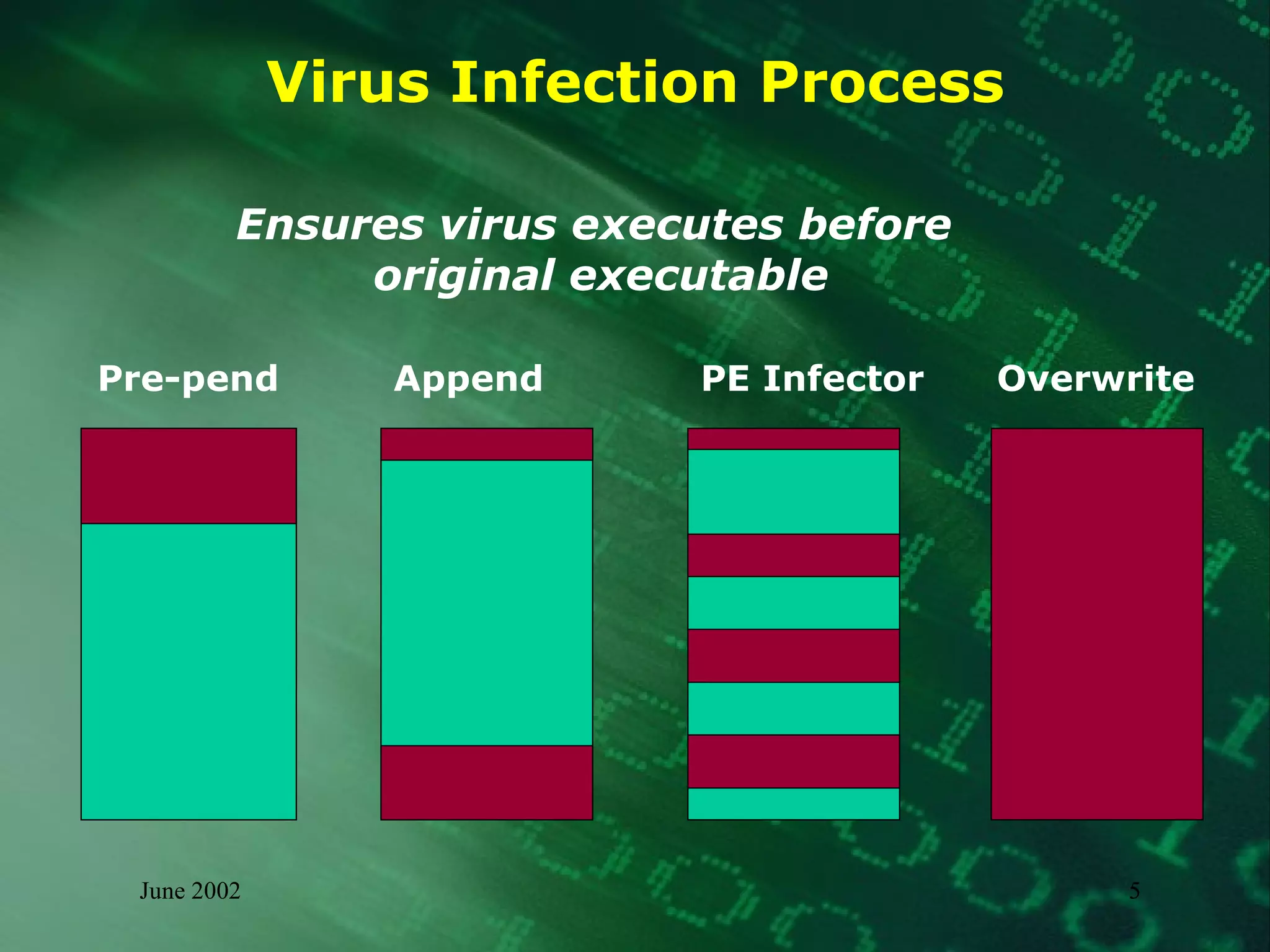
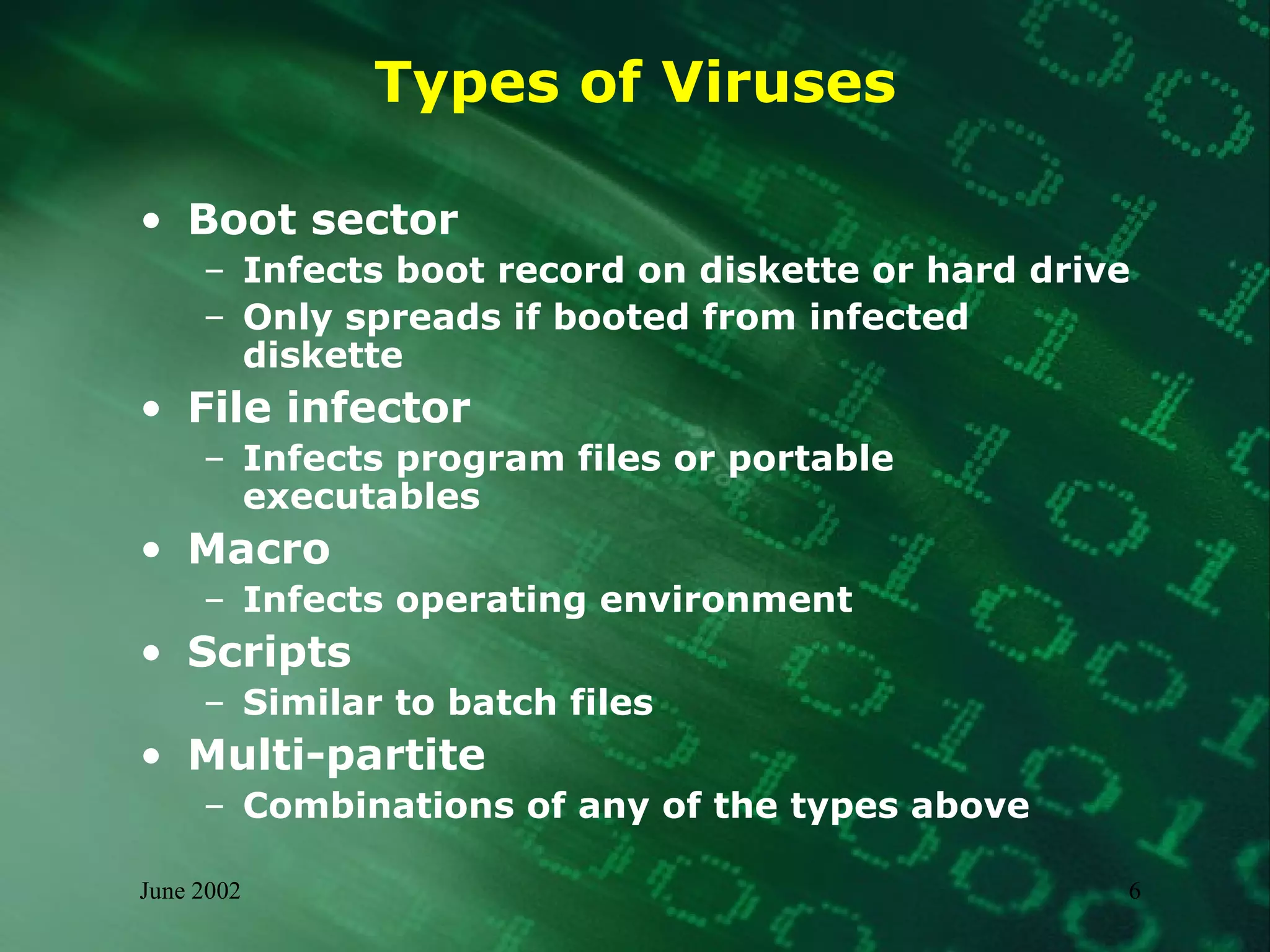
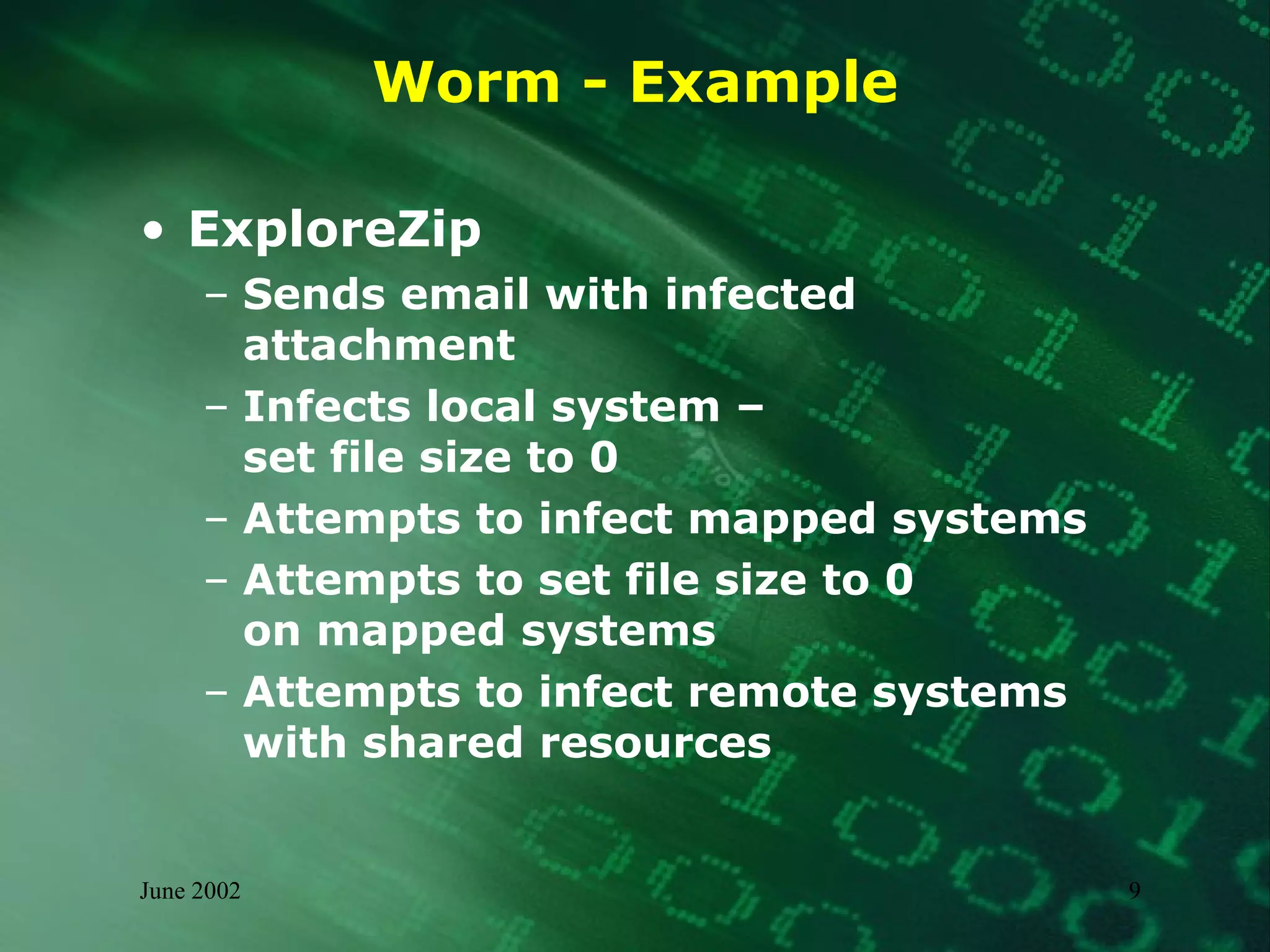
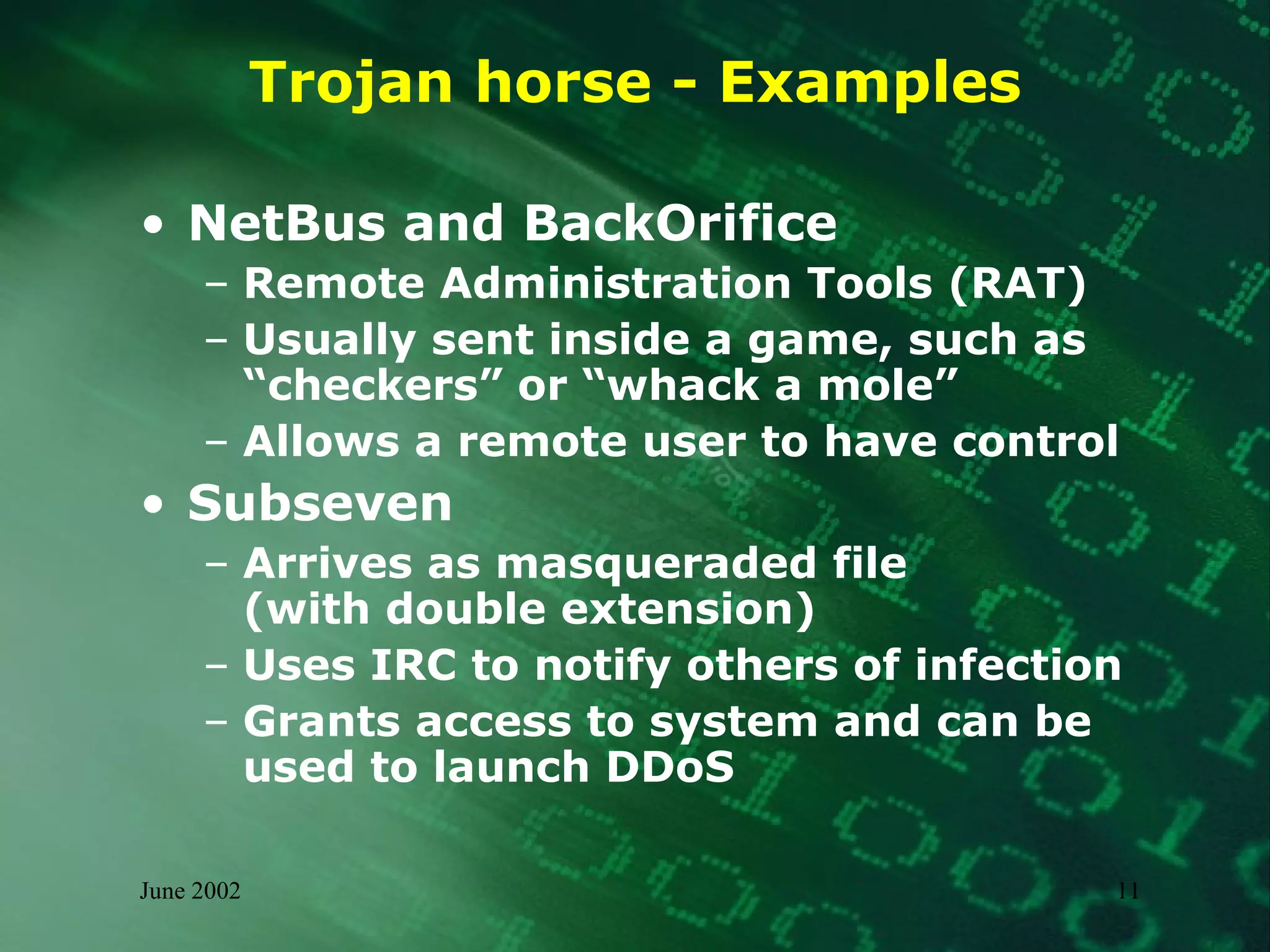
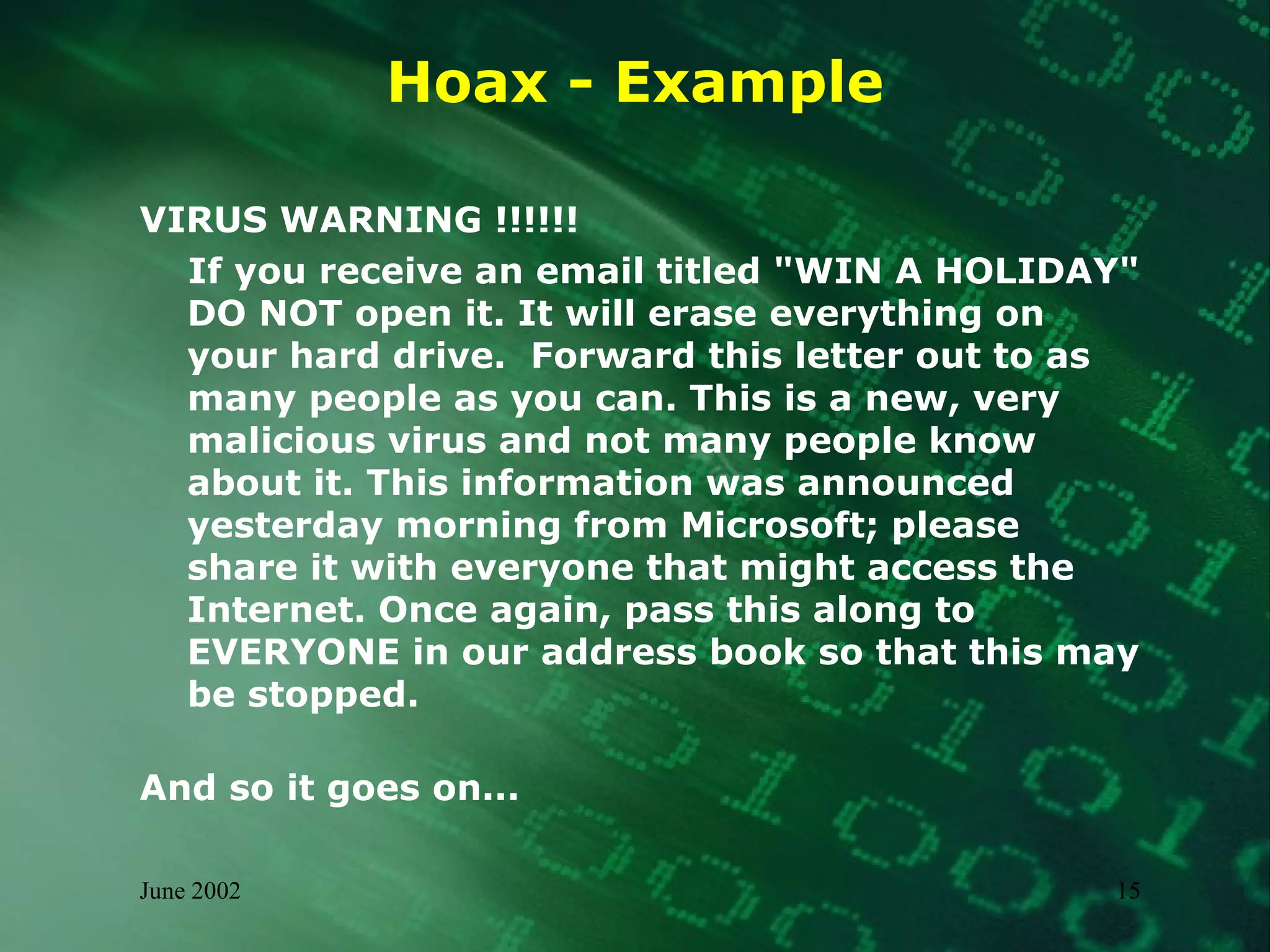
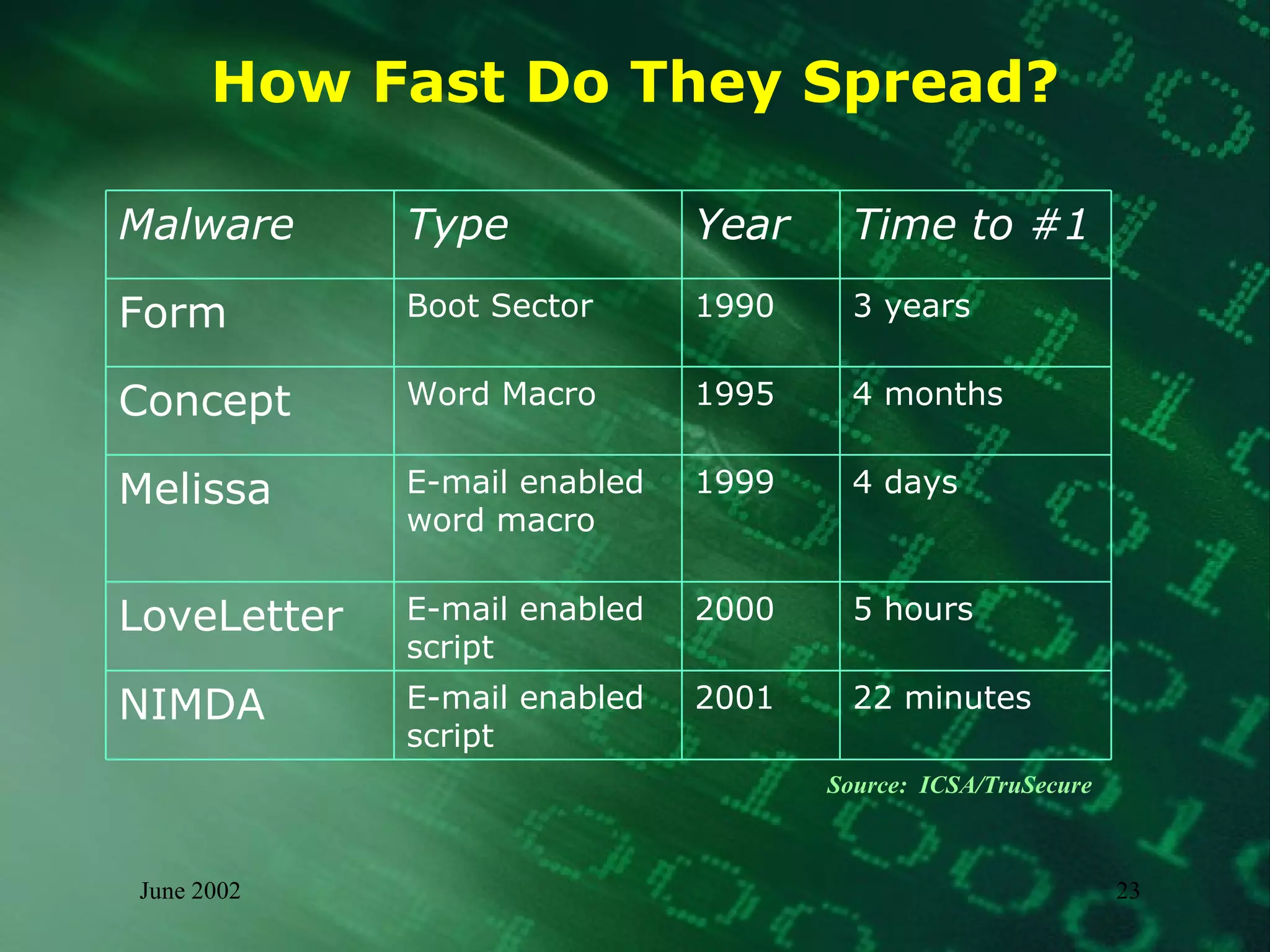
This document summarizes information about malware threats, including viruses, worms, Trojan horses, joke programs, hoaxes, and logic bombs. It discusses the types and examples of different malware, how they spread, their potential impacts, and an incident management model for preparation, detection, containment, eradication, recovery, and reporting of malware incidents. The summary concludes by stating that malware will continue to evolve and there is no single solution, requiring ongoing mitigation and management efforts.




















![Sample Message Header From: stranger <stranger@yahoo.com> To: bluminx @hotmail.com Subject: Worm Klez.E immunity Date: Thu, 13 Jun 2002 09:39:56 -0400 MIME-Version: 1.0 Received: from [63.117.44.150] by hotmail.com (3.2) with ESMTP id MHotMailBED1EBAB002B400431923F752C9606970; Thu, 13 Jun 2002 06:39:59 -0700 Received: from Zkprhj [216.54.110.216] by mail.atel.net (SMTPD32-6.06) id A08E53F007E; Thu, 13 Jun 2002 09:39:26 -0400 From [email_address] Thu, 13 Jun 2002 06:41:03 -0700 Message-Id: <200206130939556.SM02700@Zkprhj>](https://image.slidesharecdn.com/digital-immunity-the-myths-and-reality-28215/75/Digital-Immunity-The-Myths-and-Reality-32-2048.jpg)