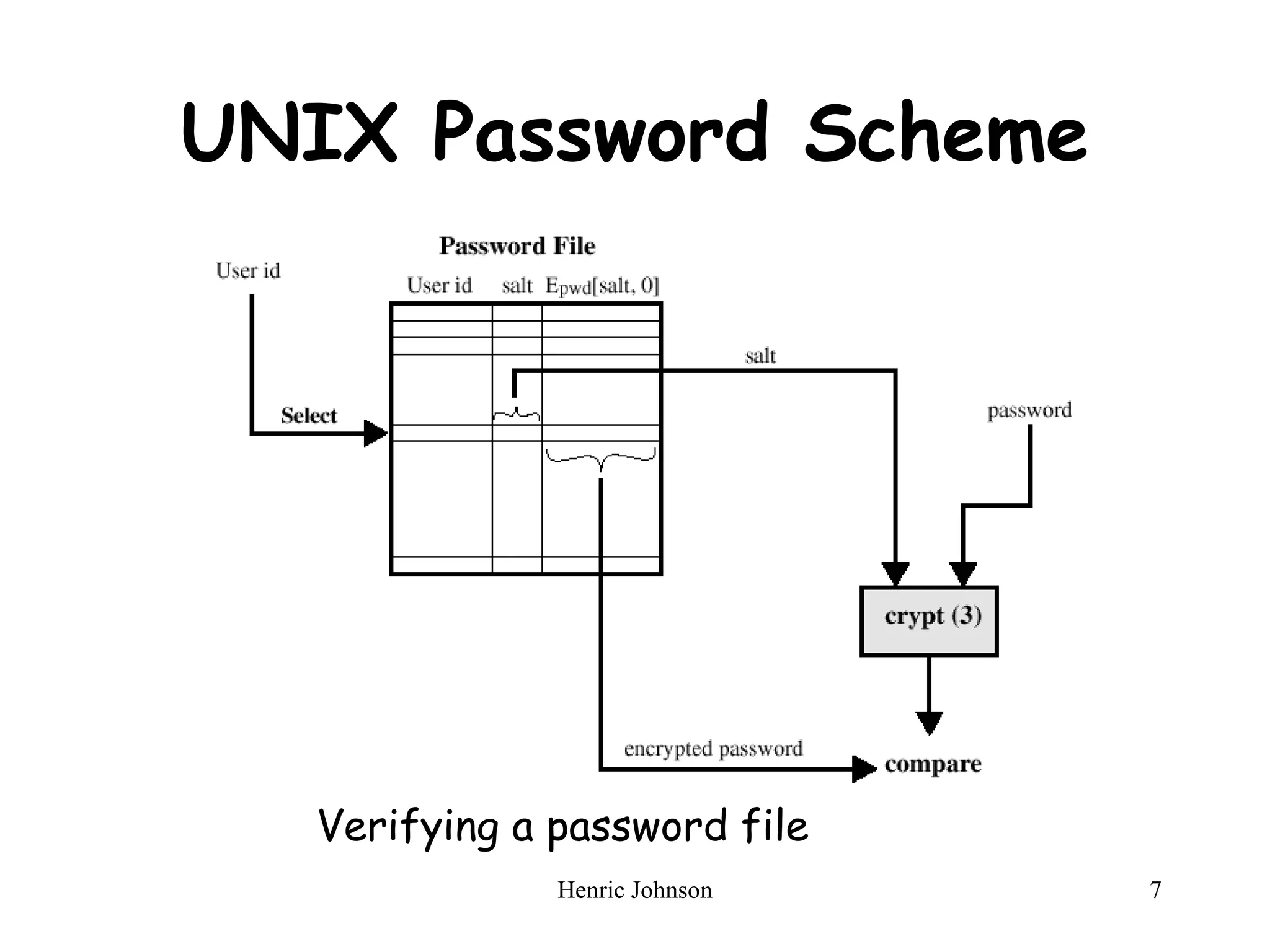
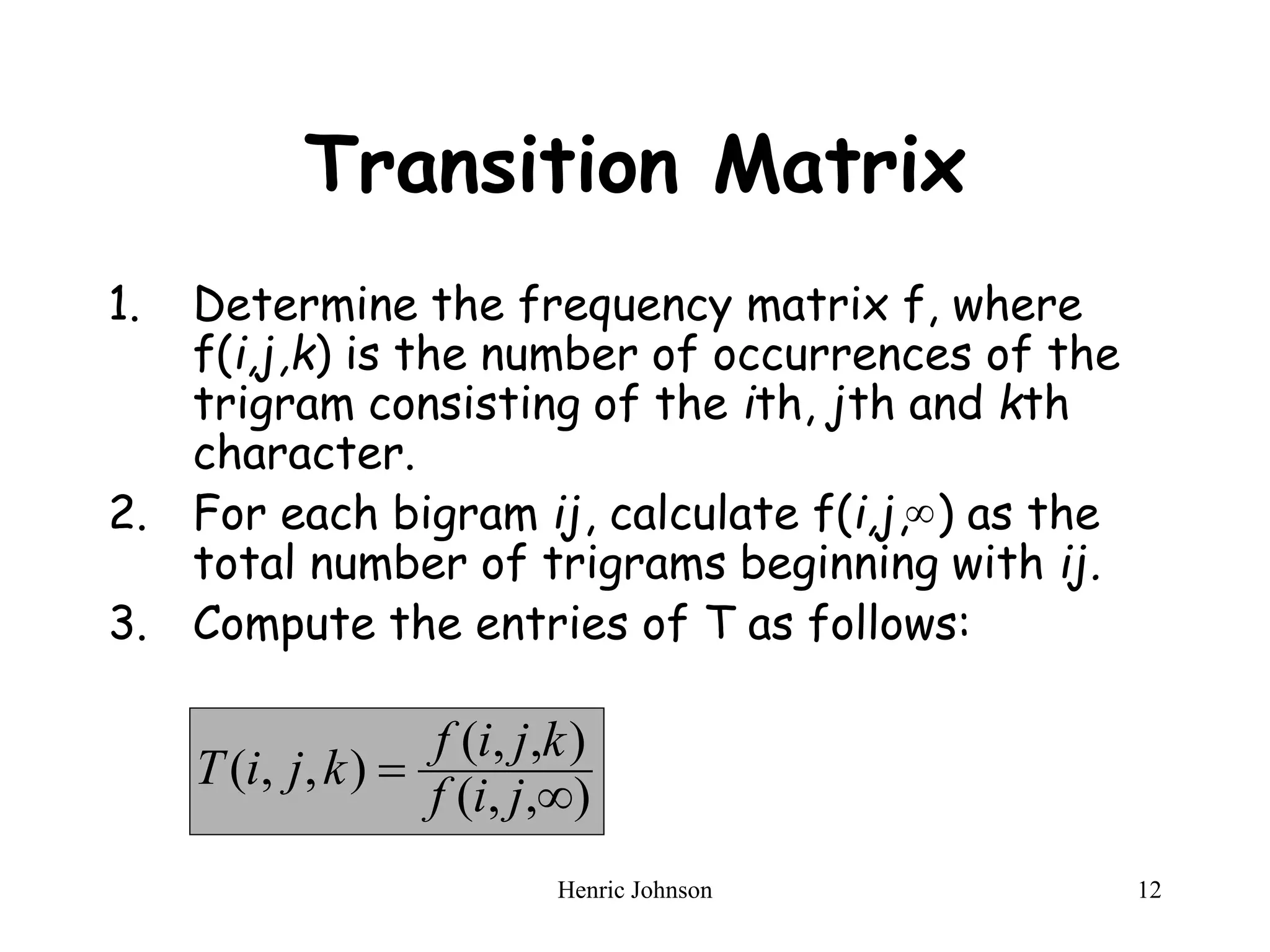
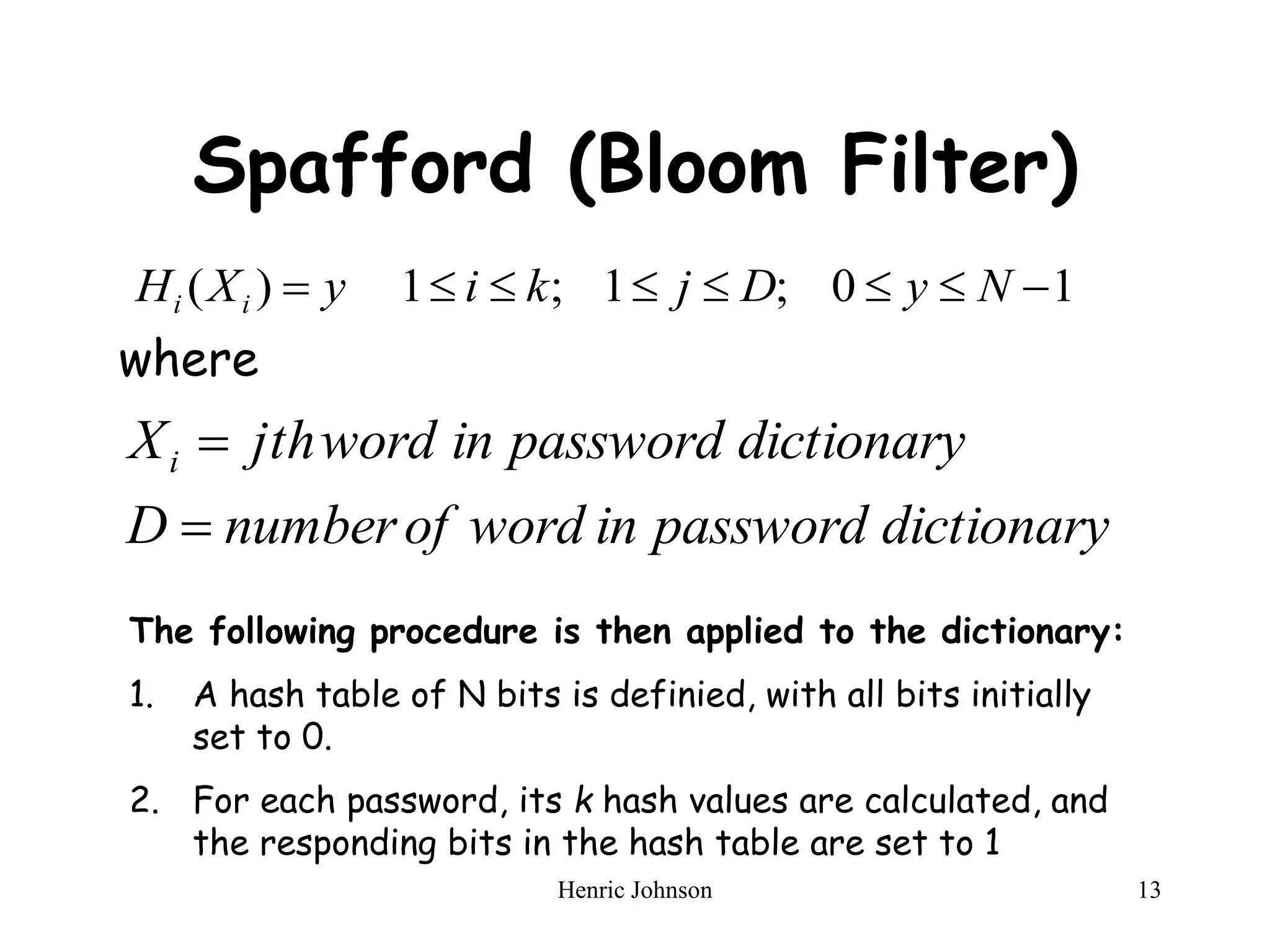
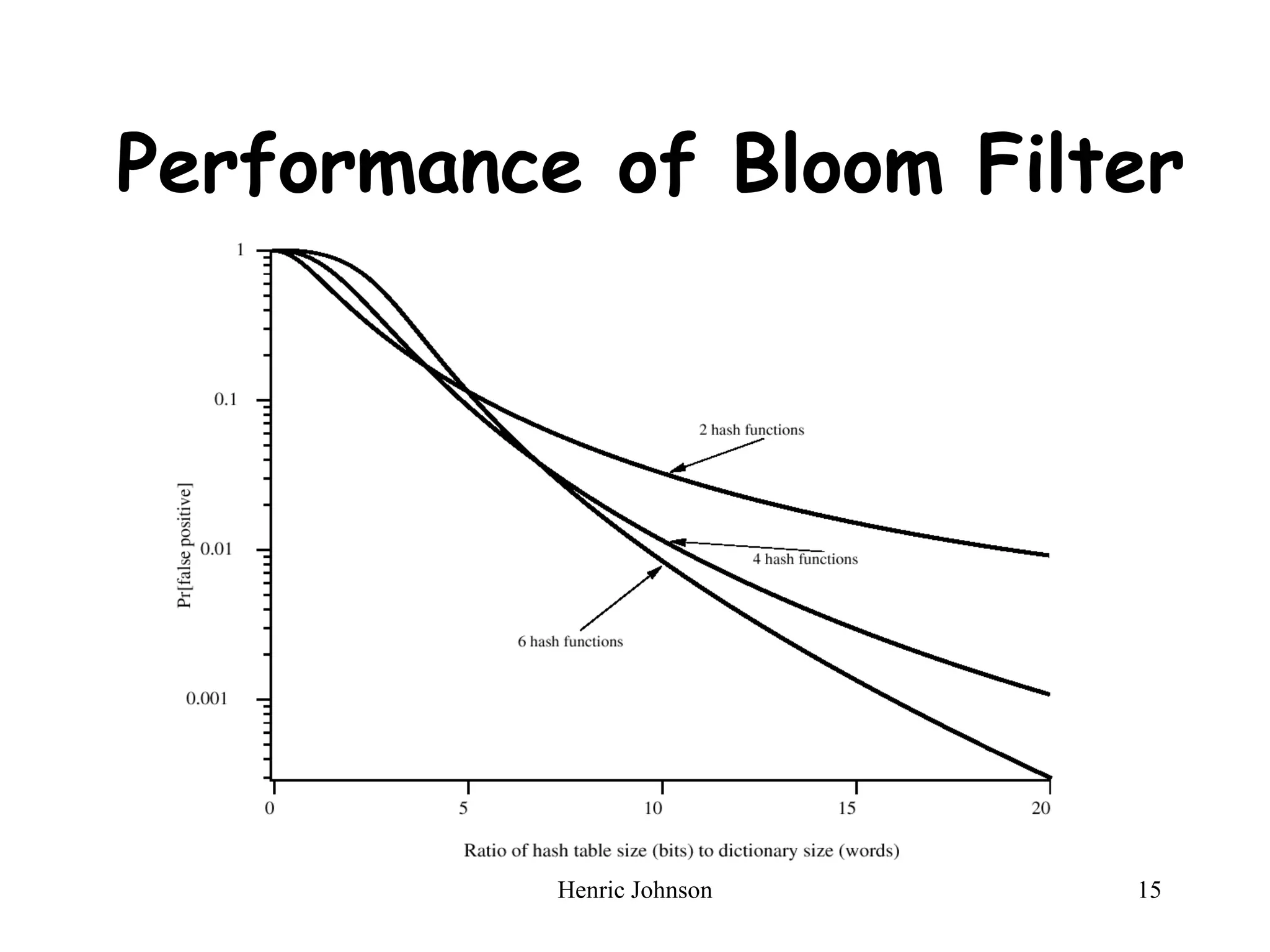
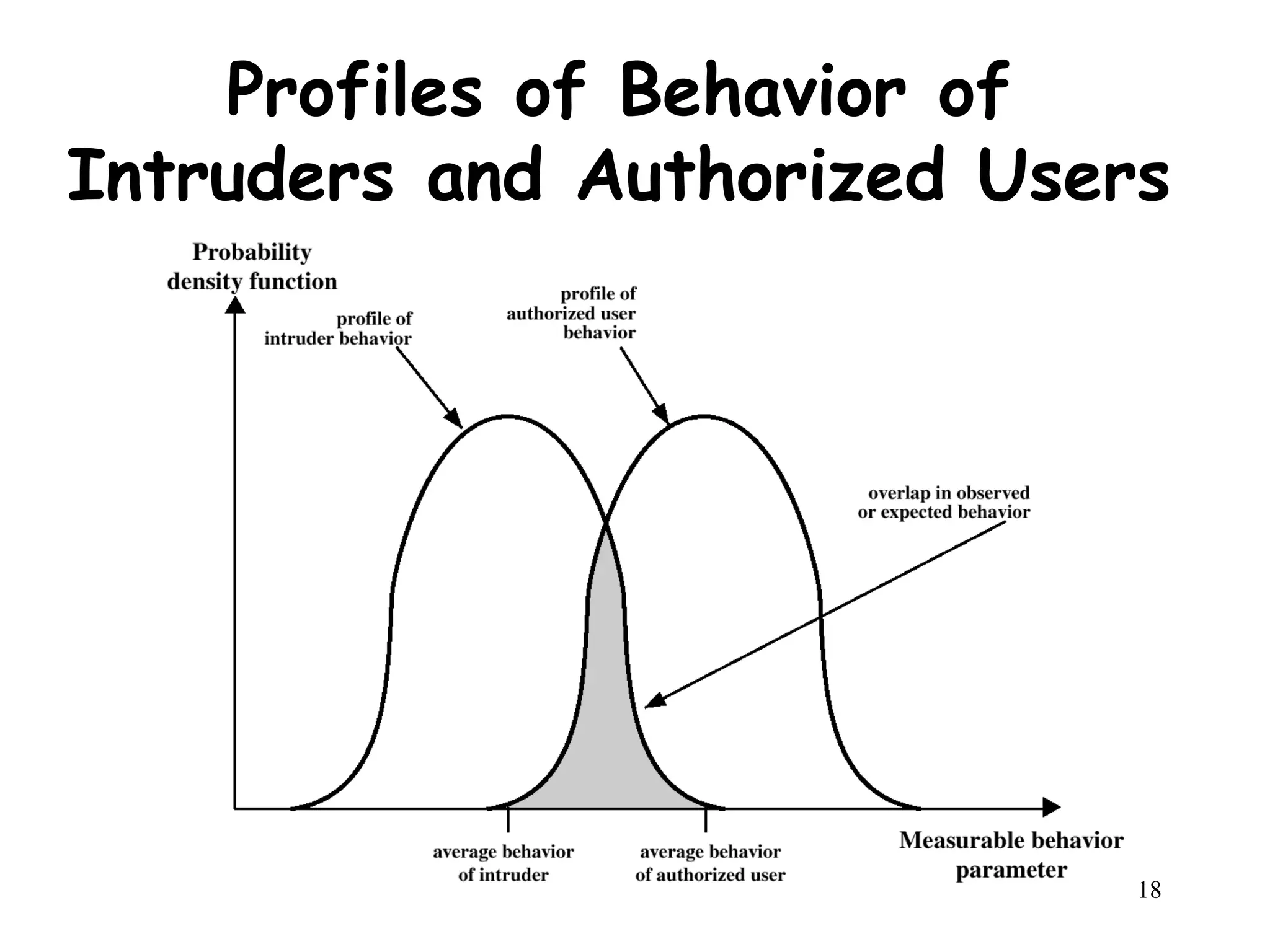
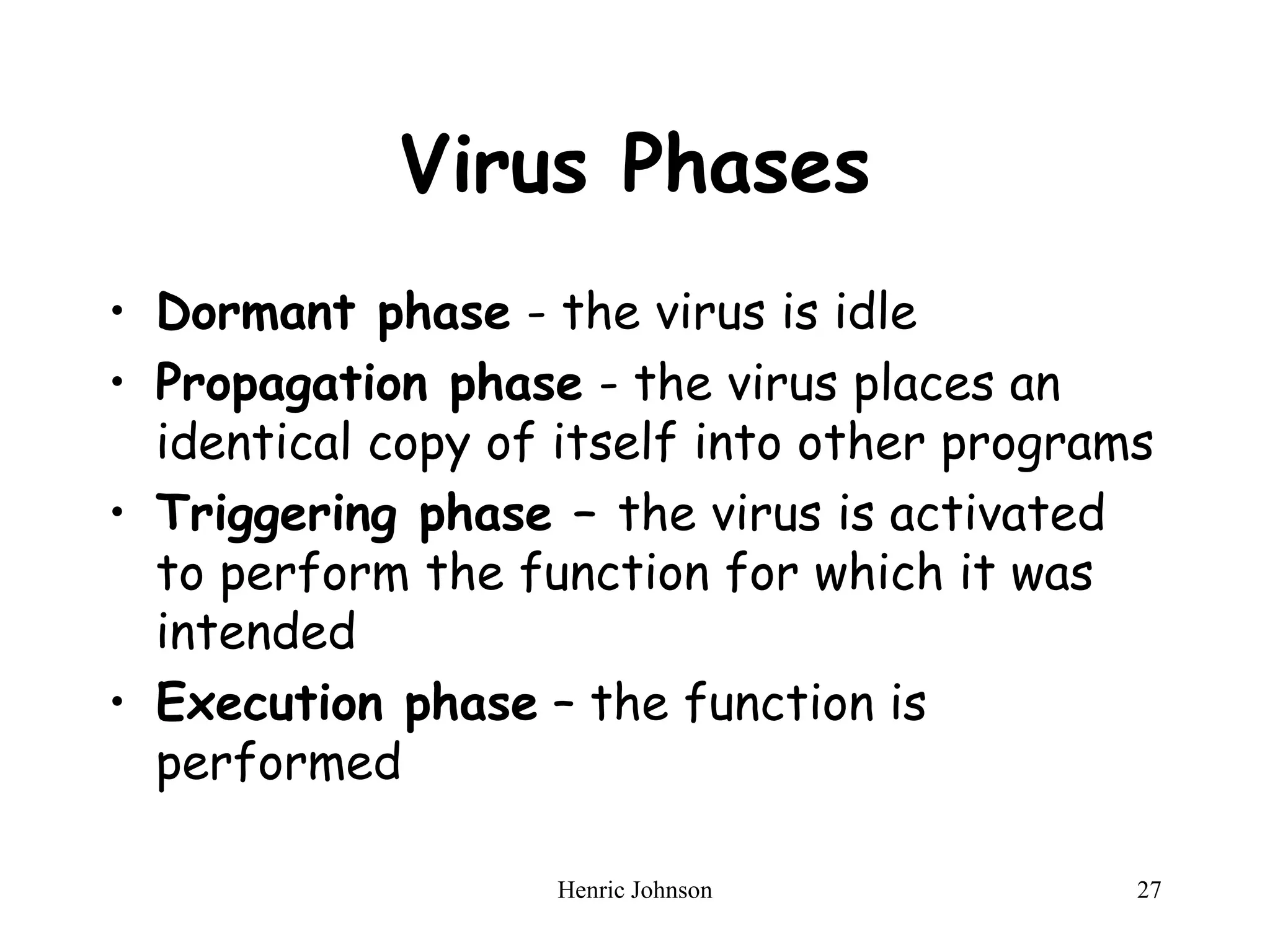
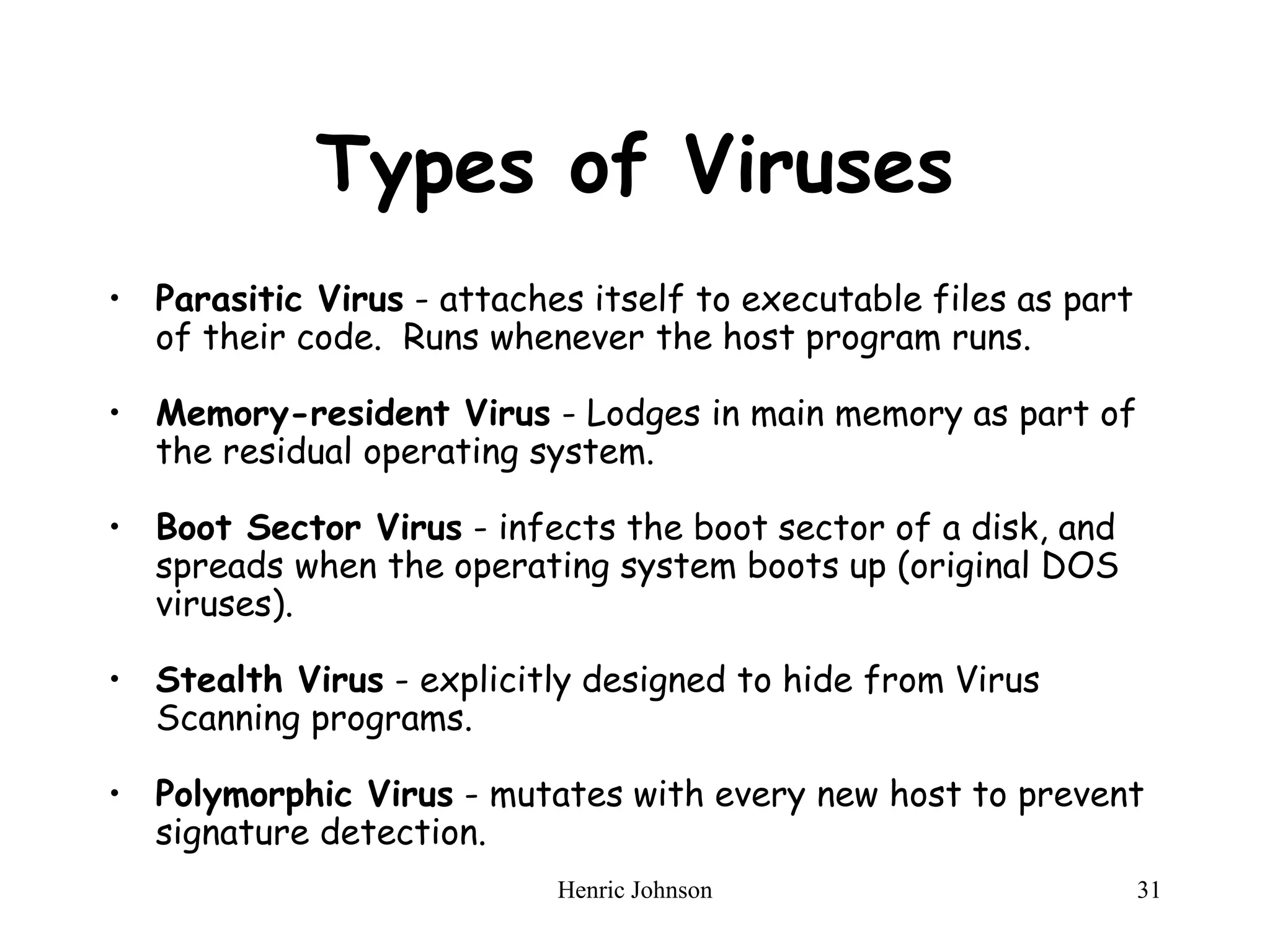
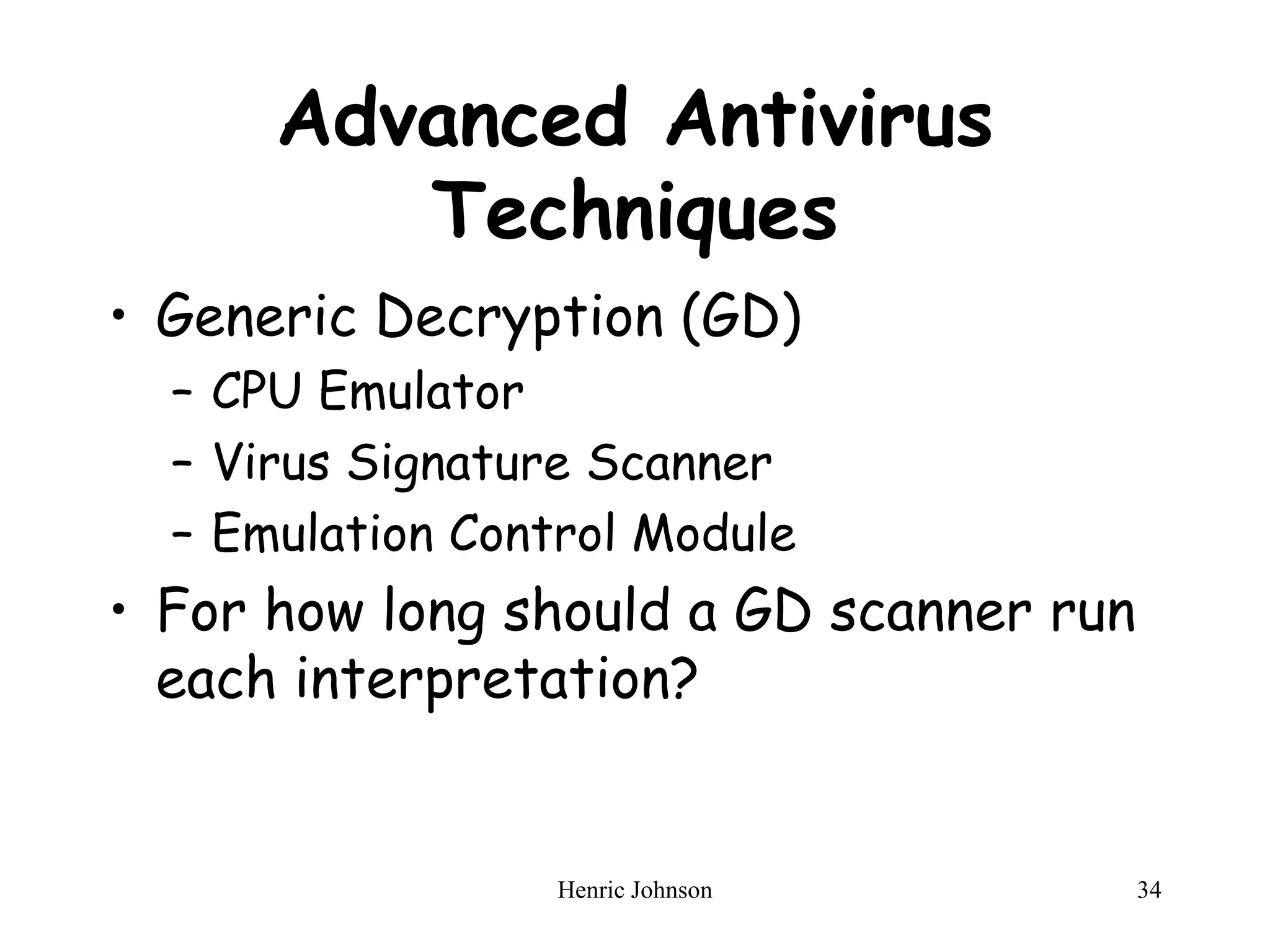
The document discusses intruders and viruses, detailing intrusion techniques, password protection strategies, and various types of malicious programs. It outlines behaviors of intruders and measures for intrusion detection, as well as the phases of viruses and antivirus approaches. Additionally, advanced antivirus techniques and recommended readings are provided for further understanding of cybersecurity threats.