This document is a thesis presentation that discusses the use of deception techniques in malware attacks and defense mechanisms. It is presented by Ajay Kumar Vishkarma to fulfill the requirements for a Master of Technology degree in Computer Science. The presentation contains 4 chapters: (1) Malware, which defines malware and discusses different types like viruses, worms, Trojans etc. and their effects; (2) Malware detection techniques; (3) Deception techniques used by attackers; and (4) Deception techniques used by defenders.




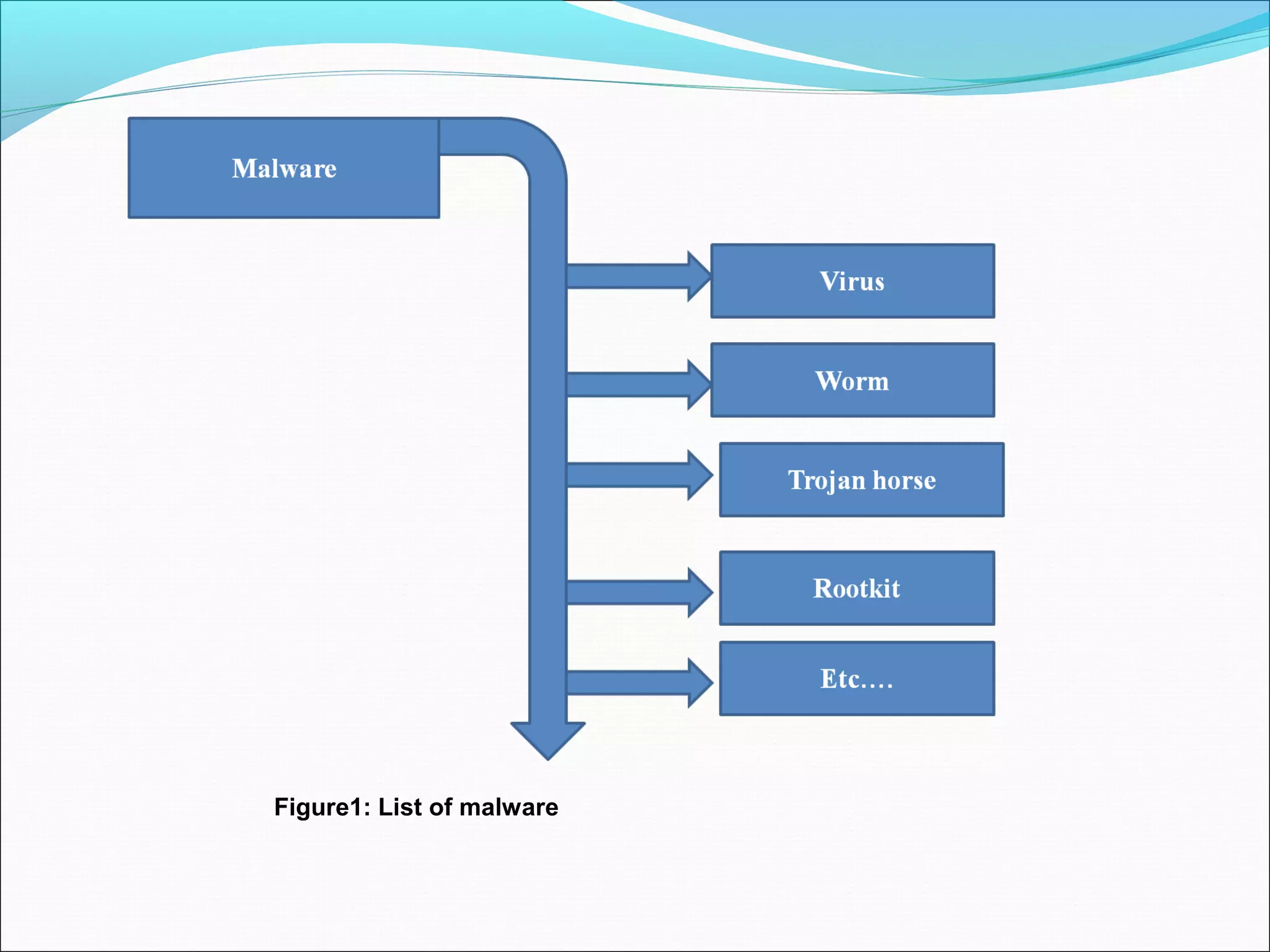
![•Malware, short for malicious software, is any software used to disrupt computer operation, gather
sensitive information, or gain access to private computer systems [1].
•It can appear in the form of executable code, scripts, active content, and other software.
•'Malware' is a general term used to refer to a variety of forms of hostile or intrusive software [2].
•The term barware is sometimes used, and applied to both true (malicious) malware and unintentionally
harmful software.
•Malware is sometimes known as a computer contaminant, as in the legal codes of several U.S. states.
•Software that causes harm due to bugs or poor design are not classified as malware; for example some
legitimate software written before the year 2000 had errors that caused serious malfunctions when the
year changed from 1999 to 2000 these programs are not considered as malware [2][3].
Malware Continue……
Introduction](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-5-2048.jpg)

![Malware Continue……
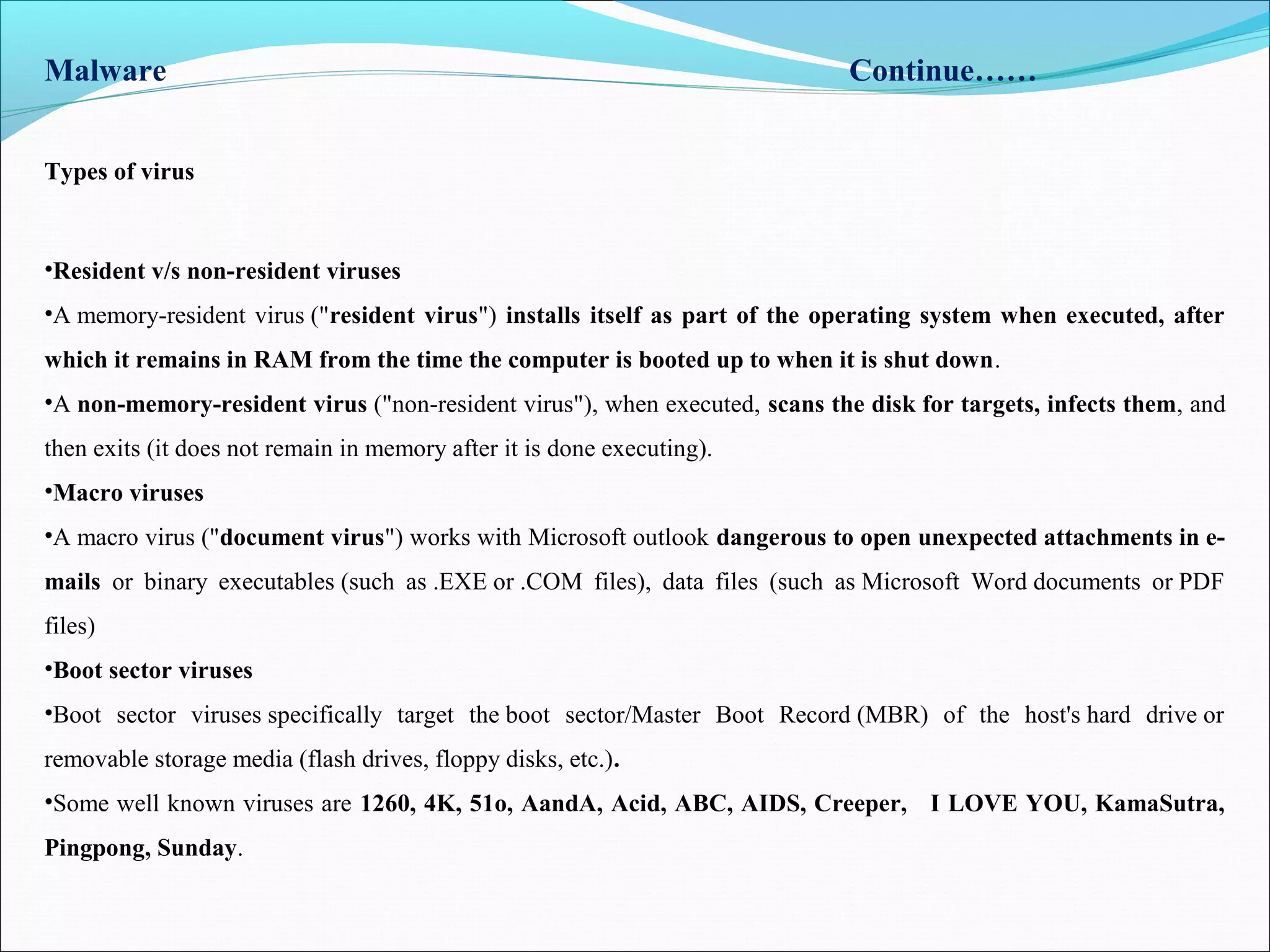
Virus
•A virus is a contagious program or code that attaches itself to another piece of software, and then
reproduces itself when that software is run.
•Most often this is spread by sharing software or files between computers through removable disk.
•It is a malware program that executed, replicates by inserting copies of itself (possibly modified) into
other computer programs, data files, or the boot sector of the hard drive; when this replication succeeds,
the affected areas are then said to be "infected“ as stealing hard disk space or CPU time, corrupting
data most of in the Microsoft Windows() and Android.
•Motives for creating viruses can include seeking profit, desire to send a political message, personal
amusement, to demonstrate that a vulnerability exists in software, for sabotage and denial of service.
•It causes billions of dollars worth of economic damage each year, due to causing systems failure,
wasting computer resources, corrupting data, increasing maintenance costs, etc.
•Unfortunately, no currently existing antivirus software is able to catch all computer viruses
(especially new ones) [2].](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-8-2048.jpg)
![Malware Continue……
Worm
•By John Brunner's 1975 novel, in “The Shockwave Rider”.
•A worm is a program that replicates itself in order to spread to other computers.
•Often; it uses a computer network to spread itself, relying on security failures on the target computer to access it.
Worms almost always cause at least some harm to the network as Morris worm ,Mydoom , Badtrans, Bagle, Witty,
Zotob [2].
•Unlike a computer virus, it does not need to attach itself to an existing program [3].
C Active worms
Camouflaging Worm (C-worm) its ability to intelligently manipulate its scan traffic volume over time for that he design
a novel spectrum based scheme to detect the C-Worm as like Nimda, Code Red, Slammer, Witty and Sasser.
Modelling
C-Worm does not show any trends while its propagation so as to hide its presence effectively [4].](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-11-2048.jpg)
![Malware Continue……
Trojan horse
•Trojans are written with the purpose of discovering financial information, taking over others computer’s system
resources, and may create a denial-of-service (DoS) attack ,srpeaed over 83% and all e-commerce theft.
•DoS attacks are attempts to make a machine or network resource unavailable to those attempting to reach it. A
Trojan often acts as a backdoor, contacting a controller which can then have unauthorized access to the affected computer.
•A Trojan may give a hacker remote access to a targeted computer system [6].
Govware
•In German-speaking countries, spyware used or made by the government is sometimes called govware.
•It is typically a Trojan horse software used to intercept communications from the target computer. Some countries like
Switzerland and Germany have a legal framework governing the use of such software.
•Examples of govware trojans include the SwissMiniPanzer and MegaPanzer and the German "state trojan" nicknamed
R2D2.
•Due to the popularity of botnets among hackers and the availability of advertising services that permit authors to violate
their users' privacy [7] [8].](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-12-2048.jpg)
![Malware Continue…
Spyware
•Recorded use on 16 October 1995 in a UseNet post that poked fun at Microsoft's business model.
•Spyware at first denoted software meant for espionage purposes.
•Spyware is software that aids in gathering information about a person or organization without their knowledge
and that may send such information to another entity without the consumer's consent or that asserts control over
a computer without the consumer's knowledge.
•"Spyware" is mostly classified into four types: system monitors, trojans, adware, and tracking cookies.
•Spyware is mostly used for the purposes of tracking and storing Internet users' movements on the Web and serving up
pop-up ads to Internet users as Internet surfing habits, user logins, and bank or credit account information [2] [9].](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-13-2048.jpg)
![Malware Continue……
Rootkit
•Rootkit is designed to get the sensitive data from others computer without realizing anything is going on [10].
•The term rootkit is a concatenation of "root" from traditional name of the privileged account on UNIX operating
systems and the word "kit" refers to the software components that implement the tool.
•Detection methods include using an alternative and trusted operating system, behavioral-based methods,
signature scanning, difference scanning, and memory dump analysis.
•Removal can be complicated or practically impossible, especially in cases where the rootkit resides in the kernel;
reinstallation of the operating system may be the only available solution to the problem [11].
•These first-generation rootkits were trivial to detect by using tools such as Tripwire that had not been compromised to
access the same information.
•Examples NTRootkit, Hooksafe,](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-14-2048.jpg)
![Malware Continue……
Figure3: Level wise activity of Rootkit in a system.
User mode : Rootkits run in Ring 3, along with other applications as user, rather than low-level system
processes [11]. It Harms (DLL file on Windows, or a .dylib file on Mac OS X)
•kernel mode: This class of rootkit has unrestricted security access, but is more difficult to write.
•The complexity makes bugs common, and any bugs in code operating at the kernel level may seriously
impact system stability, leading to discovery of the rootkit [12] [13] [14].](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-15-2048.jpg)
![Malware Continue……
Backdoors
• Backdoors are much the same as Trojans or worms, except that they open a “backdoor” onto a computer, providing a
network connection for hackers or other malware to enter or for viruses or spam to be sent.
•A backdoor is an algorithm of bypassing normal authentication, securing unauthorized remote access to a computer,
obtaining access to plaintext, and so on, while attempting to remain undetected [15].
•Default passwords can function as backdoors if they are not changed by the user.
•The threat of backdoors surfaced when multiuser and networked operating systems became widely adopted [16].
Examples of Backdoors
•MD2, MD4, MD5, SHA-0, SHA-1, Sony/BMG (2005) Sobig and Mydoom, (effects in Microsoft
Windows and Microsoft).
•A sophisticated attempt to plant a backdoor in the Linux kernel, exposed in November 2003, added a small and subtle
code change by subverting the revision control system [15].](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-16-2048.jpg)
![Malware Continue……
Object code backdoors
•Harder to detect backdoors involve modifying object code, rather than source code object code is much harder to
inspect, as it is designed to be machine-readable, not human-readable ,never appears on disk, only in memory.
•It is easily detected by simply checking for changes (differences), notably in length or in checksum, and in some cases
can be detected or analyzed by disassembling the object code [17].
Asymmetric backdoors
•A traditional backdoor is a symmetric backdoor: anyone that finds the backdoor can in turn use it. It is used by the
attacker who plants it, even if the full implementation of the backdoor becomes public.
Compiler backdoors (1984)
•A sophisticated form of black box backdoor is a compiler backdoor, where not only is a compiler subvert but it is
further modified to detect when it is compiling itself and then inserts both the backdoor insertion code (targeting the
other program) and the code modifying self-compilation, like the mechanism how retroviruses infect their host.
•This can be done by modifying the source code, and the resulting compromised compiler (object code) can compile the
original (unmodified) source code and insert itself: the exploit has been boot-strapped .
•This backdoor mechanism is based on the fact that people only review source (human-written) code, and not
compiled machine code (object code) [17] [18] [19].
Types of Backdoors](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-17-2048.jpg)
![Malware Continue……
Botnet
•The word botnet is a combination of the words robot and network. It is used to control number of compromised
machine in a network called Botnet. Example: Khan C. Smith in 2001 [20].
•A botnet is a collection of Internet-connected programs communicating with other similar programs in order to
perform tasks.
•It mundane as keeping control of an Internet Relay Chat (IRC) channel, or it could be used to send spam email or
participate in distributed denial-of-service attacks Example: Donbot, Storm, Chemeleon, AKbot, Boatnet [21] [22].
Adware
•Adware is the least dangerous and most lucrative malware that displays free illegal ads on web sites.
•The advertisements produced by adware are sometimes in the form of a pop-up [23].](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-18-2048.jpg)
![Malware Continue……
Flame (2012)
•Flame "is certainly the most sophisticated malware we encountered during our practice; arguably, it is the
most complex malware ever found” that supports a "kill" command which wipes (20 time hard ) than all traces
of the malware from the computer.
•Flame can spread to other systems over a local network (LAN) or via USB stick. It can record
audio, screenshots, keyboard activity and network traffic in Microsoft Windows operating system.
•The program also records Skype conversations and can turn infected computers into Bluetooth beacons which
attempt to download contact information from nearby Bluetooth-enabled devices 65% of the infections happened in
Iran, Israel, the Palestinian Territories, Sudan, Syria, Lebanon, Saudi Arabia, and Egypt, with a "huge majority of
targets" within Iran , Europe and North America [24].
•Flame is an uncharacteristically large program for malware at 20 megabytes.
•It is written partly in the Lua scripting language with compiled C++ code linked in, and allows other attack modules
to be loaded after initial infection [25].](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-19-2048.jpg)
![Malware Continue……
•Keyloggers
•Keyloggers are malicious applications that tend to monitor your keyboard typing activities.
•detection Tool : SpyHunter's Keyloggers [25].
Rogue security software (2008)
•Rogue AV is a rogue that deceives or misleads users into paying money for fake or simulated removal of malware or it
claims to get rid of, but instead introduces malware to the computer.
•Rogue security software mainly relies on (fraud) to defeat the security built into modern operating system
and browser software and install itself onto victims' computers for example, display a fictitious warning dialog stating
that someone's machine is infected with a computer virus, and encourage them through manipulation to install or
purchase scareware in the belief that they are purchasing genuine antivirus software [26].
Ransomware (2012-13)
•It restricts access to the computer system that it infects, and demands a ransom paid to the creators of the malware in order
for the restriction to be removed.
•Some forms of ransomware encrypt files on the system's hard drive while some may simply lock the system and display
messages intended to coax the user into paying.
•Tactics coax (sweet talk) the user into paying the malware's author to remove the ransomware, either by supplying a
program which can decrypt the files, or by sending an unlock code that undoes the changes the payload has made.
•These payments are often delivered using either a wire transfer, premium-rate text messages, through an online
payment voucher service such as Ukash or Paysafecard, or most recently, the digital currency Bitcoin [27].](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-20-2048.jpg)
![Malware Continue……
Browser hijacking
•It is the modification of a web browser's settings without the user's permission as replace the existing home page,
error page, or search page with its own.
•These are generally used to force hits to a particular website, increasing its advertising revenue.
•The homepages that are set by hijackers are often search pages, and many of these programs are spyware programs
that track personal data.
•Most installers will give users the opportunity to accept or decline an offer to install a hijacker; however, the request
to decline the offer is often ignored or presented in a very confusing manner.
•This is done for the sole reason of tricking users into installing malware [28].
•Cross-site scripting (XSS)
•It is a type of computer security vulnerability typically found in Web applications. XSS enables attackers
to inject client-side script into Web pages viewed by other users to bypass access controls such as
the same origin policy.
•Ex: non-persistent (server-side code flaws ) and persistent (DOM-based in client-side code) [29] [30].](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-21-2048.jpg)
![Malware Continue……
Chargeware
•It is a form of malware used to corrupt desktop computers and mobile devices.
•The purpose of the program is to manipulate the user into agreeing to unclear terms for fees and charges.
•An additional feature is for the malware to have deliberately difficult methods of unsubscribing, so that charges
continue for as long as possible.
•Chargeware is often associated with Internet pornography [31].
Shareware
•Shareware/trialware/demoware provided to users for a certain limited trial basis related to business, software
development, education, home, multimedia, design, drivers, games, and utilities and pursuant to a license which
restricts any commercial benefit, use or exploitation of the software on MS Window.
•Shareware is often offered as a download from an Internet website or as a compact disc included with a magazine.
•They take money or require no payment; just an email address for further use [32].
Steelware
•It refers to a type of malware that covertly transfers money or data to a third party.
•Specifically, stealware uses an HTTP cookie to redirect the commission ordinarily earned by the site for referring
users to another site [33].](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-22-2048.jpg)
![Malware Continue……
Effects of malware
•Malware is used by both black hat hackers and governments, to steal personal, financial, or business information.
•Malware is sometimes used broadly against government or corporate websites to gather guarded information, or to disrupt
their operation in general.
•However, malware is often used against individuals to gain information such as personal identification numbers or details,
bank or credit card numbers, and passwords [2] ---- [32].
•China downloads 10 to 20 terabyte data from US NIPRnet Military network in 2008, by K. Zetter. “Operation Aurora”
targeted more than 20 Organization Company including Google, Adobe, Symantec and US defense, by M. Hosenball
Edward Snowden who downloads 50000 to 200000 classified data from US National Security Agency.
•Data leak of US prison is historical malicious activity in cyber attack [34].](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-23-2048.jpg)
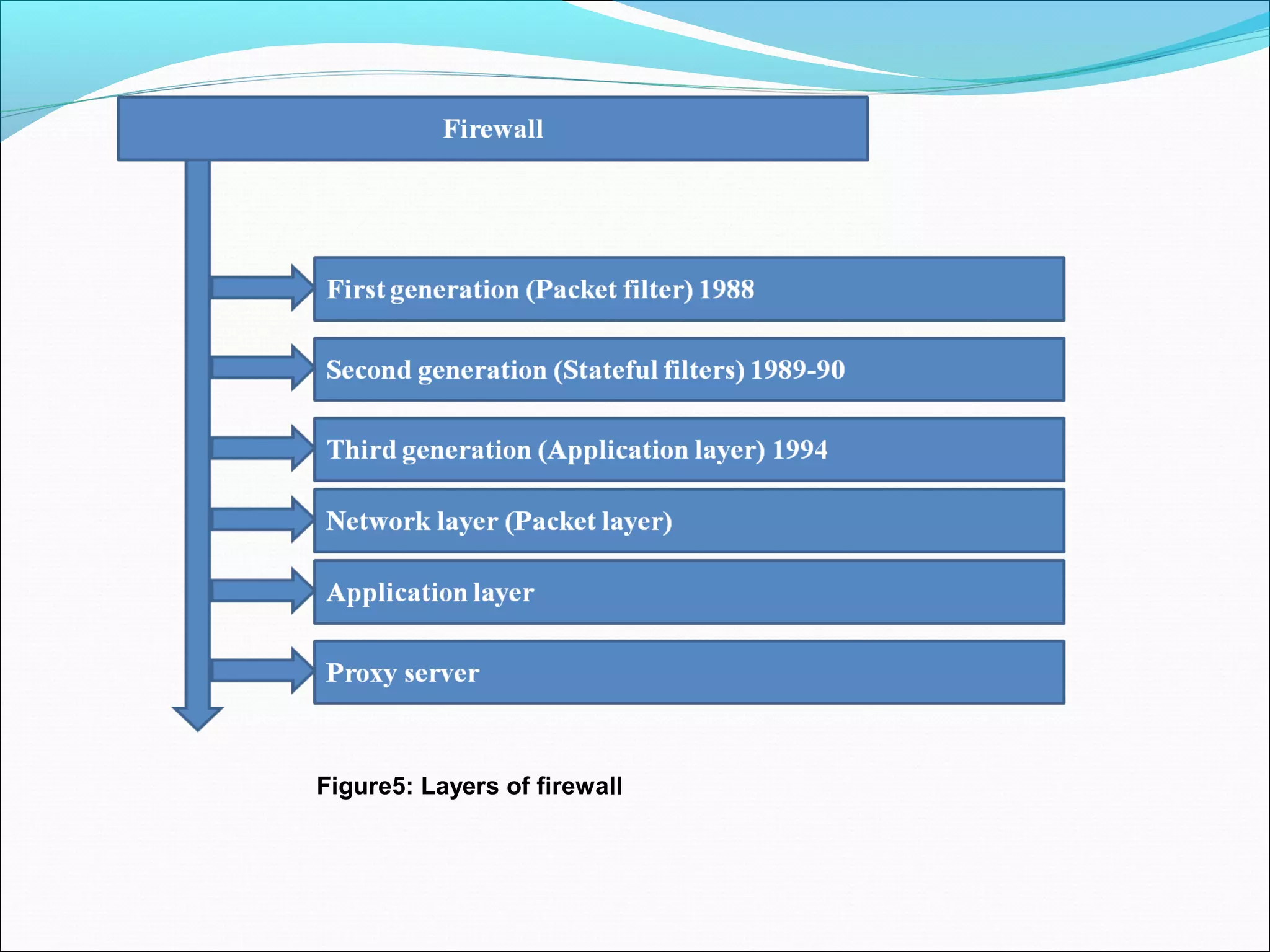
![Ch2: Malware detection technique
Firewall (1980)
•Firewalls are used by home users and organizations to try to safeguard against malware attacks based on an
applied rule set (establishes a barrier between a trusted, secure internal network and another network that is
assumed not to be secure and trusted) for software solution and hardware appliance [36].
Figure4: a block diagram of Firewall](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-27-2048.jpg)
![Malware detection technique Continue…..
First Generation (Packet Filter)
•It filters each packet based only on information contained in the packet itself (most commonly using a combination of the
packet's source and destination address, its protocol, and, for TCP and UDP traffic, the port number). (OSI Layers)
Physical, network, Transport.
Second Generation (“Stateful” Filters)
In 1989–1990 from AT&T Bell Laboratories, developed the second generation of firewalls, calling them Circuit-level
gateways.
Second-generation firewalls perform the work of their first-generation predecessors but operate up to layer 4 (transport
layer) of the OSI model.
Third Layer (Application Layer)
•Application level firewall develop in June 1994, with the Kernel enhancement of IP filter and socket transparent.
•The key benefit of application layer filtering is that it can "understand" certain applications and protocols (such as File
Transfer Protocol (FTP), Domain Name System (DNS), or Hypertext Transfer Protocol (HTTP) [37].
Proxy Server
•A proxy server may act as a firewall by responding to input packets (connection requests) in the manner of an application,
while blocking other packets.
•A proxy server is a gateway from one network to another for a specific network application, in the sense that it functions as
a proxy on behalf of the network user [36] [37].](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-28-2048.jpg)
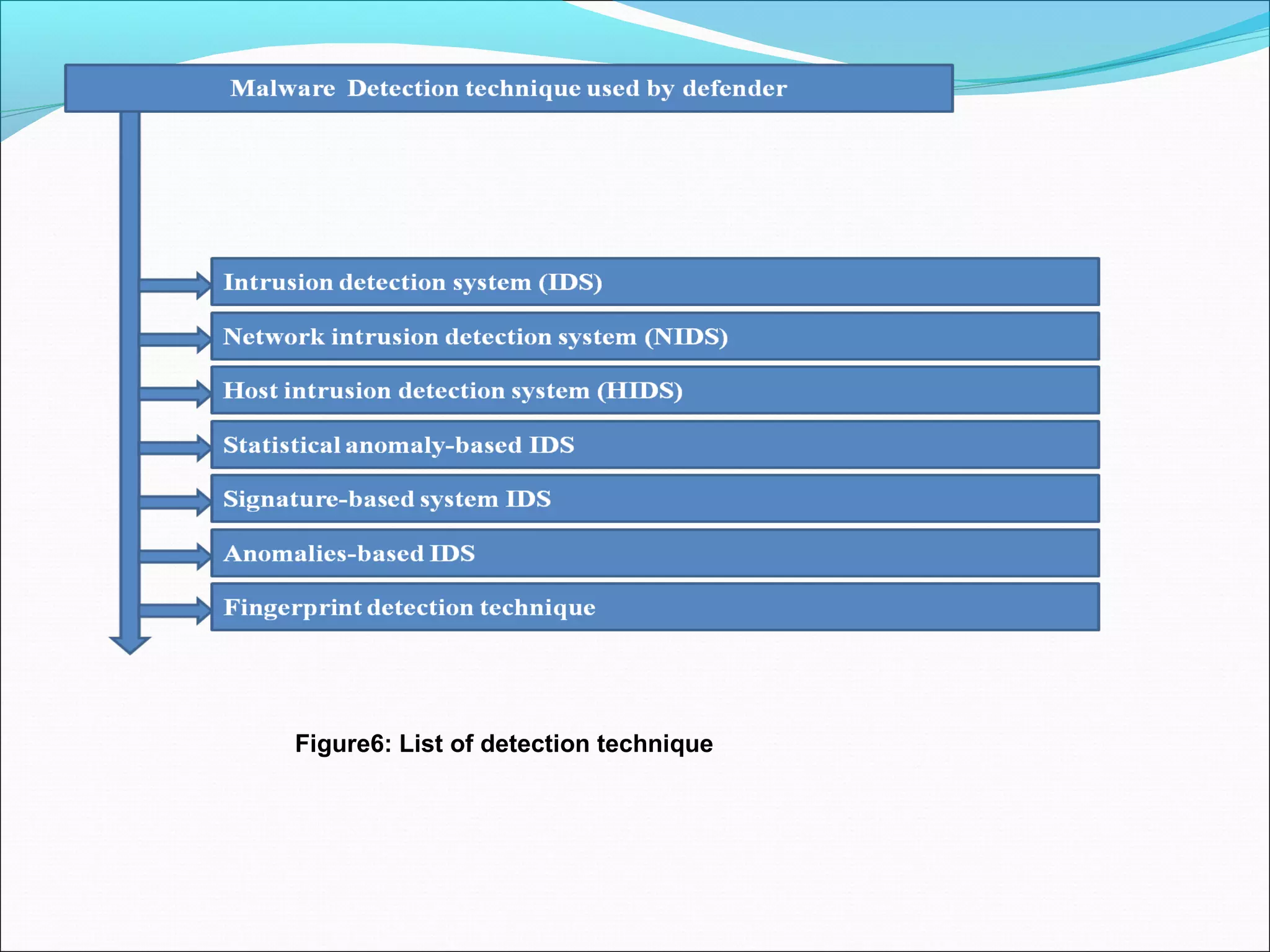
![Malware detection technique Continue…..
Intrusion detection
•An intrusion detection system (IDS) is a device or software application that monitors network or system
activities for malicious activities or policy violations and produces reports to a management station.
•IDS come in a variety of “flavors” and approach the goal of detecting suspicious traffic in different ways.
•There are network based (NIDS) and host based (HIDS) intrusion detection systems.
•NIDS: it is use to monitor traffic to and from all devices on the network. It performs an analysis for a passing
traffic on the entire subnet, works in a promiscuous mode, and matches the traffic that is passed on the
subnets to the library of known attacks. Once the attack is identified, or abnormal behavior is sensed, the alert
can be sent to the administrator. Example of the NIDS would be installing it on the subnet where firewalls are
located in order to see if someone is trying to break into the firewall.
•Tools: Honeypot, Polygraph, Hamsa.
•HIDS: it run on individual hosts or devices on the network to monitor inbound/outbound the
packet(specially for critical system) [37].](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-30-2048.jpg)
![Malware detection technique Continue…..
Statistical anomaly-based IDS
•It monitor network traffic and compare it against an established baseline, that will identify what is “normal” for that
network- what sort of bandwidth is generally used, what protocols are used, what ports and devices generally connect to
each other- and alert the administrator or user when traffic is detected which is anomalous, or significantly different,
than the baseline.
Signature-based IDS
It will monitor packets on the network and compare them against a database of signatures or attributes from known
malicious threats during that lag time your IDS would be unable to detect the new threat. By N. Virvilis and O.
Serrano [35].
use: Redesign our defenses
Anomalies-based intrusion detection
•It is suitable to find novel attacks.](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-31-2048.jpg)
![Malware detection technique Continue…..
Fingerprint detection technique
•It is used by the help of n-gram, hash, winnoing and MOSS (Measure of Software Similarity), Birthmark, Sandmark,
chaffing etc. technique to detect the same digital document.
•Example :
•we use k-gram or n-gram and hash technique to convert the document identity. In k-gram we arrange character of the
whole document in 1 gram, 2 gram 3gram….k-gram. After that we use hashing technique to short the whole gram and at
last we get final output in the form of very small character, number or both. As given below [36]:
Example of fingerprint by 5-gram:
A do run run run, a do run run
(a) Some text.
adorunrunrunadorunrun
(b) The text with irrelevant features removed.
adoru dorun orunr runru unrun nrunr runru unrun
nruna runad unado nador adoru dorun orunr runru unrun](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-32-2048.jpg)

![Malware detection technique Continue…..
(e) Windows of hashes of length 4.
*Select one minimum hash value from whole data. If minimum is more than one then select the rightmost value.
(77, 72, 42, 17) (72, 42, 17, 98)
(42, 17, 98, 50) (17, 98, 50, 17)
(98, 50, 17, 98) (50, 17, 98, 8)
(17, 98, 8, 88) (98, 8, 88, 67)
(8, 88, 67, 39) (88, 67, 39, 77)
(67, 39, 77, 72) (39, 77, 72, 42)
(77, 72, 42, 17) (72, 42, 17, 98)
(f) Minimum hash values are selected from each window.
* select all minimum value as 17 17 8 39 17
(g) Fingerprints selected by Winnowing.
[17, 3] [17,6] [8,8] [39,11] [17,15]
(h) Fingerprints paired with 0-base positional Information.](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-34-2048.jpg)
![Malware detection technique Continue…..
•Winnowing Algorithm: it is taken from selecting fingerprints from hashes of k-grams and give an upper
bound on the performance of Winnowing, expressed as a trade-off between the number of fingerprints that must
be selected and the shortest match that we are guaranteed to detect[37] [38].
•That must satisfy two properties of string of any document:
If there is a substring match at least as long as the guarantee threshold, t, then this match is detected.
Do not detect any matches shorter than the noise threshold, k.
The contain t and k=<t.
Chaffing: it like winnowing algorithms. It is used for providing confidentiality or information hiding not
for copy detecting. Therefore it deals with terminologies like sender and receiver, encryption and
decryption, key, authentication, MAC and packets etc [39].
MOSS(Measure of Software Similarity)1997: it is widely-used plagiarism detection technique even in
computer languages as C, C++, Java, Pascal, Ada etc.](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-35-2048.jpg)
![Malware detection technique Continue…..
Table1: Lines of code with Token [41].](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-36-2048.jpg)
![Malware detection technique Continue…..
Birthmark
•Birthmarking of software depends upon uniquely inherent property of same program. Same type of copy for an individual
software or program as program “p” Is the same copy of program “q”. To evaluate the strength of the birth marking
technique we examine two properties: credibility and resilience to semantics preserving transformations [42] [43].
K-GRAM BASED BIRTHMARKS
•By sliding a window of length k over the static instruction sequence as it is laid out in the executable as:
•The k-gram birthmark is the set of unique opcode sequences of length k. Let f(p) = {p1, ..., pn} and f(q) = {q1, ..., qm} be
birthmarks of the sets of modules p and q respectively. We say that two sets of modules are the same if and only if f(p) =
f(q), i.e. if |f(p)| = |f(q)| = |f(p)f(q)|.
Tamada Birthmark
The Tamada birthmarking technique is the only known module level technique which targets program theft at the bytecode
level.
Because of this we are using it as an evaluation base for the k-gram technique.
While the k-gram birthmark provides an advantage over the Tamada techniques in that it can be blindly applied at either the
module or program level.
It is also a technique which is more likely to be able to stand on its own and would not necessarily have to be used in
conjunction with other techniques if the Tamada birthmark is combined with the k-gram birthmark it is possible to
provide stronger evidence of software theft than just using the Tamada technique [45].](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-37-2048.jpg)

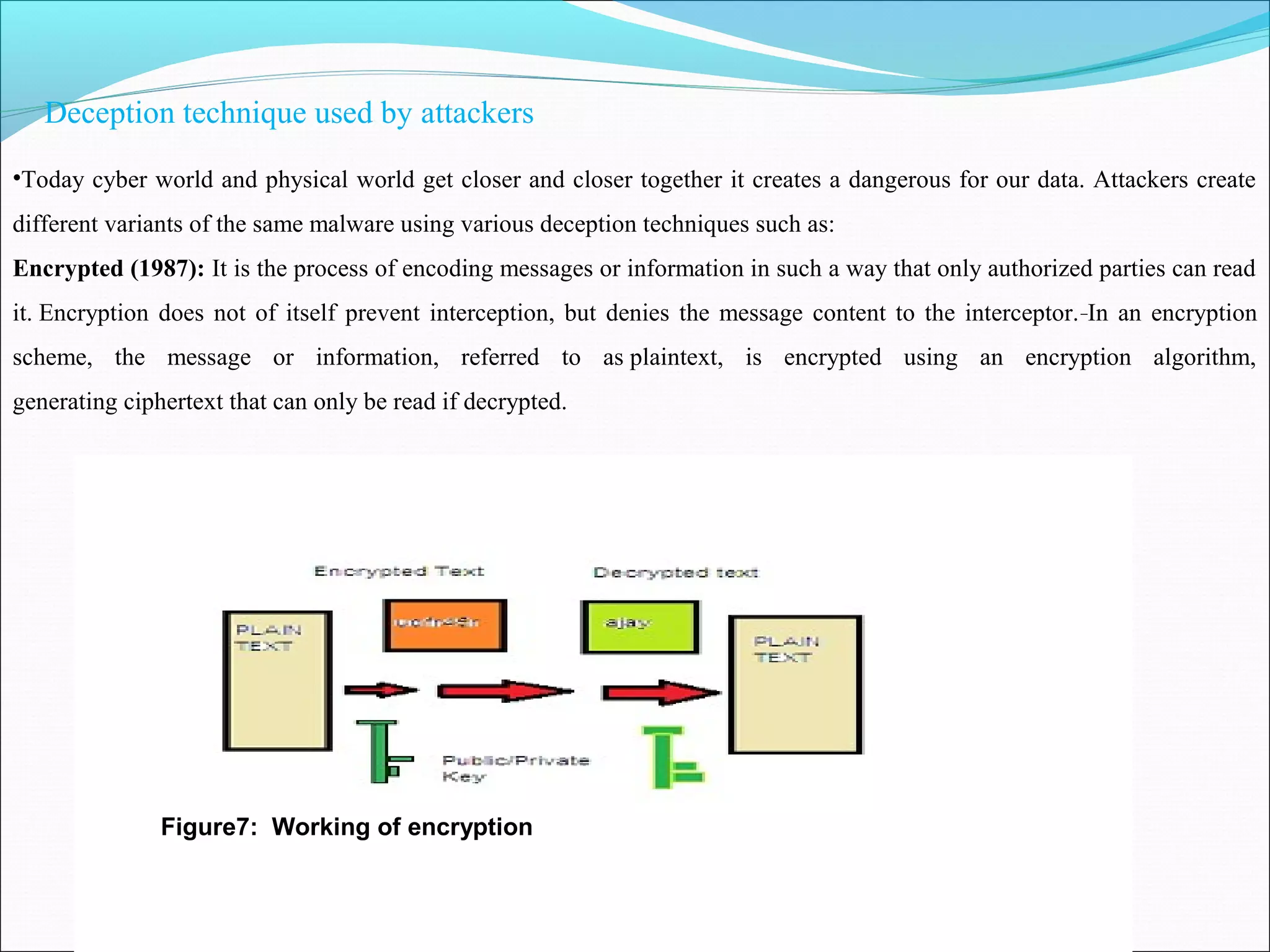

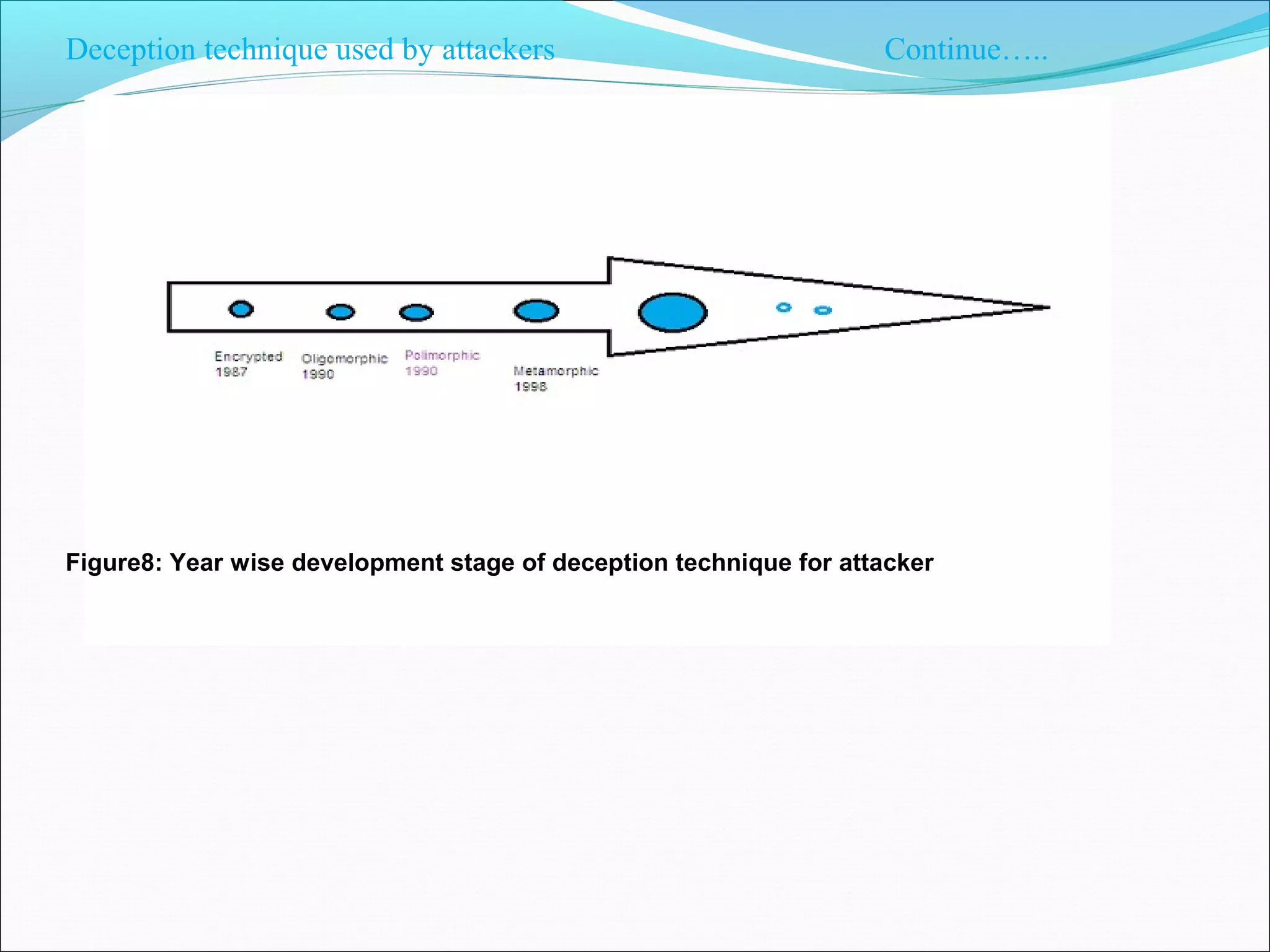
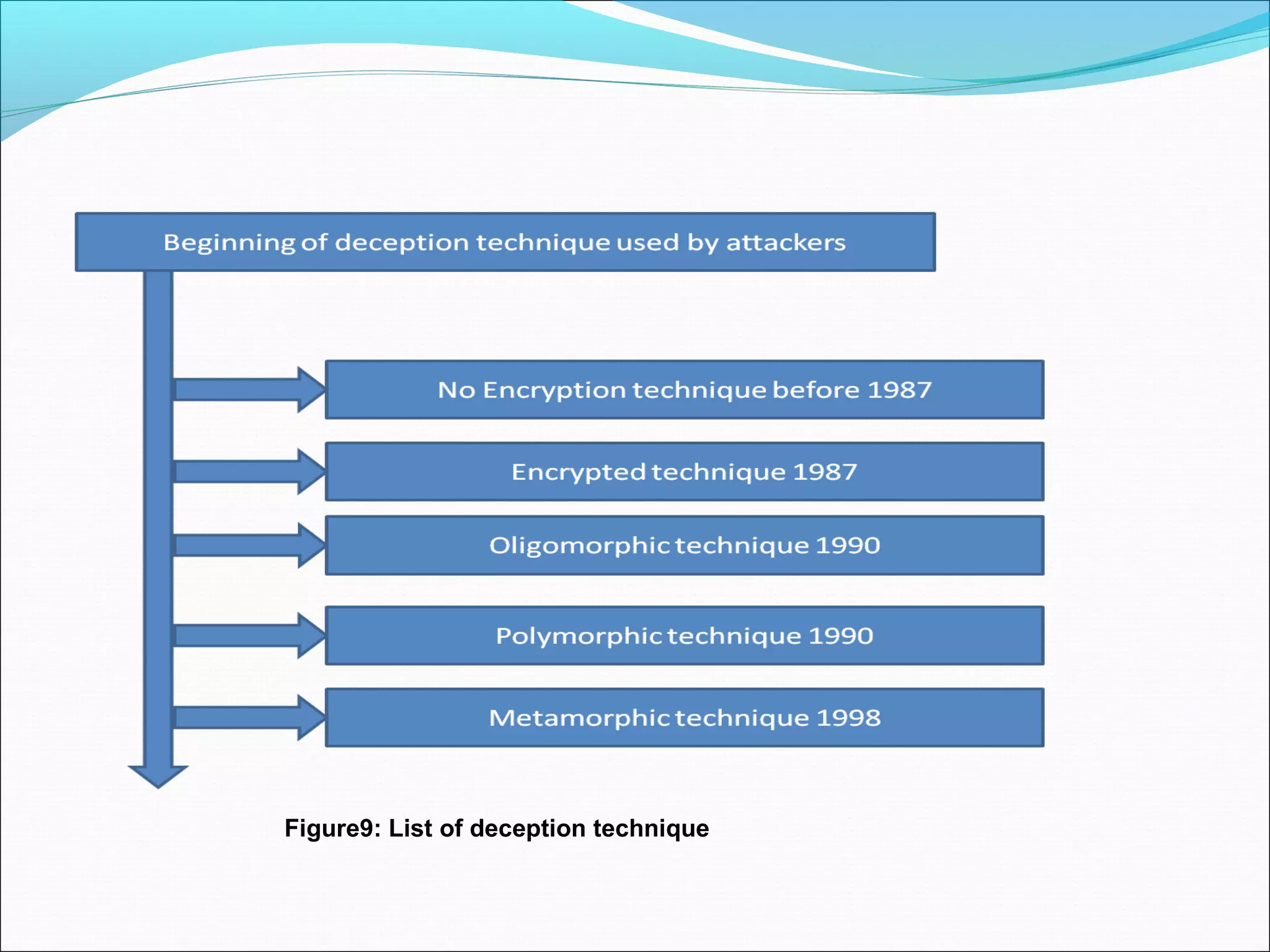
![Deception technique for defenders
•Honeypot deception technique: Honeypot is a trap set to detect, deflect, or, in some manner, counteract attempts at
unauthorized use of information systems.
•Generally, a honeypot, as shown in Figure 5, consists of a computer, data, or a network site that appears to be part of a
network, but is actually isolated and monitored, and which seems to contain information or a resource of value to attackers.
•This is similar to the police baiting a criminal and then conducting undercover surveillance [48].
Figure10: a block diagram of honeypot](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-45-2048.jpg)

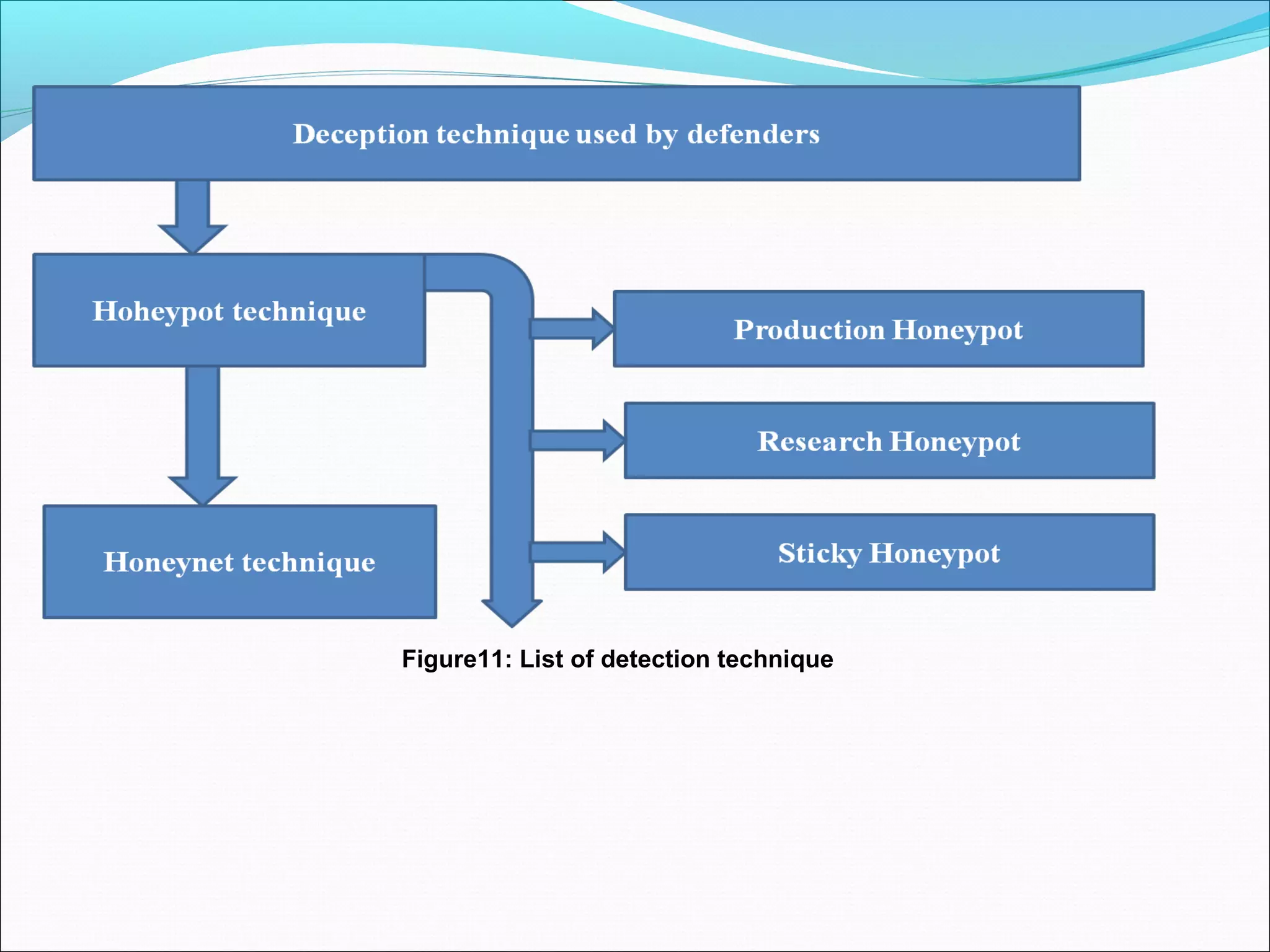
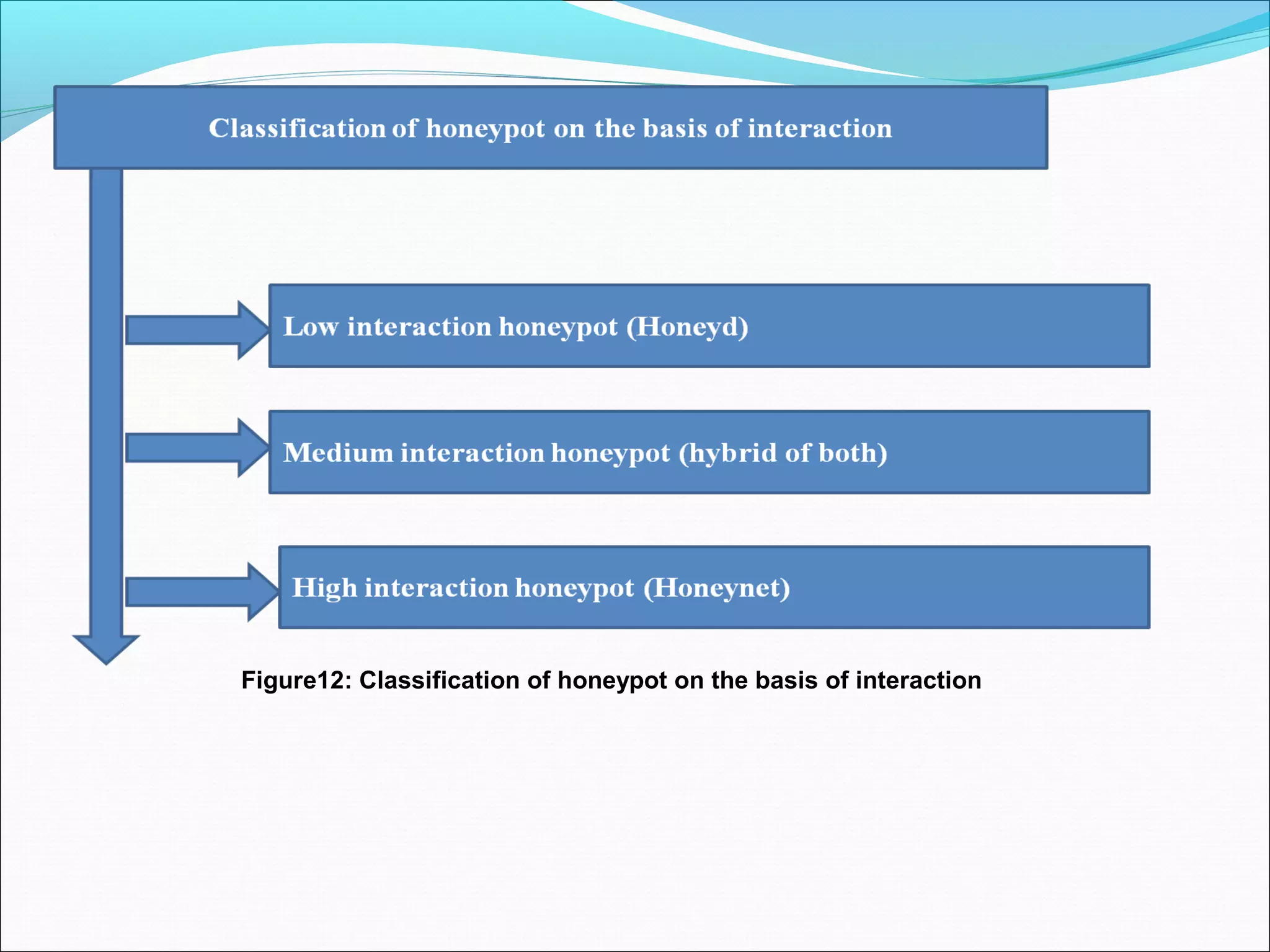
![Deception technique for defenders Continue……
Classification of Honeypots on the basis of interaction
•Low-interaction honeypots (LI-Honeypots): do not contain real operating system. These may generally copy all
activity of intruders but unable to defect their activity in a network. These are easiest to install, configure, deploy, and
maintain because of their simple design and basic functionality. Low-interaction honeypots simulate only the services
frequently requested by attacker (Honeyd).
•Medium-interaction honeypots (MI-Honeypots): same as(LI-HONEYPOT)services are more technically
Sophisticated
•High-interaction honeypots (HI-Honeypots): deploying inside a virtual machine using various virtualization software.
It captures full information about the attackers with their updated tools and technologies without any trouble so that they
are able to collect the full information about the intruders (Honeynet) [51].](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-48-2048.jpg)
![Deception technique for defenders Continue……
•Honeynet: A honeynet is a network set up with intentional vulnerabilities; its purpose is to invite attack, so that an
attacker's activities and methods can be studied and that information used to increase network security [52].
Figure13: A block diagram of honeynet](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-50-2048.jpg)


![References
[1]"An Undirected Attack against Critical Infrastructure" United States Computer Emergency Readiness Team. Retrieved 28 September 2014.
[2]M. W. Eichin and J. A. A. Rochlis. With microscope and tweezers: An analysis of the internet virus of november 1988. In Proceedings of the
1989 IEEE Computer Society Symposium on Security and Privacy, 1989.
[3] Ruchika Mehresh and Shambhu Upadhyaya. A Deception Framework for Survivability Against Next Generation Cyber Attacks. This research
is supported in part by DoD Grant No.H98230-11-1-0463.Usual disclaimers apply. In Proceedings of the Next Generation Cyber Attacks 2012.
[4]Frank Casta, Emre Can, Sezer, Jun Xu, WORM vs. WORM: Preliminary Study of an Active Counter Attack Mechanism. In Proceedings of the
ACM Press, 2002.. Copyright 2004 ACM 1-58113-970-5/04/0010. WORM'04, October 29, 2004
[5] Aruna.A, Perumal.S and Dr.A.Muthukumaravel. Modeling and Detection of Camouflaging
Worms-Using SDF. International Journal of Latest Trends in Engineering and Technology (IJLTET).Vol. 2, ISSN: 2278-621X, pp.192-198. Issue
4 July 2013
[6] Landwehr, C. E; A. R Bull; J. P McDermott; W. S Choi. "A taxonomy of computer program security flaws, with examples". 1993. DTIC
Document. Retrieved 2012-04-05.
[7] Basil Cupa, Trojan Horse Resurrected: On the Legality of the Use of Government Spyware (Govware),, pp. 419-428 LISS 2013.
[8] Jamie Crapanzano: "Deconstructing SubSeven, the Trojan Horse of Choice", 2003. SANS Institute, Retrieved on 2009-06-11.
[9] Basil Cupa, Trojan Horse Resurrected: On the Legality of the Use of Government Spyware (Govware),, pp. 419-428. LISS 2013
[10] "Rootkits, Part 1 of 3: The Growing Threat".McAfee. 2006-04-17. Archived from the original on 2006-08-23.
[11]Anson, Steve; Bunting, Steve. Mastering Windows Network Forensics and Investigation. John Wiley and Sons.. pp. 73–74. ISBN 0-470-
09762-0. Copyright Wiley 2007.](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-53-2048.jpg)
![References continue…….
[12]"Understanding Anti-Malware Technologies" Microsoft 2007-02-21. Retrieved 2010-08-17.
[13]Wang, Zhi; Jiang, Xuxian; Cui, Weidong; Ning, Peng (2009-08-11).Al-Shaer, Ehab. "Proceedings of the 16th ACM Conference on Computer
and Communications Security" CCS 2009: 16th ACM Conference on Computer and Communications Security. ACM New
York. doi:10.1145/1653662.1653728. ISBN 978-1-60558-894-0. Retrieved 2009-11-11
[14]Davis, Michael A.; Bodmer, Sean; LeMasters, Aaron (2009-09-03). "Chapter 10: Rootkit Detection".Hacking Exposed Malware and Rootkits:
Malware and rootkits security secrets and solutions. New York: McGraw Hill Professional. ISBN 978-0-07-159118-8. Retrieved2010-08
[15] wired.com: "How a Crypto ‘Backdoor’ Pitted the Tech World Against the NSA" (Zetter) 24 Sep 2013.
[16] H.E. Petersen, R. Turn. "System Implications of Information Privacy". Proceedings of the AFIPS Spring Joint Computer Conference, vol. 30,
pages 291–300. AFIPS Press: 1967
[17] Biham et al, LNCS3494 pp.36-57: "Advances in Cryptology - EUROCRYPT 2005: 24th Annual International Conference on the Theory and
Applications of Cryptographic Techniques, Aarhus, Denmark, May 22-26, 2005".
[18] G+M: "The strange connection between the NSA and an Ontario tech firm" 20 Jan 2014
[19]Karger, Paul A, Schell and Roger. "Thirty Years Later: Lessons from the Multics Security Evaluation"Computer Security Applications
Conference, 2002. Proceedings. 18th Annual (IEEE): 119-126. Doi: 10.1109/CSAC.2002.1176285. Retrieved 2014-11-08
[20]C.Y. Cho, D. Babic, R. Shin, and D. Song. Inference and Analysis of Formal Models of Botnet Command and Control Protocols, Conference
on Computer and Communications Security ACM 2010.
[21]Wang, Ping et al. "Peer-to-peer botnets". In Stamp, Mark & Stavroulakis, Peter. Handbook of Information and Communication
Security.. ISBN 9783642041174 Springer. 2010.
[22]"Trojan horse, and Virus FAQ". DSLReports. Retrieved7 April 2011.
[23]Tulloch, Mitch. Koch, Jeff; Haynes, Sandra, eds.Microsoft Encyclopedia of Security. Redmond, p. 16. ISBN 0-7356-1877-1. Washington:
Microsoft Press. 2003](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-54-2048.jpg)
![References continue…….
[24] McElroy, Damien; Williams, Christopher (28 May 2012)."Flame: World's Most Complex Computer Virus Exposed".The Daily
Telegraph. Archived from the original on 30 May 2012. Retrieved 29 May 2012.
[25]Murphy, Samantha (5 June 2012). "Meet Flame, the Nastiest Computer Malware Yet". Mashable.com. Retrieved 8 June 2012.
[26] "Symantec Report on Rogue Security Software". Symantec. 2009-10-28. Retrieved 2010-04-15.
[27]Young, A.; Moti Yung (1996). "Proceedings 1996 IEEE Symposium on Security and Privacy".
p. 129.doi:10.1109/SECPRI.1996.502676. ISBN 0-8186-7417-2
[28] "Browser Hijacker". MySearchCorp. Retrieved 3 July 2012.
[29]During the second half of 2007, 11,253 site-specific cross-site vulnerabilities were documented by XSSed, compared to 2,134 "traditional"
vulnerabilities documented by Symantec, in "Symantec Internet Security Threat Report: Trends for July–December 2007 (Executive
Summary)" (PDF) XIII. Symantec Corp. April 2008. pp. 1–3. Retrieved May 11, 2008.
[30]Grossman, Jeremiah and Robert Hansen, Seth Fogie, Petko D. Petkov and Anton Rager (2007). XSS Attacks: Cross Site Scripting Exploits
and Defense (Abstract). Elsevier Science & Technology via Google Book Search. pp. 70, 156. ISBN 1-59749-154-3. Retrieved May 28, 2008.
[31]Stuart Dredge (February 21, 2014). "The war against mobile 'adware' isn't over yet, warns Lookout". The Guardian. RetrievedMay 21, 2014.
[32]Callahan, Michael E. "The History of Shareware". Paul's Picks. Archived from the original on 2008-02-02. Retrieved2008-05-13.
[33] Erbschloe, Michael Trojans, Worms, and Spyware: A Computer Security Professional's Guide to Malicious Code. Butterworth-Heinemann.
p. 28. ISBN 9780080519685. (22 September 2004).](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-55-2048.jpg)
![References continue…….
[34] Ruchika Mehresh and Shambhu Upadhyaya. A Deception Framework for Survivability Against Next Generation Cyber Attacks. This
research is supported in part by DoD Grant No.H98230-11-1-0463.Usual disclaimers apply. In Proceedings of the Next Generation Cyber
Attacks 2012.
[35] Nikos Virvilis and Oscar Serrano. Changing the game: The art of deception against sophisticated attackers. Infosec.aueb.gr Deception
Publications CYCON-2014.
[36] Wei Zhou, Lixi Liu, He Jing, Chi Zhang, Shaowen Yao and Shipu Wang. K-Gram Based Fuzzy Keyword Search over Encrypted
Cloud Computing Journal of Software Engineering and Applications, pp. 29-32. 2013, 6
[37]Oppliger, Rolf "Internet Security: FIREWALLS and BEYOND". Communications of the ACM 40(5): 94. doi:10.1145/253769.253802.
(May 1997).
[38] Chang, Rocky "Defending Against Flooding-Based Distributed Denial-of-Service Attacks: A Tutorial". IEEE Communications
Magazine 40 (10): 42–43.doi:10.1109/mcom.2002.1039856. (October 2002).
[39] Satoru Torii, Masanobu Morinaga, Takashi Yoshioka, Takeaki Terada and Yuki Unno. Multi-layered Defense against Advanced
Persistent Threats (APT). FUJITSU Sci. Tech. J., Vol. 50, No. 1, pp. 52–59 (January 2014).
[40] Norzima Elbegbayan. Winnowing, a Document Fingerprinting Algorithm. TDDC03 Projects,. pp.01-07. Spring 2005
[41] The Crystals. Da do run run, 1963.
[42] H. Tamada, M. Nakamura, A. Monden, and K. Matsumoto. Design and evaluation of birthmarks for detecting theft of java programs.
In Proc. IASTED International Conference on Software Engineering (IASTED SE 2004), pages 569–575, Feb 2004.
[43] Kevin W. Bowyer and Lawrence O. Hall. Experience Using ”MOSS” to Detect Cheating On Programming Assignments.](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-56-2048.jpg)
![References continue…….
[44] Saul Schleimer, Daniel S. Wilkerson and Alex Aiken. Winnowing: Local Algorithms for Document Fingerprinting. SIGMOD 2003,
June 9-12, 2003, San Diego, CA. ACM 1-58113-634-X/03/06 Copyright 2003.
[45] Dominik Maier, Tilo M¨uller and Mykola Protsenko. Divide-and-Conquer: Why Android Malware cannot be stopped. ares-conference/
pp.01-10. 2014
[46] H. Tamada, M. Nakamura, A. Monden, and K. Matsumoto. Detecting the theft of programs using birthmarks. Information Science
Technical Report NAIST-IS-TR2003014 ISSN 0919-9527, Nov 2003.
[47] Ginger Myles and Christian Collberg. K-gram Based Software Birthmarks. Symposium on Applied Computing. SAC’05, March 1317,
2005, ACM 1581139640/05/0003 Copyright 2005.
[48] Aruna.A, Perumal.S and Dr.A.Muthukumaravel. Modeling and Detection of Camouflaging
Worms-Using SDF. International Journal of Latest Trends in Engineering and Technology (IJLTET).Vol., ISSN: 2278-621X, pp.192-198. 2
Issue 4 July 2013
[49] Masood Mansoori, Omar Zakaria and Abdullah Gani. Improving Exposure of Intrusion Deception System through Implementation of
hybrid Honeypot. The International Arab Journal of Information Technology, Vol. 9, No. 5, pp. 436-444 September 2012.
[50] Leita, c., Mennoud, K. & Dacier, M. ,. ScriptGen: A n A ttom ated Script Gen eration tool for Honeyd Proceedings of the 21S! Annual
Co mputer Security App l ications Conference, pp. 203-214. 2005
[51] Wira Zanoramy Ansiry Zakaria and Miss Laiha Mat Kiah. A Review on Artificial Intelligence Techniques for Developing Intelligent
Honeypot. This research is funded by UM Research Grant (UMRG). pp. 696-701.
[52] Ankush Kohli, Vikas Malik, Manjeet Singh and Gurjant Singh. Deploying Honeynet according to Perception of Attacker. International
Journal of Enhanced Research in Science Technology & Engineering, ISSN: 2319-7463, pp: (569-573). Vol. 3 Issue 3, March-2014](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-57-2048.jpg)
![References continue…….
[53] Haifeng Wang and Qinkui Chen. Dynamic Deploying Distributed Low-interaction Honeynet. JOURNAL OF COMPUTERS, VOL. 7, NO. 3,.
© 2012 ACADEMY PUBLISHER doi:10.4304/jcp.7.3. pp. 692-698 MARCH 2012.
[54] VidhyaSathish and Dr. P.Sheik Abdul Khader. AN EMPIRICAL STUDY ON IMPORTANCE OF MALWARE ANALYSIS AND
HONEYPOT TECHNOLOGY IN BOTNET RESEARCH. International Journal Of Research In Advance Technology In Engineering (IJRATE)
Volume 1, Proceedings of National Conference on Recent Trends In Web Technologies- Rtwt 2013 pp.125-127 Special Issue, October 2013.
[55] Frederico Araujo, KevinW. Hamlen, Sebastian Biedermann and Stefan Katzenbeisser. From Patches to HoneyPatches: Lightweight
Attacker Misdirection, Deception, and Disinformation CCS’14,, Copyright 2014 ACM 978-1-4503-2957-6/14/11 November 3–7, 2014
[56] Jiang, X and llingyan Xu,. BAiT-TRAP: A Catering Ho neypot Framewo r k [online]. Available at: http://www. cs. purdue. edulhom es /ji an
'{X/co lIapsar/publicat ion s/BaitTrap. Pdf. 2004.](https://image.slidesharecdn.com/finalppt-160825052844/75/list-of-Deception-as-well-as-detection-techniques-for-maleware-58-2048.jpg)
