This document discusses principles for designing network topologies, including:
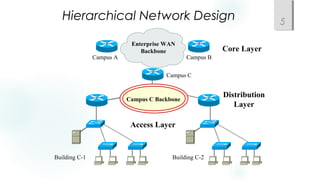
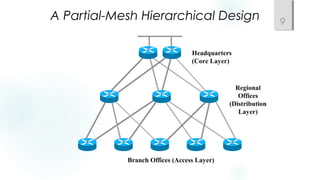
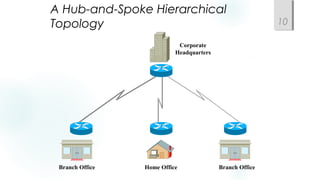
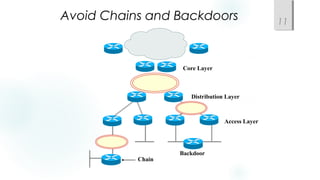
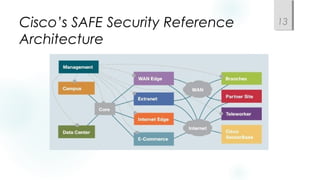
- Using a hierarchical design with core, distribution, and access layers to reduce workload on devices and facilitate scaling. This includes Cisco's common three-layer model.
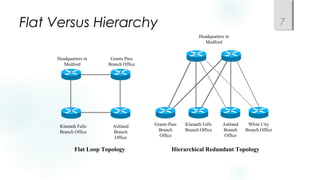
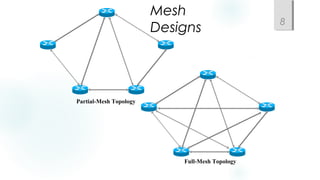
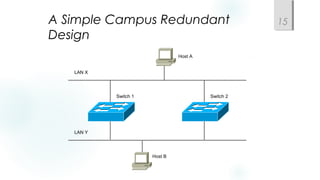
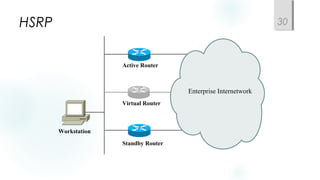
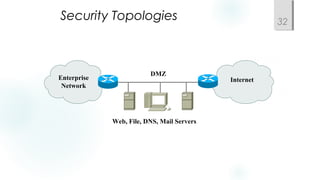
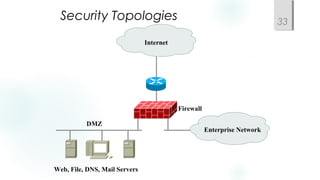
- Incorporating redundancy, modularity, and well-defined entry/exit points for protection and simplicity.
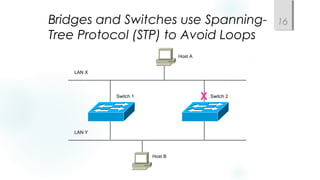
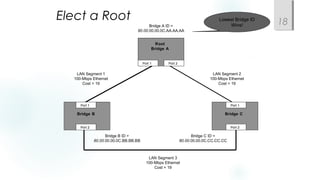
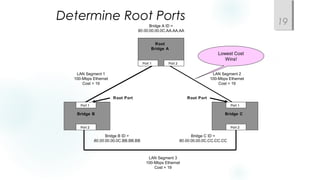
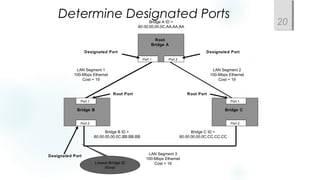
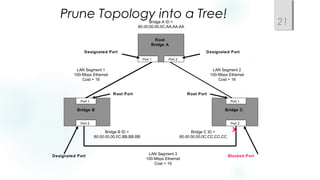
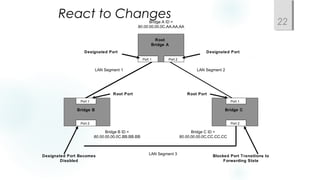
- Spanning Tree Protocol (STP) is used to prevent loops by pruning blocked ports and electing a root bridge, root ports and designated ports on switches. STP must be scaled carefully in large networks.