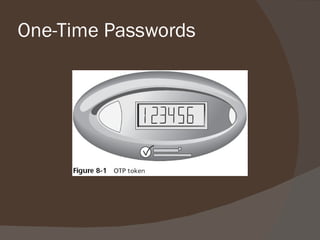
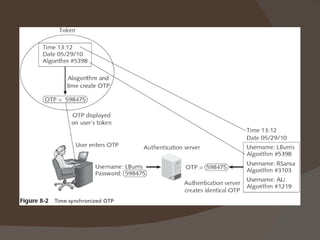
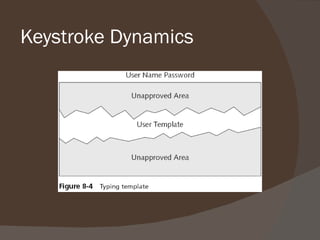
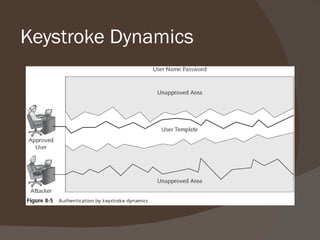
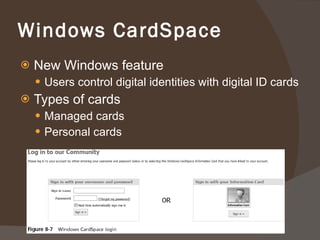
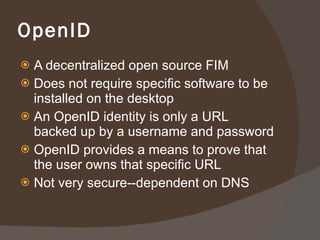
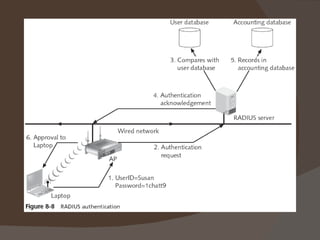
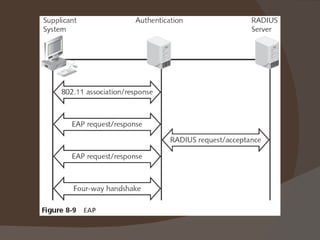
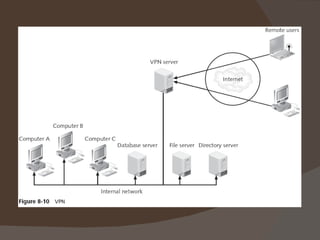
Chapter 8 discusses authentication objectives, defining key concepts like authentication, credentials, and access control. It covers various authentication models and protocols, emphasizing strong security measures such as two-factor authentication and the use of AAA servers. The chapter also explores VPN technologies and remote access policies for secure communication and management of remote users.