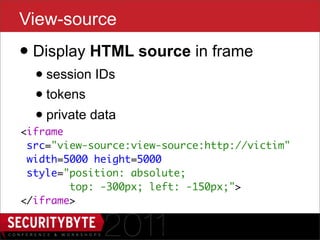
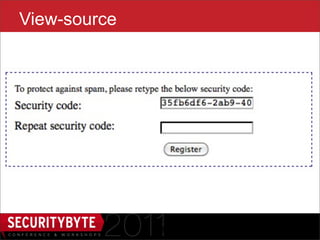
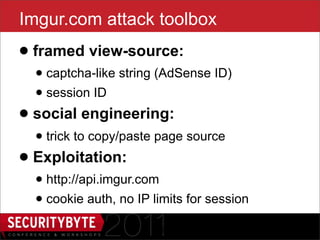
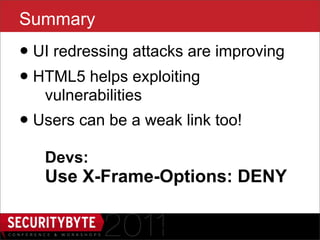
The document discusses the security risks associated with HTML5, particularly focusing on the Same Origin Policy and various attack methods such as clickjacking, cross-origin resource sharing, and silent file uploads. It highlights how user behavior and browser vulnerabilities can be exploited to launch effective attacks, emphasizing the importance of developers implementing security measures like x-frame-options. Overall, it underscores the evolving nature of UI redressing attacks and the need for increased security awareness among users and developers.


















![Drag out content extraction
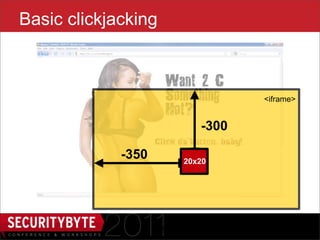
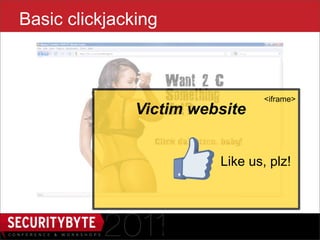
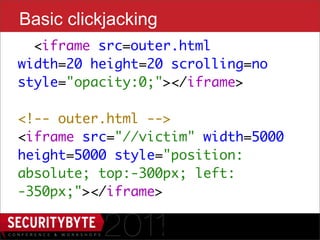
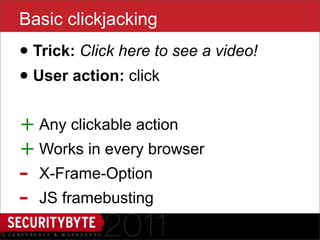
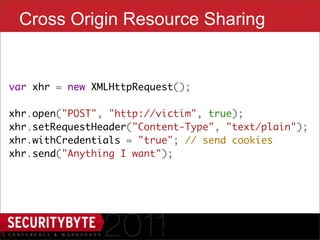
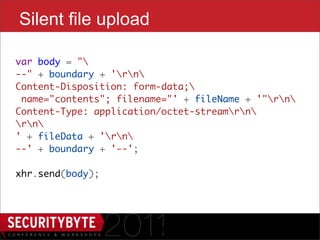
$("#iframe").attr('src', 'outer.html’);
$('#dropper').bind('drop', function() {
setTimeout(function() {
var urlmatch = $("#dropper").val()
.match(/token=([a-h0-9]+)$/);
if (urlmatch) {
var token = urlmatch[1];
// do EVIL
}
}, 100);
});
37](https://image.slidesharecdn.com/html5-somethingwickedthiswaycomes-110914134541-phpapp02/85/Html5-something-wicked-this-way-comes-37-320.jpg)