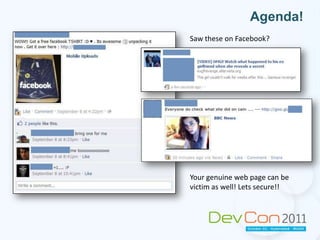
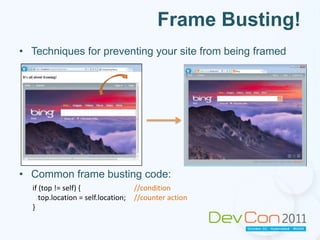
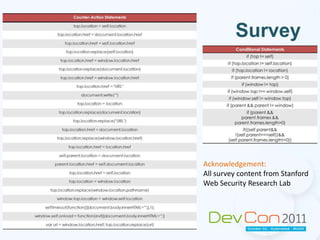
The document summarizes techniques for preventing clickjacking attacks, including frame busting code, the X-Frame-Options HTTP header, and Content Security Policy. It provides examples of how to implement these techniques and their limitations. It encourages attendees to check their own websites and applications for clickjacking vulnerabilities and ways to secure them against these risks.