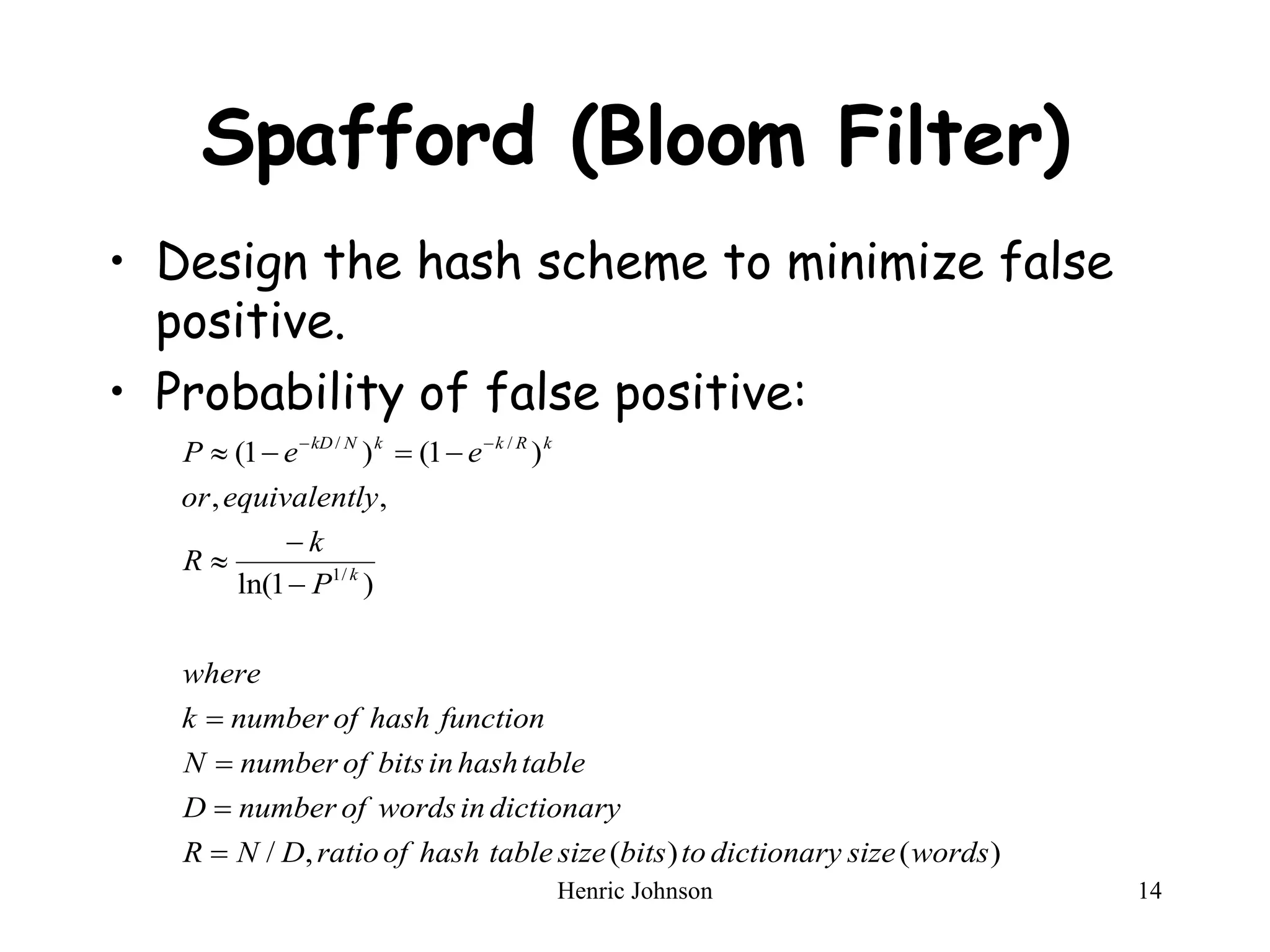
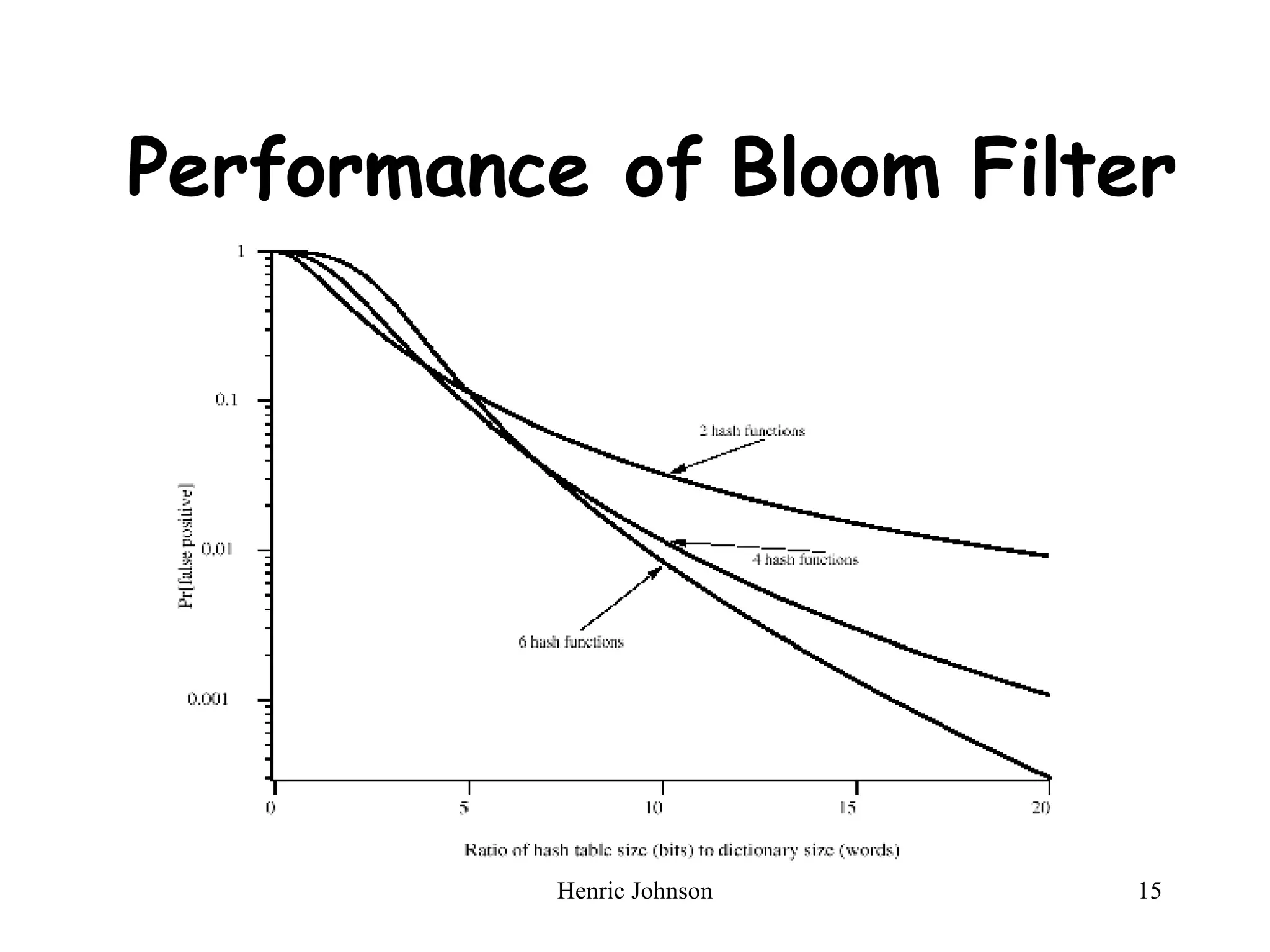
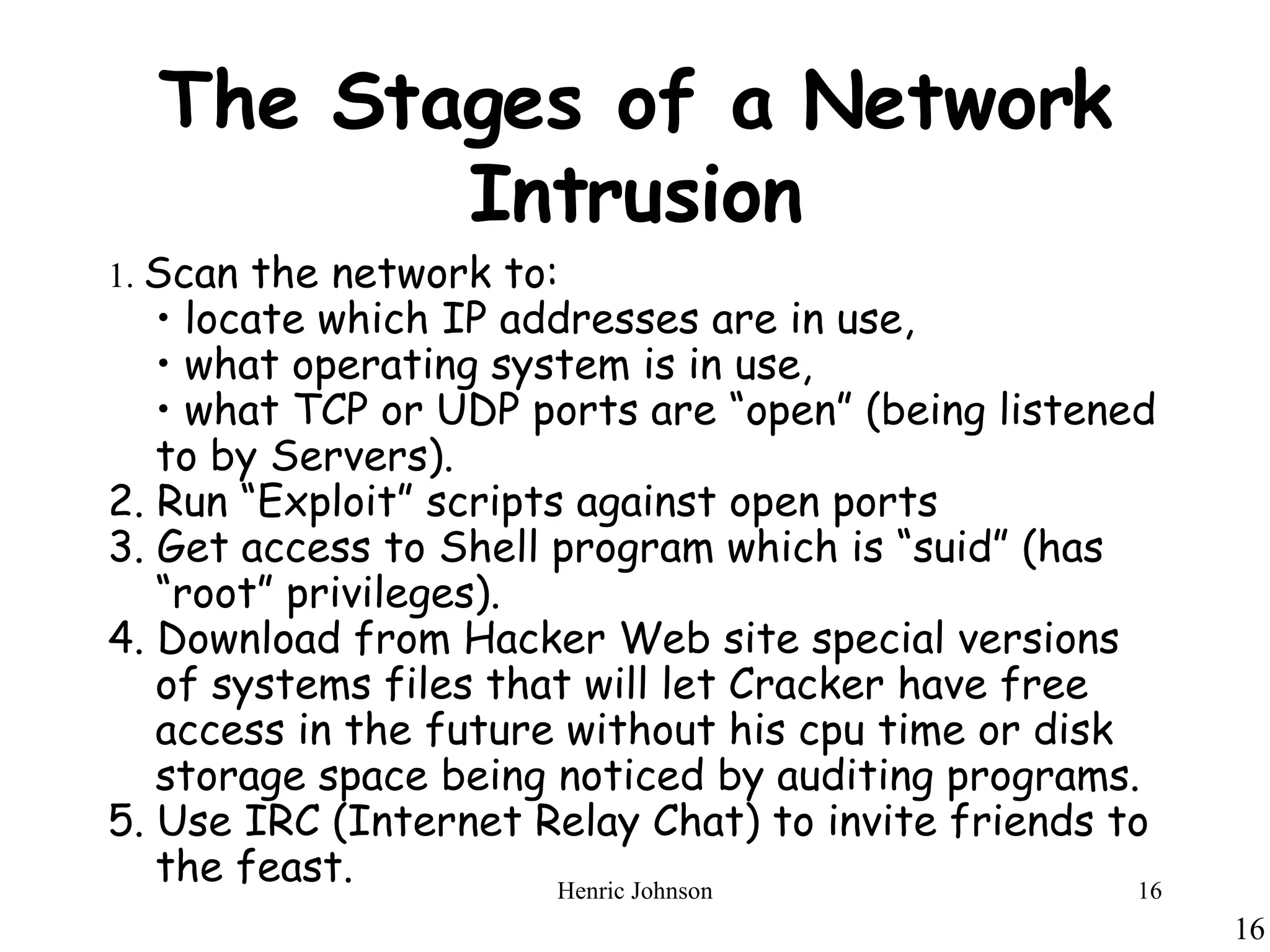
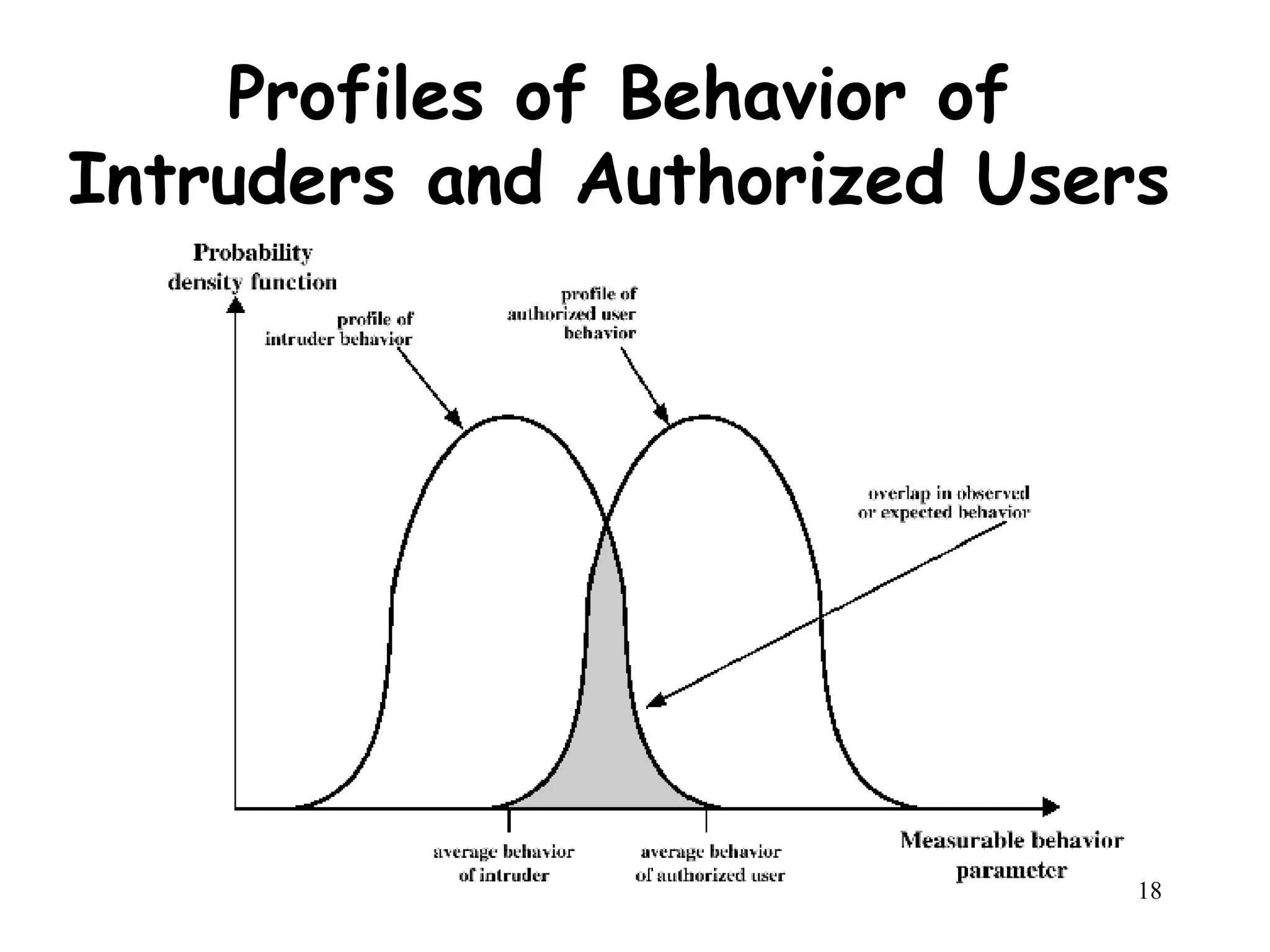
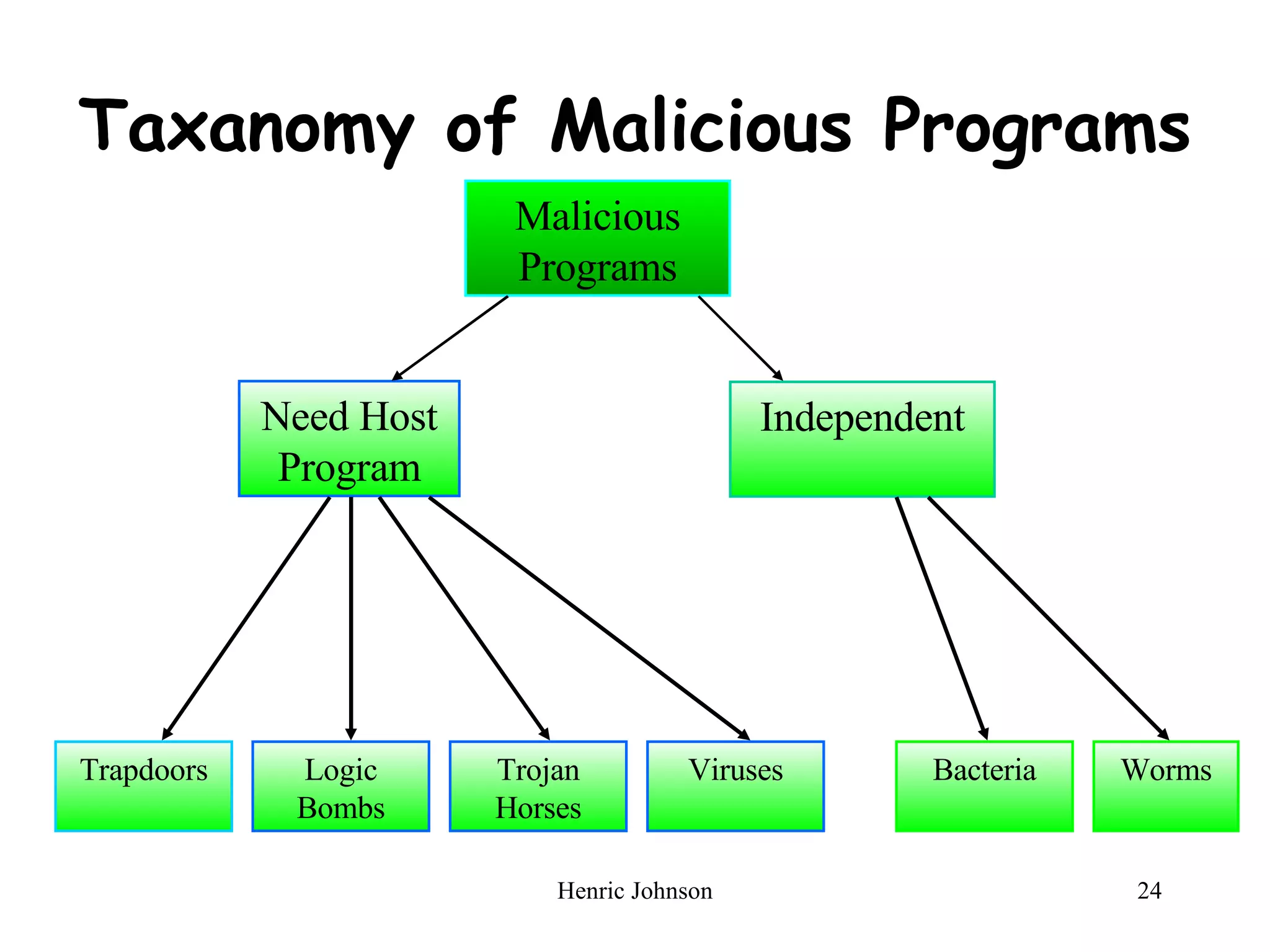
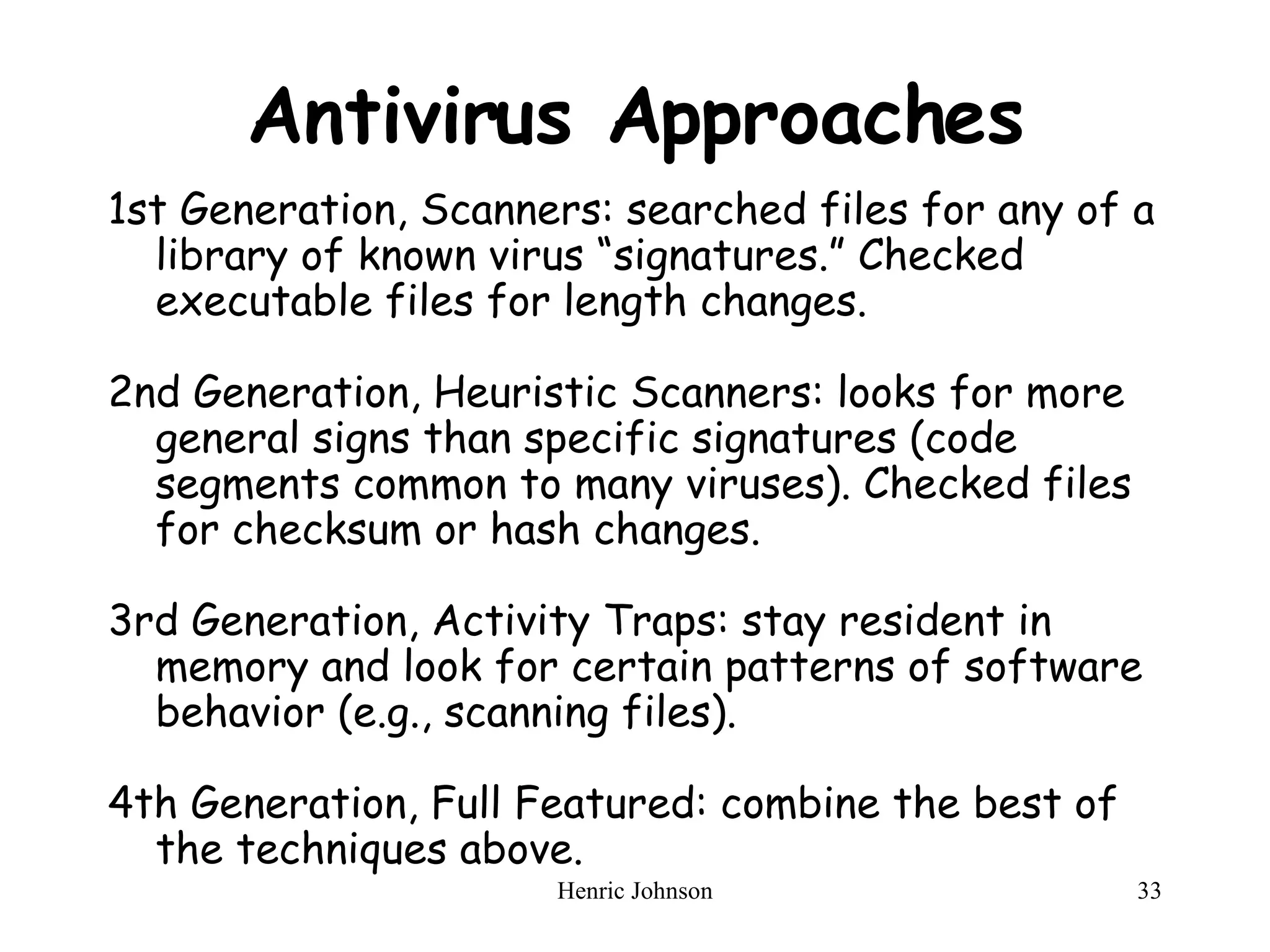
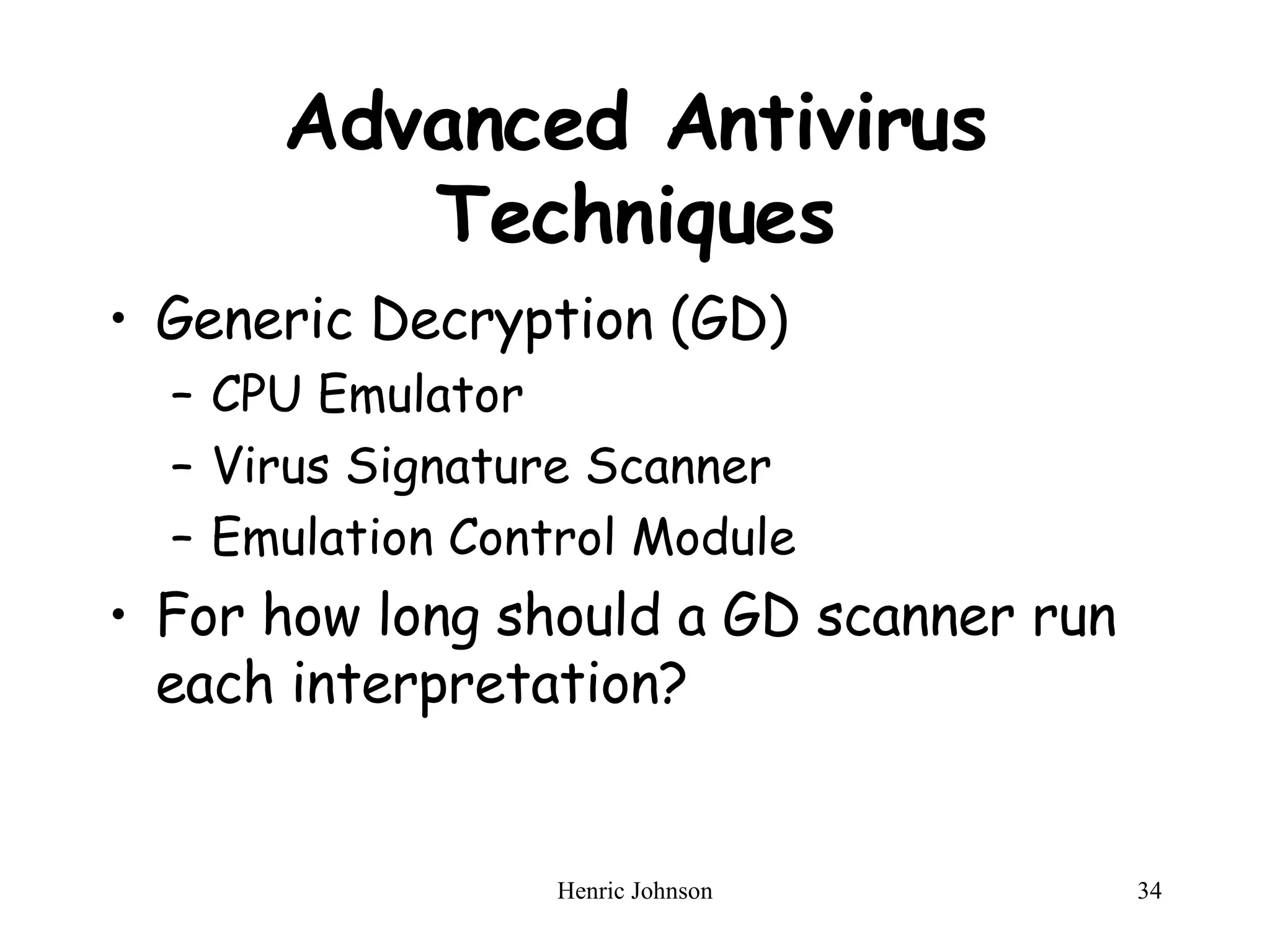
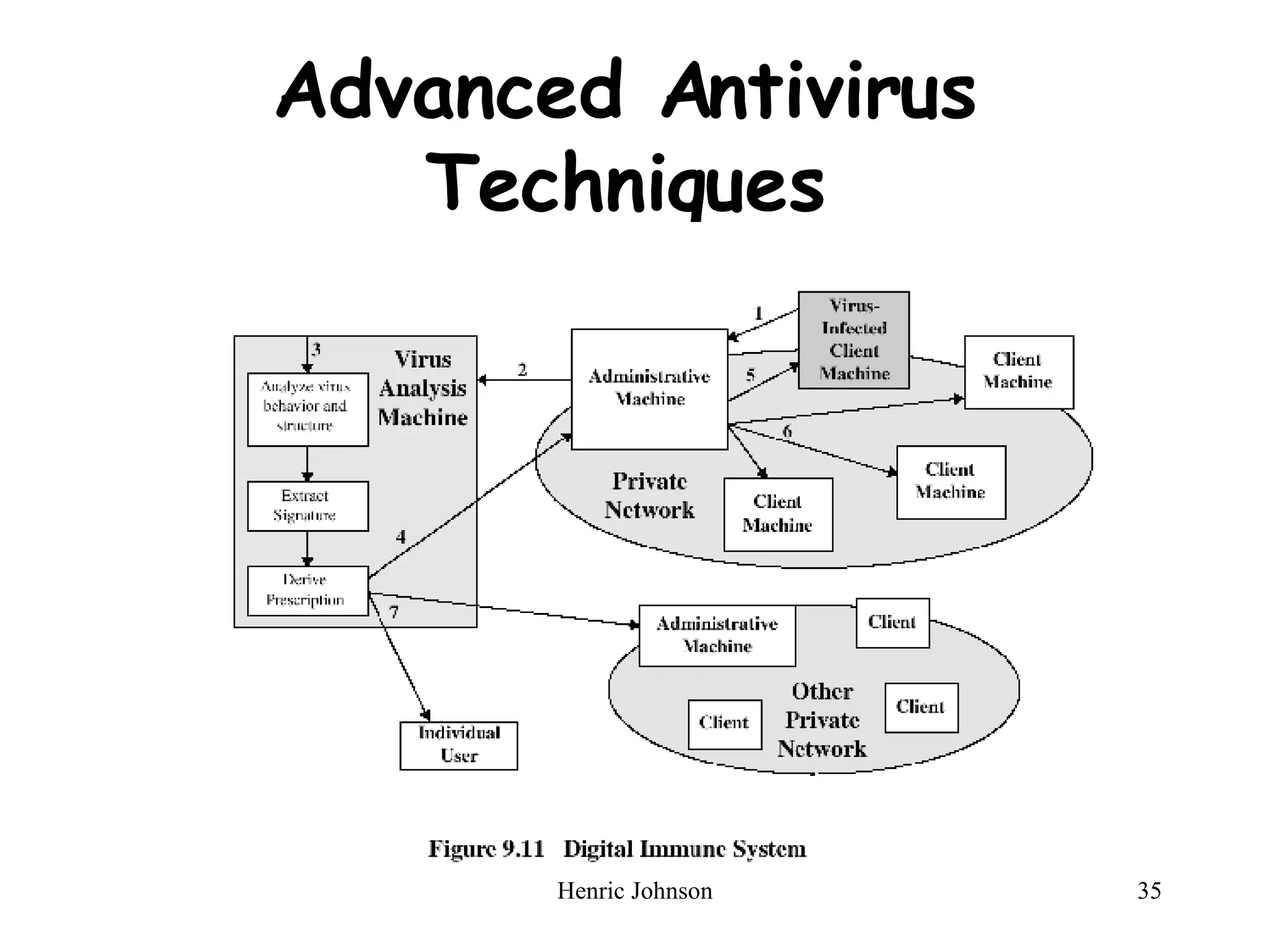
The document provides an overview of intruders, intrusion techniques, password protection, viruses, and antivirus approaches. It discusses different types of intruders and how they try to guess passwords. It also describes techniques for detecting intrusions and protecting against viruses, including how viruses spread and different types of malicious programs. The document recommends combining signature scanning, heuristic analysis, activity monitoring, and emulation to provide effective antivirus protection.
![Chapter 9 Intruders and Viruses Henric Johnson Blekinge Institute of Technology, Sweden http://www.its.bth.se/staff/hjo/ [email_address]](https://image.slidesharecdn.com/chapter-ns9-28067/75/Intruders-and-Viruses-in-Network-Security-NS9-1-2048.jpg)