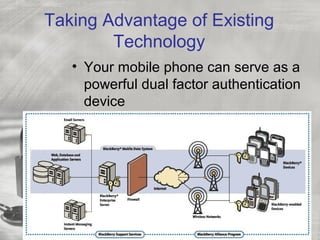
Nicholas A. Davis discusses various authentication methods and issues in electronic authentication. He covers passwords, one-time password devices, biometrics, digital certificates, and other authentication factors. Davis notes that current authentication relies too heavily on single factors like passwords, which are weak and easily stolen. He argues that the best solution is a hybrid approach using multiple authentication methods to achieve better security. Davis questions whether the future will include an official U.S. digital identity system and discusses potential benefits and drawbacks of such a system.