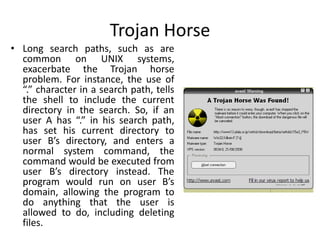
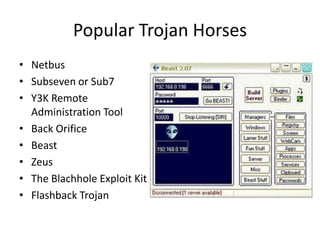
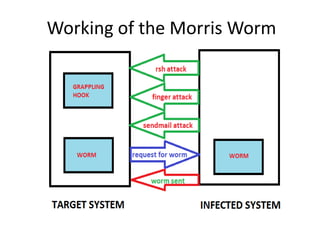
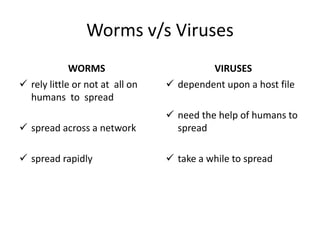
This document discusses various types of program and system threats including Trojan horses, trapdoors, buffer overflows, worms, viruses, and denial of service attacks. A Trojan horse masquerades as legitimate software to gain unauthorized access. Trapdoors are secret vulnerabilities built into programs by designers. Buffer overflows occur when more data is input than a program expects, potentially allowing code execution. Worms self-replicate to spread while viruses require host files or human action. Examples like the Morris worm and Love Bug virus are provided. Protection involves antivirus software and safe computing practices. The key differences between worms and viruses are also outlined.