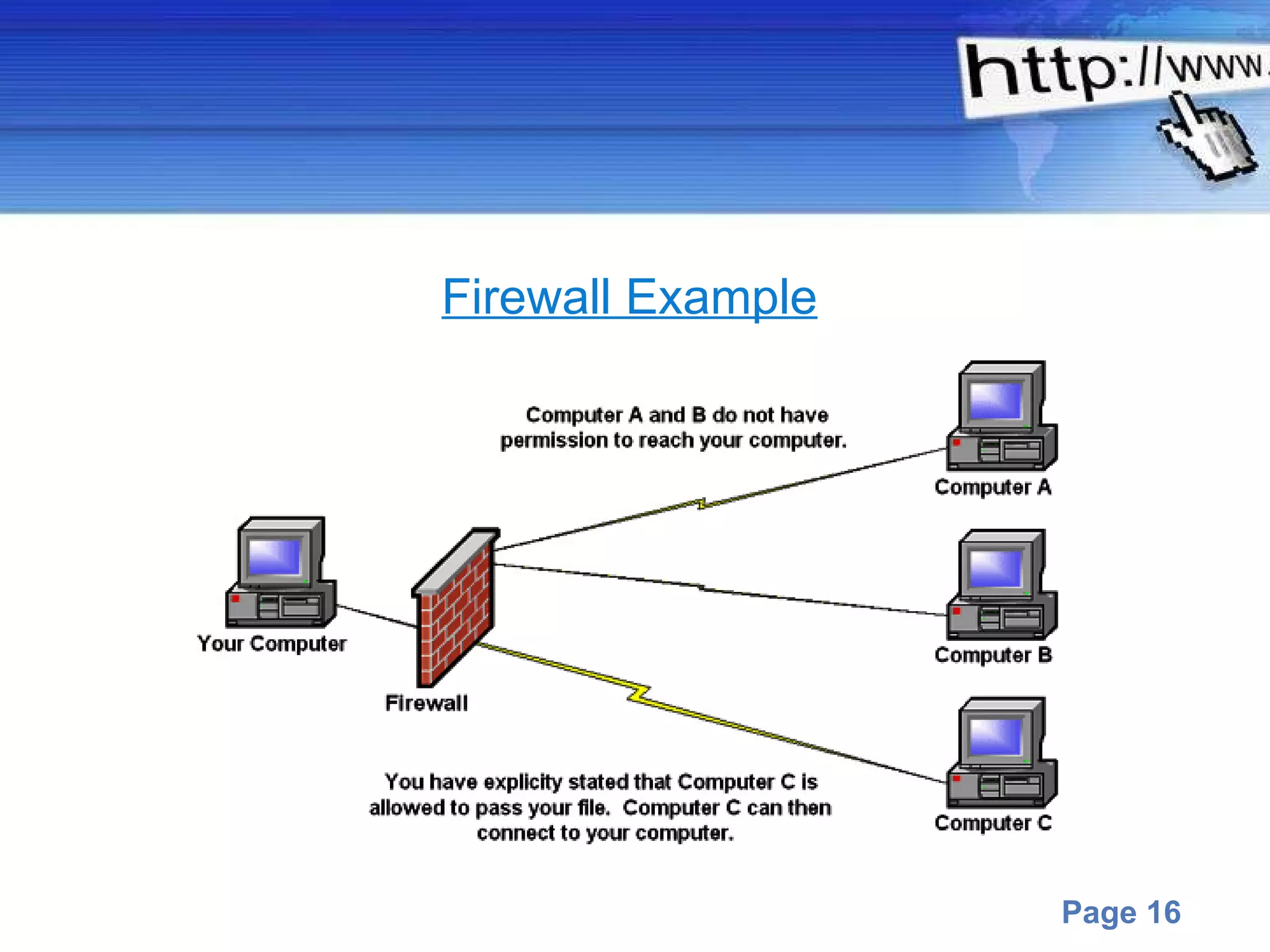
This document discusses computer infections like viruses, worms, and trojans. It describes viruses as programs that can copy themselves and infect other computers. Worms search for and implant code onto other systems through networks. Trojans appear harmless but later present malicious functions. The document also outlines protections like antivirus software, firewalls, and user education recommendations.