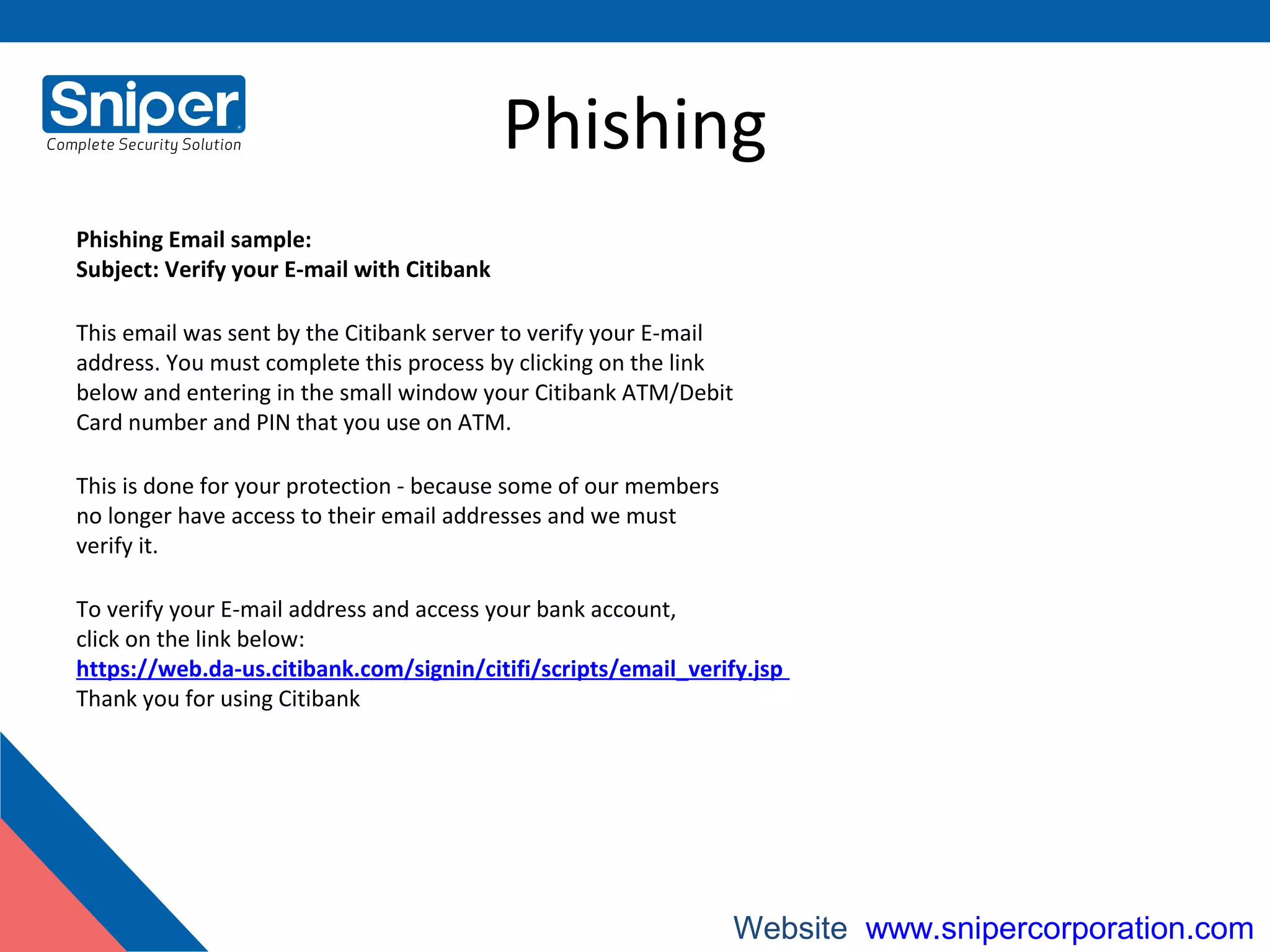
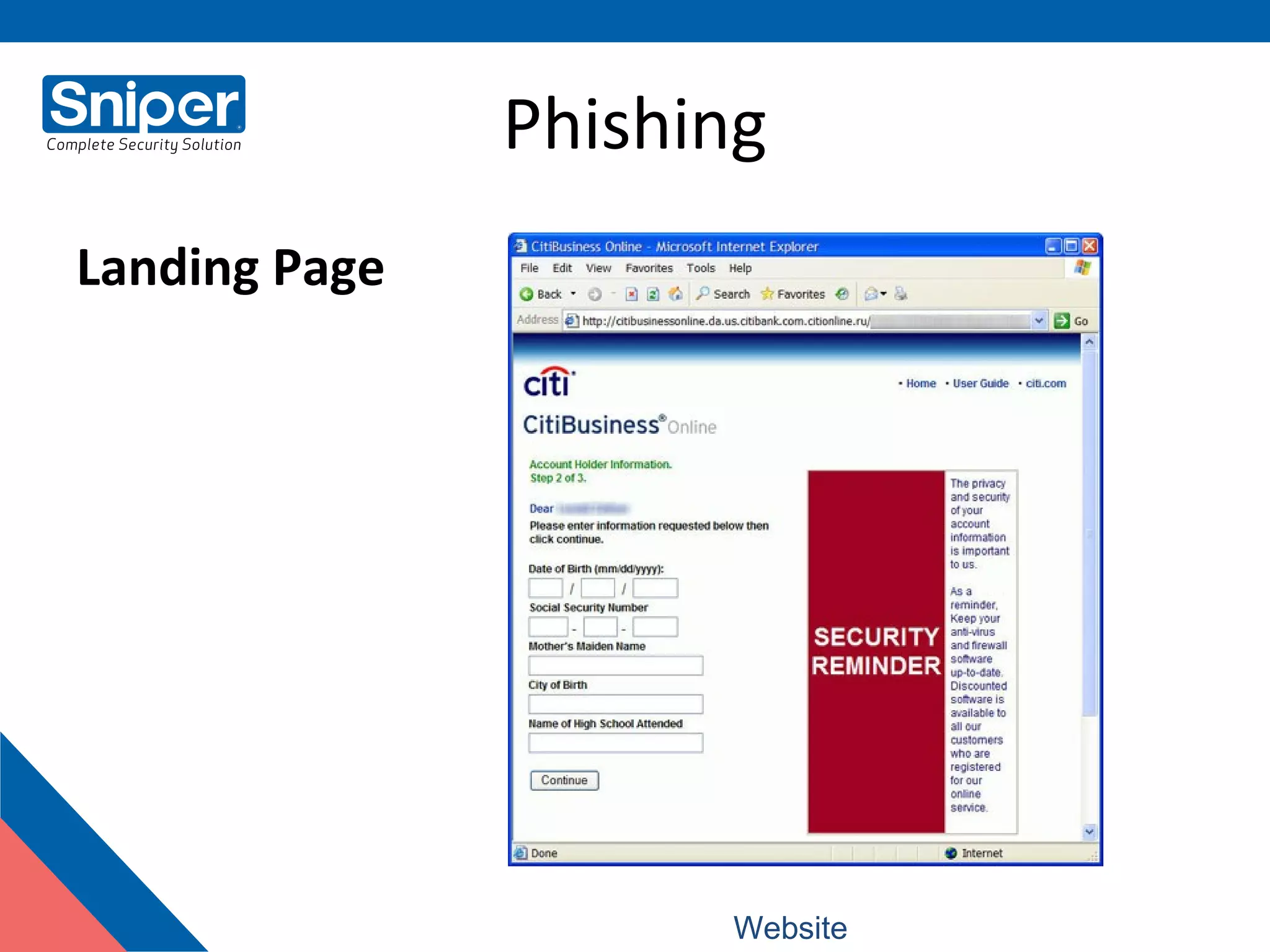
The document provides an overview of web security, detailing various threats such as hackers, viruses, ransomware, phishing, and denial of service attacks. It explains key terminologies and preventive measures, including the use of firewalls, updated browser software, and awareness against scams. Additionally, it highlights the productivity loss caused by email viruses and emphasizes actions individuals can take to secure their systems.