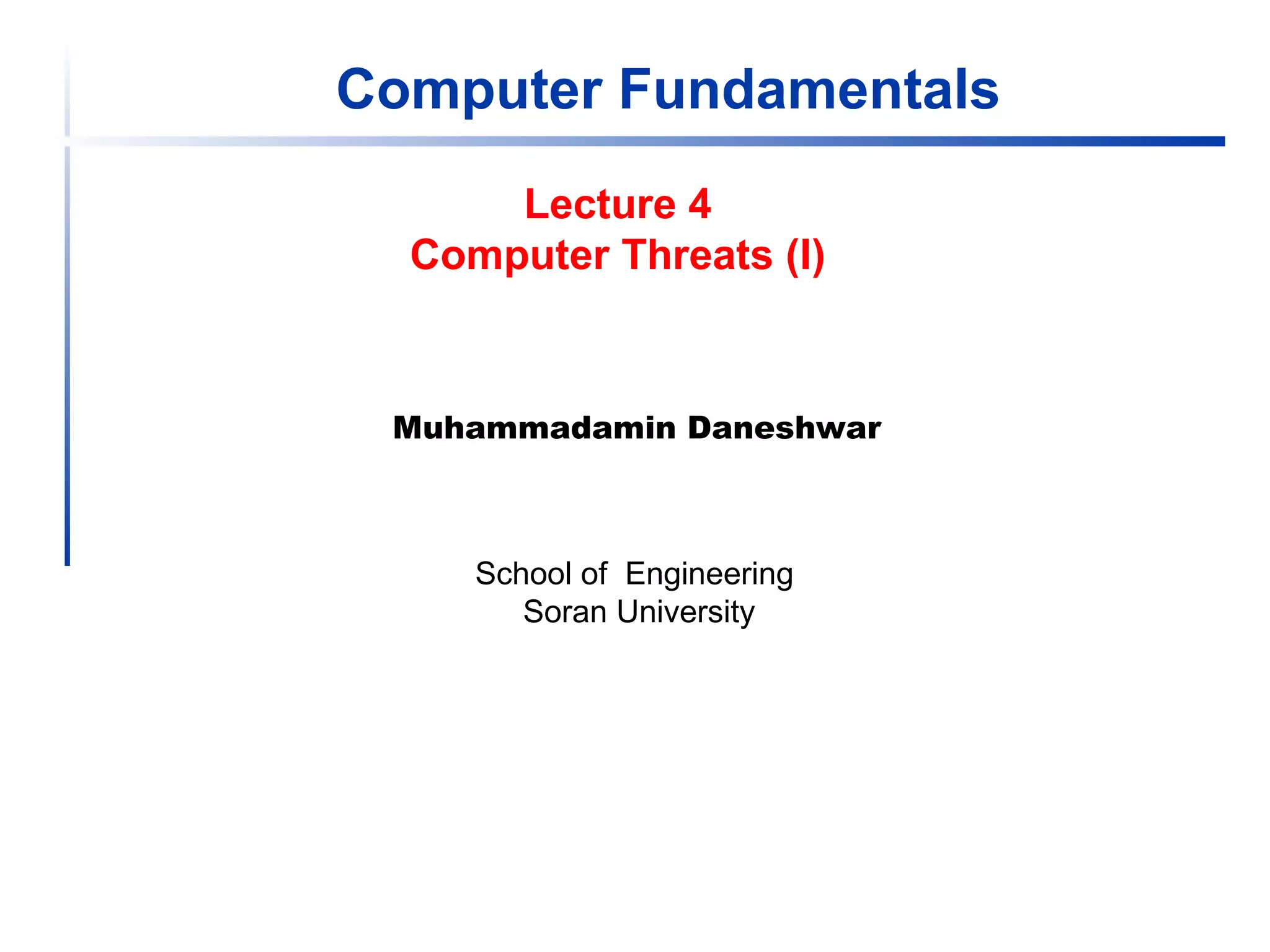
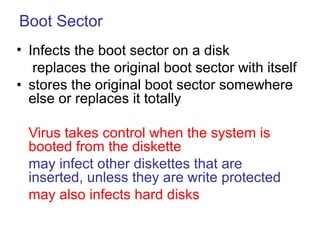
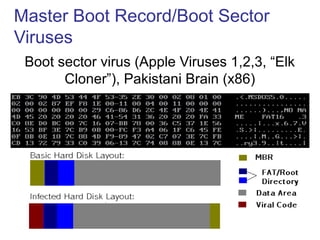
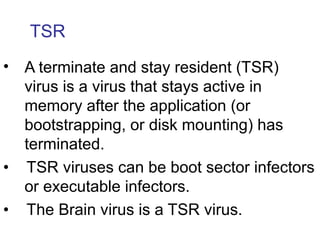
Computer viruses, worms, and other threats can damage systems. Viruses are programs that attach themselves to other programs and replicate. There are several types of viruses including boot sector, TSR, macro, and polymorphic viruses. Worms replicate independently across networks. Trojans also carry payloads but don't replicate. Antivirus software uses signatures to detect threats but also monitors for unusual activity. Maintaining strong passwords, firewalls, and updating systems help prevent infection.