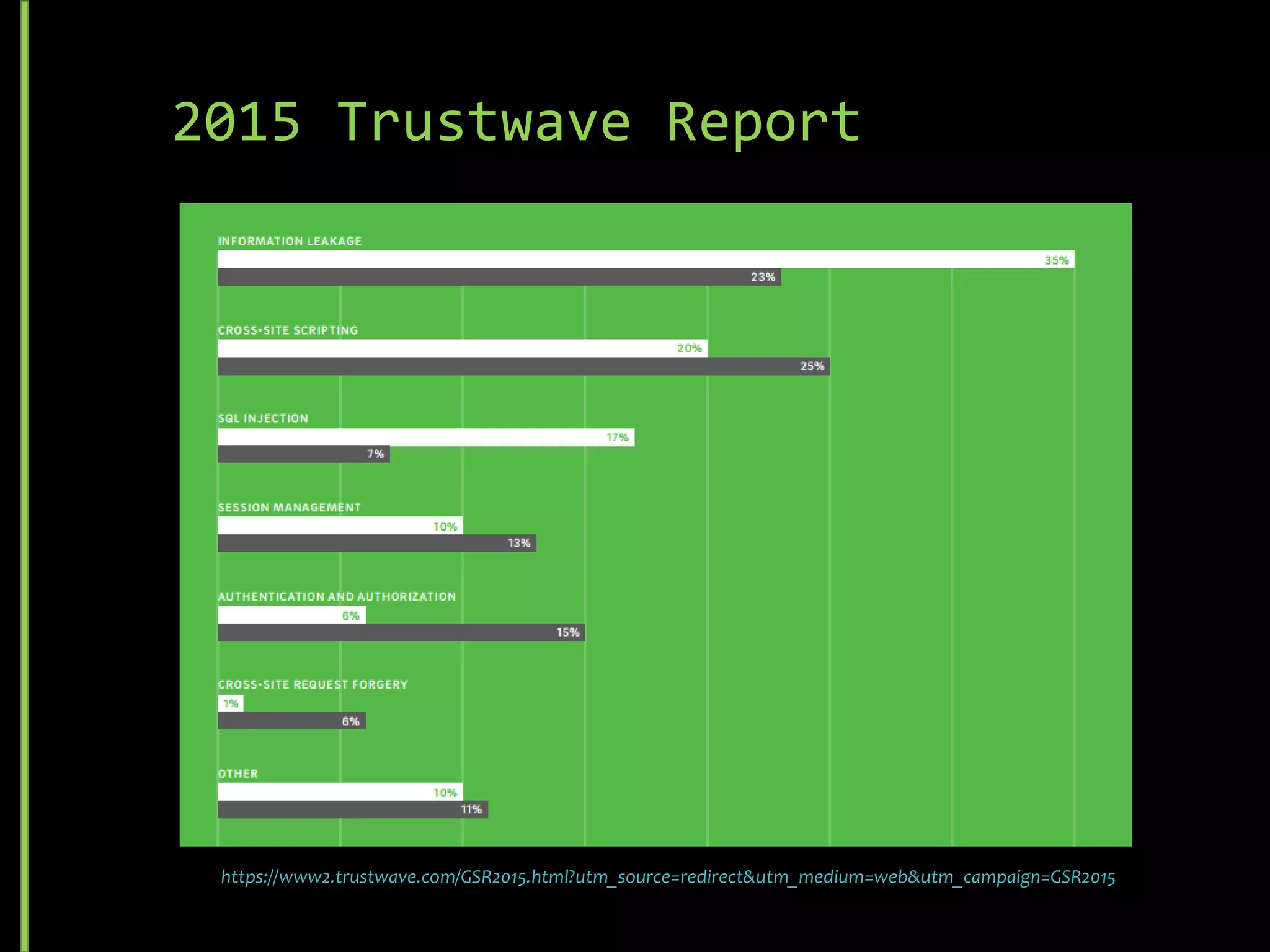
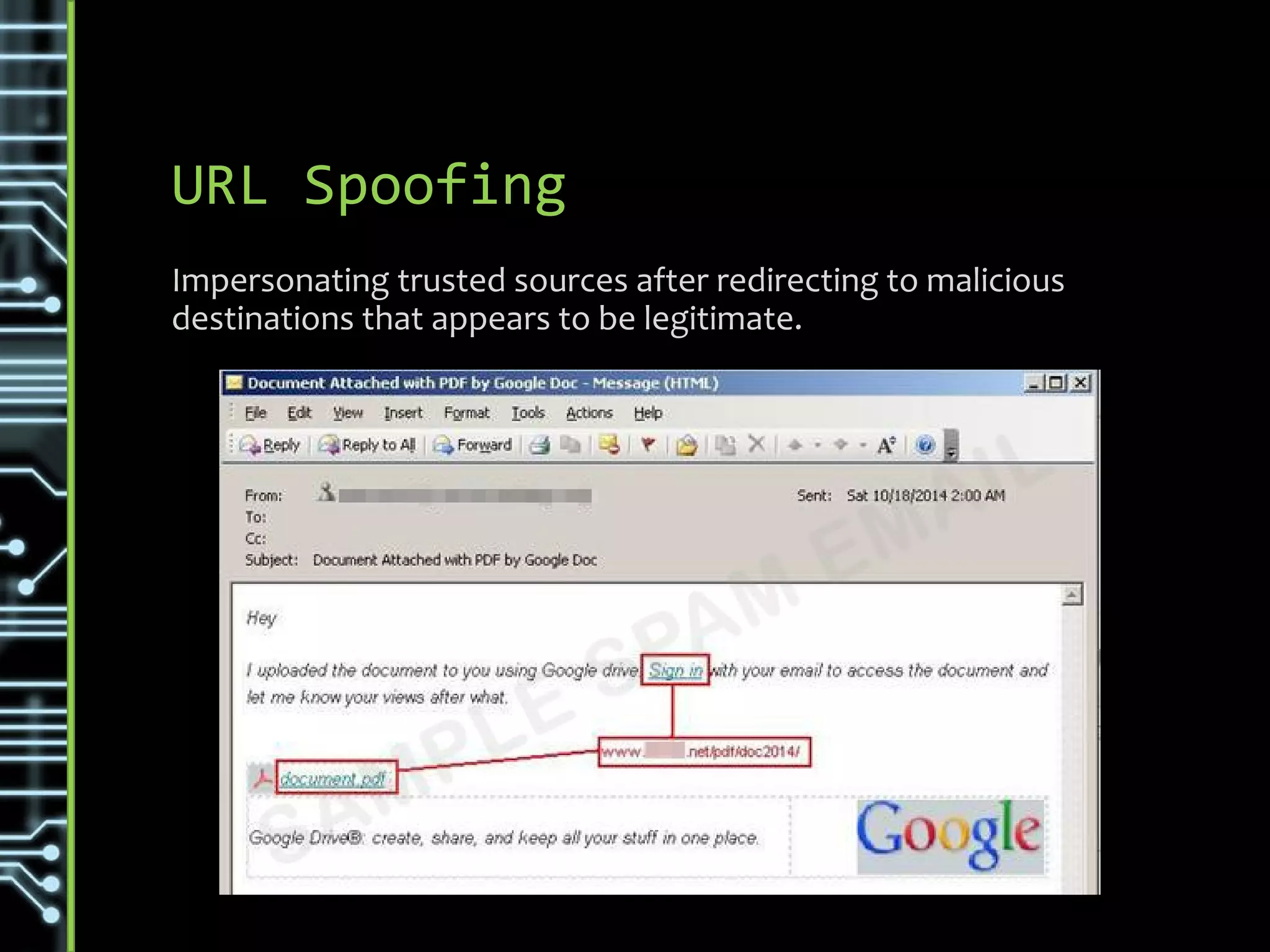
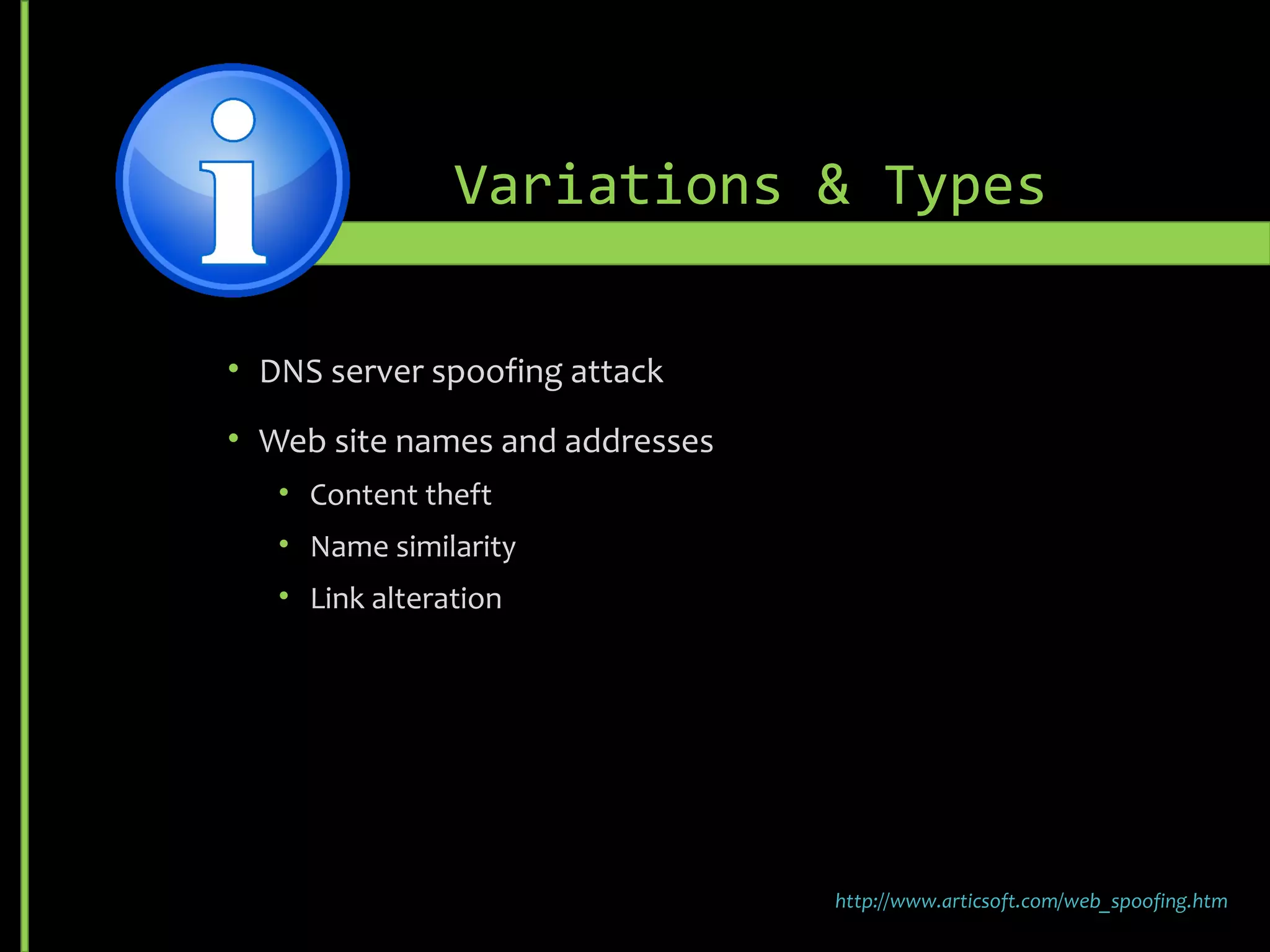
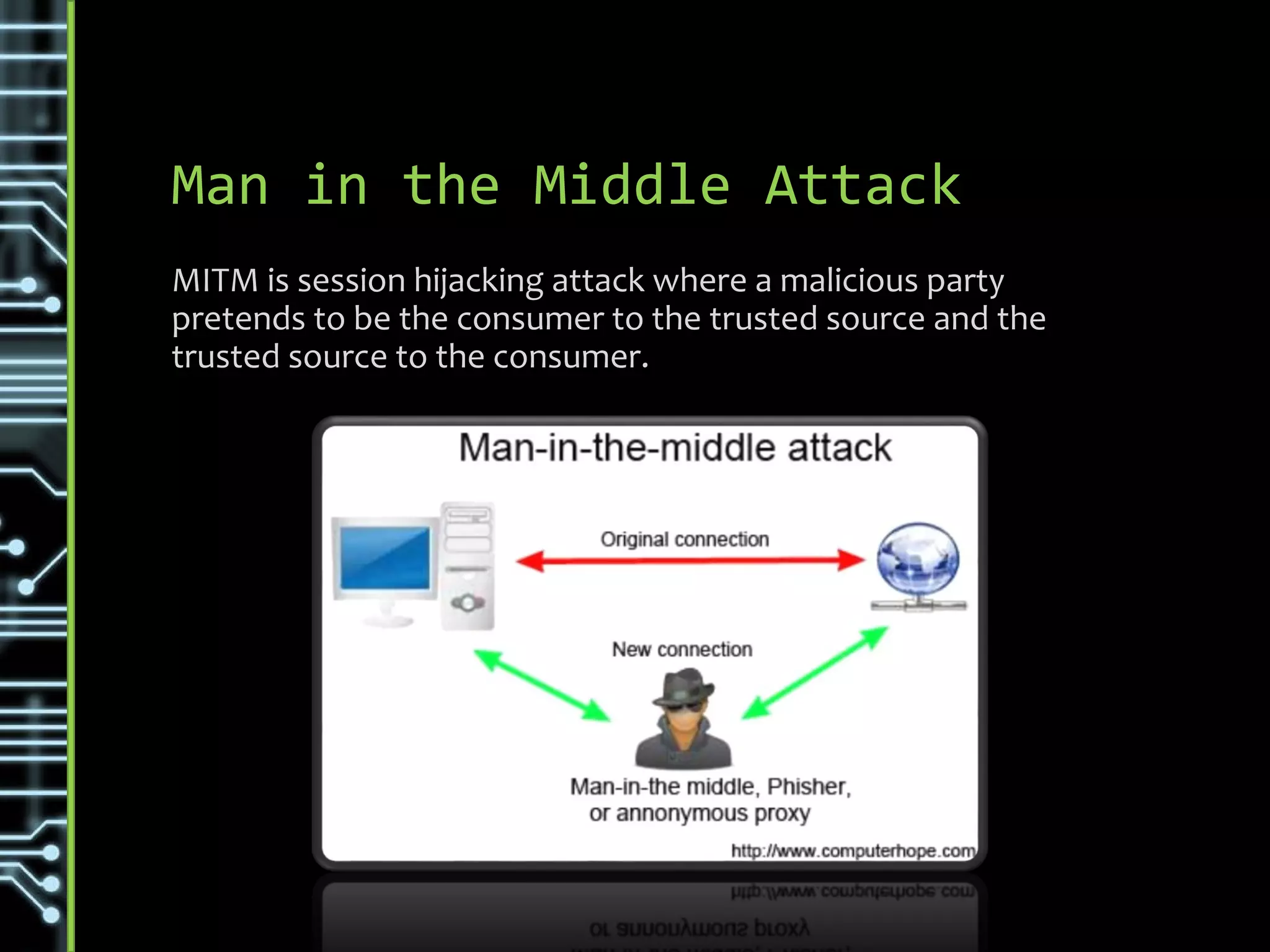
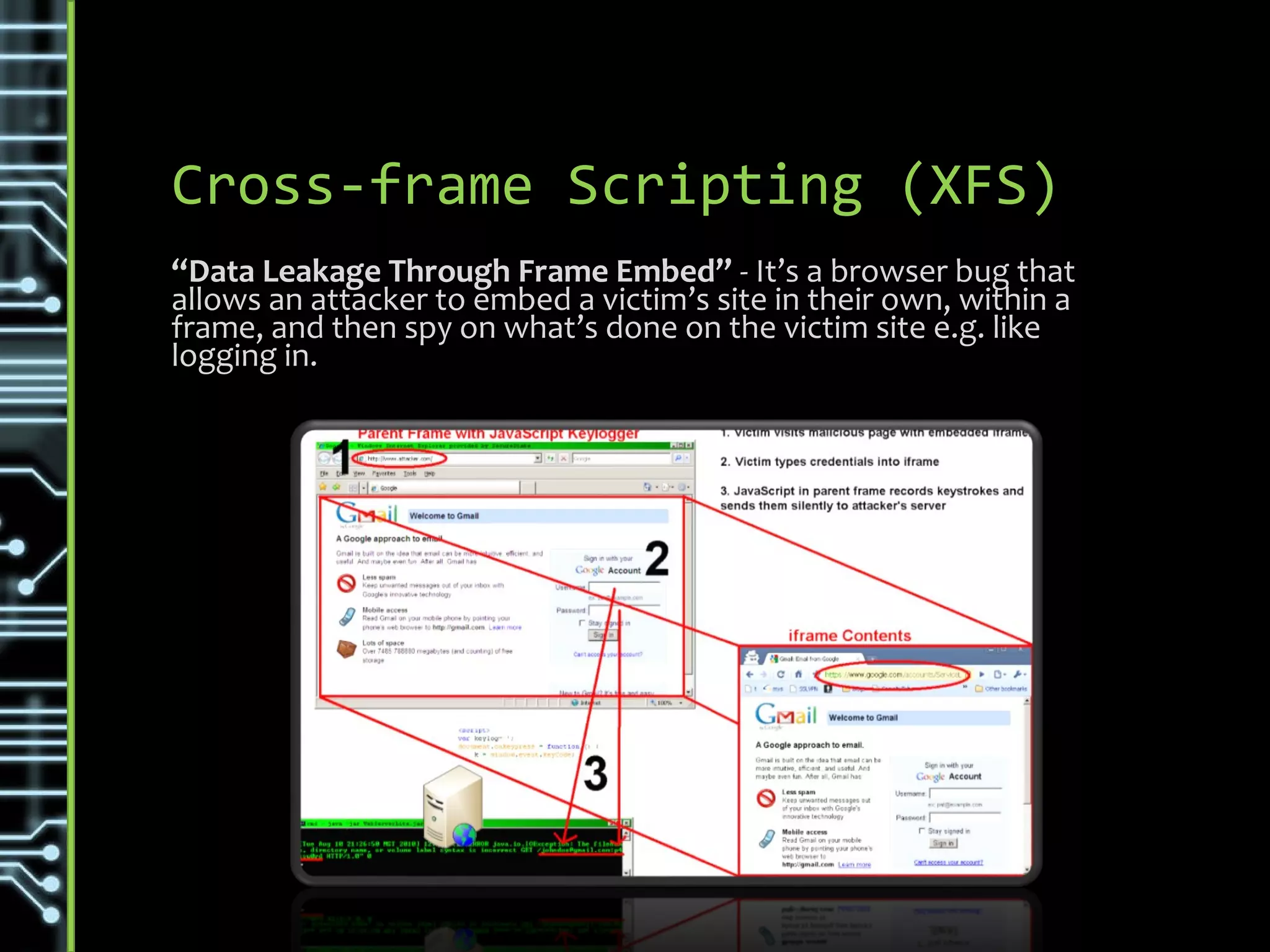
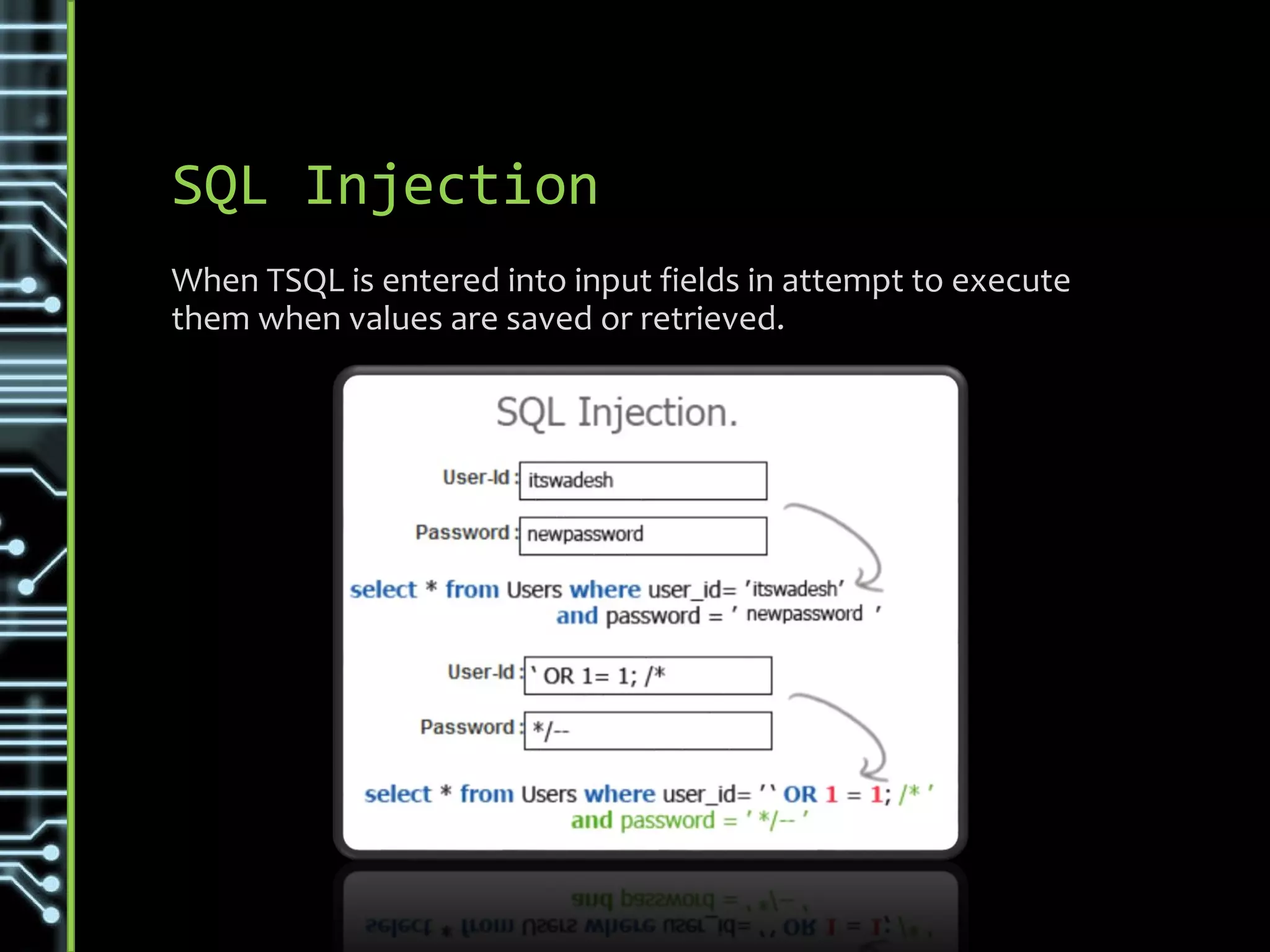
The document discusses common security threats such as URL spoofing, man-in-the-middle attacks, cross-frame scripting, SQL injection, rainbow table matching, denial of service attacks, cross-site scripting, cross-site request forgery, brute force attacks, and dictionary attacks. For each threat, it describes variations, prevention methods such as input validation, access control, and encryption, and detection techniques like monitoring for anomalous behavior.





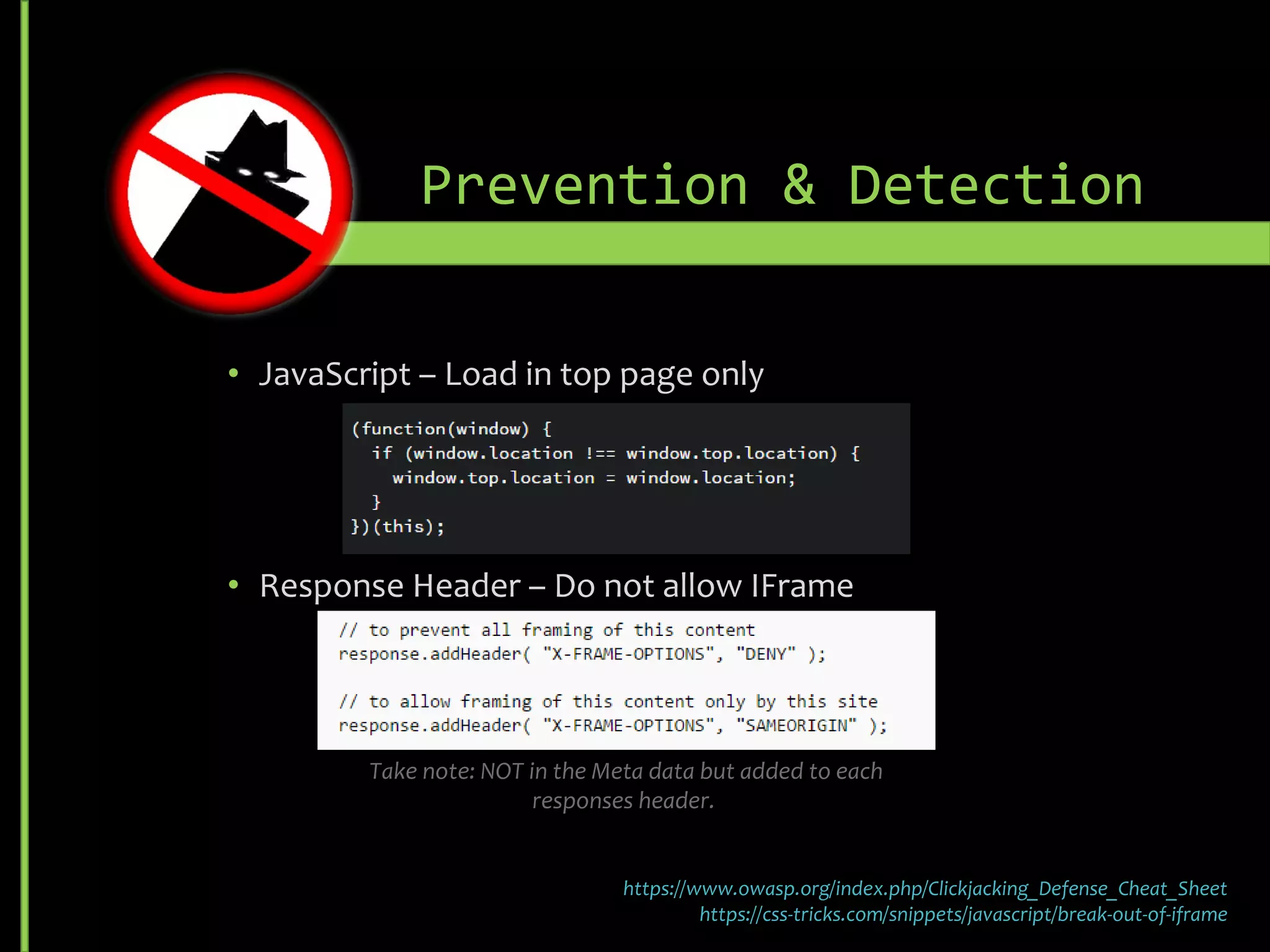
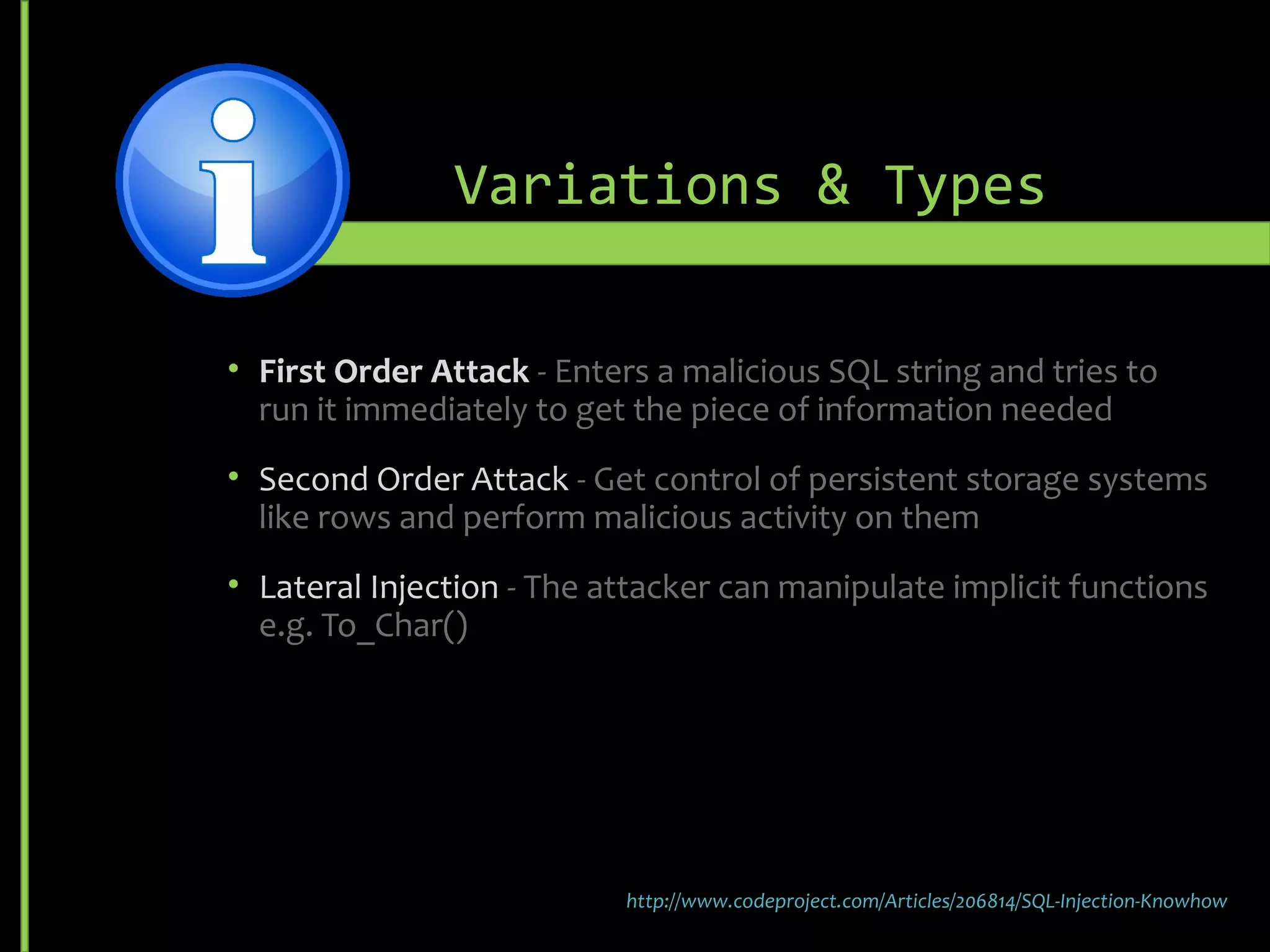
![• Do not execute Dynamic SQL [Query Strings] directly - Use
sp_executesql to parameterize input
• Limit database privileges by context -Do not assign DB Owner
right as Service Account
• Comprehensive data sanitization -Validate user input
Prevention & Detection](https://image.slidesharecdn.com/vulnerabilities-151018214743-lva1-app6891/75/Security-Vulnerabilities-15-2048.jpg)
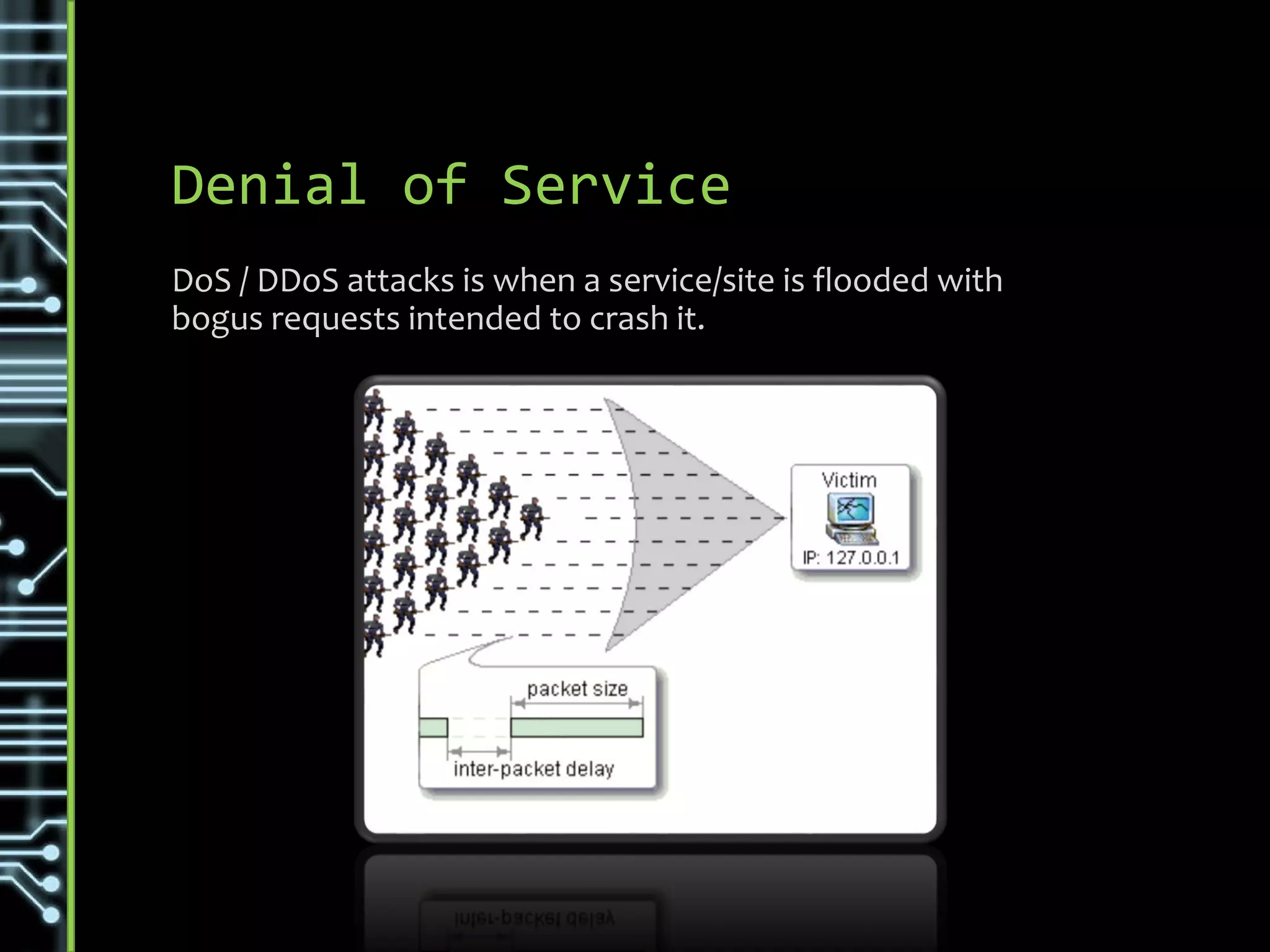
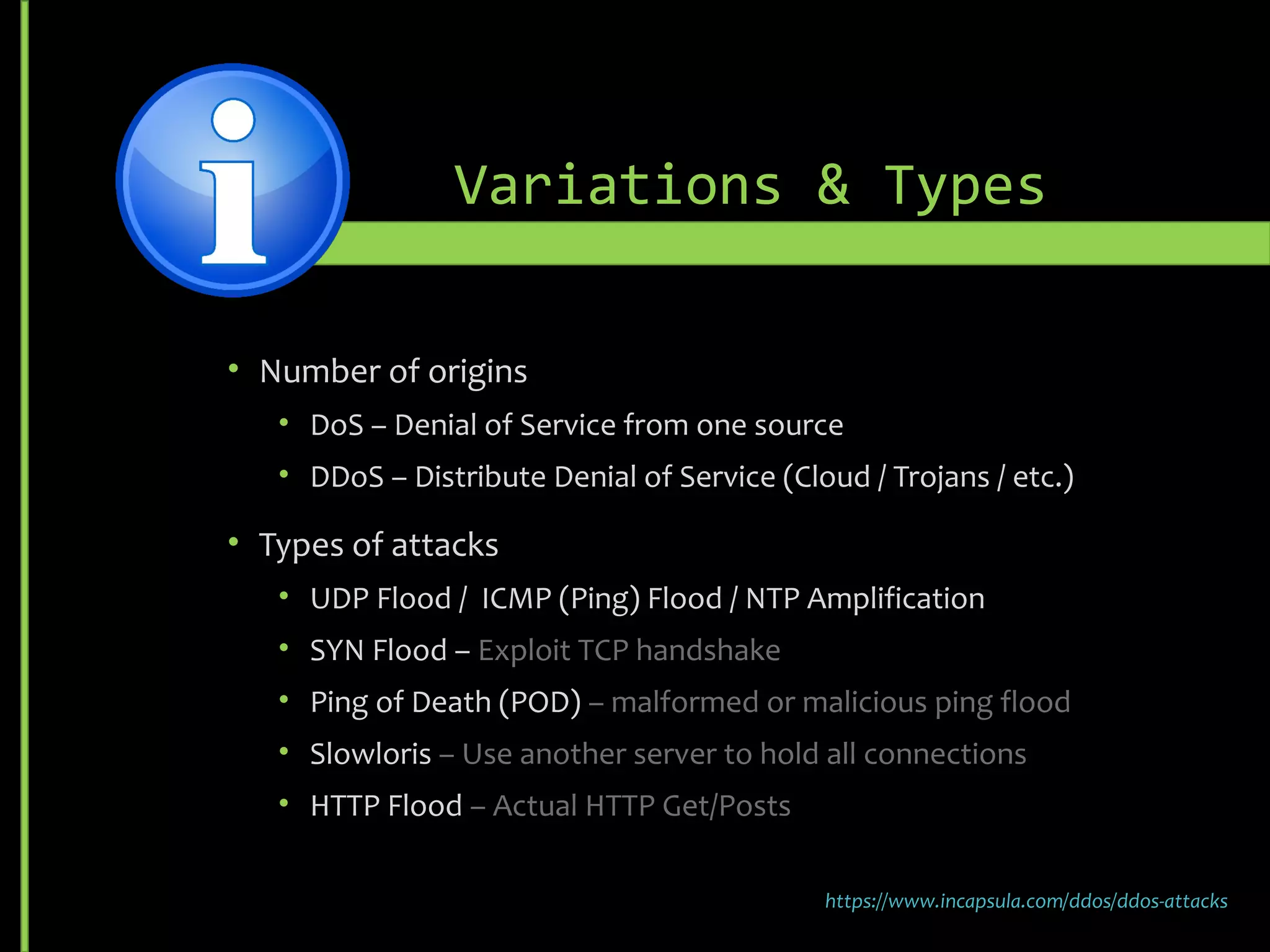

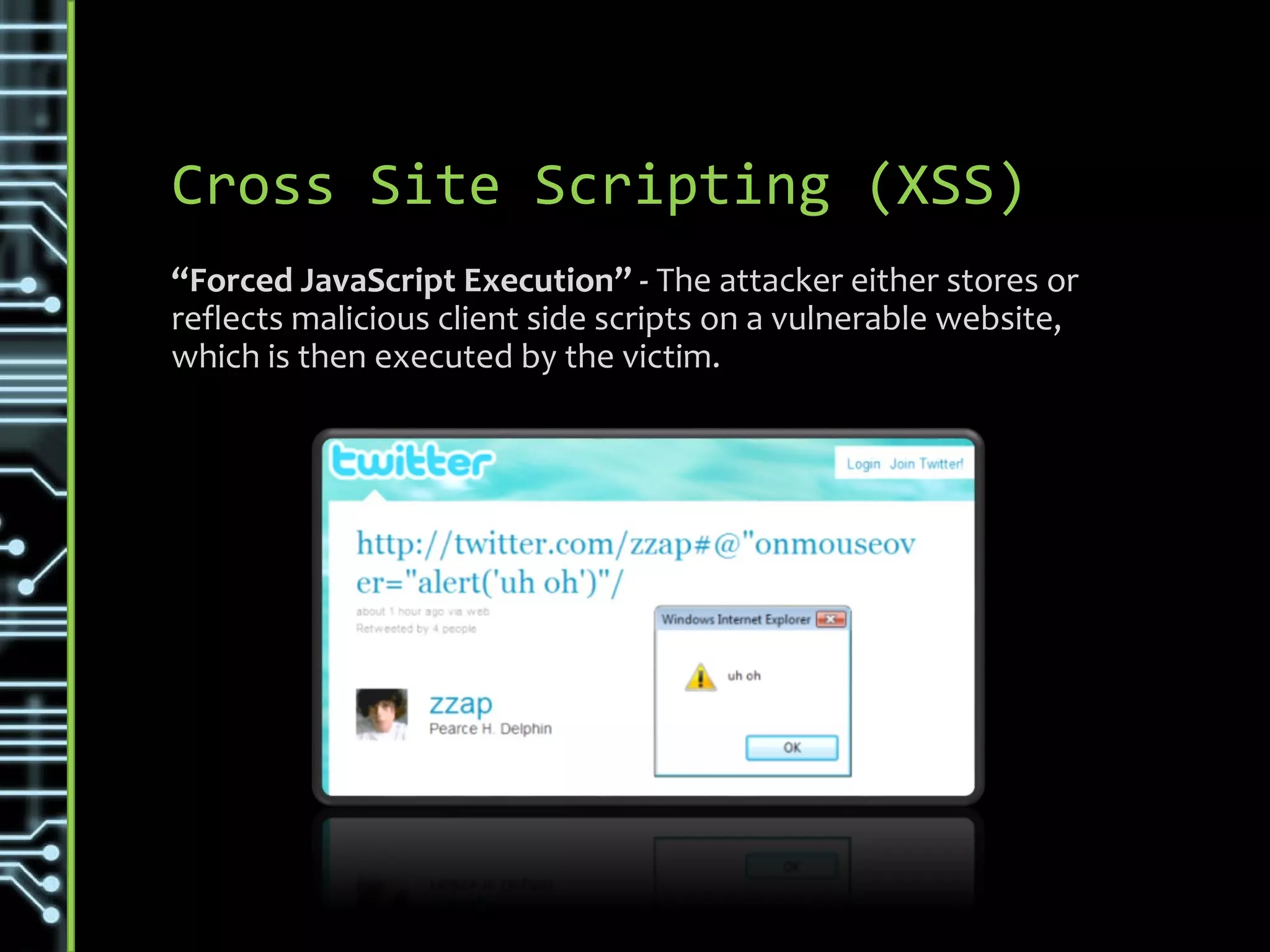


![Variations & Types
• Stored XSS - Input is stored on the target server [E.g. Database]
and then executed when rendered.
• Reflected XSS – When user input is immediately returned by a
web application in an error message [Not Stored]
• DOM Based XSS - The entire tainted data flow happens in the
browser
https://www.owasp.org/index.php/Types_of_Cross-Site_Scripting](https://image.slidesharecdn.com/vulnerabilities-151018214743-lva1-app6891/75/Security-Vulnerabilities-23-2048.jpg)











