Embed presentation





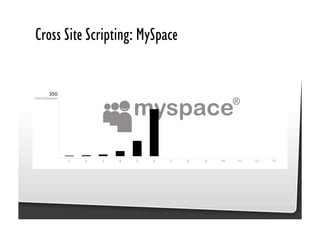
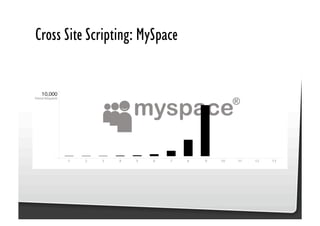
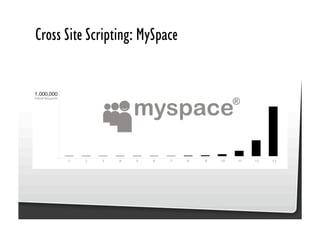
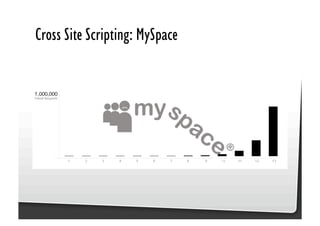
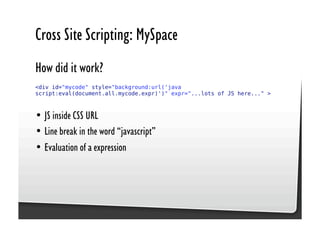
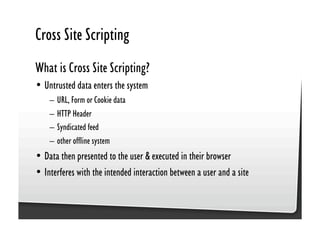




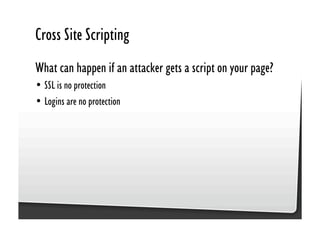
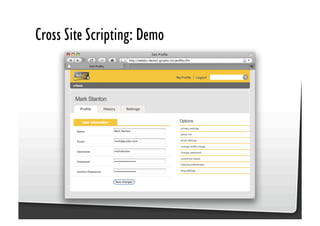
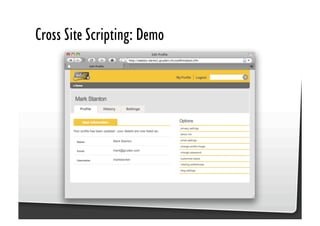
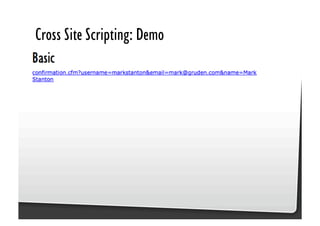
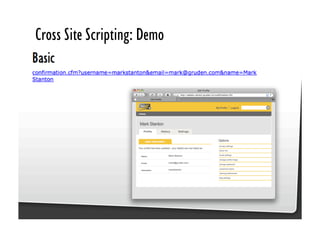
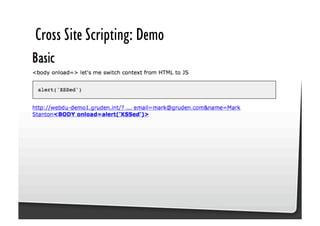
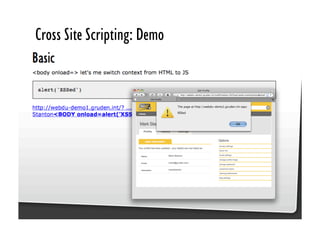
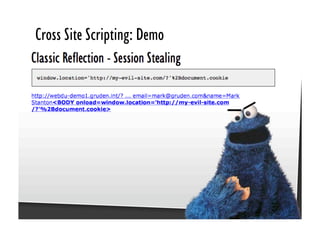
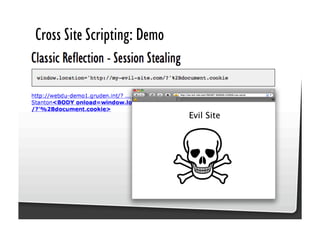
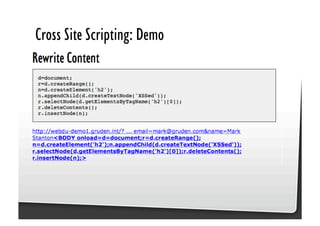
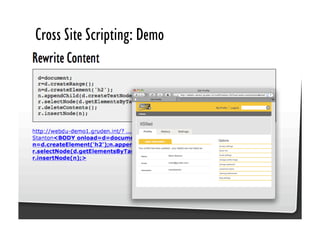
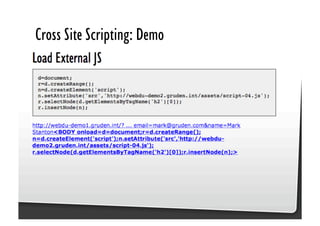
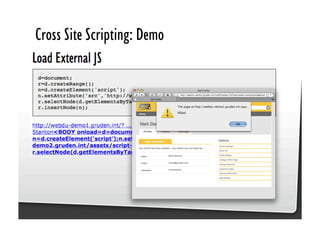
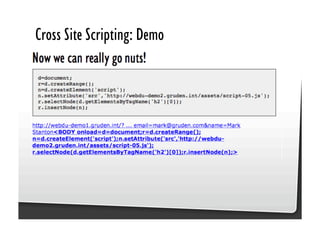
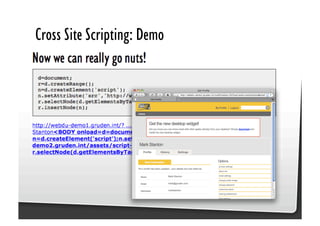
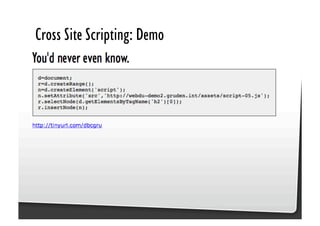
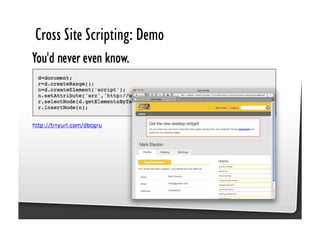
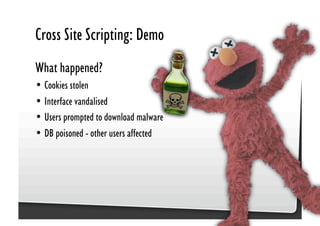

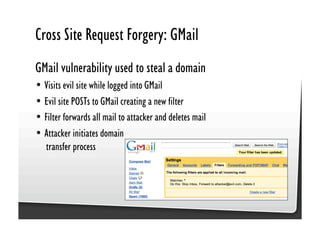
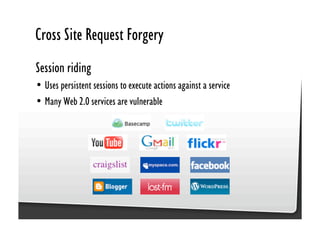


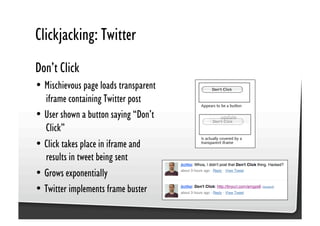




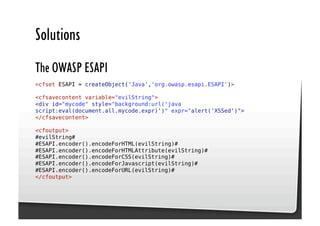

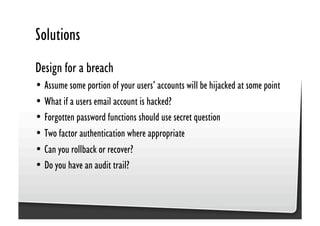
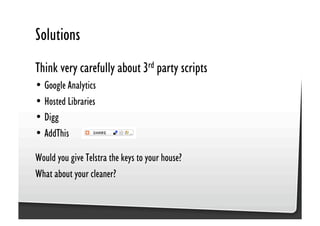





This document discusses common JavaScript security vulnerabilities like cross-site scripting (XSS), cross-site request forgery (CSRF), and clickjacking. It defines these issues and provides examples of real attacks. The document also outlines solutions for developers, including sanitizing input, escaping output, minimizing the attack surface, and designing with the assumption of breaches. Overall it stresses the importance of a holistic, multi-layered approach to JavaScript security.




















































