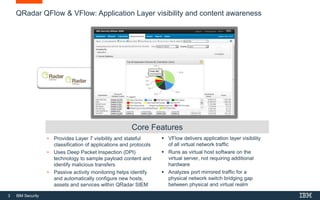
IBM's QFlow and VFlow offer deep application visibility through layer 7 traffic capture and analysis, facilitating enhanced network, application, and user monitoring. These tools integrate with QRadar SIEM for improved security intelligence and can detect threats such as zero-day attacks while ensuring compliance and thorough forensic investigations. Key features include deep packet inspection, stateful application classification, and passive monitoring for asset profiling.