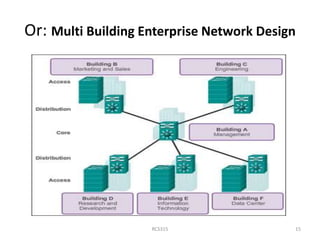
This document discusses network design principles and methodology. It begins by outlining the goals of network design which include scalability, availability, security and manageability. It then describes the network design process which involves identifying requirements, characterizing the existing network, and designing the network topology. A key part of the design is implementing a hierarchical architecture with core, distribution and access layers. The core layer is responsible for high-speed data transfer between sections and requires redundancy, load balancing and fast converging routing protocols to minimize downtime. Careful planning is needed to prevent failures and reduce human error.