid unnecessary repaints and reflows.
.NET Security Topics

This document discusses various security topics for .NET applications including cross-site scripting (XSS), SQL injection, cross-site request forgery (CSRF), clickjacking, and secure file handling. It provides definitions, examples, and mitigation strategies for each topic. Code examples are shown for XSS defenses, SQL injection defenses, CSRF defenses, clickjacking defenses, and secure file uploads. The document also includes additional tips and resources for developing secure .NET applications.
Django Web Application Security

This document discusses security best practices for Django web applications. It begins by introducing the author and their background in Python, Django, and computer security. It then covers common web vulnerabilities and attacks like information disclosure, input validation issues, session hijacking, and denial of service. Throughout, it provides recommendations for how to configure Django and code defensively to mitigate these risks, such as using parameterized queries, input sanitization, secure sessions, and cross-site request forgery protection. It emphasizes adopting a layered security approach and being vigilant about updates and monitoring.
What happens on your Mac, stays on Apple’s iCloud?!

“$ sudo ls ~/Desktop: Operation not permitted”. Apple’s Transparency, Consent, and Control (TCC) framework limits access to private information like documents, a camera, a microphone, emails, and more in order to preserve your privacy. Since authorisation is required to grant such access, the mechanism key design priority was clear user consent.
At Black Hat USA 2021, I co-presented considerable research on abusing the TCC mechanisms, however, this time, we won’t be directly exploiting the TCC. Given that iCloud has tons of macOS users’ secrets, why keep attacking the TCC? The default configuration makes Mac synchronize a lot of data. Don’t you have your iMessages/Photos/Calendars/Reminders/Notes accessible from iCloud? That’s good because you take care of your privacy… but most users don’t. :)
The brand-new research on abusing Apple’s iCloud to gain access to users’ sensitive data will be shared during the presentation. All that from a malicious applications’ perspective without any additional permissions.
Rich Internet Applications (RIA) Web Testing

This document summarizes DirectScreen, a tool that can automate and test advanced web technologies like AJAX, Java applets, Flash, and Silverlight. It discusses how DirectScreen simulates user interactions by sending mouse clicks and keystrokes. It also compares DirectScreen commands to traditional HTML click commands and explains how DirectScreen can automatically record and simulate mouse events over elements. The document provides examples of how DirectScreen can be used to automate JavaScript menus, Flash chat apps, and file uploads.
Anatomy of a WordPress Hack

The document discusses three common WordPress hacks: SQL injection, cross-site scripting (XSS), and clickjacking. For each hack, it describes how the vulnerability works and provides examples of exploits. It then notes how each issue can be fixed with just a few lines of code. The document emphasizes that WordPress security is important because nearly 20% of websites run on WordPress, making it a frequent target for attacks. It closes by thanking contributors to WordPress security and encouraging reporting new issues responsibly.
Click jacking

Clickjacking is an attack where a user is tricked into clicking on obscured elements on a website. Attackers can embed a target site in an invisible iframe to trick users into performing actions like posting messages without their consent. Adding the X-Frame-Options header is an effective defense, but many older browsers and sites remain vulnerable. Clickjacking remains a risk because client-side defenses can be bypassed and many sites have not implemented the server-side X-Frame-Options header.
How to secure web applications

I presented this presentation at owasp hyderabad oct 2012 meet. you can find more details at https://www.owasp.org/index.php/Hyderabad
Html5: something wicked this way comes - HackPra

Video recording of the talk: https://connect.ruhr-uni-bochum.de/p3g2butmrt4/
HTML5 is quickly gaining media attention and popularity among browser vendors and web developers. Having tremendous features, together with its sister specifications like Drag & Drop API, File API or Geolocation it allows developers to build rich web applications that easily blend with desktop & mobile environments.
The talk will be focused on finding the weakest link and combining several recent attack techniques to turn a security vulnerability into a successful exploit.
We'll show how to build a successful advanced UI-Redressing attack (also known as clickjacking), presenting the latest findings in this field, including malicious games and quizes. We'll work on file upload functionalities in current web applications and see how attackers might use HTML5 APIs for their advantage. Putting all these building blocks together will enable us to launch an attack and exploit even the otherwise unexploitable vulnerabilities.
Ajax to the Moon

The document discusses various techniques for enabling offline functionality in Ajax applications, including browser storage options like cookies, Firefox offline storage, and Flash shared objects. It also covers approaches for pushing data from server to client like polling, asynchronous servlets, Comet, and piggybacking on other responses. The document concludes with considerations for optimizing Ajax performance such as data formats, bandwidth usage, and client-side processing.
Unity3D Basic Concepts by: shamal aryan 

Presentation about unity, what is Unity? how to create your own game in Unity3d? Simple demo 2D graphics JAVAscript coding. unity is very easy and its a good platform. any one can ply with it, i wish you will like this presentation.
JavaScript and DOM Pattern Implementation

Covers implementation details of five important Ajax design patterns in terms of DOM, CSS and JavaScript.
Itc2009 Click Jacking

Click jacking is a method used by attackers to trick users into clicking on hidden buttons or links on legitimate pages by masking the context using other web content like graphics. Attackers can persuade victims to click where the attacker wants by placing buttons strategically. Website owners can prevent click jacking by adding frame busting code and requiring JavaScript for sensitive actions. Users should logout of sites, install plugins like NoScript, and disable plugins to help prevent click jacking.
Similar to I haz your mouse clicks and key strokes (20)
Javascript Security - Three main methods of defending your MEAN stack

Javascript Security - Three main methods of defending your MEAN stack
javascript-gone-wild-withreferences-attributions-111003035611-php

javascript-gone-wild-withreferences-attributions-111003035611-php
What happens on your Mac, stays on Apple’s iCloud?!

What happens on your Mac, stays on Apple’s iCloud?!
Recently uploaded
GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...

Effective Application Security in Software Delivery lifecycle using Deployment Firewall and DBOM
The modern software delivery process (or the CI/CD process) includes many tools, distributed teams, open-source code, and cloud platforms. Constant focus on speed to release software to market, along with the traditional slow and manual security checks has caused gaps in continuous security as an important piece in the software supply chain. Today organizations feel more susceptible to external and internal cyber threats due to the vast attack surface in their applications supply chain and the lack of end-to-end governance and risk management.
The software team must secure its software delivery process to avoid vulnerability and security breaches. This needs to be achieved with existing tool chains and without extensive rework of the delivery processes. This talk will present strategies and techniques for providing visibility into the true risk of the existing vulnerabilities, preventing the introduction of security issues in the software, resolving vulnerabilities in production environments quickly, and capturing the deployment bill of materials (DBOM).
Speakers:
Bob Boule
Robert Boule is a technology enthusiast with PASSION for technology and making things work along with a knack for helping others understand how things work. He comes with around 20 years of solution engineering experience in application security, software continuous delivery, and SaaS platforms. He is known for his dynamic presentations in CI/CD and application security integrated in software delivery lifecycle.
Gopinath Rebala
Gopinath Rebala is the CTO of OpsMx, where he has overall responsibility for the machine learning and data processing architectures for Secure Software Delivery. Gopi also has a strong connection with our customers, leading design and architecture for strategic implementations. Gopi is a frequent speaker and well-known leader in continuous delivery and integrating security into software delivery.
UiPath Test Automation using UiPath Test Suite series, part 6

Welcome to UiPath Test Automation using UiPath Test Suite series part 6. In this session, we will cover Test Automation with generative AI and Open AI.
UiPath Test Automation with generative AI and Open AI webinar offers an in-depth exploration of leveraging cutting-edge technologies for test automation within the UiPath platform. Attendees will delve into the integration of generative AI, a test automation solution, with Open AI advanced natural language processing capabilities.
Throughout the session, participants will discover how this synergy empowers testers to automate repetitive tasks, enhance testing accuracy, and expedite the software testing life cycle. Topics covered include the seamless integration process, practical use cases, and the benefits of harnessing AI-driven automation for UiPath testing initiatives. By attending this webinar, testers, and automation professionals can gain valuable insights into harnessing the power of AI to optimize their test automation workflows within the UiPath ecosystem, ultimately driving efficiency and quality in software development processes.
What will you get from this session?
1. Insights into integrating generative AI.
2. Understanding how this integration enhances test automation within the UiPath platform
3. Practical demonstrations
4. Exploration of real-world use cases illustrating the benefits of AI-driven test automation for UiPath
Topics covered:
What is generative AI
Test Automation with generative AI and Open AI.
UiPath integration with generative AI
Speaker:
Deepak Rai, Automation Practice Lead, Boundaryless Group and UiPath MVP
Video Streaming: Then, Now, and in the Future

In his public lecture, Christian Timmerer provides insights into the fascinating history of video streaming, starting from its humble beginnings before YouTube to the groundbreaking technologies that now dominate platforms like Netflix and ORF ON. Timmerer also presents provocative contributions of his own that have significantly influenced the industry. He concludes by looking at future challenges and invites the audience to join in a discussion.
20240609 QFM020 Irresponsible AI Reading List May 2024

Everything I found interesting about the irresponsible use of machine intelligence in May 2024
DevOps and Testing slides at DASA Connect

My and Rik Marselis slides at 30.5.2024 DASA Connect conference. We discuss about what is testing, then what is agile testing and finally what is Testing in DevOps. Finally we had lovely workshop with the participants trying to find out different ways to think about quality and testing in different parts of the DevOps infinity loop.
Goodbye Windows 11: Make Way for Nitrux Linux 3.5.0!

As the digital landscape continually evolves, operating systems play a critical role in shaping user experiences and productivity. The launch of Nitrux Linux 3.5.0 marks a significant milestone, offering a robust alternative to traditional systems such as Windows 11. This article delves into the essence of Nitrux Linux 3.5.0, exploring its unique features, advantages, and how it stands as a compelling choice for both casual users and tech enthusiasts.
How to Get CNIC Information System with Paksim Ga.pptx

Pakdata Cf is a groundbreaking system designed to streamline and facilitate access to CNIC information. This innovative platform leverages advanced technology to provide users with efficient and secure access to their CNIC details.
GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...

Sudheer Mechineni, Head of Application Frameworks, Standard Chartered Bank
Discover how Standard Chartered Bank harnessed the power of Neo4j to transform complex data access challenges into a dynamic, scalable graph database solution. This keynote will cover their journey from initial adoption to deploying a fully automated, enterprise-grade causal cluster, highlighting key strategies for modelling organisational changes and ensuring robust disaster recovery. Learn how these innovations have not only enhanced Standard Chartered Bank’s data infrastructure but also positioned them as pioneers in the banking sector’s adoption of graph technology.
GraphSummit Singapore | The Future of Agility: Supercharging Digital Transfor...

Leonard Jayamohan, Partner & Generative AI Lead, Deloitte
This keynote will reveal how Deloitte leverages Neo4j’s graph power for groundbreaking digital twin solutions, achieving a staggering 100x performance boost. Discover the essential role knowledge graphs play in successful generative AI implementations. Plus, get an exclusive look at an innovative Neo4j + Generative AI solution Deloitte is developing in-house.
Generative AI Deep Dive: Advancing from Proof of Concept to Production

Join Maher Hanafi, VP of Engineering at Betterworks, in this new session where he'll share a practical framework to transform Gen AI prototypes into impactful products! He'll delve into the complexities of data collection and management, model selection and optimization, and ensuring security, scalability, and responsible use.
Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf

Monitoring and observability aren’t traditionally found in software curriculums and many of us cobble this knowledge together from whatever vendor or ecosystem we were first introduced to and whatever is a part of your current company’s observability stack.
While the dev and ops silo continues to crumble….many organizations still relegate monitoring & observability as the purview of ops, infra and SRE teams. This is a mistake - achieving a highly observable system requires collaboration up and down the stack.
I, a former op, would like to extend an invitation to all application developers to join the observability party will share these foundational concepts to build on:
みなさんこんにちはこれ何文字まで入るの?40文字以下不可とか本当に意味わからないけどこれ限界文字数書いてないからマジでやばい文字数いけるんじゃないの?えこ...

ここ3000字までしか入らないけどタイトルの方がたくさん文字入ると思います。
Epistemic Interaction - tuning interfaces to provide information for AI support

Paper presented at SYNERGY workshop at AVI 2024, Genoa, Italy. 3rd June 2024
https://alandix.com/academic/papers/synergy2024-epistemic/
As machine learning integrates deeper into human-computer interactions, the concept of epistemic interaction emerges, aiming to refine these interactions to enhance system adaptability. This approach encourages minor, intentional adjustments in user behaviour to enrich the data available for system learning. This paper introduces epistemic interaction within the context of human-system communication, illustrating how deliberate interaction design can improve system understanding and adaptation. Through concrete examples, we demonstrate the potential of epistemic interaction to significantly advance human-computer interaction by leveraging intuitive human communication strategies to inform system design and functionality, offering a novel pathway for enriching user-system engagements.
By Design, not by Accident - Agile Venture Bolzano 2024

As presented at the Agile Venture Bolzano, 4.06.2024
GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024

Neha Bajwa, Vice President of Product Marketing, Neo4j
Join us as we explore breakthrough innovations enabled by interconnected data and AI. Discover firsthand how organizations use relationships in data to uncover contextual insights and solve our most pressing challenges – from optimizing supply chains, detecting fraud, and improving customer experiences to accelerating drug discoveries.
20240607 QFM018 Elixir Reading List May 2024

Everything I found interesting about the Elixir programming ecosystem in May 2024
Large Language Model (LLM) and it’s Geospatial Applications

Large Language Model (LLM) and it’s Geospatial Applications.
Elizabeth Buie - Older adults: Are we really designing for our future selves?

Elizabeth Buie - Older adults: Are we really designing for our future selves?
Recently uploaded (20)
GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...

GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...
UiPath Test Automation using UiPath Test Suite series, part 6

UiPath Test Automation using UiPath Test Suite series, part 6
20240609 QFM020 Irresponsible AI Reading List May 2024

20240609 QFM020 Irresponsible AI Reading List May 2024
Goodbye Windows 11: Make Way for Nitrux Linux 3.5.0!

Goodbye Windows 11: Make Way for Nitrux Linux 3.5.0!
How to Get CNIC Information System with Paksim Ga.pptx

How to Get CNIC Information System with Paksim Ga.pptx
GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...

GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...
GraphSummit Singapore | The Future of Agility: Supercharging Digital Transfor...

GraphSummit Singapore | The Future of Agility: Supercharging Digital Transfor...
Monitoring Java Application Security with JDK Tools and JFR Events

Monitoring Java Application Security with JDK Tools and JFR Events
Generative AI Deep Dive: Advancing from Proof of Concept to Production

Generative AI Deep Dive: Advancing from Proof of Concept to Production
Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf

Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf
みなさんこんにちはこれ何文字まで入るの?40文字以下不可とか本当に意味わからないけどこれ限界文字数書いてないからマジでやばい文字数いけるんじゃないの?えこ...

みなさんこんにちはこれ何文字まで入るの?40文字以下不可とか本当に意味わからないけどこれ限界文字数書いてないからマジでやばい文字数いけるんじゃないの?えこ...
Epistemic Interaction - tuning interfaces to provide information for AI support

Epistemic Interaction - tuning interfaces to provide information for AI support
By Design, not by Accident - Agile Venture Bolzano 2024

By Design, not by Accident - Agile Venture Bolzano 2024
GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024

GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024
Large Language Model (LLM) and it’s Geospatial Applications

Large Language Model (LLM) and it’s Geospatial Applications
Elizabeth Buie - Older adults: Are we really designing for our future selves?

Elizabeth Buie - Older adults: Are we really designing for our future selves?
I haz your mouse clicks and key strokes
- 1. I haz your mouse clicks & key strokes Akash Mahajan @ MetaRefresh 2012
- 2. click · jack · ing |klɪk ˈdʒækɪŋ| verb 1. User Interface redress attack, UI redress attack, UI Redressing 2. is when an attacker uses transparent or opaque layers to trick a user into clicking on a button or link on another page when they were intending to click on the top level page. Thus, the attacker is hijacking clicks and/or keystrokes
- 8. How to like anything on Facebook/Internet
- 9. Flash Settings Player : Because SWF files can be iframed!
- 11. FAKE REAL REAL FAKE
- 12. Mitigations • Frame Bursting –Why it fails • X Frames Header
- 13. Frame Bursting / Frame Killers i f ( t o p . l o c a t i o n != l o c a t i o n ) top.location=self.location;
- 14. Best JavaScript code for Frame Bursting <s t y l e >html f v i s i b i l i t y : h i d d e n g</ s t y l e > <s c r i p t > i f ( s e l f == t o p ) f document . documentElement . s t y l e . v i s i b i l i t y = ’visible’; gelsef top.location=self.location; g </ s c r i p t >
- 15. X-Frame-Options • Used to prevent Clickjacking • Doesn’t allow page to be rendered in a frame • DENY : Don’t render at all if inside a frame, SAMEORIGIN : Only if being served from the origin • IE8+, FF4+, Chrome5+
- 16. Akash Mahajan That Web Application Security Guy http://akashm.com | @makash akashmahajan@gmail.com | 9980527182
- 17. References • Keyboard Cat CC NC SA http://www.flickr.com/photos/atomicshark/144630706/sizes/o/in/photostream/ • I haz your mouse clicks and key strokes http://cheezburger.com/6135914240 • Just One question http://www.quickmeme.com/meme/3ow548/ • Slides 6 and 7 from https://www.owasp.org/images/3/31/OWASP_NZ_SEP2011_Clickjacking-for- shells_PDF-version.pdf • http://crypto.stanford.edu/~dabo/pubs/papers/framebust.pdf • (NoScript image source: Andrew Mason's Flickr photostream). • http://erickerr.com/like-clickjacking • http://arnab.org/blog/reputation-misrepresentation • http://erickerr.com/misc/like-clickjacking.js • http://koto.github.com/blog-kotowicz-net-examples/cursorjacking/ • http://www.mniemietz.de/demo/cursorjacking/cursorjacking.html
Editor's Notes
- OWASP DefinitionClickjacking, also known as a "UI redress attack", is when an attacker uses multiple transparent or opaque layers to trick a user into clicking on a button or link on another page when they were intending to click on the the top level page. Thus, the attacker is "hijacking" clicks meant for their page and routing them to other another page, most likely owned by another application, domain, or both.Using a similar technique, keystrokes can also be hijacked. With a carefully crafted combination of stylesheets, iframes, and text boxes, a user can be led to believe they are typing in the password to their email or bank account, but are instead typing into an invisible frame controlled by the attackerWikiPediaClickjacking (User Interface redress attack, UI redress attack, UI redressing) is a malicious technique of tricking a Webuser into clicking on something different to what the user perceives they are clicking on, thus potentially revealing confidential information or taking control of their computer while clicking on seemingly innocuous web pages.[1][2][3][4] It is a browser security issue that is a vulnerability across a variety of browsers and platforms, a clickjack takes the form of embedded code or a script that can execute without the user's knowledge, such as clicking on a button that appears to perform another function.[5] The term "clickjacking" was coined by Jeremiah Grossman and Robert Hansen in 2008.[citation needed]Clickjacking can be understood as an instance of the confused deputy problem.[6]
- Talk about CSS Z OrderHow cursor, keystrokes can be followed
