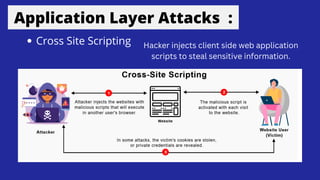
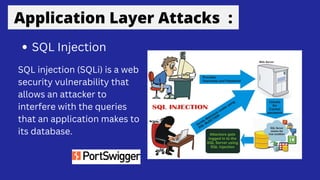
This document discusses application layer attacks and how attackers target vulnerabilities in applications and operating systems. It describes common application attack techniques like privilege escalation, improper input handling, error handling, cross-site scripting, buffer overflows, SQL injections, and DLL injections. The document provides examples of each type of attack and how attackers are able to compromise systems or access unauthorized data by exploiting vulnerabilities at the application layer.