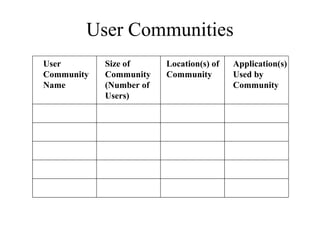
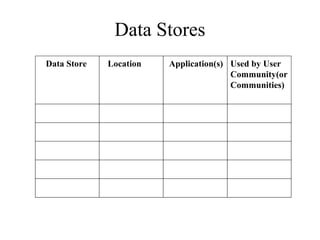
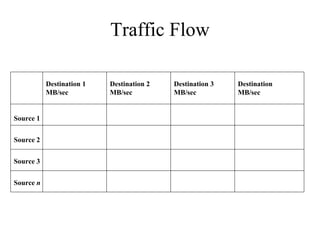
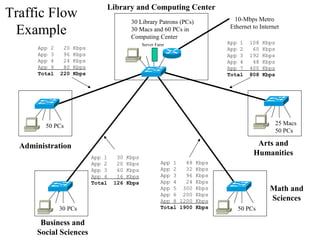
1. The document discusses factors to characterize such as traffic flow, location of sources and data stores, traffic load, behavior, and QoS requirements.
2. It describes different types of traffic flows including terminal/host, client/server, thin client, peer-to-peer, server/server, and distributed computing.
3. Quality of service requirements are discussed for ATM services and IETF differentiated and integrated services specifications.