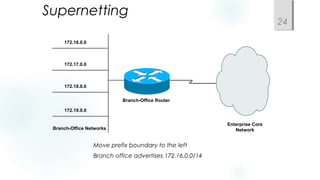
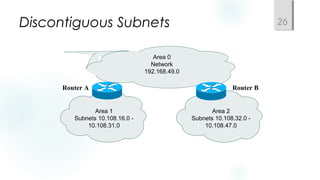
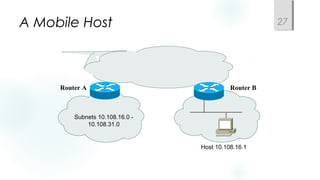
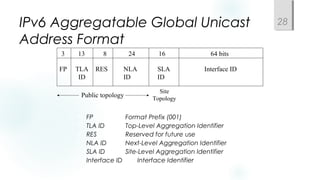
Structured models for addressing and naming make networks easier to operate and manage. Addressing and naming schemes should be assigned hierarchically from a central or distributed authority. Public IP addresses are assigned by regional internet registries, while private addresses like 10.0.0.0/8 and 172.16.0.0/12 are non-routable and used internally. The choice of static versus dynamic addressing depends on factors like network size, availability needs, and whether additional configuration is required.