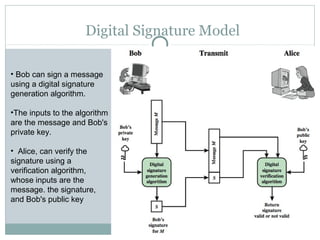
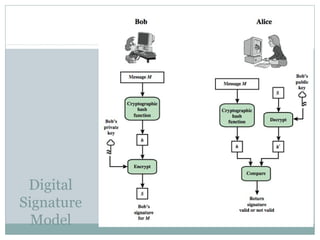
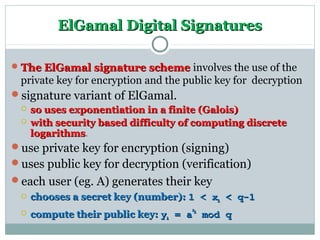
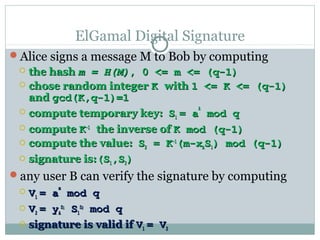
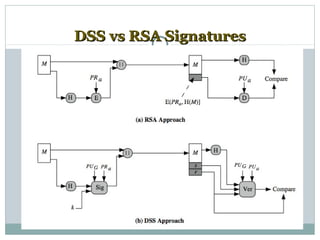
Digital signatures are authentication mechanisms that ensure the integrity and source of messages by attaching a code derived from the message's hash and the creator's private key. The document discusses various digital signature models, their security requirements, and different algorithms like ElGamal and DSS, highlighting potential attacks and the significance of using a public-private key infrastructure. It emphasizes the importance of properties such as verifiability by third parties, resistance to forgery, and proper key management to prevent disputes.





![[GOLD 88] then defines success at breaking a
signature scheme as an outcome in which C can do
any of the following with a non-negligible
probability:
Total break: C determines A’s private key.
Universal forgery: C finds an efficient signing
algorithm that provides an equivalent way of
constructing signatures on arbitrary messages.
Selective forgery: C forges a signature for a
particular message chosen by C.
Existential forgery: C forges a signature for at least
one message. C has no control over the message.
Consequently, this forgery may only be a minor
nuisance to A.](https://image.slidesharecdn.com/informationanddatasecuritydigitalsignatures-170928114350/85/Information-and-data-security-digital-signatures-10-320.jpg)



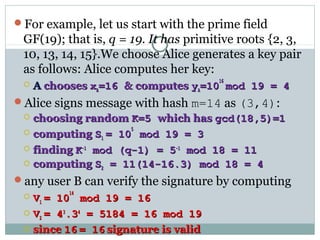



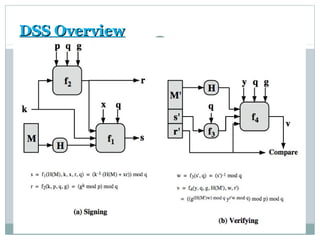
![DSA Signature CreationDSA Signature Creation
to sign a message M the sender:
generates a random signature keygenerates a random signature key k, k<qk, k<q
nb.nb. kk must be random, be destroyed after use, andmust be random, be destroyed after use, and
never be reusednever be reused
then computes signature pair:
r = (gr = (gkk
mod p)mod qmod p)mod q
s = [ks = [k-1-1
(H(M)+ xr)] mod q(H(M)+ xr)] mod q
sends signaturesends signature (r,s)(r,s) with messagewith message MM](https://image.slidesharecdn.com/informationanddatasecuritydigitalsignatures-170928114350/85/Information-and-data-security-digital-signatures-24-320.jpg)
![DSA Signature VerificationDSA Signature Verification
having received M & signature (r,s)
to verify a signature, recipient computes:
w = sw = s-1-1
mod qmod q
u1= [H(M)w ]mod qu1= [H(M)w ]mod q
u2= (rw)mod qu2= (rw)mod q
v = [(gv = [(gu1u1
yyu2u2
)mod p ]mod q)mod p ]mod q
if v = rv = r then signature is verified .](https://image.slidesharecdn.com/informationanddatasecuritydigitalsignatures-170928114350/85/Information-and-data-security-digital-signatures-25-320.jpg)