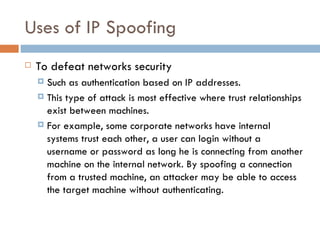
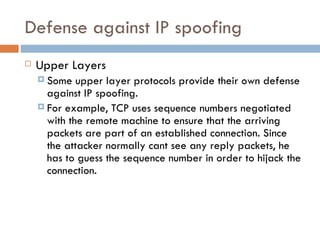
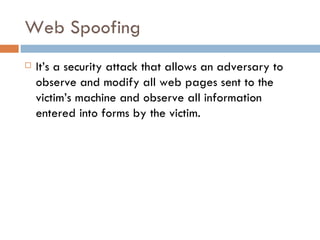
Web spoofing involves masquerading as another user or program to gain an illegitimate advantage. There are several types of spoofing, including IP spoofing where the sender address is falsified, and web spoofing where an adversary can observe and modify web pages sent to the victim. Defenses include ingress/egress filtering to block spoofed IP addresses, and users verifying URLs and SSL certificates when entering sensitive information online.









![Email Spoof with PHP function mail() The mail() function allows you to send mail. bool mail ( string $to , string $subject , string $message [, string $additional_headers [, string $additional_parameters ]] ) Example : www.rootspot.com/jose/mail](https://image.slidesharecdn.com/spoofing-100325110549-phpapp01/85/Spoofing-14-320.jpg)